Devices
|
|
Connecting all of these components requires physical devices. Large multinational corporations, as well as small and medium-sized corporations, are building networks of enormous complexity and sophistication. These networks work by utilizing miles and miles of both wiring and wireless technologies. Whether the network is totally wire and fiber-based, or totally wireless, the method of transmitting data from one place to another opens vulnerabilities and opportunities for exploitation. These vulnerabilities appear whenever an opportunity exists to intercept information from the media.
The devices briefly described here are the components that you will typically encounter in a network.
Firewalls
Firewalls are one of the first lines of defense in a network. There are different types of firewalls, and they can be either stand-alone systems or included in other devices such as routers or servers. Many firewalls are add-in software available for servers or workstations. The basic purpose of a firewall is to isolate one network from another. Firewalls are becoming available as appliances, meaning they are installed into the network between two networks. Appliances are freestanding devices that operate in a largely self-contained manner. They should require less maintenance and support than a server-based product.
Firewalls function as one of the following:
-
Packet filter
-
Proxy firewall
-
Stateful inspection
The proxy shown in Figure 3.2 effectively limits access from outside networks, while allowing inside network users to access outside resources.
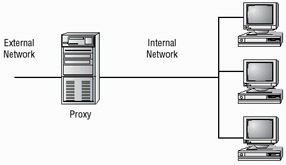
Figure 3.2: A proxy firewall blocking network access from external networks
The proxy in this illustration is also performing firewall functions. The end user in this network uses the proxy server to manage traffic and receive returning information. This section discusses three of the most common functions that firewalls perform.
Packet Filter
A firewall operating as a packet filter will pass or block traffic to specific addresses based on the type of application. A packet filter may allow web traffic on Port 80 and block Telnet traffic on Port 23. This type of filtering is included in many routers. If a received packet request asks for a port that is not authorized, the filter may reject the request or simply ignore it. Many packet filters can also specify which IP addresses can request which ports and allow or deny them based on the security settings of the firewall. Packet filters are growing in sophistication and capability. A packet filter does not analyze the contents of a packet; it decides whether to pass it or not based on the addressing information of the packet.
Proxy Firewall
Think of a proxy firewall as an intermediary between your network and another. Proxy firewalls are used to process requests from an outside network and evaluate whether the request is forwarded or not. The proxy will intercept all of the packages and reprocess them for use internally. This process includes hiding IP addresses. The proxy firewall will examine the data and make rules-based decisions about whether to forward the request or refuse it.
The proxy firewall provides better security than packet filtering because of the increased intelligence that a proxy firewall offers. Requests from internal network users are routed through the proxy. The proxy, in turn, repackages the request and sends it along, thereby effectively isolating the user from the external network.
A server-based proxy firewall will typically use two NIC cards. This type of firewall is referred to as a dual-homed firewall. One of the cards is connected to the outside network and one is connected to the internal network. The proxy software manages the connection between the two NIC cards. This effectively segregates the two networks from each other and offers increased security. Figure 3.3 illustrates a dual-homed firewall segregating two networks from each other.
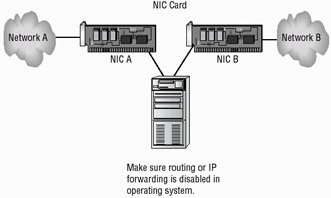
Figure 3.3: A dual-homed firewall segregating two networks from each other
You are the network administrator of a small network. You are installing a new firewall server using Windows 2000. After you complete the installation, you notice that the network does not appear to be routing traffic through the firewall and that inbound requests are not being blocked. This presents a security problem for the network because you have been getting unusual network traffic lately.
The most likely solution to this problem deals with the fact that Windows 2000 offers the ability to use IP forwarding in a dual-homed server. IP forwarding bypasses your firewall and uses the server as a router. Even though the two networks are effectively isolated, the new router is doing its job well and it is routing IP traffic.
You will need to verify that IP forwarding and routing services are not running on this server
The proxy function can occur at either the application level or the circuit level. Application-level proxy functions will read the individual commands of the protocols that are being served. This type of server is very advanced and must know the rules and capabilities of the protocol used. This type of proxy would know the difference between a GET and a PUT operation, for example, and would have rules specifying how to execute them. A circuit-level proxy creates a circuit between the client and the server and does not deal with the contents of the packets that are being processed.
A unique application-level proxy server must exist for each protocol supported. Many proxy servers also provide full auditing, accounting, and other usage information that would not normally be kept by a circuit-level proxy server.
| Note | Combining firewalls with other firewalls will provide a variety of configuration and security options. See Chapter 6, "Working with a Secure Network," for further details. |
Stateful Inspection
The last section on firewalls focuses on the concept of stateful inspection. Stateful Inspection is also referred to as stateful packet filtering. Most of the devices we use in networks do not keep track of how information is routed or used. Once a packet is passed, the packet and path are forgotten. In stateful inspection or stateful packet filtering, records are kept using a state table that tracks every communications channel. Stateful inspections occur at all levels of the network and provide additional security, especially in connectionless protocols such as User Datagram Protocol (UDP) and Internet Control Message Protocol (ICMP). This process adds additional complexity to the process. DoS attacks present a challenge because flooding techniques are used to overload the state table and effectively cause the firewall to shut down or reboot.
Routers
The primary instrument used for connectivity between two or more networks is the router. Routers work by providing a path between the networks. A router will have two connections used to join the networks. Each connection will have its own address and will appear as a valid address in its respective network. Figure 3.4 illustrates a router being connected between a LAN and a WAN.
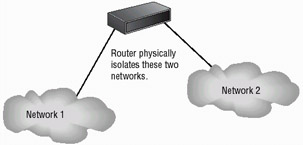
Figure 3.4: Router connecting a LAN to a WAN
Routers are very intelligent devices, and they store information about the networks to which they are connected. Most routers can be configured to operate as packet-filtering firewalls. Many of the newer routers also provide advanced firewall functions.
Routers are also used to translate from LAN framing to WAN framing (for example, a router that connects the 10BaseT network to the T1 network shown in Figure 3.4). This is needed because the network protocols are different in LANs and WANs. Such routers are referred to as border routers. They serve as the outside connection of a LAN to a WAN, and they operate at the border of your network. Like the Border Patrol of many countries, they decide who can come in and under what conditions.
Dividing internal networks into two or more subnetworks is a common use for routers. Routers can also be connected internally to other routers, effectively creating zones that operate autonomously. Figure 3.5 illustrates a corporate network that uses the combination of a border router for connection to an ISP and internal routers to create autonomous networks for communications. This type of connection keeps local network traffic off the backbone of the corporate network and provides additional security to internal users.
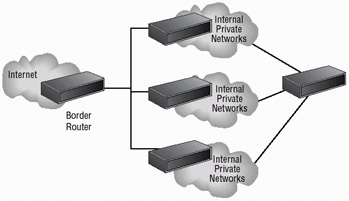
Figure 3.5: A corporate network implementing routers for segmentation and security
Routers establish communication by maintaining tables about destinations and local connections. A router contains information about the systems connected to it and where to send requests if the destination is not known. These tables grow as connections are made through the router.
Routers communicate routing and other information using three standard protocols (RIP, BGP, and OSPF). Routing Information Protocol (RIP) is a simple protocol that is part of the TCP/IP protocol suite. Routers that use RIP routinely broadcast the status and routing information of known routers. RIP also attempts to find routes between systems using the smallest number of hops or connections. Border Gateway Protocol (BGP) is a relatively new protocol that allows groups of routers to share routing information. Open Shortest Path First (OSPF) is a protocol that allows routing information to be updated faster than with RIP.
Routers are your first lines of defense, and they must be configured to pass only traffic that is authorized by the network administrators. In effect, a router can function as a firewall if it is configured properly.
Switches
Switches are multiport devices that improve network efficiency. A switch will typically have a small amount of information about systems in a network. The use of switches improves network efficiency because of the virtual circuit capability. Switches also improve network security because the virtual circuits are more difficult to examine with network monitors. You can think of a switch as a device that has some of the capabilities of routers and hubs. The switch maintains limited routing information about systems in the internal network and allows connections to systems like a hub. Many modern hubs also provide switching capabilities. Figure 3.6 shows a switch in action between two workstations in a LAN. The connection is not usually secure nor is it encrypted; however, it does not leave the switched area and become part of the overall broadcast traffic as typically found on a star- based or bus-based LAN.

Figure 3.6: Switching between two systems
Wireless Access Points
The primary method of connecting a wireless device to a network is with a wireless portal. A wireless access point is a low-power transmitter/receiver, also known as a transceiver, which is strategically placed for access. The portable device and the access point communicate using one of several communications protocols including IEEE 802.11 (also known as Wireless Ethernet).
Wireless communications, as the name implies, do not use wires as the basis for communication. Most frequently, they use a portion of the Radio Frequency (RF) spectrum called microwave. Wireless communication methods are becoming more prevalent in computing because the cost of the transmitting and receiving equipment has fallen drastically over the last few years. Wireless also offers mobile connectivity within a campus, building, or even a city. Most wireless frequencies are shared frequencies, in that more than one person may be using the same frequency for communication. Figure 3.7 illustrates a wireless portal being used to connect a computer to a company network. Notice that the portal connects to the network and is treated as any other connection used in the network.
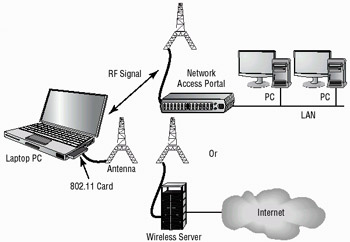
Figure 3.7: Wireless access point and workstation
Wireless communications, although convenient, are not usually secure. Virtually any police scanner can be used to intercept the frequencies that wireless access points use. Connecting the output from the scanner to the audio port on a PC, using very inexpensive software, and decoding wireless communications is a relatively straightforward proposition. If wireless portals are installed in a building, the signals will frequently radiate past the inside of the building, and they can be detected and decoded outside of the building using very inexpensive equipment. Most of the newer wireless controllers use special ID numbers and must be configured in the network cards to allow communications. Using ID number configurations does not necessarily prevent wireless networks from being monitored.
| Warning | Never assume that a wireless connection is secure. The emissions from a wireless portal may be detectable through walls and for several blocks from the portal. Interception is extremely easy to accomplish given that RF is the medium used for communication. Newer wireless devices offer data security. If this is available, it should be used. |
Modems
A modem is a hardware device that connects the digital signals from a computer to the analog telephone line. It allows these signals to be transmitted longer distances than are possible with digital signals. The word "modem" is an amalgam of the words "modulator" and "demodulator," which are the two functions that occur during transmission.
Modems present a unique set of challenges from a security perspective. Most modems will answer any call made to them when connected to an outside line. Once the receiving modem answers the phone, it will generally synchronize with a caller's modem and make a connection. A modem, when improperly connected to a network, can allow instant unsecured access to the data and resources in a system or network. Many of the PCs being built and delivered today come standard with internal modems. If a physical security breach occurs, a modem can be used as a remote connection to your network that allows unrestricted access. This can occur with no knowledge on the part of the owner of the system or the network administrators. Modems, unless specifically needed, should be disabled or removed completely from network workstations. If this is not possible, they should be configured so as not to auto-answer incoming calls.
Many preconfigured administrative systems provide modem connections for remote maintenance and diagnostics. These connections should be either password-protected or have a cut-off switch so that they do not expose your network to security breaches.
Remote Access Services
Remote Access Services (RAS) is a product offered by Microsoft on Windows- based products to facilitate the process of connecting two computers via a modem or other connection over a long distance. You will encounter the term RAS used interchangeably to describe both the Microsoft product and the process of connecting remote systems. Figure 3.8 depicts a dial-up connection being made from a workstation to a network using a RAS server on the network. In this case, the connection is being made between a Windows- based system and a Windows Server using POTS (Plain Old Telephone Service) and a modem.
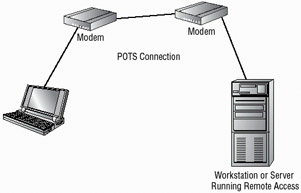
Figure 3.8: A RAS connection between a remote workstation and a Windows server
The RAS connection is accomplished via dial-up or network technologies, such as VPNs, ISDN, DSL, or cable modems. RAS connections may be secure or in the clear, depending on the protocols that are used in the connection.
Telecom/PBX Systems
Telecommunications or telecom capabilities have undergone radical changes in the last 10 years. The telephone systems and technologies available to deal with communications have given many small businesses fully integrated voice and data services at very reasonable prices.
These changes have complicated the security issues that must be handled. One of the primary tools in communication systems is the Private Branch Exchange (PBX) system. PBX systems now allow users to connect voice, data, pagers, networks, and almost any other conceivable application into a single telecommunication system. In short, a PBX system allows a company to be its own phone company.
The technology is developing to the point where all communications occur via data links to phone companies using standard data transmission technologies, such as T1 or T3. This means that both voice and data communications are occurring over the same network connection to a phone company or a provider. This allows a single connection for all communications to a single provider of these services.
Potentially, your phone system is a target for attack. Figure 3.9 shows a PBX system connected to a phone company using a T1 line. The phone company, in this drawing, is abbreviated CO (Central Office). The CO is where the phone company systems that deal with routing and switching of calls and services exist.
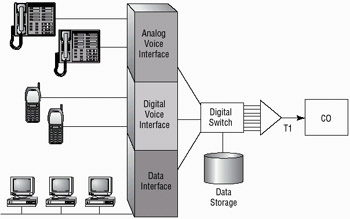
Figure 3.9: A modern digital PBX system integrating voice and data onto a single network connection
If your phone system is part of your data communication network, an attack on your network will bring down your phone system. This can cause the stress level in a busy office to increase dramatically.
The problems of security in this situation also increase because now you must also work to assure security for your voice communications. No incidents of phone systems being attacked by malicious code have been reported yet, but such attacks will probably become a concern in the near future.
| Warning | Imagine if you will that someone left a voice message for the president of your company. A phreaker (someone who abuses phone systems, as opposed to data systems) might intercept this message, alter it, and put it back. The results of this prank could cause a calamity for the company (or at least you). Make sure that the default password is changed after the installation has occurred on the maintenance and systems accounts. |
Virtual Private Network
A Virtual Private Network (VPN) is a private network connection that occurs through a public network. A private network provides security over an otherwise unsecure environment. VPNs can be used to connect LANs together across the Internet or other public networks. A VPN requires either special hardware to be installed or a VPN software package running on servers and workstations. With a VPN, the remote end appears to be connected to the network as if it were connected locally.
VPNs typically use a tunneling protocol such as L2TP, IPSec, and PPTP. Figure 3.10 shows a remote network being connected to a LAN using the Internet and a VPN. This connection appears to be a local connection, and all message traffic and protocols are available across the VPN.
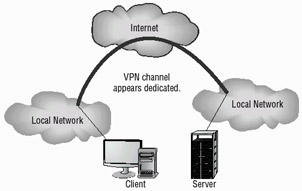
Figure 3.10: Two LANs being connected using a VPN across the Internet
VPNs are becoming the connection of choice when establishing an Extranet or Intranet between two or more remote offices. The major security concern when using a VPN is encryption. PPTP offers some encryption capabilities, although it is weak. IPSec offers higher security, and it is becoming the encryption system used in many secure VPN environments.
| Note | Even though a VPN is created through the Internet or other public network, the connection logically appears to be a part of the local network. This is why a VPN connection used to establish a connection between two private networks across the Internet is considered a private connection or an Extranet. |
Network Monitoring and Diagnostics
Network monitoring is an area as old as data communications. Network monitoring is the process of using a data-capture device or other method to intercept information from a network. Network monitors come in one of two forms. This section will introduce you to network monitors, commonly referred to as sniffers, and Intrusion Detection Systems (IDS). These tools allow you to examine the actual activity on your network or, in the case of an IDS, add intelligence to the process, monitor system logs, monitor suspicious activities, and take corrective action when needed.
| Note | The concepts of network monitoring and IDS are briefly covered here, and they are covered in greater detail later in the book in Chapter 4, "Monitoring Communications Activity." |
Network Monitors
Network monitors, otherwise called sniffers, were originally introduced to help troubleshoot network problems. Simple network configuration programs, like IPCONFIG, do not get down on the wire and tell you what is physically happening on a network. Examining the signaling and traffic that occurs on a network requires a network monitor. Early monitors were bulky and required a great deal of expertise to use. Like most things in the computer age, they have gotten simpler, smaller, and less expensive. Network monitors are now available for most environments, and they are very effective and easy to use.
Today network-monitoring systems usually consist of a PC with a NIC card and monitoring software. This monitoring software is menu-driven, is easy to use, and has a big help file. The traffic displayed by sniffers can become overly technical and require additional technical materials. You can buy these materials at most bookstores, or you can find it on the Internet for free. With a few hours of work, most people can make network monitors work efficiently and use the data they present.
Sniffer is a trade name like Kleenex. It's the most well-known network monitor, so everyone started calling network monitoring hardware "sniffers."
Intrusion Detection Systems
Intrusion Detection Systems (IDS) have been marketed as the ultimate and final answer to network security. An IDS is software that runs on either individual workstations or on network devices to monitor and track network activity. Using an IDS, a network administrator can configure the system to respond just like a burglar alarm in your building. IDS systems can be configured to evaluate systems logs, look at suspicious network activity, and disconnect sessions that appear to violate security settings.
The technology shows great promise, but it is still relatively new. Many vendors have oversold the simplicity of these tools. They are quite involved and require a great deal of planning and maintenance to work effectively. Many manufacturers are selling IDS systems with firewalls, and this area shows great promise. Firewalls by themselves will prevent many common attacks, but they do not usually have the intelligence or the reporting capabilities to monitor the entire network. An IDS, in conjunction with a firewall, allows both a reactive posture with the firewall and a preventative posture with the IDS. Figure 3.11 illustrates an IDS working in conjunction with a firewall to increase security.
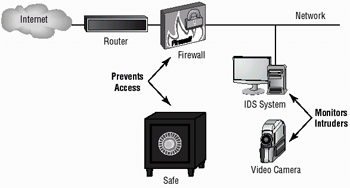
Figure 3.11: An IDS and a firewall working together to secure a network
In the event the firewall is compromised or penetrated, the IDS system can react by disabling systems, ending sessions, and even potentially shutting down your network. This provides a higher level of security than either device provides by itself. If it helps, think of the IDS/firewall combination as a camera and a safe. The safe prevents many burglars from gaining access, and the camera catches them in the act.
Workstations
Workstations are particularly vulnerable in a network. Most modern workstations, regardless of their operating systems, communicate using services such as file sharing, network services, and applications programs. Many of these programs have the ability to connect to other workstations or servers to work.
These connections are potentially vulnerable to interception and exploitation. The process of making a workstation or a server more secure is called platform hardening. The process of hardening the operating system is referred to as OS hardening. OS hardening is a part of platform hardening that deals only with the operating system. Platform hardening procedures can be categorized into three basic areas:
-
The first area to address is removing unused software, services, and processes from the workstations, (e.g., as the server service from a workstation). The services and processes may create opportunities for exploitation.
-
The second area involves ensuring that all services and applications are up-to-date (including available service and security packs) and configured in the most secure manner allowed. This may include assigning passwords, limiting access, and restricting capabilities.
-
The third area to address involves the minimization of information dissemination about the operating system, services, and capabilities of the system. Many attacks can be targeted at specific platforms once the platform has been identified. Many operating systems use default account names for administrative access. If at all possible, these should be changed.
Your Information Systems (IS) department is screaming about the amount of unauthorized software that is being installed on many of the Windows 2000 systems on your network. What advice can you offer them on how to minimize the impact of this software?
Many of the newer systems, such as Windows 2000, allow permissions to be established to prevent software installation. You would want to evaluate the capabilities of the settings in the workstations for security. This process is referred to as locking down a desktop. You can lock down most desktops to prevent the installation of software. This may also prevent users from automatically upgrading software, and it may create additional work for the IS department. You will need to evaluate both issues to determine what the best approach to take is.
Servers
Most modern server products also offer workstation functionality. In fact, many servers are virtually indistinguishable from workstations. Linux functions as both a workstation and a server in most cases. Windows 2000, while having multiple versions of workstation and server, communicates to networks in a virtually identical manner.
Most successful attacks against a server will also work against a workstation, and vice versa. Additionally, servers will run dedicated applications, such as SQL Server or a full-function web server.
| Note | An early version of IIS installed a default mail system as a part of its installation. This mail system was enabled unless specifically disabled. This mail server suffered from most of the vulnerabilities that were discussed in Chapter 2, "Know Your Enemy," as they related to virus and worm infections. Make sure that your system runs only the services, protocols, and processes that are needed. Turn off or disable things you do not need. |
Mobile Devices
Mobile devices, including pagers and Personal Digital Assistants (PDAs), are becoming very popular. Many of these mobile devices use either RF signaling or cellular technologies for communication. If the device uses the Wireless Applications Protocol (WAP), the device in all likelihood does not have security enabled. Several levels of security exist in the WAP protocol. These protocols include:
-
Anonymous authentication, which allows virtually anyone to connect to the wireless portal.
-
Server authentication, which requires the workstation to authenticate against the server.
-
Two-way (client and server) authentication, which requires both ends of the connection (client and server) to authenticate to confirm validity. Most newer palm systems are configured to allow authentication. This authentication can be configured to challenge the user of the device to log on, as well as allow the user to challenge the server.
Note WAP is covered in more detail in Chapter 4.
Many new wireless devices are also capable of using certificates to verify authentication. Figure 3.12 shows a mobile systems network. This network uses both encryption and authentication to increase security.
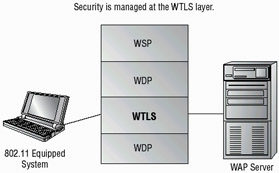
Figure 3.12: A mobile environment using WAP security
The Wireless Session Protocol (WSP) manages the session information and connection between the devices. The Wireless Transaction Protocol (WTP) provides services similar to TCP and UDP for WAP. The Wireless Datagram Protocol (WDP) provides the common interface between devices.
|
|
EAN: 2147483647
Pages: 167