Best Practices for Securing L2TP
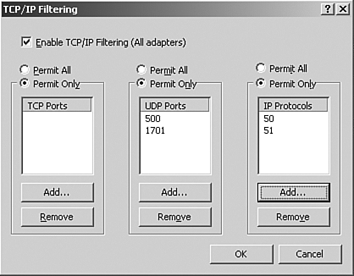
| It is important to note that L2TP is, in and of itself, a tunneling protocol. By itself it offers no data encryption. L2TP is traditionally used with IPSec to add encryption to this IP tunnel. L2TP offers a feature that used to be unavailable with PPTP. This feature is the ability to place the VPN server behind a Network Address Translation device. This is to say that the L2TP VPN device does not require a routable IP address to be usable from the Internet. It merely requires that the appropriate UDP port be mapped to the firewall and the necessary protocols be passed to the L2TP server. These ports, configured in the Advanced TCP/IP Settings for the system network adapter shown in Figure 18.1, are specified: Figure 18.1. Port filtering for L2TP.
To secure the L2TP server itself, it is useful to treat the VPN server like a firewall. This is to say that all unessential services should be disabled. The POSIX subsystem should be disabled and the OS2 subsystem should be disabled as well. File securities should be audited to ensure that no users have access to any of the files. The High Security Workstation template from the Security Analysis and Configuration Tool is a great starting point. To ensure that traffic passes through the VPN device it should be configured with at least two network cards that should be addressed on different networks. One NIC would connect to the production network and the other would normally connect to the DMZ network. This enables you to configure the two interfaces differently. TCP/IP filtering should be enabled on the DMZ interface of the L2TP device. Only the required ports and protocols should be accepted by the server. This greatly minimizes the attack profile of the server. Because this server is a gateway into the network, it should be treated as such and locked down as far as possible. Using L2TP in Parallel with a FirewallIt is a fairly common practice to install a VPN device in parallel with the firewall. This is to say that both the firewall and the VPN device have an interface that is connected directly to the Internet. Remote VPN users connect directly to the VPN device and their traffic does not pass through the firewall. This configuration requires that the VPN device itself be well hardened and secured. Careful monitoring of the device will also help to ensure that it is not compromised. This configuration is often used in cases where the firewall is not able to correctly pass L2TP traffic to the VPN device. One advantage of the VPN in parallel with the firewall is that it offloads traffic from the firewall, resulting in a smaller load on the firewall. Configuration of the VPN is also simpler as there is no configuration of the firewall necessary. This configuration can also reduce the number of licenses needed for the firewall because each VPN connection doesn't use up an outgoing session license. If an L2TP device is going to be run in parallel with the firewall it is preferable for the device to be a dedicated VPN device with a dedicated operating system. If the L2TP device runs a full operating system, such as Windows Server 2003 RRAS, it is recommended you perform the following tasks :
Running the L2TP Device in Parallel To run the L2TP device in parallel with the firewall, it will be necessary to have at least two Network Interface Cards in the device. The port filtering should only be placed on the external interface. Using L2TP in Series with a FirewallIf the firewall supports it, there are numerous security advantages to placing the L2TP VPN device in series with a firewall. The concept of layering security is a popular one and the philosophy works well with VPNs. In addition to being able to secure the local VPN device as was described in the previous section, "L2TP in Parallel with Firewall," having the firewall in series and ahead of the VPN device enables you to filter traffic at the firewall as well. In this way, before the VPN device could be attacked , the firewall would first have to be compromised. Anything that increases the time necessary to compromise a system increases the overall security of an environment. Most Application Layer firewalls, Proxy Level firewalls, and Port Filtering firewalls will work very well with L2TP. L2TP can be passed through a firewall as well as be translated to an Internet host via Network Address Translation. This allows smaller companies with a single IP address to map L2TP services through a firewall back to an internal VPN device. L2TP Client RequirementsTo make an L2TP/IPSec virtual private network (VPN) connection, you must first have an Internet connection. If a system tries to make a VPN connection before it has an Internet connection, it will likely experience a noticeable delay, perhaps 60 seconds, and then receive an error message stating that there was no response or that something is wrong with the modem or other communication device. To use L2TP/IPSec connections, it is useful to understand how an L2TP/IPSec connection works. When a system starts the connection, an initial L2TP packet is sent to the server. This packet is requesting a connection. This packet causes the IPSec layer on the client computer to negotiate with the VPN device to set up an IPSec protected session. This protected session is also called a security association or simply an SA. Based on network speed and latency, the IPSec negotiations can take from a few seconds to several minutes. When an SA has been established, the L2TP session starts. When this session starts, the user will be prompted for a username and password. After the VPN device accepts the username and password, the session setup is completed. Some common issues with the use of L2TP/IPSec connections include:
Many small networks use a router or firewall with NAT functionality to share a single routable address among all the computers on the network. The original version of IPSec drops a connection that goes through a NAT because it detects the NAT's address-mapping as packet tampering. Home networks also frequently use an NAT. This blocks the use of L2TP/IPSec unless the client and VPN gateway both support the NAT Transparency standard for IPSec. NAT transparency is supported by Windows Server 2003. Leveraging Remote Access PoliciesFor a common policy, you must choose the following:
For a custom policy, you must configure the following:
|
EAN: 2147483647
Pages: 325
- Chapter VIII Personalization Systems and Their Deployment as Web Site Interface Design Decisions
- Chapter X Converting Browsers to Buyers: Key Considerations in Designing Business-to-Consumer Web Sites
- Chapter XII Web Design and E-Commerce
- Chapter XIV Product Catalog and Shopping Cart Effective Design
- Chapter XVI Turning Web Surfers into Loyal Customers: Cognitive Lock-In Through Interface Design and Web Site Usability