4.2 EMV(TM) data elements
4.2 EMV ¢ data elements
An EMV ¢ debit/credit payment application in the ICC consists of a set of data elements that can be accessed by the terminal after a successful selection of the application. A data element is the smallest information unit that can be identified by a name , a description of its logical content, and a format.
Data elements are mapped onto data objects, which are BER-TLV encoded, as defined in the ISO/IEC 8825 standard [9]. Each data object consists of three fields: a tag, a length, and a value. Section 3.4 explained that the BER-TLV encoding is appropriate when interoperability is a requirement.
When the value field of a data object consists of one single data element, it is called a primitive data object. When the value field of a data object recursively encapsulates one or more other data objects, it is called a constructed data object. Figure 4.2 shows the recursive representation of the value field of the constructed data objects.
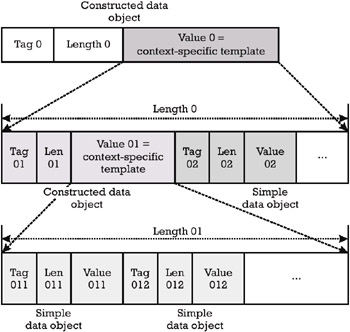
Figure 4.2: Recursive representation of constructed data objects.
The tag uniquely identifies a data object within the environment of an EMV ¢ application. Although the BER-TLV encoding rules specify that the tag can be represented on 1, 2, or more than 2 bytes, the tags currently used in EMV 2000 are represented on either 1 or 2 bytes. Different tags are assigned to primitive data objects and constructed data objects, with a specific meaning in the application environment. The tag field encodes a class, a type, and a number.
-
The first byte of the tag specifies the following:
-
The class, using the bits b8 and b7 (details about the tag's class are presented in Book 3 [3], Annex B1.1):
-
00 ” universal class ;
-
01 ” application class , including templates defined in EMV 2000 and ISO 7816;
-
10 ” context specific class , including primitive data objects defined in EMV 2000 and specific data objects defined by an EMV ¢ payment system operator;
-
11 ” private class , containing primitive and constructed data objects at the discretion of the issuer of an EMV ¢ application in the ICC.
-
-
The type, using the bit b6:
-
0 ”primitive data object;
-
1 ”constructed data object.
-
-
The tag number, using the bits b5, b4, b3, b2, and b1. These five bits can encode a tag number in the range of 0 to 30. When the value of these five bits is 31 (all bits on 1) the tag number is continued in the second byte of the tag, in the range of 31 to 127.
-
-
The second byte of the tag encodes tag numbers that are greater than or equal to 31 (all bits 0) or less than or equal to 127 (01111111). Bit 8 of the second byte is 0 in case the tag number is less than or equal to 127, and is 1 in case a third byte is needed for encoding a tag number greater than or equal to 128.
The length field of a BER-TLV encoded data object specifies the number of bytes needed to represent the value field of the data object.
-
When the length of the value field is less than or equal to 127, the length field is encoded on one single byte with b8 = 0.
-
When the length of the value field is greater than 128, b8 = 1inthe first byte, while the remaining bits b7 b1 in the first byte encode the number of bytes needed for the representation of the length. A length in the range of 128 to 255 needs a second byte, while a length in the range of 256 to 65,535 needs also a third byte.
The data elements accepted by the EMV 2000 specification are divided in two classes:
-
Data elements that may be used for application selection, as presented in Book 1 [1], Annex B, Table B-1;
-
Data elements that may be used for EMV ¢ debit/credit financial transaction interchange, as presented in Book 3 [3], Annex A, Table A-1.
The complete specification of an EMV ¢ data element in any of the aforementioned tables contains the following items:
-
Name: This specifies a unique identifier attached to a data element in the EMV 2000 specifications (e.g., Application Cryptogram).
-
Description: This specifies a brief description of the data element in the context of the EMV 2000 specifications (e.g., "Cryptogram returned by the ICC in the response of the GENERATE AC command").
-
Format: This specifies the encoding rule of the value field. Several encoding rules can be mentioned:
-
n nbr: numeric type on a number of digits equal to nbr ;
-
n 6 YYMMDD: numeric type with a date content (year, month, day);
-
an nbr: alphanumeric type on a number of characters equal to nbr ;
-
b: binary value. In the case of the application cryptogram, the format is binary.
-
-
Template: A data object, primitive or constructed, can be further encapsulated in a context-specific template. Thus, this field describes whether or not the current data element is encapsulated in a certain template.
-
Source: This specifies the device (namely, the ICC, the terminal, or the IH) that is concerned with the current data element (e.g., the ICC stores the application cryptogram).
-
Tag: This uniquely identifies the data element in the EMV ¢ environment.
-
Length: This determines the length of the value field of a data object.
EMV ¢ data elements either mapped to primitive or constructed BER-TLV encoded data objects can be grouped in record templates. One or several record templates that are semantically related can be further grouped in an AEF (see Section 3.4.2). The mapping of EMV ¢ data objects in record templates and their collection in AEFs are left at the discretion of the issuer.
EAN: 2147483647
Pages: 131