Single Address Space Solutions
| When segmenting the Layer 3 portion of the network, several levels of separation can be achieved. The most basic one is simply restricting the prefixes that can be reached by a group of hosts. You can achieve this over a single address space with access control lists (ACLs). As you may already be thinking, the scenarios in which this is viable are few because of the limited flexibility of ACL rules (which are defined based on IP addresses). In general, you can use ACLs for scenarios requiring connectivity of many hosts to a centralized resource. Guests who should be restricted to only access the Internet are an example of a group that could be isolated by means of ACLs. Creating ACLs for groups that have a need for peer-to-peer traffic is impractical because of the endless number of combinations and permutations that must be taken into account to write these ACLs. Note Future technologies such as role-based ACLs may allow the creation of ACLs based on user role rather than IP address. This will simplify ACL rules dramatically, allowing the scalable use of ACLs for control of peer-to-peer traffic. For the time being, we limit our discussion to the currently available technologies. Remember, however, that with the right enhancements, a single address space solution based on ACLs could prove powerful. The main advantage of continuing to use a single address space is that the routing and switching environment in the enterprise remains unaltered. By distributing ACLs around the Layer 3 edge of the network (usually the distribution switches), it is possible to restrict the list of prefixes that can be reached by certain hosts. This is a rudimentary mechanism for creating separate user groups and is illustrated in Figure 6-5. Figure 6-5. Distributed ACL-Based Reachability Control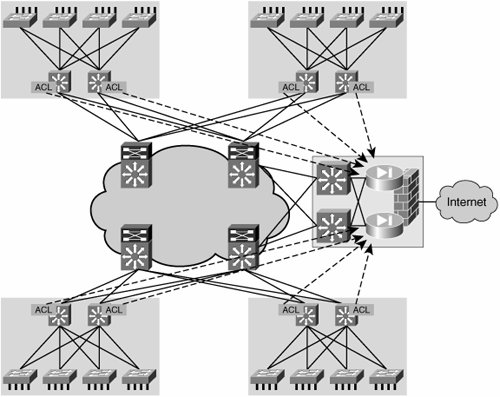 The use of ACLs can restrict access to a resource, but it cannot determine which route will be followed to access this resource. Policy-based routing (PBR) enables you to steer traffic over a specific route. This capability is of interest when different groups accessing the same services must be subject to different types of control before accessing the shared services. For instance, in an environment where guests are provided with Internet access, both visitors and employees use the same Internet gateway, but guest traffic must traverse accounting and monitoring devices before reaching the Internet gateway. PBR could be used to divert the guest traffic to the control devices, while employee traffic continues to flow freely to the Internet access gateway. A combination of ACLs and PBR might allow the creation of different user groups. However, these mechanisms require intensive configuration and are extremely static (and therefore hard to scale and maintain). In Example 6-12, we provide the ACL and PBR configuration necessary to provide guest Internet access as described previously. Instead of assigning the SVIs at the distribution to VRFs, ACLs are applied to these interfaces, thus acting on any traffic entering the Layer 3 portion of the network and enforcing any reachability restrictions or privileges that the user group may have. Example 6-12. Guest Internet Access Based on ACLs
The access list in Example 6-12 achieves the following:
Note The ACL in Example 6-12 is generic enough to be seamlessly applied to all distribution routers. Note that this is possible only because of the simplicity of the guest Internet access requirement. The ACL must be applied to the first-hop SVI in every guest VLAN at the distribution. The use of routed ACLs is preferred over VLAN ACLs because they are applied unidirectionally and we are not concerned about restricting return traffic. The configuration in Example 6-13 applies the ACL to the corresponding SVI. Example 6-13. Applying ACLs to a Group
As discussed previously, should guest traffic need to be subject to special controls before going to the Internet, ACLs are not enough. PBR can complement the solution by rerouting guest traffic to the control devices right before it goes to the Internet gateway. The policy defined in Example 6-14, when applied inbound at the penultimate hop before reaching the Internet gateway, will allow guest traffic to use a different path to reach the Internet. Example 6-14. Path Differentiation with PBR
These statements simply match any traffic coming from one of the guest subnets (TO-BBSM ACL) and set the next hop for this traffic to the address of the policy-enforcement device. It is important to keep in mind that the PBR policy is applied only to inbound traffic (from the perspective of the device). |
EAN: 2147483647
Pages: 128