Understanding Outlook s Security
Understanding Outlook's SecurityOne of Outlook's strengths is its programmability. Outlook supports VBA, enabling you to use procedures to automate many mundane tasks . When you need more than VBA provides, you can install COM add-ins to provide features that Microsoft didn't build into Outlook.
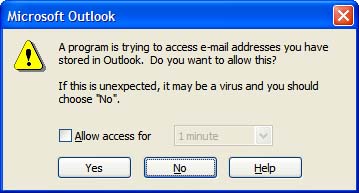
This programmability comes with a high price tag: Anything you can do, virus writers can do too, and they usually have destruction on their minds, not helping Outlook users work smarter . Outlook 2003 provides a good mix of security and usability. Microsoft assumes that you know not to install add-ins or use VBA code that comes from questionable sources, so it allowed Outlook to trust COM add-ins and project code. That means code now runs without triggering annoying dialogs, such as the one shown in Figure 8.1. Figure 8.1. The object model security dialog warns you when a program is trying to send mail on your behalf . The responsibility to ensure that unsafe add-ins aren't installed now falls on your shoulders, not Microsoft's. Plenty of safeguards are still built in, but in the end, keeping your system secure and free from viruses, trojan horses, and worms is your responsibility, and that's how it should be.
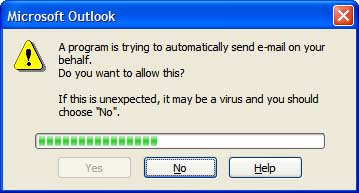
Outlook's first line of defense is Outlook Object Model (OOM) security. If you're using a COM add-in that's not updated for Outlook 2003, you'll notice the most visible effect of the OOM security: A warning dialog alerts you that something is trying to access email addresses or send mail on your behalf (see Figure 8.2). Figure 8.2. A second warning dialog displays as new messages are created. After the green bar completes, you need to choose Yes or N o to send the message. As you can see from this figure, the dialog asks whether you want to allow it to send email. In most cases, you'll want to choose Yes and allow it access for 1 to 10 minutes. However, if you're not sure what's causing the warning dialog to appear, play it safe and choose N o. Outlook Object Model SecurityOutlook's object model security protects you by preventing untrusted code from accessing your messages and address lists. When a program attempts to access your Outlook data, you'll see one or both of the dialogs shown in the previous section in Figures 8.1 and 8.2. However, published Outlook forms, Visual Basic for Applications code, and properly written Outlook COM add-ins won't trigger the security prompts for standalone users. Exchange administrators will still be able to manage Outlook security through the Outlook Security Settings folder and form.
Security in the Reading PaneThe Reading Pane is secure because it doesn't support active content. All potentially dangerous attachments are blocked (including scripts) and Outlook no longer allows iframes to display in email. Open messages offer the same level of protection that you have with the Reading Pane, so if you like using the Reading Pane, go ahead and use it. Many HTML elements are disabled in email, including forms, submissions, and other active content. Open the message and choose V iew, View in Internet Z one if you need to make the content. The message is displayed using the Internet Zone settings normally used for browsing the Internet. Never lower the security settings using the T ools, O ptions, Security tab ”it's not safe to do so. If the source is trustworthy, use the V iew, View in Internet Z one menu selection when you need to reduce the security level on your email. Don't view messages from unknown sources in the Internet zone. Understanding Web BeaconsAlso known as Web bugs , Web beacons are images with a URL that includes a code to identify the email address it was sent to. Every time the image loads, the sender is informed of the email address that viewed the message. This lets the sender know that the email address is active and ripe for future mailings . Although Web beacons are often used by spammers to verify valid email addresses, they're also used by legitimate mailers, including many newsletters and advertisers, to learn who reads the messages and which layouts or ad campaigns result in the highest levels of readership .
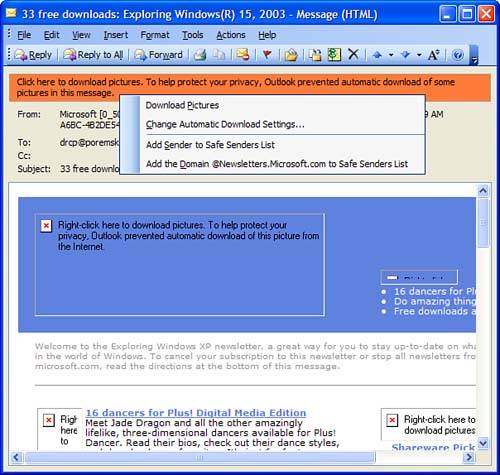
You can selectively show the images that are blocked by Outlook or disable Web beacon blocking for all messages from specific domains or disable it for all email you receive. Click on the InfoBar or right-click on any image placeholder in the message and select Download Pictures to display the images in an individual message (see Figure 8.3). Choose C hange Automatic Download Settings to change the global options. Figure 8.3. Messages containing external images show only the picture placeholders and text informing you why the images are missing. You have four methods you can use to change how Outlook uses external content:
Although I recommend against disabling the feature completely, trusting senders or domains is an acceptable option.
In most cases, using the Safe Senders and Safe Recipients lists is preferable to changing your Internet Zone settings. Doing so gives you better security when browsing the sender's Internet site, while allowing their images and external content to display in your email. One of the Safe Sender options is Also Trust E-mail from My C ontacts. I recommend against choosing this option for several reasons:
Clicking once per message takes a second or I can add individuals or their domains to the Safe Senders list as needed.
Outlook, Outlook Express, and Internet Explorer share the security zone settings. That means when you add a domain to the trusted zone, browsing the domain's Internet site is also in the trusted zone. Use this option only when you already trust the Internet site because adding the domain to the Safe Senders list provides more protection with the least amount of hassle. Finally, if you really don't like Outlook blocking your external content on any of your messages, you can disable the feature completely. This is not recommended; it's safer to trust senders. After you enable external content on a message using the InfoBar, it remains enabled on that message and will download each time you view the message because external content isn't cached locally.
|
EAN: 2147483647
Pages: 228