Remote Access Trojans
|
| < Day Day Up > |
|
The term trojan horse originally came from the Greek epic poem the Iliad, by Homer. In the story of the Trojan war, the Greeks left a large wooden horse as an apparent peace offering to the Trojans. Once the horse was brought inside the city walls of Troy, the Greek soldiers that were hiding inside of the hollow horse emerged and assisted in capturing the city. In the information security field, trojans are malicious programs that are often disguised as other programs such as jokes, games, network utilities, and sometimes even the trojan removal program itself! Trojans are often used to distribute backdoor programs without the victim being aware that they are being installed. Backdoors operate in a client-server architecture and allow the intruder to have complete control of a victim’s computer, remotely over the network. They give an intruder access to just about every function of the computer including logging keystrokes, activating the webcam, logging passwords, uploading and downloading files, and much, much more. They even have password protection and encryption features for intruders to protect the computers they own! There are hundreds, maybe even thousands, of trojan programs circulating the Internet, usually with many variations of the code. This makes them very difficult to detect with antivirus software.
In this section we will be using Scan2.log that was provided by the Honeynet Research Alliance as part of the Honeynet Project Scan of the Month challenge. Scan2.log is located on the accompanying CD-ROM in the /captures directory. We will also be using our own, lab-created backdoor packet captures called subseven_log and netbus_log, also located on the accompanying CD-ROM in the /captures directory.
SubSeven Legend
SubSeven Legend (also referred to as SubSeven) is one of the most common Windows backdoor trojans. It is an older program and most virus software can detect it, but there are many variations of it floating around the Internet. SubSeven is smart enough to notify the intruder, via Internet Relay Chat (IRC), e-mail, or some other method, that the victim computer is online. It runs over a TCP connection with a default port of 27374, although this port is configurable. SubSeven has numerous features that allow the intruder to completely control the victim computer.
Figure 8.6 shows a packet capture of a SubSeven Legend client-server interaction. SubSeven Legend is the anniversary edition of SubSeven. The intruder is running the client on 192.168.1.1, which is connected to the server on the victim computer at 192.168.1.200. You will notice that the server is running on the default port 27374 and data is being pushed between the client and server.
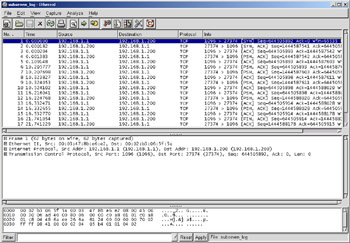
Figure 8.6: SubSeven Legend Backdoor Trojan
Using the Follow TCP Stream feature of Ethereal will show what is going on between the SubSeven server and client. Figure 8.7 shows the connection day and time and the version of the SubSeven server. Next, it shows that the intruder performed a directory listing of C:\, and downloaded the file secret.txt. However, the data for this file is obscured.
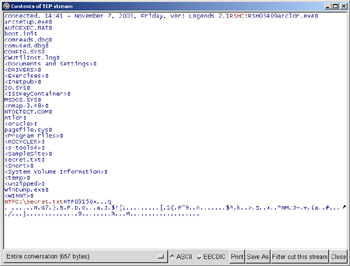
Figure 8.7: SubSeven Client-Server Interaction
NetBus
The NetBus backdoor trojan is also one of the older and more common Windows backdoor trojans. It is easily detectable using antivirus software, but like SubSeven, many variations exist. It runs over a TCP connection with default ports of 12345 and 12346, but is configurable. Like SubSeven it has numerous features that allow the intruder to completely control the victim computer.
Figure 8.8 shows a packet capture of a NetBus client-server interaction. The intruder is running the client on 192.168.1.1, which is connected to the server on the victim computer at 192.168.1.200. You will notice that the server is running on the default ports 12345 and 12346 and data is being pushed between the client and server. The two separate source ports indicate two distinct TCP connections.
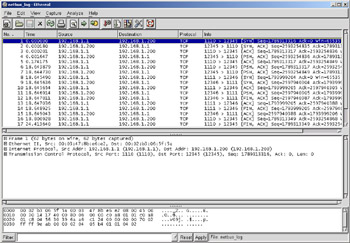
Figure 8.8: NetBus Backdoor Trojan
Using the Follow TCP Stream feature of Ethereal will show what is going on between the NetBus server with the port 12345 and the client. Figure 8.9 shows the version of the NetBus server and also shows that the intruder downloaded the file C:\temp\secret.txt. Figure 8.10 shows the client revealing the contents of the downloaded file! This means that not only the intruder, but anyone else on the line with a sniffer, can read the contents of the file as it is transmitted.
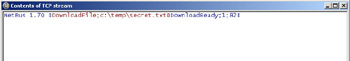
Figure 8.9: NetBus Client-Server Interaction

Figure 8.10: NetBus Client-Server Content
RST.b
RST.b is a newer, less widely used, backdoor access trojan that affects various Linux platforms. The backdoor listens in promiscuous mode for User Datagram Protocol (UDP) packets to any port. To access the backdoor, the intruder sends a UDP packet containing the payload “DOM”. There is more information on this backdoor at www.qualys.com/alert/remoteshellb.html.
Figure 8.11 shows a packet capture of an intruder scanning for systems infected with the RST.b trojan. We filtered on UDP to focus in on the last nine UDP packets. The intruder uses different source IP addresses and random destination ports to prevent IDSs from detecting the scan. Because the RST.b trojan listens in promiscuous mode, it will respond to UDP packets, containing the “DOM” payload, on any port.
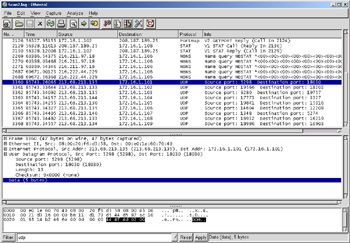
Figure 8.11: RST.b Backdoor Scan
Trojans, Viruses, and Worms: What is the difference?
Many people get confused over the difference between a virus, a worm, and a trojan. The terms tend to be used interchangeably, but they are really three very distinct entities. They each use different ways to infect computers, and each has different motivations behind its use.
A virus is a program that can infect files by attaching to them, or replacing them, without the knowledge of the user. A virus can execute itself, and replicate itself to other files within the system. To do this, it often attaches to executable files, known as host files. Viruses travel from computer to computer when users transmit infected files or share storage media, such as a floppy disk. Viruses may be benign or malicious. A benign virus does not have any destructive behavior; it presents more of an annoying or inconvenient behavior, such as displaying messages on the computer at certain times. A benign virus still consumes valuable memory, CPU time, and disk space. Malignant viruses are the most dangerous because they can cause widespread damage, such as altering software and data, removing files or erasing the entire system. However, there are no viruses that can physically damage your computer hardware. There are several types of viruses, including the following:
-
File infector A virus that attaches to an executable file.
-
Boot sector A virus that places code in the boot sector of a computer so that it is executed every time the computer is booted.
-
Master boot record A virus that infects the first physical sector of all disks.
-
Multi-partite A virus that will use a number of infection methods.
-
Macro A virus that attaches itself to documents in the form of macros.
A trojan is a program that is covertly hiding another, potentially malicious, program. The trojan is often created to appear as something fun or beneficial, such as a game or helpful utility. However, when a user executes the program, the hidden malicious program is also executed without the user’s knowledge. The malicious program is then running in memory and could be controlling backdoor access for the intruder, or destroying system files or data. A trojan could also contain a virus or a worm. Trojans do not replicate or propagate themselves; they are often spread by unknowing users who open an e-mail attachment to execute a file downloaded from the Internet.
A worm is a program much like a virus that has the added functionality of being able to replicate itself without the use of a host file. With a worm, you don’t have to receive an infected file, or use an infected floppy to become infected; the worm does this all on its own. A worm actively replicates itself and propagates itself throughout computer networks. Not only will a worm consume valuable system resources, it can also consume network bandwidth while it is propagating or attempting to propagate.
|
| < Day Day Up > |
|
EAN: 2147483647
Pages: 105