Using Active Directory Domains and Trusts
Windows 2000 Active Directory Domains and Trusts is an MMC snap-in that you can use to view a tree display containing all the domains in your forest. With this snap-in, you can manage the trust relationships between the domains, change the domain mode, and configure the user principal name (UPN) suffixes for the forest. Active Directory Domains and Trusts also provides access to Active Directory Users and Computers for each domain that you use to view and modify the properties of individual objects.
Launching Active Directory Domains and Trusts
Windows 2000 Server adds the Active Directory Domains and Trusts Manager snap-in to the Start menu by default, so after logging on using an account with administrative privileges, you can run the utility by selecting Active Directory Domains and Trusts from Administrative Tools in the Start menu's Programs group. The MMC snap-in file is called Domain.msc, so you can also launch the manager from the Run dialog box by executing that filename.
When Active Directory Domains and Trusts Manager loads, the console tree (on the left) displays all the domains in the forest in expandable tree fashion, stemming from a root labeled Active Directory Domains and Trusts, as shown in Figure 11-16. The result pane (on the right) displays the children of the currently selected domain, or if you select the root, the root domains of all the trees in the forest. The functions provided by Active Directory Domains and Trusts are all accessible from the Action menus produced by clicking a domain name or the root object, as well as within the Properties window for a domain.
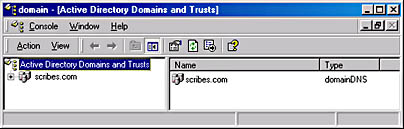
Figure 11-16. The Active Directory Domains and Trusts snap-in.
Changing the Domain Mode
When you open the Properties window for a domain, the General tab (shown in Figure 11-17) displays the NetBIOS name by which the domain is known to downlevel clients and enables you to specify a description for that domain. This tab also displays the domain's current operational mode and allows you to change it.
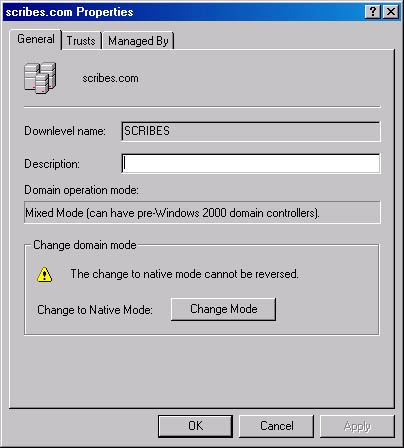
Figure 11-17. The General tab of the Properties window for a domain.
By default, newly installed domain controllers operate in mixed mode, which means that you can use Windows NT BDCs as domain controllers in a Windows 2000 domain. Thus, you can upgrade an existing Windows NT domain to Windows 2000 gradually by first upgrading the Windows NT PDC to Windows 2000. You can then use Active Directory to store information about your domain and modify the directory using the Active Directory snap-ins included with Windows 2000 Server.
When Windows 2000 Server is operating in mixed mode, the Windows NT BDCs are fully functional domain controllers in the Active Directory domain, capable of multiple-master replication just like Windows 2000 domain controllers. The only drawback to using mixed mode is that you can't take advantage of the Windows 2000 advanced grouping features, such as the ability to nest groups and create groups with members in different domains.
Once you've upgraded all the Windows NT BDCs in your domain to Windows 2000, you can switch the computer to native mode, which enables these grouping capabilities. However, once you switch the operational mode for the domain from mixed to native, you can't switch it back without reinstalling Active Directory. Be sure that you'll have no further need for Windows NT domain controllers on your network before making this modification.
![]()
NOTE
Mixed mode refers to the domain controllers only in a particular domain. After switching to native mode, you can still use Windows NT domain controllers in the same tree, as long as they are located in different domains.
Managing Domain Trust Relationships
The trust relationship between domains is managed on the Trusts tab of a domain's Properties window (Figure 11-18). When you establish a trust relationship between two domains, users in one domain can access resources located in another trusted domain. An Active Directory domain tree is a collection of domains that share not only the same schema, configuration, and namespace, but are also connected by trust relationships.
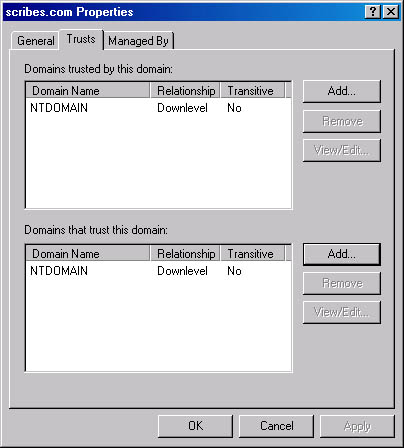
Figure 11-18. The Trusts tab of the Properties window for a domain.
Windows 2000 supports two types of trust relationships: the explicit, one-way trusts used by Windows NT, and the transitive, hierarchical trusts provided in Active Directory domains by the Kerberos security protocol. Windows NT trust relationships function in only one direction. For example, when domain A trusts the users in domain B, it doesn't automatically follow that B trusts the users in A. An administrator must explicitly create the trusts in both directions to achieve a mutual relationship between the domains.
Active Directory automatically creates Kerberos trust relationships in all the domains in a tree; they run in both directions, and they are transitive. A transitive trust relationship is one that is propagated throughout a tree hierarchy. For instance, when domain A trusts domain B and domain B trusts domain C, then domain A trusts domain C. The creation of each new domain in a tree includes the establishment of the trust relationships with all the other domains in the tree, enabling users to access resources in any one of the tree's domains (assuming they have the appropriate permissions) without manual configuration by an administrator.
To provide domain access to users in another tree or to grant the users in your domain access to another tree, you can manually establish trust relationships by clicking one of the Add buttons on the Trusts tab and specifying the name of a domain. These are one-way relationships; you must establish a trust for each domain in order to create a bidirectional trust. Depending on the nature of the domain to trust or be trusted, the relationship might or might not be transitive. You can establish a transitive trust relationship with Windows 2000 domains in another tree, but relationships with Windows NT domains can't be transitive.
To establish a trust relationship with another domain, you specify the name of the domain in the Add Trusted Domain dialog box and supply a password. To complete the process, an administrator of the other domain must specify the name of your domain in the Add Trusting Domain dialog box and furnish the same password. Both domains must approve before the systems can establish the trust relationship.
Specifying the Domain Manager
The third tab in a domain's Properties window, shown in Figure 11-19, identifies the individual who is the designated manager for the domain. This tab provides contact information about the manager derived from the associated user account in Active Directory. You can change the manager by clicking the Change button and selecting another user account from the Active Directory display shown.
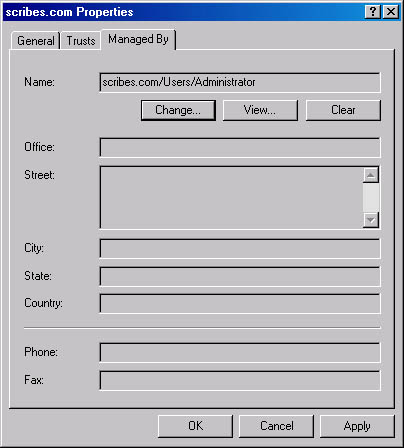
Figure 11-19. The Managed By tab of a domain's Properties window.
Configuring UPN Suffixes for a Forest
A UPN is a simplified name that users can supply when logging on to Active Directory. The name uses the standard e-mail address format consisting of a user-name prefix and a domain-name suffix, separated by an at sign (@), as defined in RFC 822 (for example, user@domain.com). UPNs provide network users with a unified logon name format that insulates them from the Active Directory domain hierarchy and the need to specify the complex LDAP name for their user objects when logging on.
By default, the suffix of the UPN for users in a particular forest is the name of the first domain created in the first tree of that forest, also called the forest DNS name. Using Active Directory Domains and Trusts Manager, you can specify additional UPN suffixes that users can employ in place of the forest DNS name when logging on. To do this, you select the root object in the console tree of the main Active Directory Domains and Trusts display (that is, the object labeled Active Directory Domains and Trusts), and choose Properties from the Action menu. On the UPN Suffixes tab, click the Add button to specify additional suffixes. These suffixes apply to the entire forest and are available to any user in any domain of any tree in that forest.
Managing Domains
The Active Directory Domains And Trusts snap-in also provides access to the Active Directory Users And Computers snap-in that you use to view and modify the objects in a domain and their properties. When you select a domain in the console tree of the main display and choose Manage from the Action menu, the MMC opens the Active Directory Users And Computers snap-in with the focus on the selected domain.
EAN: 2147483647
Pages: 366