| There are many ways to perform network auditing and information gathering from a PC environment. These range from operating system programs like ping and Tracert (or Traceroute), to more extensive and insidious tools like the infamous Nmap. However, the iPAQ and other handheld computers suffer from a severe shortage of these types of built-in programs. At least they did, until a couple of feature packed-network information programs were released. The names of these programs are Net Force and vxUtil. They are both useful, and each has features the other doesn't include. By using these programs together, you have at your disposal the equivalent of an operating system's range of networking tools. The following is a breakdown of the programs and some screenshots of the programs in action. See Figures 10.8 and 10.9 for a screenshot of each of the startup screens. Figure 10.8. The vxUtil main screen.  Figure 10.9. The Net Force Echo screen.  Installing Net Force and vxUtil Net Force is a professionally designed program, which means the installation is a snap. This program, like CENiffer, only requires the user to download and run the executable file to install the program. The programs are then ported to the Pocket PC computer and included under the program listing. The utilities included with Net Force are as follows : -
Echo (Net Force) ” This is the standard Echo program that sends data to a server running the echo daemon, which should return the same data. -
WHOIS (Net Force & vxUtil) ” WHOIS is the standard utility used to look up information on existing domains. For example, a WHOIS on VirusMD.com returns the following: Domain Name: VIRUSMD.COM Registrar: NETWORK SOLUTIONS, INC. Whois Server: whois.networksolutions.com Referral URL: http://www.networksolutions.com Name Server: NS2.PHPWEBHOSTING.COM Name Server: NS1.PHPWEBHOSTING.COM Updated Date: 05-nov-2001 >>> Last update of whois database: Mon, 20 May 2002 16:49:04 EDT <<< The Registry database contains ONLY .COM , .NET , .ORG , and .EDU domains and Registrars. -
finger (Net Force & vxUtil) ” finger is another standard utility that has lost much functionality because of Windows. It is a tool to query a server for its user list, if the server is running the finger service. -
Subnet Calculator (Net Force and vxUtil) ” This program is helpful in determining what IP addresses belong to a network. When setting up a network, a mask address is used to determine the range of IP addresses that can be assigned to different computers. This basically becomes the limiting factor for that network segment. Knowing this helps a network auditor create a map of the computer connections. -
Password generator (vxUtil) ” One of the most common ways a hacker can gain access to a computer is through the use of a weak password. A password generator is programmed to know all the rules for creating a strong and solid password (Don't believe the rumors that "password generator" tools phone home to create heuristic brute-force dictionaries.) -
TFTP Server and Client (Net Force) ” Trivial File Transfer Protocol is a type of communication that requires no password or authentication. If you know the name of the server and the exact name of the file, you can access information. This aspect of Net Force allows you to share files with other network users, whether they are wireless or wired (see Figure 10.10). However, this also means that you are now susceptible to attack. Figure 10.10. Net Force's TFTP Server screen.  -
ping (Net Force & vxUtil) ” ping is a computer version of radar. This program sends out a signal, to which another signal is returned. If no signal is returned, the other computer is not online. Although this is the typical assumption, it is possible to stop a computer from replying to pings , thus making it appear invisible. Figure 10.11 is a screenshot of vxUtil performing a ping on the IP address 192.168.0.1. Figure 10.11. vxUtil's ping program. 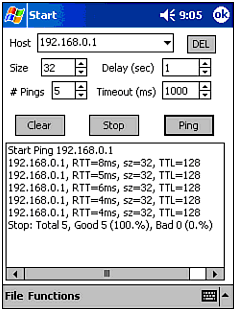 -
Ping sweeper (vxUtil) ” A ping sweeper is used to test the existence of computers on a subnet. It sends out a ping to each possible IP address, and waits for replies. Just as with ping, a reply typically means a computer is online, and no reply means the IP address is unused (see Figure 10.12). Figure 10.12. vxUtil in a ping sweep. 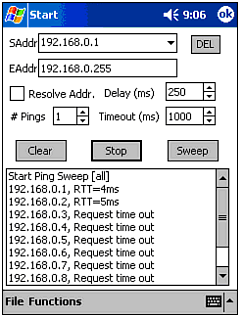 -
Port scanner (Net Force & vxUtil) ” A port scanner is used to probe for open ports on a computer (see Figure 10.13). This is important because an open port means there is a program or service running on the computer. Thanks to standardization, a security professional can often determine what programs are running on a computer based on a simple port scan. Figure 10.13. vxUtil performing a port scan. 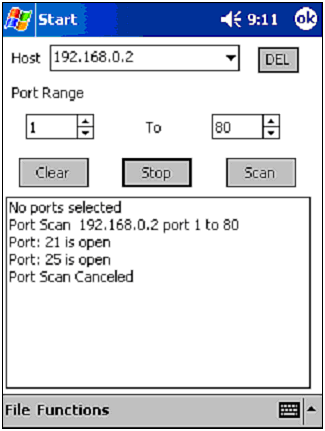 -
HTTP Fetch (Net Force & vxUtil) ” HTTP Fetch is a basic text-based Web browser. Although this seems mundane, it can be informative because of the capability to retrieve raw Web page code. This is particularly handy if you are using the default Internet Explorer as your Web browser because that version does not enable you to view the source code. -
DNS Lookup/Audit (Net Force & vxUtil) ” Every computer connected to the Internet ironically has one thing in common: it is unique. This uniqueness facilitated the creation of a human-friendly naming convention built on top of the numbering scheme used by computers. Although domain names are useful to the average user, security consultants will want to be able to determine the actual IP address of Web servers and other servers online. In addition, they will also want to be able to perform reverse lookups on IP address blocks to see whether there are any domain names assigned to them. This tool allows you to do that, and all from the comfort of your Pocket PC-based computer (see Figure 10.14). Figure 10.14. vxUtil performing a DNS audit. 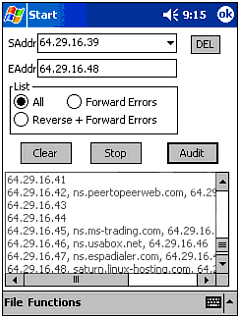 -
Tracert (vxUtil) ” Tracert is one of the most powerful informational programs available for the PC environment. With it, you can determine where and how a connection is made to a server online. For example, if you're on an iPAQ and you want to learn the IP addresses of the routers, you can perform a tracert to http://www.virusmd.com and watch the path appear before your eyes. -
Information (Net Force & vxUtil) ” This is a general information tool that provides the user with information about the network to which he is connected, and most importantly, the iPAQ's IP address (see Figure 10.15). The IP address is key to performing any further probing. In other words, if you want to call the police about a burglar breaking into the house next door, you had better know your own address so you can tell the cops where to go! Figure 10.15. Net Force's network information screen. 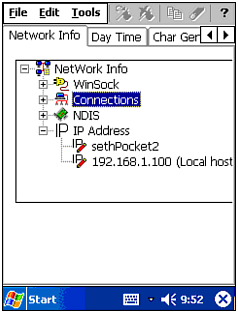 From this review of Net Force and vxUtil, you should be able to see just how much power an iPAQ can have for both hackers and security consultants. The amount of information one can gather through the discussed tools is staggering. Although the use of these tools might be tedious , there are times when only a palmtop will do ” and for those times, there is Net Force and vxUtil. |







