Chapter 3: Managing Security and Privacy in the 2007 Office System
The security of your computer and the privacy of the information you store and transmit using it are of vital concern. How many news stories have you read about computers under attack? Any number of worms, viruses, malware, and the like can do harm to your computer and the data on it. How many stories have you heard about the mistaken disclosure of personal data-or about data not so mistakenly stolen-from large data stores in which confidential and private information of all sorts is stored?
Personal computers, software, and information technology in general have made communications between people much faster, made many workers more productive, and opened opportunities for commerce and leisure in lots of ways. But to offset benefits such as these are problems like spam, identity theft, and information leaks. Computer users and administrators who manage networks and computer systems are more concerned than ever about security and privacy. You may be familiar, for example, with the need to control when a macro can run. Macros are helpful because you can use them to automate repetitive and common tasks, but macros can pose a security risk because the program code they contain can rapidly run through a series of commands and possibly introduce or spread a virus on your computer.
In this chapter, we’ll take a look at some of the security and privacy features in the 2007 Microsoft Office release. Many of these features apply to any and all of the 2007 Office release programs that you work with. Others are more specific and relate to one or just a few of the programs. To start, we’ll take a look at the Trust Center, which you use to specify how to manage the types of programs and situations that can make your computer and your information more vulnerable.
Working in the Trust Center
In the 2007 Office release, you use the Trust Center to manage security and privacy settings for Microsoft Office applications. The Trust Center provides options related to the specific application you’re using-settings for how you want to control connections to external data in Microsoft Office Excel 2007 spreadsheets, for example-as well as settings that apply to how the 2007 Office system in general handles certain security and privacy concerns.
To open the Trust Center in the 2007 Office release programs Word, Excel, PowerPoint, or Access, follow these steps:
-
Click the Microsoft Office Button, and then click Options. (Options will be preceded by the name of the particular program; for example, Access Options.)
-
Click Trust Center.
-
To update and set options in the Trust Center, click Trust Center Settings.
To open the Trust Center in Microsoft Visio, Microsoft Outlook, Microsoft Publisher, or Microsoft InfoPath, follow these steps:
-
On the Tools menu, click Trust Center.
-
Click the security category that you want to work with.
Figure 3–1 shows the Trust Center window for Word 2007. It provides links to privacy options, general security settings for Microsoft Windows, and the Trust Center Settings button.
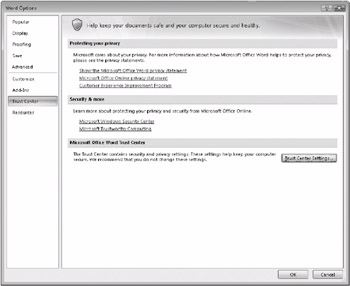
Figure 3–1: The Trust Center provides links to privacy settings and several pages that you use to manage security settings for macros, add-ins, and other potential security threats.
For more information about privacy options, see “Setting Your Privacy Options” later on page 58.
Click Trust Center Settings to display the pages that you use to manage the specific security settings for macros, privacy options, and other security areas. The Macro Settings page for Word 2007 is shown in Figure 3–2. As you can see, the Trust Center is organized into a number of categories-Add-Ins, ActiveX Settings, Privacy Options, and so on. Each category is identified on the left side of the window. Click a label to display the settings and options for that category. The labels and options in other 2007 Office release applications are the same or similar in most cases. We’ll look in more detail at a number of the options in these categories later in this section and in the sections ahead.
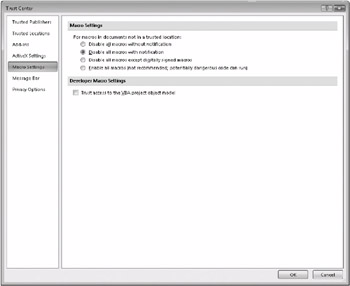
Figure 3–2: The Trust Center includes pages with specific security options for macros, add-ins, ActiveX controls, and other settings.
| Note | In Excel 2007, the Trust Center includes an area named External Content. You use this section to specify options for managing connections to external data (a link to a Microsoft Access database or a Microsoft SQL Server database, for example) that are included in an Excel workbook. This area of the Excel Trust Center also lets you specify security settings for links to other Excel workbooks. Three choices are presented in each case-trust all connections or links (which Microsoft doesn’t recommend), receive a notification (a prompt) when you’re working with a connection or link (the default choice), or to disable all connections or links, which would probably affect the experience of many users who rely on these features. |
Digital Signatures and Trusted Publishers
Many users of the Microsoft Office system rely on macros that they (or possibly a coworker) create to help them perform and complete routine tasks more quickly. Similarly, an add-in can supplement the features and capabilities of a Microsoft Office application. These types of programs, however, can also do a lot of damage to your computer and your data if the program code they contain is designed for malicious purposes. You don’t want to run these types of programs without knowing who developed and provided them to you in the first place.
For more information about Trust Center settings for macros and add-ins, see “Setting Security Options for Macros and Add-Ins” on page 54.
Security options for macros and add-ins are related to digital signatures and trusted publishers. A digital signature is used to authenticate documents, e-mail messages, and macros through cryptography. Digital signatures help assure you that whoever signed the program (the publisher) is who they claim to be and that the content included in the program has not been modified or tampered with since it was digitally signed. A digital signature essentially proves the origin of the signed goods.
A publisher is a software developer (Microsoft, an independent software vendor, or someone in your company or department) who has created a macro, add-in, or other type of application extension that you and others will use with Microsoft Office applications. The Trust Center lets you compile a list of publishers that you trust-those publishers whose digital signatures are valid and current and whose code you allow to run.
Here’s the information that a publisher has to provide to the security apparatus of Microsoft Office to be considered trustworthy:
-
The program (a code project like a macro or an add-in) must include the digital signature of the developer.
-
The signature must be valid, current, and issued by a reputable certificate authority.
-
The publisher must be included on your list of trusted publishers.
| Note | A certificate authority is a commercial entity that issues digital certificates. They know which publishers have been assigned to specific certificates; they sign certificates to attest to their validity; and they keep track of which certificates are current and which have expired. Two of the better known certificate authorities are Certisign and VeriSign. |
If a macro or an add-in is digitally signed by one of your trusted publishers in the manner that the Trust Center requires, all goes according to plan. You can run the code without further intervention because you know that it comes from an entity that you trust. But if the Trust Center doesn’t detect that all these criteria have been met when you begin to run an add-in or a macro, the program is considered to be potentially unsafe, and you’ll see an alert in the Message Bar that notifies you of this fact, as shown in Figure 3–3.
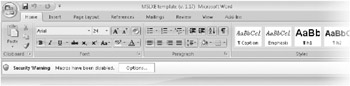
Figure 3–3: You’re alerted to a potentially unsafe macro or add-in in the Message Bar.
When you see such an alert, click Options on the Message Bar to display the dialog box shown in Figure 3–4. In the dialog box, you can see an explanation of why the macro was blocked. When a security dialog box such as the one shown in Figure 3–4 appears, you can leave the macro disabled, enable the macro, or choose to trust the publisher by clicking Trust All Documents From This Publisher. You should enable the macro only if you are sure that it comes from a source that you trust. The option to trust the publisher appears only if the digital signature is valid. Clicking this option means that all software that comes from this publisher will be trusted from this point on.
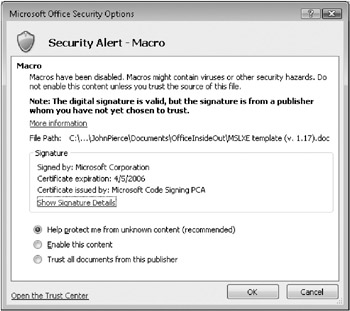
Figure 3–4: The security dialog box provides an option to add a publisher to your trusted publisher’s list.
| Note | If you receive a warning indicating that no digital signature is present or that the signature is invalid, you should not enable the content or trust the publisher unless you are sure that the code comes from a trustworthy source. For example, if the document that contains the macro was sent to you in e-mail, be sure you know who the sender is and maybe even check that they sent the message. If not, contact the source of the document for more information. |
If you aren’t sure which option to choose, you can look at the details of the signature and the certificate that was used to create it to see whether there are any potential problems. Click Show Signature Details in the Security Options dialog box, and you’ll see the Digital Signature Details dialog box, shown in Figure 3–5. A valid digital signature is identified by a message at the top of the dialog box, where the digital signature is identified as okay. You should also note the timestamp details in the Countersignatures frame. These details indicate that the certificate authority-in this example, VeriSign-has verified and approved the digital signature. The date for the timestamp (June 24, 2005, in this example) should be a date that falls within the valid date range for the certificate. To see the date range for the certificate, click View Certificate. The publisher should also be a trusted publisher. If the publisher is not trusted by default, you must explicitly trust it. If you don’t, the content signed by that publisher does not pass the security checks.
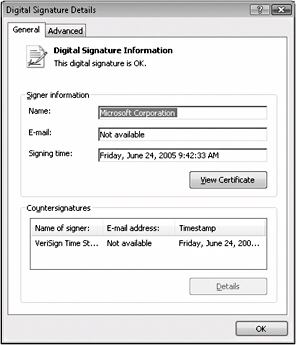
Figure 3–5: Review the details of a digital signature in the Digital Signature Details dialog box.
A digital signature that presents problems will be identified with a red X. The red X can appear for the following reasons:
-
The digital signature is invalid. For example, the content has been altered since it was signed.
-
This digital signature has expired.
-
The certificate associated with the digital signature was not issued by a certificate authority.
-
The publisher is not trusted.
When there is a problem with a digital signature, you should contact the source of the signed content or the administrator or department that is responsible for your organization’s computer security. If you think that the macro or other program is trustworthy, you can save the document to a trusted location. (You’ll learn more about working with trusted locations later in the chapter.) Documents that are stored in a trusted location-like the code that comes from a trusted publisher-are allowed to run without being checked by the Trust Center.
External content-content from the outside-is any content that is linked from the Internet or an intranet to an Excel workbook or a PowerPoint presentation. Scam artists can use external content to steal your personal information or to run malicious code on your computer without your knowledge or consent. To help protect your security and privacy, the 2007 Office system blocks external content such as images, linked media, hyperlinks, and data connections in Excel workbooks and PowerPoint presentations. If your workbook or presentation contains external content, when you try to open the file the Message Bar notifies you that the data connection has been disabled.. You will not be able to view or edit the content in your workbook or presentation. If you click Options on the Message Bar, a security dialog box appears, giving you the option to enable the external content. You should only unblock the content if you are sure that it is from a trustworthy source.
Using Trusted Locations
Settings in the Trust Center let you specify to what degree you will trust a file that contains code in a macro, an add-in, or another type of application extension. A trusted location, as mentioned earlier, is a folder or document location that Microsoft Office applications such as Word, Excel, PowerPoint, Access, and Visio use to trust documents, allowing the documents to open and run code that they include without notifying you. Figure 3–6 shows the Trusted Locations page of the Trust Center in Excel. You can see that several trusted locations are already defined. These refer to default locations that Microsoft Office creates for storing templates and files that run when you start an application.
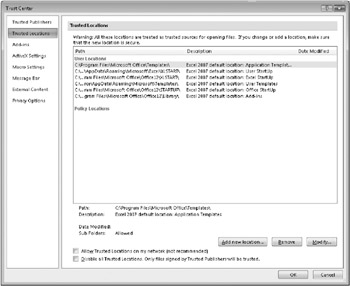
Figure 3–6: Documents listed under Trusted Locations run any code they contain without notification.
Adding a trusted location to the list that the 2007 Office release provides is a decision you should consider carefully, especially if you’re thinking of setting up a remote location, such as a server share or a Microsoft Windows SharePoint Services document library or slide library as a trusted location. Notice, for example, that the option Allow Trusted Locations On My Network is not selected by default and is not recommended. You need to be thoughtful because the code included in any document that is stored in a trusted location will run without challenge by Microsoft Office. (Administrators can restrict which locations can be trusted on client computers and what types of locations can be added, so you might not be able to designate every location you want as a trusted location.) Any location that you trust needs to be managed with restricted access so that only those people who are authorized to publish documents and code can use the location.
Trusting all documents that are stored in a particular folder might seem risky, but having the ability to create a single trusted location for all the files you want to work with on a specific project, for example, or simply files that you work with regularly can provide better security. For one thing, it lets you keep security settings that apply to documents not stored in a trusted location at a more restrictive level. In other words, you’re not tempted to use less restrictive security settings more widely. Documents stored in a trusted location are trusted for macro code (written in Visual Basic for Applications) and can also update data from remote sources automatically. These documents can initialize ActiveX controls, use add-ins, and so on. Once documents are tucked safely away in a trusted location, they run without displaying security prompts.
| Note | Certain folders that are considered high risk, such as the Outlook cache for attachments, the Temp folder, and others in which documents are sometimes stored temporarily, can-not be used as a trusted location. |
The steps to add, modify, or remove a trusted location are straightforward in themselves. To create a trusted location, click Add New Location (shown in Figure 3–6), and then fill in the dialog box shown in Figure 3–7. You need to specify the path to the location and select a couple of other options. To modify a location (for example, to specify that subfolders of a location can be trusted along with the parent folder), click Modify. Click Remove to delete a trusted location.
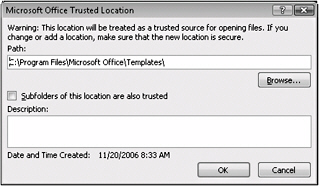
Figure 3–7: You can use this dialog box to add a trusted location or to modify the settings for one that is already set up.
Microsoft Update is a service that delivers updated files and downloads for Windows, Microsoft Office, and other Microsoft programs. Updates often address security vulnerabilities or update features that can help keep your computer secure. In Windows Control Panel, you can choose options for installing updates from Microsoft Update (listed as Automatic Updates). You can choose to install updates automatically or use one of the options that let you decide when to download and install the updates yourself. Of course, you can also choose not to get updates, but that choice means you might miss a critical security patch. (To change your Automatic Updates settings, you must be logged on to Windows with an administrator account.) You can also periodically check for updates for a 2007 Office release program. In Access, Excel, PowerPoint, or Word, click the Microsoft Office Button, and then click Options. Click Resources, and then click Get Updates. If you’re working in InfoPath, Microsoft OneNote, Outlook, Publisher, Microsoft Project, SharePoint Designer, or Visio, on the Help menu, click Check For Updates. You can then follow the directions on the Microsoft Update site.
Setting Security Options for Macros and Add-Ins
If you’ve worked with security settings in Microsoft Office 2003 (using the Security dialog box), you’re probably familiar with the settings Very High, High, Medium, and Low. These settings control when macros can run in an Office 2003 application. The Medium setting, for example, lets you choose which macros to run. The High setting allows you to run only those macros that come from trusted sources.
Like the Trust Center in the 2007 Office release, the Office 2003 Security dialog box lets you see your list of trusted publishers. This area of the dialog box includes an option that lets you trust all the add-ins and templates that are installed on your computer.
The Trust Center in the 2007 Office release has replaced these settings with more descriptive ones. In the Trust Center, you can make specific designations for how to handle add-ins, for example, as well as macro settings. As a summary of these settings, and in the event that you want to select security settings to match those you used in Office 2003, Table 3–1 compares the security settings in Office 2003 with those for macros and add-ins in the 2007 Office release. For Office 2003, the table lists the level from the Security dialog box and indicates whether the option to trust all add-ins and templates was selected or not. For the 2007 Office release, the table lists which setting to select in the Trust Center (on either the Macro Settings or the Add-Ins page) and whether you need to select an option regarding trusted locations, which appears on the Trusted Locations page in the Trust Center.
| Microsoft Office 2003 | 2007 Office System | |
|---|---|---|
| Level | Trust all installed add-ins and templates? | |
| Very High | Yes | Macro Setting: Disable all macros without notification |
| Very High | No | Macro Setting: Disable all macros without notification Add-Ins Setting: Disable all application add-ins |
| High | Yes | Macro Setting: Disable all macros with notification |
| High | No | Macro Setting: Disable all macros with notification Add-Ins Setting: Require application add-ins to be signed by trusted publisher Disable notification for unsigned add-ins (code will remain disabled) Trusted Locations: Disable all trusted locations; only files signed by trusted publishers will be trusted |
| Medium | Yes | The default settings in the 2007 Office system match this Macro Setting: Disable all macros with notification |
| Medium | No | Macro Setting: Disable all macros with notification Add-Ins Setting: Require application add-ins to be signed by trusted publisher Trusted Locations: Disable all trusted locations; only files signed by trusted publishers will be trusted |
| Low | N/A | Macro Setting: Enable all macros (not recommended; potentially dangerous code can run) |
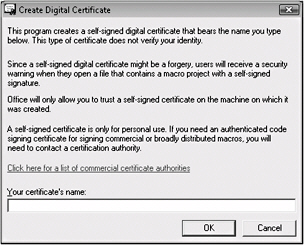
To test macro projects on your own computer, you can create a self-signing certificate using a tool called Selfcert.exe. (You can run this tool from the Start menu by selecting Digital Certificate For VBA Projects under Microsoft Office Tools.) Microsoft Office trusts a self-signed certificate only on a computer that has that certificate in the Personal Certificates store. Keep in mind that a digital certificate you create isn’t issued by a formal certificate authority. To obtain a digital certificate for signing macros or add-ins you want to share, you need to obtain a digital certificate from a commercial certificate authority. You might also be able to obtain a certificate from your internal security administrator or network administrator.
To create your own digital certificate, click the Start button, point to All Programs, click Microsoft Office, click Microsoft Office Tools, and then click Digital Certificate For VBA Projects. (These steps vary slightly depending on which version of Windows you are using: Windows XP or Windows Vista.) In the Create Digital Certificate dialog box, shown here, enter a name for the certificate, and then click OK. When the certificate confirmation message appears, click OK again.
You can then view the certificate in the Personal Certificates store in Microsoft Internet Explorer. (On the Tools menu, click Internet Options, and then click the Content tab. Click Certificates, and then click the Personal tab.)
To digitally sign a macro project, first open the file that contains the project you want to sign. Open the Visual Basic Editor. (You might need to display the Developer tab in Word, Excel, or PowerPoint before you open the Visual Basic Editor.) In the Visual Basic Project pane of the editor, select the project that you want to sign. On the Tools menu, click Digital Signature. If you haven’t previously selected a digital certificate or want to use another one, click Choose, select the certificate, and then click OK twice. To use the current certificate, click OK.
You should sign macros only after you have tested your macro or other program because whenever the code in a signed macro project is changed, the digital signature is removed. If you have the valid digital certificate that was used to sign the project on your computer, the macro project is automatically re-signed when you save it. When you digitally sign macros, it is important to obtain a timestamp so that other users can verify your signature even after the certificate used for the signature has expired. If you sign macros without a timestamp, the signature remains valid only for the period of time that your certificate is valid.
Security Settings for ActiveX Controls
An ActiveX control, which might be provided in a text box or on a toolbar, runs in programs such as Internet Explorer and Microsoft Office applications. They can provide additional functions to a program by responding to user input or to changes in the state of a Web page. But because ActiveX controls can access your file system and change settings for the operating system, an ActiveX control can, in effect, take over your computer and damage it.
Figure 3–8 shows the ActiveX Settings page in the Trust Center for PowerPoint. You’ll see that the settings here are similar to those for macros and add-ins. You can choose to let these controls run without notification (probably not the wisest choice), disable all controls (which means you have to do without the benefits these controls provide), or impose a level of restriction that helps you weed out the ActiveX controls that could potentially do you harm.
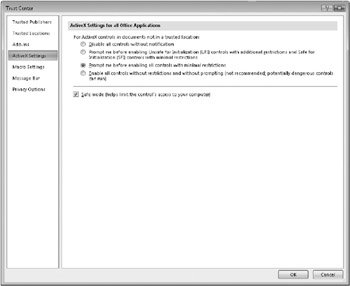
Figure 3–8: The Trust Center provides security settings for ActiveX controls.
Microsoft has provided developers with guidance for how to make the ActiveX controls they create more secure. The Trust Center also examines an ActiveX control that’s part of a document to check whether it contains any well-known indicators that would flag it as potentially unsafe. The Trust Center checks, for example, whether the controls have been marked (digitally signed) as being Safe For Initialization (SFI).
The Trust Center also checks the document that contains the ActiveX control. If the document contains a Visual Basic for Applications (VBA) project, the Trust Center is more restrictive because the document contains both macros and ActiveX controls. As it does with a potentially unsafe macro, the Trust Center displays a warning when an ActiveX control is present and lets you choose whether to enable the control or not.
For the most part, you can probably leave the default setting for ActiveX controls selected. With this setting, you’ll receive a prompt asking you to enable any ActiveX control. The first and fourth settings shown in Figure 3–8-that is, disabling or enabling all controls-are either too restrictive or not restrictive enough. The second setting, which refers to SFI controls as well as those considered Unsafe For Initialization (UFI) provides some flexibility in when and how a control is enabled. In a document that contains a VBA project-meaning that a macro project is present-this setting initially prevents all ActiveX controls from running. When you open a document, you’re notified about the presence of an ActiveX control. If you choose to enable the control, a UFI ActiveX control is loaded with additional restrictions. An SFI ActiveX control is loaded with minimal restrictions.
In a document that doesn’t contain a VBA project, SFI ActiveX controls are enabled with minimal restrictions. The Message Bar doesn’t appear, and you won’t see any notifications about the presence of ActiveX controls in your documents. However, if there is at least one UFI ActiveX control in the document, you are notified, and any UFI ActiveX controls are disabled.
EAN: 2147483647
Pages: 299