Section 15.6. Adware, Spyware, and Other Threats
15.6. Adware, Spyware, and Other ThreatsJust about everybody's heard the terms virus and spyware by now, but they're only a few examples of a growing category of software called malware : programs designed for malicious purposes. Most slip into your PC behind your back, leaving problems in their wakes. This section describes the various types of malware, how to identify them, and most importantly, how to get rid of them. Figure 15-9. These "phishing" emails are some of more than 35 million fraudulent email messages sent to people during the first six months of 2005, according to IBM. Don't respond to any requests like this that arrive through email; they're all scams. Instead, type the company's email address into your browserdon't click the emailed linkand then forward the email to the company's security department.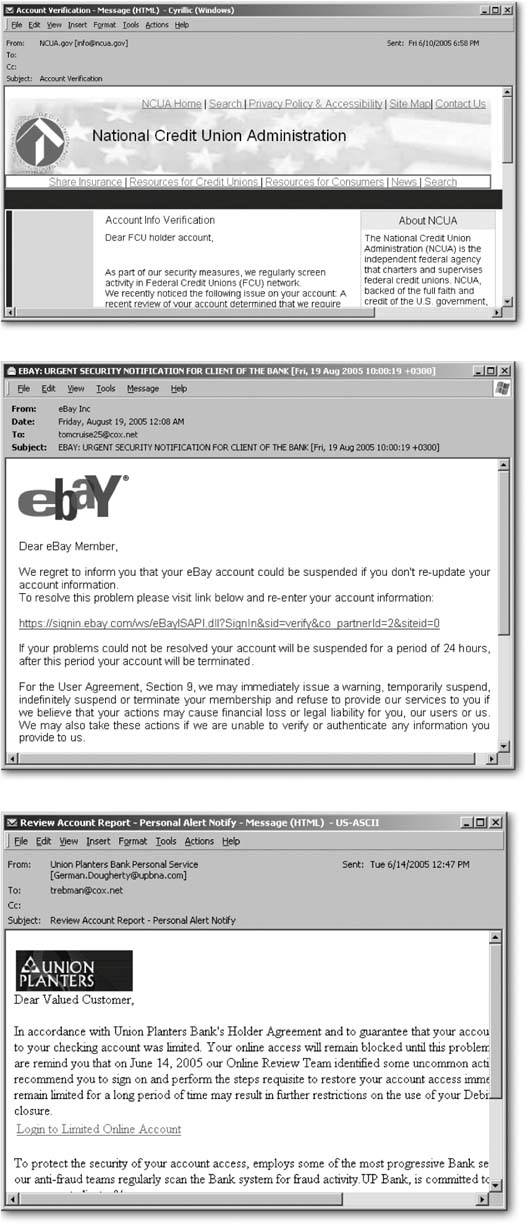 15.6.1. Types of MalwareMalware goes unloved by everybody but its creators . Unfortunately, removing malware is much more difficult than becoming infected by it. Here are some of the most common types of malware found today, so you'll know just what your antivirus program is talking about.
15.6.2. SymptomsAny or all of these symptoms may appear when your PC's infected with a virus, spyware, or other malware variant:
When your PC's acting strangely, fire up a free spyware scanning program (see Section 15.6.3.2) instead of calling tech support or reinstalling software. If you've never run an anti-spyware program before, you'll be amazed at all the critters it finds bedding down in your PC. 15.6.3. RemovalLike a bad cold, malware is easy to catch, but difficult to get rid of. A variety of programs detect, remove, and protect against infections. Although some antivirus programs are slowly adding spyware removal to their inventories, most only protect you from viruses. Unless your virus program specifically says that it detects and removes spyware, you need two separate programs: one to remove viruses, and another to recognize and remove spyware. The key word here is recognize . When these programs scour your PC, they search for code that matches code in their databases. When they find a match, they either delete it or send it into "quarantine," leaving it powerless. But since the most recently released viruses and spyware don't yet appear in the latest databases, the programs can't detect them. To keep up, companies constantly update their databases, sometimes hourly. That's why running any antivirus or anti-spyware program requires you to download the latest database. Antivirus programs usually require a yearly subscription for access to their latest databases. Some programs keep themselves automatically updated, visiting the Internet and downloading what they need in the background. Others require you to connect to the Internet and download the latest "definitions" each time you run the program. But whether they call it a database or a definition, it's mandatory; without this new information, the program's no defense against the latest batch of villains . 15.6.3.1. Antivirus programsWindows XP doesn't include any antivirus program, but Microsoft offers a page that links to discount trial offers from a variety of software manufacturers including the four biggies: Symantec (www. symantec .com), McAfee (www. mcafee .com), Trend Micro (www.trendmicro.com), and Computer Associates (www.ca.com). The following page is an excellent first stop if you're running an unprotected PC. To download the trial versions, visit this Web page:
Several companies offer free antivirus software, letting you try a product without any strings attached. They're limited to personal use, which means you're not supposed to run them if you're working in an office. Their updates and definitions don't download as quickly as do the pay versions; and they offer no technical support. Some are given away in the hope you'll upgrade to the pay versions with their additional features. These are the three biggest antivirus freebies:
Note: Windows XP's Security Center nags you when you install an antivirus program that it doesn't recognize. If XP's Security Center doesn't recognize your's, stop the nagging screens by visiting the Security Center (Start  Control Panel Control Panel  Security Center) and then choose "Change the way Security Center alerts me." There, you can turn off the Virus Protection option, effectively stifling the alerts. Security Center) and then choose "Change the way Security Center alerts me." There, you can turn off the Virus Protection option, effectively stifling the alerts. |
| TROUBLESHOOTING MOMENT Removing Specific Viruses |
| If you recognize a certain virus on any PC, perhaps spotting a telltale file name or symptom, you may not need to buy a virus checker. Several sites offer free tools that specialize in the removal (rather than the detection) of common and particularly damaging viruses. Symantec offers free removal tools for nearly 100 common viruses:
You'll find similar downloadable tools at these sites:
Those three sites each require separate tools for the viruses you're able to identify on your own, but McAfee packs up 54 of its removal tools into one handy program called "Stinger." Stinger scans your hard drive, and identifies and removes the most common viruses and worms. Stinger is certainly no substitute for an up-to-date antivirus program that catches the latest week's virus arrivals. But at around 500 KB, it's a great addition to your USB drive. Before using any PC, insert your USB drive and run Stinger to let the program purge the PC of the most common viruses.
|
15.6.3.2. Removing spyware and adware
The first step in removing spyware and adware is to not get tricked into installing it. Lots of spyware tries to install itself automatically when you click a pop-up ad, like the ones shown in the top of Figure 15-10. As the software begins to install, it spills the beans midway through the fine print of the multipage End User Legal Agreement, shown in Figure 15-10, bottom. Most people miss this not-so-fine print as they race to click the I Accept button.
To avoid picking up unwanted software, follow these tips:
-
Install Service Pack 2 (see Section 15.4) and turn on Internet Explorer's pop-up blocker (Section 13.3).
-
Better yet, switch to Firefox, which doesn't support the type of programming exploited by many unwanted programs.
Figure 15-10. Top and Middle: Pop-up ads lure you by mimicking Windows XP's own messages or claiming to do something useful.
Bottom: When you install this "junk email blocking" software, more details emerge deep in the licensing agreement: the utility displays targeted ads and popups from both the company itself and third-parties. And get this part: "Spam Blocker Utility, from time to time, may work with email direct marketers, affiliates , and/or sponsors to offer users the opportunity to subscribe to various subscriptions to newsletters and information, whether by e-mail or otherwise ."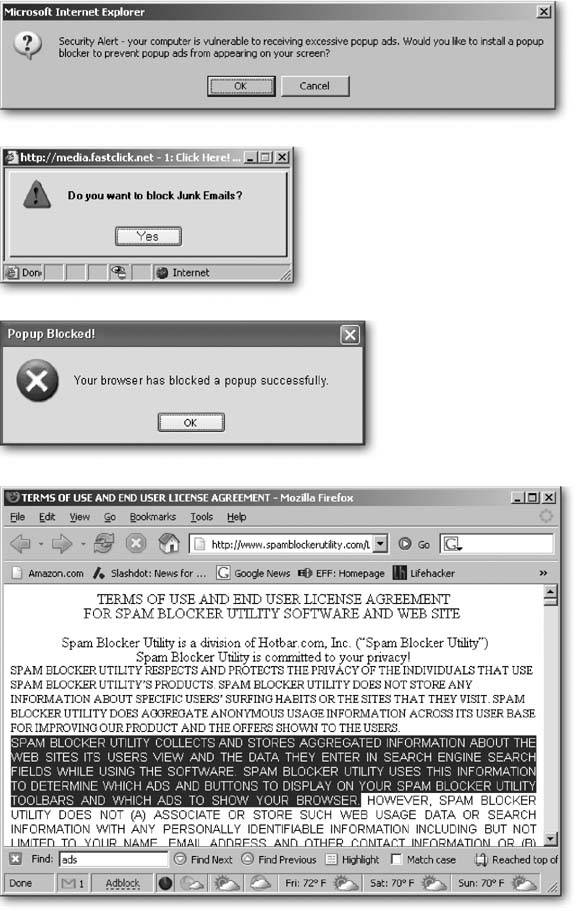
-
Don't click any pop-ups except the X in their upper right-hand corners. (Clicking the pop-up's button marked Close sends you to the company's Web site.) If you're barraged with pop-ups, don't try to close them individually. Instead, close them all in one swoop: right-click the group of Internet Explorer programs on your taskbar and then, from the shortcut menu, choose Close Group .
-
Read licensing agreements thoroughly before installing anything offered to you on the Internet.
If it's too late, and your PC's plagued with unwanted toolbars , ads, and other nuisances, several free programs can scan your PC and strip away any spyware or adware they find.
-
Ad-Aware SE (www.lavasoftusa.com/support/download/)
-
Spybot-S&D (www.safer-networking.org)
When those programs can't catch a particularly clingy piece of spywareor they won't even runfollow these steps to put Windows into troubleshooting mode, giving the spyware killers a better chance to wring the spyware out of your PC:
-
Download and install both pieces of anti-spyware software mentioned above .
Some spyware restricts Internet Explorer so it can't visit anti-spyware sites. If your copy of Internet Explorer's in similar bad shape, download and install Firefox (see Section 13.1.2). It's a much more difficult target for spyware programs.
-
Load each program, one at a time, updating its definitions and then closing it without performing any kind of scanning operation .
-
Disconnect from the Internet and restart Windows XP in Safe Mode .
Disconnect your PC from the Internet by unplugging your PC's phone or network cable, or unplugging its wireless adapter.
Safe Mode, a basic troubleshooting tool, starts Windows in a no-frills mode, bypassing all but the most basic drivers and not running your PC's normal "start up" softwarewhich often consists of spyware or adware. To enter Safe Mode, restart your PC (Start
 Turn Off Computer
Turn Off Computer  Restart), and then press F8 once or twice a second before Windows XP loads. When Windows XPs Boot Mode menu appears, select Safe Mode.
Restart), and then press F8 once or twice a second before Windows XP loads. When Windows XPs Boot Mode menu appears, select Safe Mode. -
Run Ad-Aware SE and remove any spyware it finds .
-
Run Spybot-S&D and remove any spyware it finds .
-
Restart your PC normally and reconnect to the Internet .
-
Visit Windows Update with Internet Explorer and install any "critical" patches .
Be sure to download and install any patches marked "Critical." If you've turned on Automatic Updates (see Section 15.3), you shouldn't find many, if any.
Tip: Microsoft entered the anti-spyware market, and it's currently giving away a copy of the program during its testing phase. Feel free to download it (www.microsoft.com/athome/security/spyware/software/default.mspx) and let it extricate any spyware the other two programs may have missed.