Remote Access
|
|
One of the primary purposes for having a network is the ability to connect systems together. As networks have grown, many technologies have come on the scene to make this process easier and more secure. A key area of concern relates to the connection of systems and other networks that are not part of your network. This section discusses the more common protocols used to facilitate connectivity.
Serial Line Internet Protocol
Serial Line Internet Protocol (SLIP) is an older protocol that was used in early remote access environments. SLIP was originally designed to connect UNIX systems together in a dial-up environment, and it supports only serial communications. SLIP is a very simple protocol that is used to pass TCP/IP traffic. The protocol is not secure, nor is it efficient. Many systems still support SLIP strictly for legacy systems. SLIP is not widely used anymore, and it has largely been replaced by Point-to-Point Protocol (PPP).
Point-to-Point Protocol
Introduced in 1994, Point-to-Point Protocol (PPP) has largely replaced SLIP. PPP offers multiple protocol support including AppleTalk, IPX, and DECnet. PPP works with POTS, Integrated Services Digital Network (ISDN), and other faster connections such as T1. PPP does not provide data security, but it does provide authentication using CHAP. Figure 3.13 shows a PPP connection over an ISDN line. In the case of ISDN, PPP would normally use one 64Kbps B channel for transmission. PPP allows many channels in a network connection (such as ISDN) to be connected or bonded together to form a single virtual connection.
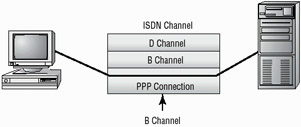
Figure 3.13: PPP using a single B channel on an ISDN connection
PPP works by encapsulating the network traffic in a protocol called Network Control Protocol (NCP). Authentication is handled by Link Control Protocol (LCP). A PPP connection allows remote users to log on to the network and have access as though they were local users on the network. PPP does not provide for any encryption services for the channel.
As you might have guessed, the unsecure nature of PPP makes it largely unsuitable for WAN connections. A dial-up connection using PPP works very well, because it is not common for an attacker to tap a phone line. To counter this, other protocols have been created that take advantage of the flexibility of PPP and build on it. You want to make sure that all of your PPP connections use secure channels, dedicated connections, or dial-up connections.
Remote users who connect directly to a system using dial-up connections do not necessarily need to have encryption capabilities enabled. If the connection is a direct one, the likelihood that anyone would be able to tap an existing phone line is relatively small. However, you should make sure that connections through a network do use an encryption-oriented tunneling system.
802.1X Wireless Protocols
The IEEE 802.1x protocols refer to a broad range of wireless protocols for wireless communications. There are two major families of standards for wireless communications: the 802.11 family and the 802.16 family. The 802.11 standards are discussed in more detail in Chapter 4 under "Wireless Systems." The 802.16 standard is undergoing debate in the IEEE and was finalized in the fall of 2002.
The 802.11 protocols are primarily short-range systems suitable for use in buildings and campus environments.
VPN
VPNs are used to make connections between private networks across a public network, such as the Internet. These connections are not guaranteed to be secure unless a tunneling protocol, such as PPTP, and an encryption system, such as IPSec, is used. A wide range of options, including proprietary technologies, is available for VPN support. Many of the large ISPs and data communication providers provide dedicated hardware with VPN capabilities. Many servers also provide software VPN capabilities for use between two networks.
VPN systems can be dedicated to a certain protocol, or they can pass whatever protocols they see on one end of the network to the other end. A pure VPN connection appears as a dedicated wired connection between the two network ends.
RADIUS
Remote Authentication Dial-In User Service (RADIUS) is a mechanism that allows authentication of dial-in and other network connections. A RADIUS server can be managed centrally, and the servers that allow access to a network can verify with a RADIUS server whether or not an incoming caller is authorized. In a large network with many connections, this allows a single server to perform all authentications. Figure 3.14 shows an example of a RADIUS server communicating with an ISP to allow access to a remote user. Notice that the remote server is actually functioning as a client to the RADIUS server. This allows centralized administration of access rights.
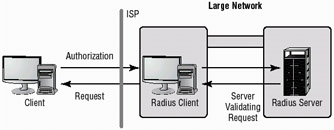
Figure 3.14: The RADIUS client manages the local connection and authenticates against a central server.
The major difficulty with a single server RADIUS environment is that the entire network may refuse connections if the server malfunctions. Many RADIUS systems allow multiple servers to be used to increase reliability. All of these servers are critical components of the infrastructure, and they must be protected from attack. The RADIUS protocol is an IETF standard, and it has been implemented by most of the major operating system manufacturers.
TACACS/+
Terminal Access Controller Access Control System (TACACS) is a client/ server-oriented environment, and it operates in a similar manner to RADIUS. The most current method or level of TACACS is TACACS/+. TACACS/+ allows credentials to be accepted from multiple methods, including Kerberos. The TACACS client/server process occurs in the same manner as the RADIUS process illustrated in Figure 3.14. CISCO has widely implemented TACACS/+ for connections. TACACS/+ is expected to become widely accepted as an alternative to RADIUS.
Tunneling Protocols
Tunneling protocols add an additional capability to the network. They provide the ability to create tunnels between networks that can be more secure, support additional protocols, and provide virtual paths between systems. The most common protocols used for tunneling are Point-to-Point Tunneling Protocol (PPTP), Layer 2 Forwarding (L2F), Layer 2 Tunneling Protocol (L2TP), and IPSec:
PPTP PPTP supports encapsulation in a single point-to-point environment. PPTP encapsulates and encrypts PPP packets. This makes PPTP a favorite low-end protocol for networks. The negotiation between the two ends of a PPTP connection is done in the clear. Once the negotiation is performed, the channel is encrypted. This is one of the major weaknesses of the PPTP protocol. A packet-capture device, such as a sniffer, that captures the negotiation process can potentially use that information to determine the connection type and information about how the tunnel works. Microsoft developed PPTP, and they support it on most of their products. PPTP uses port 1723 and TCP for connections.
L2F L2F was created by Cisco as a method of creating tunnels primarily for dial-up connections. L2F is similar in capability to PPP and should not be used over WANs. L2F does provide authentication, but it does not provide encryption. L2F uses port 1701 and TCP for connections.
L2TP Relatively recently, Microsoft and Cisco agreed to combine their respective tunneling protocols into one protocol: the Layer Two Tunneling Protocol (L2TP). L2TP is a hybrid of PPTP and L2F. L2TP is primarily a point-to-point protocol. L2TP supports multiple network protocols and can be used in networks besides TCP/IP. L2TP works over IPX, SNA, and IP. This gives L2TP the capability of being used as a bridge across many different types of systems. The major problem with L2TP is that it does not provide data security, in that the information is not encrypted. Security can be provided by protocols such as IPSec. L2TP uses port 22 and TCP for connections.
SSH Secure Shell (SSH) is a tunneling protocol originally designed for UNIX systems. SSH uses encryption to establish a secure connection between two systems. SSH also provides security equivalent programs such as Telnet, FTP, and many of the other communications-oriented programs under UNIX. SSH is now available for use on Windows systems as well. This makes SSH the preferred method of security for Telnet and other cleartext-oriented programs in the UNIX environment. SSH uses port 22 and TCP for connections.
IPSec IPSec (Internet Protocol Security) is not a tunneling protocol, but it is used in conjunction with tunneling protocols. IPSec is oriented primarily toward LAN-to-LAN connections, rather than dial-up connections. IPSec provides secure authentication and encryption of data and headers. This makes IPSec a good choice for security. IPSec can work in either Tunneling mode or Transport mode. In Tunneling mode, the data or payload and message headers are encrypted. Transport mode encrypts only the payload.
Your company wants to support network connections for remote users. These users will use the Internet to access desktop systems and other resources in the network. What would you advise the company to consider?
You would want your organization to implement a tunneling protocol that supports security. A good solution would be a VPN connection that uses IPSec. You may also want to explore protocols like SSL, TLS, and SSH as alternatives. All of these protocols offer security as a part of their connection process.
|
|
EAN: 2147483647
Pages: 167