| IP is a network layer protocol that provides a connectionless service for the delivery of data. Since it is connectionless, IP is an unreliable protocol that does not guarantee the delivery of data. On the Internet, IP is the protocol used to carry data, but the actual delivery of the data is assured by transport layer protocols such as TCP. IP headers contain 32-bit addresses that identify the sending and receiving hosts . Routers use these addresses to select the packet's path through the network. IP spoofing is an attack that involves faking the return address in order to defeat authentication. That's why you should not depend only on the validity of the source address when performing authentication. IP packets may also be split ( fragmented ) into smaller packets, permitting a large packet to travel across a network that can only handle smaller packets. The Maximum Transmission Unit (MTU) defines the maximum packet size a specific network can support. IP then reassembles the fragmented packets on the receiving end. However, as we will see later, fragmentation attacks can be used to defeat firewalls under the right circumstances. 6.4.1 IP Packet Format An IPv4 packet contains several types of information, as illustrated in Figure 6-3. IPv6 is discussed later in the chapter. Figure 6-3. A representation of IP packet fields 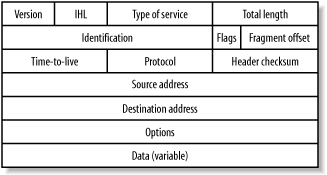 The following discussion describes the IP packet fields illustrated in Figure 6-3: -
- Version
-
This is a four-bit field indicating the version of IP in use (in this case, IPv4). -
- IP header length (IHL)
-
Specifies the header length in 32-bit (4-byte) words. This limits the maximum IPv4 header length to 60 bytes, which was one of the reasons for IPv6. -
- Type-of-service
-
Assigns the level of importance and processing instructions for upper layers . -
- Total length
-
Provides the length in bytes of the IP datagram (the data payload plus the IP header). -
- Identification
-
A unique ID number that orders the data at the destination. This is a 16-bit number that is important in fragmentation. -
- Flags
-
These are the fragmentation flags. These flags specify whether a packet can be fragmented and, if so, whether the packet is the last fragment of a packet sequence. Only two bits of this three-bit field are defined. The first bit is used to specify the "do not fragment" field. If this field is set, then the PMTU (Path MTU) is calculated, ensuring that all packets sent along the route are small enough to avoid fragmentation at MTU bottlenecks. The second bit indicates if the particular fragment is the last piece of the datagram or not. -
- Fragment offset
-
Specifies the order of the particular fragment in the packet sequence. -
- Time-to-live
-
Defines a counter to keep packets from looping endlessly. The host sets this field to a default value, and each router along the path decrements this field by one. When the value drops to one, the next router drops the packet. The process prevents infinite looping of forlorn packets. -
- Protocol
-
This eight-bit field defines the protocol that will receive the packet from the IP layer. -
- Header checksum
-
This field checks for IP header integrity. Note that this is not a cryptographic checksum and can be easily forged. -
- Source address
-
This 32-bit field specifies the sender's address. -
- Destination address
-
This 32-bit field specifies the receiver's address. -
- Options
-
Specifies various options. -
- Data
-
Includes the information payload. |
