Secure Things that You Can do Now
To get the ball rolling, two relatively simple things that you can consider now will provide some good security without any complications. All the other security procedures that I discuss in the book start off as being protection against an ordinary user . It is only when you combine a number of different protection techniques and set them up in a certain way that you have security for your database. Here is an overview of the straightforward secure things that you can easily do and descriptions of where they are applicable .
MDE Format: Gold Standard Security for Objects
If you want to secure the forms, reports , and modules in your database, there is no better and quicker way to do so than to convert your database to the compiled format, called the MDE format. Before you do that, you need to
-
Split your database into two databases. The first will hold all your software (queries, forms, reports, macros, and modules) and the second will hold all your data and relationships. Many of this book's readers will no doubt know this structure, but if you don't understand it, you should read the section on splitting your database in Chapter 4.
-
Make sure that development is not happening to the live front-end database. You will need to have well-established control over who develops the front-end database and where that development takes place before you embark on using the MDE format.
-
Ensure that development takes place on a computer drive to which the database users do not have access.
To make an MDE-format database, all you have to do is choose Tools ˜ Database Utilities ˜ Make MDE, and you will have your MDE-format database.
If you are unsure whether the MDE format database will suit your needs, use it yourself as your production version. Once you have completed your test, direct a small number of users to try the MDE version. Generally, switching over to the MDE format is quite simple as long as you have good control of front-end database development. For further description of MDE databases, read Chapter 11.
| Caution | The MDE format will not provide any security for your tables, queries, or macros. |
Use the Operating System to Restrict Who Uses the Database
To preclude some of your fellow network users from opening your database, your best option is to use the operating system to restrict the people who will actually have access to the database. To give you some understanding of how this process works, I will give you a brief rundown here:
-
Place your database and related files in the specific database folder.
-
Create a new group of users (which I call "Access Editors") by using a Windows Server or Windows Peer-to-Peer computer.
-
Make any Windows user whom you want to open the database a member of this new group.
-
Remove all permissions for users and groups that currently have operating system permissions to open and use the files in the special database folder.
-
Grant permissions to the new user group (Access Editors) so that they can create, modify, and delete any files in that special database folder (as shown in Figure 1-2).
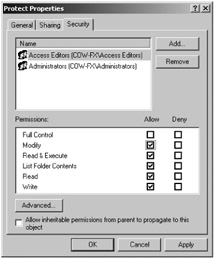
Figure 1-2: The permissions on a folder that a normal Access database uses.
Although this sample is not complete, I thought it was important enough to demonstrate the permissions in the Windows professional and server operating systems. Using this method to reduce the number of people using the database is very important because the Windows operating system's security is the result of much past and ongoing research for Microsoft. You can find out more about the operating system permissions in Chapter 12, particularly how to set up folders so that users cannot browse the folder contents. To supplement this security, this book discusses how you can combine using the Windows operating system with the Access internal security tools whenever it can.
In the next section, I will outline one of the more interesting bylines to the book ”the topic of upgrading software. At this juncture, let me tell you that my normal counsel to clients is to bide their time when it comes to software upgrades. Unusually though, while writing this book, I came to realize that I was impressed by the subtle but useful changes that the newer versions of Access and Windows offered to protect the database.
EAN: 2147483647
Pages: 176
- Chapter I e-Search: A Conceptual Framework of Online Consumer Behavior
- Chapter VI Web Site Quality and Usability in E-Commerce
- Chapter IX Extrinsic Plus Intrinsic Human Factors Influencing the Web Usage
- Chapter XVI Turning Web Surfers into Loyal Customers: Cognitive Lock-In Through Interface Design and Web Site Usability
- Chapter XVIII Web Systems Design, Litigation, and Online Consumer Behavior