Internet Connections
|
|
The Internet is perhaps the area of largest growth for networks. The Internet is a worldwide network that offers the capability of instantaneous connections between networks, no matter where they are located. The technology started as a research project funded by the Department of Defense and has grown at an enormous rate. Within a few years, virtually every computer in the world is expected to be connected to the Internet. This creates a security nightmare and is one of the primary reasons that the demand for professionals trained in information and computer security is expected to grow exponentially.
The following section describes some of the more common protocols including the World Wide Web, Telnet, FTP, e-mail, and SMTP.
| Note | The information on ports and sockets in this section is intended for background information and is not tested on the exam. |
Ports and Sockets
As you already know, the primary method of connection between systems using the Internet is the TCP/IP protocol. This protocol establishes connections and circuits using a combination of the IP address and a port. A port is an interface that is used to connect to a device. Sockets are a combination of the IP address and the port. If you attempt to connect to a remote system with the IP address 192.168.0.100 that is running a website, you will use Port 80 by default. The combination of these two elements gives you a socket. The full address and socket description would then be 192.168.0.100:80.
IP is used to route the information from one host to another through a network. The four layers of TCP/IP encapsulate the information into a valid IP packet that is then transmitted across the network. Figure 3.15 illustrates the key components of a TCP packet requesting the home page of a website. The data will be returned from the website to Port 1024 on the originating host.
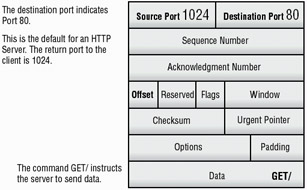
Figure 3.15: A TCP packet requesting a web page from a web server
The source port is the port that is being addressed on the destination. The destination port is the port to which the data will be sent. In the case of a WWW application, these would both contain 80. A number of the fields in this packet are used by TCP for verification and integrity and you need not be concerned with them at this time.
However, the data field contains the value Get /. This requests the home or starting page from the web server. In essence, this requested the home page of the site 192.168.0.100 Port 80. The data is formed into another data packet that is passed down to IP and sent back to the originating system on Port 1024.
The connections to most services using TCP/IP are based on this port model. Many of the ports are well documented, and the protocols to communicate with them are well known. If a vendor has a technological weakness or implements security poorly, the vulnerability will become well known and exploited in a short amount of time.
E-mail is one of the most popular applications in use on the Internet. Several very good e-mail servers and clients are available. Figure 3.16 demonstrates the process of transferring an e-mail message.
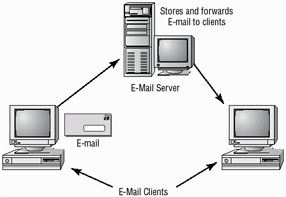
Figure 3.16: E-mail connections between clients and a server
The most common e-mail systems use SMTP, POP, or IMAP protocols. These protocols use the TCP protocol for session establishment:
Simple Mail Transport Protocol (SMTP) Simple Mail Transport Protocol (SMTP) is a mail delivery protocol that is used to send e-mail between an e-mail client and an e-mail server, as well as between e-mail servers. Messages are moved from client to server to client via the Internet. Each e-mail can take different paths from the client to the server. In this situation, the clients are on two different e-mail servers, they could both be on the same server and the process would appear transparent to the user. SMTP uses port 25 and TCP for connections.
Post Office Protocol (POP) Post Office Protocol (POP) is a newer protocol that relies on SMTP for message transfer for receiving e-mail. POP provides a message store that can be used to store and forward messages. If a server is not operating, the originating server can store a message and try to resend it later. POP3, the newest version of POP, allows messages to be transferred from the waiting post office to the e-mail client. The current POP standard uses port 109 for POP2 and 110 for POP3. The POP protocol uses TCP for connections.
Internet Message Access Protocol (IMAP) Internet Mail Access Protocol (IMAP) is the newest player in the e-mail field, and it is rapidly becoming the most popular. Like POP, IMAP has a store and forward capability. However, it has much more functionality. IMAP allows messages to be stored on an e-mail server instead of being downloaded to the client. IMAP allows messages to be downloaded based on search criteria. Many IMAP implementations also allow connection using web browsers. The current version of IMAP (IMAP 4) uses port 143 and TCP for connection.
| Note | S/MIME and PGP are two of the more popular methods of providing security for e-mails. These are covered in more detail in Chapter 8, "Cryptography Standards." |
E-Mail Vulnerabilities
E-mail accounts typically use a separate logon name and password from the OS-user ID and password. This somewhat minimizes the security risk, unless they are the same. The authentication information for e-mail is not always encrypted and is subject to sniffing. Further, the message is unencrypted and all contents are subject to exposure. If your e-mail servers are located in another facility and you use the Internet to communicate, your e-mails are very easily intercepted and read. If privacy is an issue, you will need to encrypt them using one of the packages or encryption schemes discussed later in this book.
| Note | Any misuse of corporate resources such as e-mail servers are considered security issues by most organizations. |
The following list describes some of the security risks your e-mail server can face:
Spam Spam refers to unsolicited junk mail received by most e-mail users today. The volume of unsolicited e-mail is growing, and entire industries have grown to advertise using e-mail. There is little you can do to stop spam. It appears in your e-mail like most other legitimate e-mail. You can think of this as the equivalent of junk mail in your mailbox. Preventative measures include installing spam filters on e-mail clients, spam filters on servers, and tough legislation about spam.
Many marketing companies send out thousands, if not millions, of e-mails a month attempting to sell you products and services. One of the dangers of spam is that attachments sent via spam may contain viruses or other malicious code.
Hoaxes Hoaxes are another annoying e-mail trend that is growing. From a security perspective, hoaxes include notification of new virus threats. These e-mails can be very convincing when they are received by unsuspecting users.
| Note | A large-scale hoax that is going around falsely notifies you that the e-mail sender has previously sent you a virus. The e-mail includes an attachment and directions that explain how to cure the virus. If you download and execute the supposed virus fix, you will inadvertently infect yourself with a virus or delete a required operating system file. This particular e-mail hoax has been causing havoc with help desks because the message is so convincing. |
Web
An earlier section provided an example of a web request between two hosts. The data that is returned from the host is returned using Hypertext Markup Language (HTML). HTML is nothing more than a coding scheme to allow text and pictures to be presented in a specific way in a web browser. HTML can be created any number of ways, including manual coding and in graphical design programs. These HTML files are read, interpreted by your browser, and displayed on your system. If you want to see what HTML looks like, you can set your browser to view source code. You will see things similar to a word processor coding for virtually every characteristic of the web page you are viewing.
Websites are nothing more than a collection of these pages, which are called into your browser when you hit a link or scroll through the pages. Most developers want more than the ability to display pages and pages of colored text on your computer. To make creative and sophisticated websites possible, web browsers have become more complicated, as have web servers. Current browsers include audio, visuals, animations, live chats, and almost anything else you can imagine. Figure 3.17 illustrates some of the content that can be delivered over the Internet via a web server.
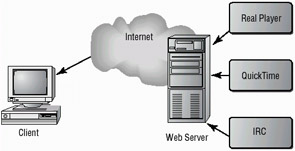
Figure 3.17: A web server providing streaming video, animations, and HTML data to a client
This capability is accomplished in one of several ways. The most common way involves installing applications that talk through the server to your browser. These applications require additional ports to be opened through your firewall and routers. Unfortunately, this inherently creates additional security vulnerabilities.
| Note | Each port you leave open in your network increases your vulnerability. If you open the ports necessary to use the popular program NetMeeting, you are exposing your users to additional opportunities for attack. NetMeeting has had a number of security vulnerabilities in the past, and it will probably have more in the future. |
Each of the popular services is now offered in conjunction with web-enabled programs such as Flash and Java. These services use either a socket to communicate or a program that responds to commands through the browser. If your browser can be controlled by an application, your system is at great risk of being coerced into giving the attacker information you did not want them to have. Servers are also vulnerable to this because they must process requests from browsers for information or data. A little research into the vulnerabilities of a proposed new service may save you a lot of time should you become the target of an attack.
Secure Web Connections
There are two common ways to provide secure connections between a web client and a web server. The most common methods are SSL/TLS and HTTP/S.
SSL/TLS Secure Socket Layer (SSL) and Transport Layer Security (TLS) are two common protocols used to convey information between a web client and a server. The SSL protocol uses an encryption scheme between the two systems. The client initiates the session, the server responds indicating that encryption is needed, and then they negotiate an appropriate encryption scheme. TLS is a newer protocol that merges SSL with other protocols to provide encryption. TLS supports SSL connections for compatibility, but it also allows other encryption protocols, such as Triple DES, to be used. SSL/TLS uses port 443 and TCP for connections.
HTTP/S HTTP Secure (HTTP/S) is a protocol that is used for secure connections between two systems using the Web. HTTP/S protects the connection between the two systems. All traffic between the two systems will be encrypted. HTTP/S uses SSL or TLS for connection security. HTTP/S uses port 443 and TCP for connections.
| Note | Do not confuse Secure HTTP (S-HTTP) with HTTP/S. S-HTTP is a different protocol. S-HTTP systems negotiate an encryption connection between each other. S-HTTP can provide some of the capabilities of HTTP/S, but it is not as secure. See Chapter 8, "Cryptography Standards," for more information. |
Web Vulnerabilities
The growth of the Web and user demands for more features have spurred the creation of a new set of vulnerabilities that must be evaluated and managed. Increasingly, web browsers and other web-enabled technologies allow servers to send instructions to the client to provide multimedia and other capabilities. This is creating a problem for security professionals because these various protocols offer potential vulnerabilities.
This section discusses the more common vulnerabilities that exist in web-based applications. These vulnerabilities include malicious code, viruses, and exploitations.
JavaScript
JavaScript is a programming language that allows access to system resources of the system running the script. These scripts can interface with all aspects of an operating system just like programming languages, such as the C language. This means that JavaScript scripts, when executed, can potentially damage systems or be used to send information to unauthorized persons. JavaScript scripts can be downloaded from a website and executed. A JavaScript script is a self-contained program that can be run as an executable file in many environments.
Java Applets
A Java applet is a small, self-contained Java script that is downloaded from a server to a client and then run from the browser. The client browser must have the ability to run Java applets in a virtual machine on the client. Java applets are used extensively in web servers today, and they are becoming one of the most popular tools used for website development.
Java-enabled applications have the ability to accept programmed instructions from a server. These applications can control certain aspects of the client environment. Java requires the downloading of a virtual machine to run the Java applications or applets. Java scripts run on the client. Many applications are Java-enabled, which means they have the ability to run Java scripts as part of their capabilities.
The applets run in a restricted area of memory called the sandbox. The sandbox limits the applet's access to user areas and system resources. An applet that runs in the sandbox is considered safe. A safe applet will not attempt to gain access to sensitive system areas. Errors in the Java virtual machine that runs in the applications may allow some applets to run outside of the sandbox. When this occurs, the applet is unsafe and may perform malicious operations. This weakness has been exploited by attackers on client systems.
Signed Applets
Signed applets are similar to Java applets—with one key difference. A signed applet does not run in the Java sandbox, and it has higher system access capabilities. Signed applets are not usually downloaded from the Internet. This type of applet is usually provided by in-house or custom-programming efforts. These applets can also include a digital signature to verify authenticity. If the applet is verified as authentic, it will be installed. Users should never download a signed applet unless they are sure that the provider is trusted. A signed applet from an untrustworthy provider has the same security risks as an unsigned applet.
Most web browsers have settings that can be used to control Java access. This allows clients to control resource access using Java applets or scripts.
ActiveX
ActiveX is a technology that was implemented by Microsoft. ActiveX allows customized controls, icons, and other features to increase the usability of web- enabled systems. ActiveX uses a method called authenticode for security. Authenticode is a type of certificate technology that allows ActiveX components to be validated by a server. ActiveX runs on the client.
ActiveX components are downloaded to the client hard disk, potentially allowing additional security breaches. Web browsers can be configured so that they require confirmation to accept an ActiveX control. Many users do not understand these confirmation messages when they appear, and they automatically accept the components. Automatically accepting an ActiveX component or control creates the opportunity for security breaches on a client system when the control is used. An ActiveX control contains programming instructions that can contain malicious code or create vulnerabilities in a system.
Buffer Overflows
Buffer overflows occur when an application receives more data than it is programmed to accept. This situation can cause an application to terminate. The termination may leave the system sending the data with temporary access to privileged levels in the attacked system. This exploitation is usually a result of a programming error in the development of the software. Buffer overflows are becoming less common because this exploit is now more known. Buffer overflows have been a major source of exploitation in the past, and they will probably continue to be exploited in the future.
Cookies
Cookies are text files that a browser maintains on the user's hard disk. A cookie will typically contain information about the user. Cookies are used to provide a persistent, customized web experience for each visit. A cookie can contain the history of a client to improve customer service. If a bookstore wants to know your buying habits and what types of books you last viewed at the bookstore, they can load this information into a cookie on your system. The next time you return to that store, the server can read your cookie and customize what it presents to you. Cookies can also be used to timestamp a user to limit access. A financial institution may send your browser a cookie once you have authenticated. The server can read the cookie to determine when a session is expired. Obviously, cookies are considered a risk because they contain your personal information. And if this information gets into the wrong hands, this is a potential security risk.
CGI
Common Gateway Interface (CGI) is an older form of scripting that was used extensively in early web systems. CGI scripts could be used to capture data from a user using simple forms. CGI scripts are not widely used in new systems and are being replaced by Java, ActiveX, and other technologies. The CGI script ran on the web server, and it interacted with the client browser. CGI is frowned upon in new applications because of its security issues, but it is still widely used in older systems.
SMTP Relay
SMTP relay is a feature designed into many e-mail servers that allows them to forward e-mail to other e-mail servers. Initially, the SMTP relay function was intended to help bridge between systems. This capability allows e-mail connections between systems across the Internet to be made easily. Unfortunately, this feature has been used to generate a great deal of spam on the Internet. An e-mail system that allows this type of forwarding to occur is referred to as an open relay. Open relays can be used by unscrupulous individuals to send advertisements and other messages through open relay servers. SMTP relaying should be disabled on your network unless it is limited to only the e-mail servers in your domain.
You have just received a call from a client indicating that their e-mail server is acting peculiarly. When you arrive at the site, you notice that there are over 20,000 e-mails in the outbound mail folder and that the system has no disk space available. When you shut down the e-mail software, you delete these files and restart the e-mail server. You notice that the outbound mail folder begins to fill up again. What problem could this server be encountering?
E-marketers may be using the server as a relay. This hijacking will continue until you disable the SMTP relay capabilities in the server. Many older systems do not allow SMTP relaying to be turned off. These servers will need to be upgraded or replaced to prevent this from continuing.
File Transfer Protocol
File Transfer Protocol (FTP) was the most common protocol used to transfer files between systems on the Internet for many years. FTP is available on most major server environments.
The WWW has replaced many of the functions that Telnet and FTP served in the past. FTP is still commonly used, but it is becoming less popular as other methods of file downloading are becoming available. Most popular browsers allow the connection to an FTP site to be accessed as a website, and HTTP supports file transfer capabilities. This provides a graphical interface that users can use without having to be exposed to the command structure that FTP uses by default.
This section discusses the FTP protocol, its vulnerabilities, and ways to secure it.
FTP Connections
FTP has three separate functions. FTP is a protocol, a client, and a server. The client system runs a program called FTP. The server runs a service called FTP server. The FTP client and server communicate using the FTP protocol. The client requests a connection to a server that runs the FTP service. The client and server communicate using a protocol that defines the command structure and interactions between the client and server.
Blind FTP/Anonymous
Early FTP servers did not offer security. Security was based on the honor system. Most logons to an FTP site used the anonymous logon. By convention, the logon ID was the user's e-mail address, and the password was anonymous. This honor system is still used in systems where public access to files is wanted. In this situation, the only security offered is what is configured by the operating system. In most cases, the honor system was used strictly for downloading files from an FTP server to a client. A client could not upload files without using a different logon ID.
Secure FTP
Secure FTP (S/FTP) is accomplished using a protocol called Secure Shell (SSH). As discussed earlier, SSH is a program that allows connections to be secured by encrypting the session between the client and the server. SSH is available for UNIX and other systems that provide similar capabilities to FTP. SSH is a type of tunneling protocol that allows access to remote systems in a secure manner.
File Sharing
File sharing is accomplished by storing files on an assigned location on the server or workstation. When files are stored on a workstation, the connection is referred to as a peer-to-peer connection. The assigned location is typically a subdirectory located on one of the disk drives on the server or another workstation. In an FTP connection, a file can be uploaded from a client using the PUT command. A download with FTP is accomplished using the GET command. Most modern servers and applications allow an application program to access shared files at the record level. This type of sharing allows multiuser applications, such as databases, to function. Web browsers typically accept files from a web server by downloading them from the server. These downloaded files are then processed through the browser and displayed to the user.
Vulnerabilities and Sniffing
FTP has a major flaw. The user ID and password are not encrypted and are subject to packet capture. This creates a major security breach—especially if you are connecting to an FTP server across the Internet.
Your organization has a large number of remote users who transfer files to your system across the Internet. These file transfers are essential parts of your business, and they must be allowed to continue. You want to provide additional security to your users so that information will not be compromised. How might you accomplish this?
You could implement SSH or other secure protocols for FTP file transfers. This would allow information to be sent across the Internet in a secure manner. You may also be able to use TLS, SSL, or other secure format to accomplish this.
|
|
EAN: 2147483647
Pages: 167
- Chapter III Two Models of Online Patronage: Why Do Consumers Shop on the Internet?
- Chapter IX Extrinsic Plus Intrinsic Human Factors Influencing the Web Usage
- Chapter X Converting Browsers to Buyers: Key Considerations in Designing Business-to-Consumer Web Sites
- Chapter XIV Product Catalog and Shopping Cart Effective Design
- Chapter XV Customer Trust in Online Commerce