An Introduction to Spread Spectrum
|
| < Day Day Up > |
|
The premier technology that overthrows the fundamental assumption that spectrum must be licensed to avoid interference is "Spread Spectrum," a technology that spreads a radio signal out over an entire frequency range, preventing concentration of the signal in any one place, allowing large numbers of users to share the same bandwidth. The military developed it for use in reliable, secure, mission-critical communications systems, based on ideas worked out in the 1940s to overcome intentional interference by hostile jamming and eavesdropping.
In 1924 Alfred N.Goldsmith filed the earliest U.S. patent that can be construed as being spread spectrum. Later, in 1940, Hedy Lamarr, the actress, created the concept of spread spectrum and two years later received a U.S. patent for a "secret communication system." The patent was issued to her and George Antheil, a film-score and avant-garde composer, to whom Lamarr had turned for help in perfecting her idea. The Lamarr-Antheil system uses a (primitive and probably unworkable) mechanical switching device similar to a player piano roll to shift frequencies faster than an enemy could follow them.
In Robert Scholt's highly acclaimed historical paper entitled "The Origins of Spread Spectrum Communications," Scholt states that one of the earliest applications of spread spectrum was the communications link between Roosevelt and Churchill during World War II, although at the time the technique was not known as spread spectrum. The full text of the Scholt paper can be found in the IEEE Transactions on Communications, Vol. Com-30, No. 5., May 1982, 822-854. (Robert Scholt received the 1983 Leonard G. Abraham Prize Paper Award and the 1984 IEEE Donald G. Fink Prize award for his work.)
After the invention of the transistor and microelectronics, the U.S. Army began using spread spectrum in the 1950's for Electronic Counter Countermeasures and in electronic warfare because of its characteristics of Low Probability of Interference (LPI), Low Probability of Detection (LPD), and anti-jam capability.
More recently, spread spectrum has been combined with digital technology for spy-proof and noise-resistant battlefield communications. In 1962, Sylvania installed it on ships sent to blockade Cuba. (Indeed, it was Sylvania that came up with the name "spread spectrum.") But spread spectrum also has been utilized in a few, special non-military applications. The NASA space shuttle S-Band communications links implemented spread spectrum for interference avoidance. The spread spectrum-based Tracking and Data Relay Satellite System (TDRSS) program was used for multiple access purposes in which several users simultaneously share the same satellite repeater power and bandwidth.
Wireless equipment engineers also realized that spread spectrum technology offered many solutions to questions that had previously stalled the development of credible wireless networking. These innovative engineers realized that spread spectrum techniques could allow wireless systems to reuse frequencies within the Institutional Scientific Medical (ISM) band without interference. That was important, because the discovery meant that low-cost, FCC license-free wireless networking products could become a reality. By the mid-1990s the FCC had a number of wireless networking standards presented for its review.
The term "spread spectrum" arose from the characteristic broad spectral shape of the transmitted signal. Although spread spectrum techniques are widely used today in mainstream wireless systems, its full potential wasn't realized until there was enough computing power available to exploit its full capabilities.
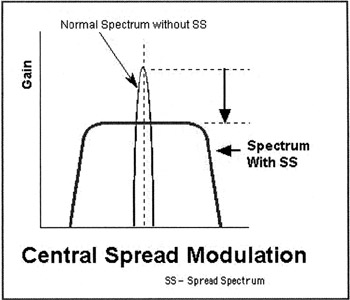
Figure 5.1: A spread spectrum signal wave.
In a spread spectrum system, signals are chopped up, distributed across many frequency bands and then reassembled on the other end. Spread spectrum allows two or more users to share the same frequency band, sometimes at the same time, sometimes at different times, depending on the system used. It's reminiscent of the way Internet routers allow millions of people to share the same data networks. However, the Internet processes data packets in a decentralized way, and spread spectrum enables receivers to distinguish overlapping communications based on codes that identify data packets belonging to specific users. The smarter the devices are-at both ends of the transmission-the more users a system can accommodate. This means that a Wi-Fi transmission won't necessarily interfere with a cellular voice communications service using the same spectrum segment. Thus, there isn't any need to give any one service exclusive use of a particular band of spectrum; all that's needed are mechanisms to ensure that equipment used to transmit and receive does so cooperatively, rather than in a contentious manner.
Spread spectrum is designed to trade off bandwidth efficiency (i.e. the signal is spread over a broad range of frequencies) for reliability, integrity, and security. This means that more bandwidth is consumed than in the case of narrowband transmission, but this tradeoff produces a signal that is, in effect, louder and thus easier to detect, provided that the receiver knows the parameters of the spread spectrum signal being broadcast. A receiver that is tuned to the right frequency and possessing the proper decoding procedure can extract the message, thus allowing a greater number of users to share the bandwidth. (For a receiver that does not have these capabilities, a spread spectrum signal just looks like background noise.)
| Note | In the past, systems that used the radio spectrum relied primarily on narrowband modulation techniques whereby all of the power in a transmitted signal is confined to a very narrow portion of the frequency bandwidth. The problem with these techniques is that an interfering frequency at or near the transmitting frequency can cause interference, rendering the signal unrecoverable. Amplitude Modulation (AM) is an example of a narrowband technique in which the amplitude (volume) of the carrier signal is made stronger or weaker based on the information in the signal to be transmitted. The large amounts of power associated with AM allow the signal to travel long distances before it attenuates to an undetectable level. That's why AM radio stations' broadcast signals can be received over long distances |
In order to qualify as a spread spectrum signal, the following criteria must be met:
-
The transmitted signal bandwidth is greater than the minimal information bandwidth needed to successfully transmit the signal.
-
Some function other than the information itself is being employed to determine the resultant transmitted bandwidth.
There are many benefits to using spread spectrum. For instance, since the signal is spread over a large bandwidth, its duration on any particular frequency in the allocated frequency segment is just a fraction of a second, and its "power density" is very low. This means that the average detectable power on any given channel is extremely low, and other devices using the same channel won't notice the spread spectrum transmission. And since the transmitted spread spectrum signal is uniformly spread over a wide range of frequencies, the signal steers clear of interference and noise from other signals.
Interestingly, the bandwidth at these frequencies can be "reused," because when spread spectrum coexists with narrowband signals, the only result is a slight increase in the "noise floor" in any given slice of spectrum used by the conventional narrowband transceivers. In other words, narrowband transceivers can continue to use their respective slices of the spectrum, and any overlapping spread spectrum signals will only be detected as a slight background noise. Moreover, as we've seen, spread spectrum transceivers can also share the same frequency band with other spread spectrum transceivers.
Spread spectrum communications are normally secure, because spread spectrum produces a pseudo-random signal, so the transmitted signal appears as noise to other receivers-only receivers possessing the proper duplicate pseudo-random noise code sequence are able to recover the signal. Hence, multiple stations can simultaneously transmit spread spectrum and narrowband broadcasts.
The reader might wonder, if spread spectrum technology is supposedly secure and Wi-Fi uses it, why is there such concern over Wi-Fi security? Many Wi-Fi vendors initially did claim that it was difficult or impossible to "despread" or demodulate the signals, but this is not actually the case; spread spectrum techniques are not absolutely secure. Wi-Fi's spread spectrum technology modulates the RF signal and spreads the transmission over the entire frequency band allocated for Wi-Fi communication. The spread spectrum technique Wi-Fi uses adds a redundant pattern to each bit transmitted and only the sender and receiver hardware are supposed to know the particular code used to generate these patterns. In actuality, intruders can crack this code relatively easily, since spread spectrum was incorporated into Wi-Fi not for reasons of security, but because of the improved signal-to-noise ratio and resistance to interference.
| Note | Don't worry, the industry is working diligently to address Wi-Fi's security dilemma and have come up with some very innovative solutions as discussed in Chapters 6 and 17. |
Getting back now to our perusal of spread spectrum, there are a number of incarnations of spread spectrum modulations, but we will only discuss, very briefly, two-frequency hopping and direct sequence-both have advantages and disadvantages associated with them. It's these two spread spectrum techniques that play a large part in the acceptance of the IEEE 802.11 standard for the implementation of wireless LANs.
DSSS and FHSS
Direct Sequence Spread Spectrum (DSSS) works by taking a modulated narrowband carrier rapidly modulating its phase so that it expands, occupying a bandwidth much greater than the information bandwidth of the signal. This modulation/expansion is performed by multiplying the information signal by a code called a "spreading code" or pseudo-noise (PN) spreading sequence, a deterministic, computed, binary sequence of bits (1s and 0s) that nevertheless appears to be random. This code is generated by a pseudorandom generator that produces one out of millions of possible binary number sequences of a fixed length. After a given number of bits are produced, this code repeats itself exactly. This "almost random" code has a bit rate significantly greater than the information bit rate, and when it is used to modulate the carrier phase it spreads the signal energy over a wider portion of the frequency spectrum than would the narrow-band signal alone. The amount that the signal is spread is determined by the ratio of the bit rate of the spreading sequence divided by the data rate of the information signal (this ratio is also known as the "processing gain") The bandwidth of the spread signal is the product of the bandwidth of the unspread signal and the processing gain. Each bit of the pseudorandom number sequence is often referred to as a "chip," and the bit rate of the sequence is called the "chip rate." The receiver then uses the same PN sequence to "despread" and "decrypt" the original signal by multiplying the signal with a locally generated reproduction of the PN sequence.
Since the transmission is spread across a wide frequency band (a result of the spreading process), transmission power is lower than that of narrowband transmissions. Thus, to other radio services operating in the same band, the signal appears to be low power background noise. But since the signal is low power and spread across a wide frequency range, the spread spectrum signal itself is susceptible to noise. However, in cases of signal corruption the redundant data helps to recover the original signal; the number of chips is directly proportional to the immunity from interference.
Unlike DSSS, which chops the data into small pieces and spreads them across the frequency domain, in Frequency Hopping Spread Spectrum (FHSS) systems, the carrier frequency of the transmitter abruptly changes (or hops) as dictated by a generated pseudorandom code sequence. A short burst of data is transmitted on a narrowband and then the transmitter quickly returns to another frequency and transmits again. The sequence of hops the transmitter makes is pseudo-random, but the receiver knows the pattern, enabling it to receive each short burst of data at the proper frequency and time and thus reproduce the original constant signal. Since the transmitter and receiver are synchronized, the stream of data appears to be constant. (To other radio services, the FHSS signal appears as a short burst of noise.)
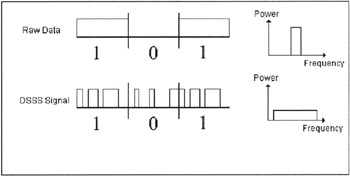
Figure 5.2: Direct Sequence Spread Spectrum.
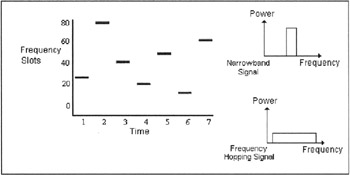
Figure 5.3: Spread Spectrum using the frequency hopping technique.
There are certain rules governing how a FHSS device must behave to ensure that a device doesn't use too much bandwidth or linger too long on a single frequency. For instance, in North America, the ISM band is separated into 75 hopping channels and the power transmitted on each channel must not exceed one Watt.
Frequency hopping devices have different characteristics when compared to DSSS devices. First, DSSS provides a higher throughput and is more immune to interference than frequency hopping. However, there is a tradeoff: DSSS uses two to three times more power and tends to be more costly than FHSS. But, since FHSS's immunity to interference tends to be lower than DSSS signals, if a burst of data is corrupted on one hop then the entire data packet must be sent again. Still, frequency hopping does have one major advantage over direct sequence-several access points can coexist in the same area. Consequently, if an access point is struggling to cope with a large number of users, another access point can be added to take some of the load. This cannot be done with DSSS access points as they would block each other from transmitting.
Such techniques, however, do trade off power against bandwidth and range. A narrowly focused, high-power signal overwhelms other signals. To understand this, consider one of the raucous Sunday morning talk shows, where everyone is speaking at once. As each pundit tries to get their thought across, each person begins to speak ever louder, causing a domino effect as everyone at the table begins to yell louder and louder in an effort to be heard. In the ensuing carnage, no one can be heard, so no one gets his or her message across. On the other hand, if a low-power signal is spread over a wide range of frequencies or is sent a shorter distance, many communications can coexist. The same occurs in the case of a "pundits' corner"-if everyone speaks in a calm, controlled manner, everyone's point of view can be heard and considered.
|
| < Day Day Up > |
|
EAN: 2147483647
Pages: 273