CENiffer
| Wireless networks have a unique weakness that can enable anyone with the right equipment the capability to capture and read data as it is sent over the airwaves. This could include emails, chats, Web page requests and more. In other words, if it can be sent over a network, it can be sniffed. Even in the PC environment, sniffers often require Linux or a "patched" version of Windows. If you are familiar with these tools, you will already know that sniffers, although simple in concept, are often complex in interpretation. You need to understand how TCP/IP layers work, what hex and ASCII are, and have a firm grip on understanding how to read network messages. The amount of information is sometimes overwhelming, and it can take even the most dedicated expert a relatively long time to analyze. For these reason, we would not expect a sniffer to show up on a platform with such a limited amount of memory and resources. However, CENiffer is just that! It is a sniffer capable of running on a Pocket PC-based computer, such as an iPAQ. CENiffer is a fully functional sniffer with many of the features that you would only expect to find in a full PC version. The following is a list of some of these features:
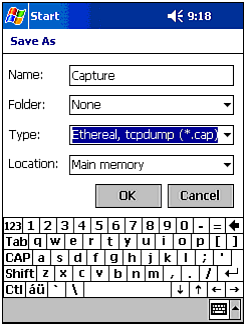
After trying CENiffer, you will see it is packed full of features and options that make it one of the best sniffers available for Pocket PC-based computers. The next few pages will walk you through the program and illustrate just how powerful it is. Installing CENifferInstalling CENiffer is also fairly simple. However, there is one twist: You must install the downloaded file on the Pocket PC-based computer. In other words, you will need to download the program to your PC, transfer the *.cab file to your Pocket PC computer, and execute it from there. You can also simply download the file from your mobile computer using the built-in browser. You must also install the appropriate version for your Pocket PC-based processor type (StrongARM, MIPS, or SH3). Using CENifferUpon opening the program, you are presented with a blank screen and the typical tool bar. The first thing to do is set up how and where you want to record the session. As you can see from Figure 10.3, you can save data in an expansion card in various formats. Figure 10.3. Setting up CENiffer to capture data in an Ethereal-compatible format. After you have this set up, it's time to create some filters. A filter will enable you to remove the excess data and target only what is of interest. For example, you can filter all ICMP traffic, or all traffic to a certain host. To set a filter up, click on Options
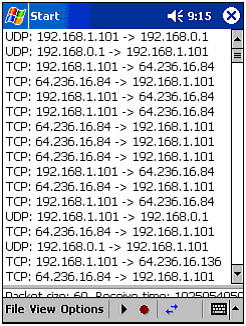
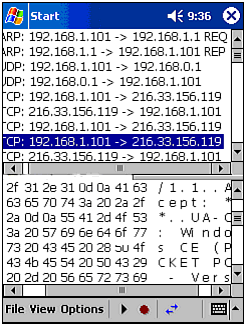
Figure 10.4. Setting up an HTTP filter using CENiffer. Figure 10.5. CENiffer filter list. Next, determine whether you want to sniff only data passing to and from the iPAQ you are operating, or whether you want to capture all data passing through the airwaves. To do the latter, you will need to enable promiscuous mode by clicking on Options As the program captures data, it will list the MAC addresses, IP addresses, or protocol and port numbers of the packets being captured. You can change this view by using the double arrow button on the toolbar. As illustrated in Figure 10.6, it should not take long to start capturing valuable information. In this example, we are capturing all data between a WLAN client and a random Web site. As you can see, the traffic is mostly TCP, with a few UDP packets sent between the client and the Internet gateway. Figure 10.6. Using CENiffer to capture data. After you have captured enough data, you are ready to analyze it. To do this, click the Play arrow off, and select a packet to view. After you have done this, you will be presented with the packet's transmission and header information. This information tells you the purpose of the packet's transmission (see Figure 10.7). If you scroll further down, you can view the actual data sent in the packet as it appears in hex and ASCII. This is the information that will be dumped into the saved file for future analysis. To do this, you can load the file in Ethereal (or in a text editor, if you are really an expert) on your PC. Figure 10.7. Detailed information in a packet. As you can see, this program is a fully functional sniffer, right on your Pocket PC computer. In fact, this program is so feature-rich that it can complement a laptop-based sniffer (Sniffer or EtherPeek) quite well. If you have a need to monitor network traffic with minimal equipment, get your hands on CENiffer. |
EAN: 2147483647
Pages: 171
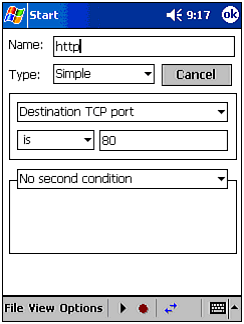
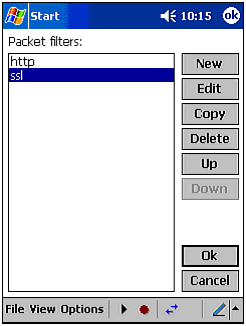
 Filters. This will present you with a blank list that you have to fill. To add a filter, click on the Add button, followed by Edit. Give the filter a name and configure it to filter based on a set of rules. In Figure 10.4, we set up CENiffer to filter all traffic on port 80, which is the default Web server (http) port. In addition to simple sniffing, CENiffer supports OFDL, which allows for some very in-depth control over what and how CENiffer filters packets. After you have some entries (see Figure 10.5), close the filter screen. The following lists the types of filters available:
Filters. This will present you with a blank list that you have to fill. To add a filter, click on the Add button, followed by Edit. Give the filter a name and configure it to filter based on a set of rules. In Figure 10.4, we set up CENiffer to filter all traffic on port 80, which is the default Web server (http) port. In addition to simple sniffing, CENiffer supports OFDL, which allows for some very in-depth control over what and how CENiffer filters packets. After you have some entries (see Figure 10.5), close the filter screen. The following lists the types of filters available: