Who Uses Network Analysis?
|
| < Day Day Up > |
|
System administrators, network engineers, security engineers, system operators, even programmers, all use network analyzers. Network analyzers are invaluable tools for diagnosing and troubleshooting network problems. Network analyzers used to be dedicated hardware devices that were very expensive. New advances in technology have allowed for the development of software network analyzers. This makes it more convenient and affordable for administrators to effectively troubleshoot a network. It also brings the capability of network analysis to anyone who wishes to perform it.
The art of network analysis is a double-edged sword. While network, system, and security professionals use it for troubleshooting and monitoring of the network, intruders can also use network analysis for harmful purposes. A network analyzer is a tool, and like all tools they can be used for both good and bad intentions.
The following list describes a few reasons why administrators use network analyzers:
-
Converting the binary data in packets to human-readable format
-
Troubleshooting problems on the network
-
Analyzing the performance of a network to discover bottlenecks
-
Network intrusion detection
-
Logging network traffic for forensics and evidence
-
Analyzing the operations of applications
-
Discovering a faulty network card
-
Discovering the origin of a Denial of Service (DoS) attack
-
Detecting spyware
-
Network programming to debug in the development stage
-
Detecting a compromised computer
-
Validating compliance with company policy
-
As an educational resource when learning about protocols
-
For reverse-engineering protocols in order to write clients and supporting programs
How are Intruders Using Sniffers?
When used by malicious individuals, sniffers can represent a significant threat to the security of your network. Network intruders often use network sniffing to capture valuable, confidential information. The terms sniffing and eavesdropping have often been associated with this practice. However, sniffing is now becoming a non-negative term and most people use the terms sniffing and network analysis interchangeably.
Using a sniffer in an illegitimate way is considered a passive attack. It does not directly interface or connect to any other systems on the network. However, the computer that the sniffer is installed on could have been compromised using an active attack. The passive nature of sniffers is what makes detecting them so difficult. We will discuss the methods used to detect sniffers later in this chapter.
The following list describes a few reasons why intruders are using sniffers on the network:
-
Capturing clear-text usernames and passwords
-
Compromising proprietary information
-
Capturing and replaying Voice over IP telephone conversations
-
Mapping a network
-
Passive OS fingerprinting
Obviously, these are illegal uses of a sniffer, unless you are a penetration tester whose job it is to find these types of weaknesses and report them to an organization.
For sniffing to occur, an intruder must first gain access to the communication cable of the systems that are of interest. This means being on the same shared network segment, or tapping into the cable somewhere between the path of communications. If the intruder is not physically present at the target system or communications access point, there are still ways to sniff network traffic. These include:
-
Breaking into a target computer and installing remotely controlled sniffing software.
-
Breaking into a communications access point, such as an Internet Service Provider (ISP) and installing sniffing software.
-
Locating/finding a system at the ISP that already has sniffing software installed.
-
Using social engineering to gain physical access at an ISP to install a packet sniffer.
-
Having an insider accomplice at the target computer organization or the ISP install the sniffer.
-
Redirecting communications to take a path that includes the intruder’s computer.
Sniffing programs are included with most rootkits that are typically installed on compromised systems. Rootkits are used to cover the tracks of the intruder by replacing commands and utilities and clearing log entries. They also install other programs such as sniffers, key loggers, and backdoor access software. Windows sniffing can be accomplished as part of some RAT (Remote Admin Trojan) such as SubSeven or Back Orifice. Often intruders will use sniffing programs that are configured to detect specific things, such as passwords, and then electronically send them to the intruder (or store them for later retrieval by the intruder). Vulnerable protocols for this type of activity include telnet, FTP, POP3, IMAP, SMTP, HTTP, rlogin, and SNMP.
One example of a rootkit is T0rnKit, which works on Solaris and Linux. The sniffer that is included with this rootkit is called t0rns and is installed in the hidden directory /usr/srec/.puta. Another example of a rootkit is Lrk5 (Linux Rootkit 5), which installs with the linsniff sniffer.
Intruders commonly use sniffer programs to control back doors. One method is to install a sniffer on a target system that listens for specific information. Then, backdoor control information can be sent to a neighboring system. The sniffer picks this up, and acts appropriately on the target computer. This type of backdoor control is often hard for investigators to detect, since it looks like the innocent neighbor system is the compromised target. cd00r is an example of a backdoor sniffer that operates in non-promiscuous mode, making it even harder to detect. Using a product like Nmap to send a series of Transmission Control Protocol (TCP) SYN packets to several predefined ports will trigger the backdoor to open up on a pre-configured port. More information about Cdoor can be found at www.phenoelit.de/stuff/cd00r.c.
| Note | A rootkit is a collection of trojan programs that are used to replace the real programs on a compromised system in order to avoid detection. Some common commands that get replaced are ps, ifconfig, and ls. Rootkits also install additional software such as sniffers. |
| Note | Nmap is a network scanning tool used for network discovery and auditing. It can send raw IP packets to destination ports on target systems. |
What does Sniffed Data Look Like?
We have done a lot of talking about sniffers and what they are used for, but the easiest way to grasp the concepts previously discussed is watching a sniffer in action. Figure 1.2 shows a capture of a simple FTP session from a laptop to a Sun Solaris system. The two highlighted packets show you just how easy it is to sniff the username and password. In this case, the username is “root” and the password is “password”. Of course, allowing root to FTP into a system is a very poor security practice; this is just for illustration purposes!
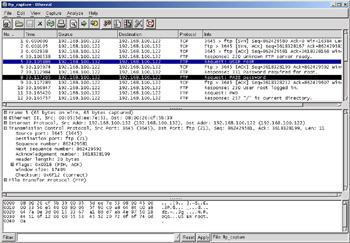
Figure 1.2: Example of Sniffing a Connection
Common Network Analyzers
A simple search on SecurityFocus (www.securityfocus.org/tools/category/4) shows the diversity and number of sniffers available. Some of the most prominent ones are:
-
Ethereal Of course, this one is the topic of this book! Ethereal is obviously one of the best sniffers available. It is being developed as a free commercial quality sniffer. It has numerous features, a nice graphical user interface (GUI), decodes for over 400 protocols, and it is actively being developed and maintained. It runs on both UNIX-based systems and Windows. This is a great sniffer to use, even in a production environment. It is available at www.ethereal.com.
-
WinDump This is the Windows version of tcpdump available at http://windump.polito.it. It uses the WinPcap library and runs on Windows 95/98/ME/NT/2000/XP.
-
Network Associates Sniffer This is one of the most popular commercial products available. Now marketed under McAfee Network Protection Solutions, Network Associates has an entire Sniffer product line for you to peruse at www.nai.com.
-
Windows 2000/NT Server Network Monitor Both Windows 2000 Server and NT Server have a built-in program to perform network analysis. It is located in the Administrative tools folder, but is not installed by default, so you may have to add it from the installation CD.
-
EtherPeek This is a commercial network analyzer by WildPackets. There are versions for both Windows and Mac, as well as other network analysis products that can be found at www.wildpackets.com.
-
Tcpdump This is the oldest and most common network sniffer. The Network Research Group (NRG) of the Information and Computing Sciences Division (ICSD) at Lawrence Berkeley National Laboratory (LBNL) developed tcpdump. It is command line-based and runs on UNIX-based systems. It is being actively developed and maintained at www.tcpdump.org.
-
Snoop This command line network sniffer is included with the Sun Solaris operating system. It is especially competent at decoding Sun-specific protocols.
-
Sniffit This network sniffer runs on Linux, SunOS, Solaris, FreeBSD and IRIX. It is available at http://reptile.rug.ac.be/~coder/sniffit/sniffit.html.
-
Snort This is a network intrusion detection system that uses network sniffing. It is actively developed and maintained at www.snort.org. For more information, refer to Snort 2.0:Intrusion Detection (Syngress Publishing, ISBN: 1-931836-74-4)
-
Dsniff This is very popular network sniffing package. It is a collection of programs to sniff specifically for interesting data such as passwords, and to facilitate the sniffing process such as evading switches. It is actively maintained at www.monkey.org/~dugsong/dsniff.
-
Ettercap This sniffer is designed specifically to sniff in a switched network. It has built-in features such as password collecting, OS fingerprinting, and character injection. It runs on several platforms including Linux, Windows, and Solaris. It is actively maintained at http://ettercap.sourceforge.net.
-
Analyzer This is a free sniffer for the Windows OS that is being actively developed by the makers of WinPcap and WinDump at
-
Politecnico di Torino. It can be downloaded from http://analyzer.polito.it.
-
Packetyzer This is a free sniffer for the Windows OS that uses Ethereal’s core logic. It tends to run a version or two behind the current release of Ethereal. It is actively maintained by Network Chemistry at www.networkchemistry.com/products/packetyzer/index.html.
Carnivore or Vegetarian?
No talk about network analyzers would be complete without the mention of Carnivore. While certainly not a commonly used network analyzer, it has created a lot of talk in the security world as well as the media. Carnivore is the code name for the FBI’s network analyzer. It is used to monitor relevant communications among selected individuals as part of a criminal investigation. Its name has been changed to DCS100 in an attempt to obscure its image and to calm the public’s fear of its misuse. When necessary, federal agents will arrive at a suspect’s ISP with a “black box”, which is merely a dedicated server running Windows 2000 or NT and the FBI’s Carnivore software preloaded. The server is placed on the ISP’s trunk to read header information for any traffic going to or coming from the suspect. This was rather common at numerous ISPs after September 11, 2001.
Many people have been concerned about the use of Carnivore and its ability to intercept all traffic, mostly due to privacy issues. They are concerned about how Carnivore works, how it could be misused by law enforcement, and the privacy debate over cable taps in general.
Carnivore is an Internet wiretap designed by the U.S. Federal Bureau of Investigation (FBI). It is designed with the special needs of law enforcement in mind. For example, some court orders might allow a pen-register monitoring of just the From/To e-mail addresses, whereas other court orders might allow a full capture of the e-mail. A summary of Carnivore’s features can be seen within the configuration program shown in Figure 1.3.
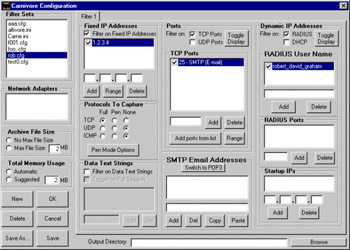
Figure 1.3: Carnivore Configuration Program
The features are:
-
Filter sets The settings are saved in configuration files; the user can quickly change the monitoring by selecting a different filter set.
-
Network adapters A system may have multiple network adapters; only one can be selected for sniffing at a time.
-
Archive file size A limit can be set on how much data is captured; by default, it fills up the disk.
-
Total memory usage Network traffic may come in bursts faster than it can be written to disk; memory is set aside to buffer the incoming data.
-
Fixed IP address All traffic to/from a range of IP addresses can be filtered. For example, the suspect may have a fixed IP address of 1.2.3.4 assigned to their cable modem. The FBI might get a court order allowing them to sniff all of the suspect’s traffic.
-
Protocols to capture Typically, a court order will allow only specific traffic to be monitored, such as SMTP over TCP. In Pen mode, only the headers are captured.
-
Data text strings This is the Echelon feature that looks for keywords in traffic. A court order must specify exactly what is to be monitored, such as an IP address or e-mail account. Such wide-open keyword searches are illegal in the United States. The FBI initially denied that Carnivore had this feature.
-
Ports A list of TCP and UDP ports can be specified. For example, if the FBI has a court order allowing e-mail capture, they might specify the e-mail ports of 25 (SMTP), 110 (POP3), and 143 (IMAP).
-
SMTP e-mail addresses A typical scenario is where Carnivore monitors an ISPs e-mail server, discarding all e-mails except those of the suspects. An e-mail session is tracked until the suspect’s e-mail address is seen, then all the packets that make up the e-mail are captured.
-
Dynamic IP addresses When users dial up the Internet, they are logged in via the RADIUS protocol, which then assigns them an IP address. Normally, the FBI will ask the ISP to reconfigure their RADIUS servers to always assign the same IP address to the suspect, and will then monitor all traffic to/from that IP address. Note: if you are a dial-up user and suspect the FBI is after you, check to see if your IP address is the same every time you dial up. Sometimes this isn’t possible. Carnivore can be configured to monitor the RADIUS protocol and dynamically discover the new IP address assigned to the suspect. Monitoring begins when the IP address is assigned, and stops when it is unassigned.
The FBI developed Carnivore because other existing utilities do not meet the needs of law enforcement. When an e-mail is sent across the wire, it is broken down into multiple packets. A utility like mailsnarf will reassemble the e-mail back into its original form. This is bad because the suspect’s defense attorneys will challenge its accuracy: Did a packet get dropped somewhere in the middle that changes the meaning of the e-mail? Did a packet from a different e-mail somehow get inserted into the message? By capturing the raw packets rather than reassembling them, Carnivore maintains the original sequence numbers, ports, and timestamps. Any missing or extra packets are clearly visible, allowing the FBI to defend the accuracy of the system.
Another problem that the FBI faces is minimization of the sniffed data. When the FBI wiretaps your line, they must assign an agent to listen in. If somebody else uses your phone (like your spouse or kids), they are required to turn off the tape recorders. In much the same way, Carnivore is designed to avoid capturing anything that does not belong to the suspect. A typical example would be using Carnivore to monitor the activities of a dial-up user. Carnivore contains a module to monitor the RADIUS traffic that is used by most ISPs to authenticate the user and assign a dynamic IP address. This allows Carnivore to monitor only that user without intercepting any other traffic.*
The following websites have more information on Carnivore:
-
www.fbi.gov
-
www.robertgraham.com/pubs/carnivore-faq.html
-
www.stopcarnivore.org
*Excerpt from Robert Graham’s chapter in Hack Proofing Your Network, Second Edition. Syngress Publishing 1-928994-70-9.
|
| < Day Day Up > |
|
EAN: 2147483647
Pages: 105