| Traditional wisdom with software updates is that you wait for other administrators who are clamoring to be first on the bandwagon to install the updates and find out what, if any, issues the updates caused. Once there has been some public testing and it looks as though the update helps more than it hurts, you go ahead and install it. But now, in this day and age of constant Internet attacks, it is increasingly risky to leave a computer unpatched and vulnerable, especially with respect to security updates. You now have to balance these two approaches carefully. For updates that contain new features and functionality, there is less reason to rush to install, especially on a server. On the other hand, it is probably advisable to install security updates as soon as possible. Fortunately, because patches are qualified by both Apple and the open source community, security updates are usually timely, reliable, and unlikely to create problems. The Software Update Server can permit users to run the application as they normally would, except for the fact that they are actually connecting to your server. To set up and manage the Software Update service, please refer to Chapter 13, "Client Management." Another option when you're securing a server is to restrict the users who can access the server via ssh. Since ssh is turned on by default when you install and configure Mac OS X Server, a good password may not be enough to keep others out. You can use open source software contained in Mac OS X Server to generate a key and then give the key to individuals who are permitted to log in via ssh. To create an ssh key 1. | Launch the Terminal application located in /Applications/Utilities, enter the command ssh-keygen t dsa, and press Return (Figure 10.31).
Figure 10.31. Using the Terminal to create a public/private key pair. 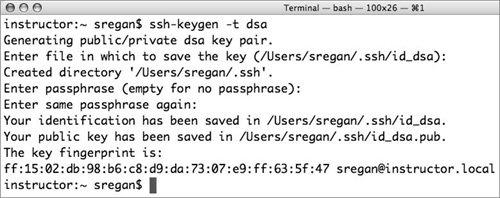
This command generates the two files necessary for the encryption using the type dsa: the file id_dsa contains the private part of the key, and the file id_dsa.pub contains the public part of the key.
| 2. | In the line that appears after pressing Return from step 1, you do not need to provide a filename. So you can press Return again.
| 3. | On the line that now appears, you can add an optional passphrase to encrypt the private key with Triple-DES encryption for even more security.
| 4. | Copy the id_dsa.pub file to your administrator's home folder on the server. If it doesn't already exist, create a folder called .ssh in the home folder on the server, move the id_dsa.pub file into the .ssh/ folder, and rename it authorized_keys (Figure 10.32).
Figure 10.32. Renaming the file on the server. 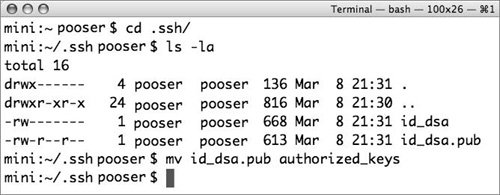
| 5. | On your server, open and edit the /etc/sshd_config file using any command-line editor by changing the following lines from:
#PasswordAuthentication yes #ChallengeResponseAuthentication yes
to
PasswordAuthentication no ChallengeResponseAuthentication no
| | | 6. | You may want to restart your server at this point because attempting to stop and restart ssh can cause you to lock yourself out of your server.
| 7. | Attempt to log in again from the Mac OS X computer that generated the keys and enter the passphrase when requested.
Any hackers who attempt to log in using your short name will not be able to log in without the private key on their computer.
|
 Tips Tips
It's a good idea to also copy the .ssh directory on your server from your administrator's home folder to root's home folder, thus keeping a direct remote root login safer by restricting it to key access. Make a backup copy of the keys, and install them on all machines that may require other administrators to ssh into the server. You may also wish to copy the authorized_keys file from one administrator account to other accounts or to generate individual keys for each user. If you don't enter a passphrase when you generate a key, then when a user opens the Terminal and attempts to log in with the admin account, they won't be asked for a password or passphrase. This can be dangerous, because the client computer can access the server by opening the Terminal and typing in ssh admin_name@ip_address.
|


 Tips
Tips