10.1 The Purpose of Cryptography
| < Day Day Up > |
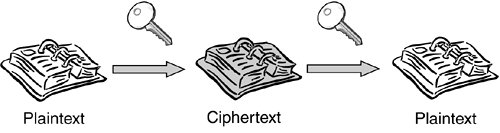
| The purpose of cryptography is to protect data transmitted in the likely presence of an adversary. As shown in Figure 10.1, a cryptographic transformation of data is a procedure by which plaintext data is disguised, or encrypted , resulting in an altered text, called ciphertext , that does not reveal the original input. The ciphertext can be reverse-transformed by a designated recipient so that the original plaintext can be recovered. Figure 10.1. The Process of Encryption and Decryption Cryptography plays an essential role in
Keeping secrets is a long-standing tradition in politics, the military, and commerce. The invention of public-key cryptography in the 1970s has enabled electronic commerce to blossom in systems based on public networks, such as the Internet. There are two primary approaches to cryptography (see Figure 10.2). In secret-key cryptography, the key used to decrypt the ciphertext is the same as the key that was used to encrypt the original plaintext. In public-key cryptography, the key used to decrypt the ciphertext is different from but related to the key that was used to encrypt the original plaintext. Figure 10.2. Secret-Key and Public-Key Encryption Each approach has its strengths and weaknesses. Many of the cryptographic services enterprise applications need use both approaches. However, most application developers will not be aware of the underlying machinery that is deployed. For example, most users of SSL-enabled Web browsers are not aware that both public- and secret-key cryptography are essential parts of the SSL protocol. Naively, we can think about cryptography primarily as a means for keeping and exchanging secrets. This is the confidentiality property that cryptography affords us. However, other essential cryptographic services are provided. When exchanging a message, whether encrypted or not, we often want to verify its integrity. Someone, particularly in public networks, may have modified the message. Data-integrity verification includes authenticating the origin of the message. Was the message from the source that we think sent the message? Once we accept that the message is from an authenticated entity and was not modified after being created, we also want to consider whether the sender can repudiate ”deny sending ”the message by claiming that someone stole the cryptographic key used to authenticate the message. Therefore, nonrepudiation is an essential feature of cryptographic systems e-businesses use. |
| < Day Day Up > |
EAN: 2147483647
Pages: 164