Using Cross-Forest Trusts Effectively
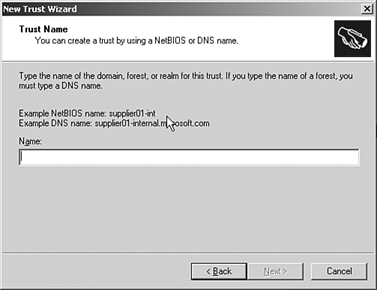
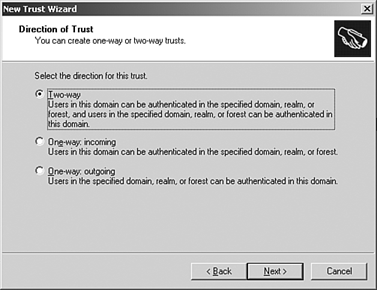
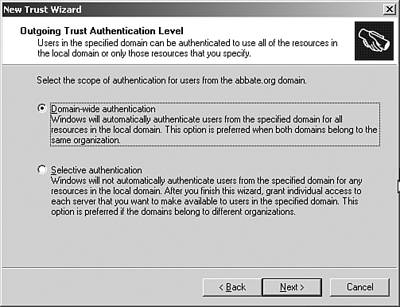
| Windows 2003 introduced two new concepts in the use of forests; cross-forest authorization and cross-forest authentication. Cross-forest authentication allows users secure access to resources in another forest. This feature enables users to securely access resources in other forests, using either NTLM or Kerberos. This allows access without sacrificing single sign-on or the benefits of having a single user ID and password maintained in the user's home forest. Cross-forest authorization allows you to select users and groups from trusted forests for use in local groups or ACLs. This is a similar concept to domain trusts that were used in NT 4.0 domains. This feature retains the forest's role as a security partition while still allowing trust between forests. It allows the trusting forest to enforce restrictions on what security identifiers (SIDs) will be accepted when users from trusted forests attempt to access protected resources. To create a cross forest trust, perform the following steps:
Account/Resource ForestsWith the ability to now support trusts between forests, many previously unavailable Active Directory architectures become available. Forests can be built to support a single Active Directoryaware application. Schema changes to that application would be independent of the schema supporting the account forest. Resource forests could be brought up to allow developers or QA groups to work in environments that look identical to production without the fear of changes to the schema affecting production users. Company AcquisitionBack in the days of NT 4.0 domains, company mergers or acquisitions were fairly easy to handle from a domain point of view. With the simple creation of a trust, resources could be ACLed with user information from the other company. When Windows 2000 and Active Directory came along, this scenario became a lot more challenging. Now with Windows 2003 and the support for cross-forest trusts, the fairly simple days of granting access to a resource via a trust have returned. Although a cross-forest trust should not be considered a long-term solution for company acquisition or mergers, it is an excellent tool to get immediate access to resources. Companies in this situation should look back to their original Active Directory design and make determinations as to how best to integrate the new resources; either as a new domain in the forest or collapsing them into a single domain potentially as an OU. If the requirements of the partner are sufficient to warrant a separate forest, the trust could be maintained long term . |
EAN: 2147483647
Pages: 325