Scanning
|
| < Day Day Up > |
|
Network scanning is used to identify available network resources. Also known as discovery or enumeration, network scanning can be used to discover available hosts, ports, or resources on the network. Once a vulnerable resource is detected it can be exploited and the device compromised. Sometimes there is an actual intruder behind the scanning and sometimes it is a result of worm activity. We will be focusing on active intruder scanning in this section, while worm activity will be covered in a later section. Security professionals also use network scanning to assist in securing and auditing the network. In this section we will be using Scan1.log, which contains several different types of scans and was provided by the Honeynet Research Alliance as part of the Honeynet Project Scan of the Month challenge. Scan1.log is located on the accompanying CD-ROM in the /captures directory.
| Note | The Transmission Control Protocol (TCP) protocol is connection-oriented and is initialized by completing a 3-way handshake. The TCP 3-way handshake consists of an initial packet sent with the SYN flag, a return packet with both the SYN and ACK flags, and completed with a packet with an ACK flag. |
TCP Connect Scan
The first scan that we will be analyzing is the TCP Connect scan. It is used to determine which ports are open and listening on a target device. This is the most basic form of scanning because it completes the TCP 3-way handshake with open ports, and immediately closes them. An intruder sends a SYN packet and analyzes the response. A response packet with the Reset (RST) and Acknowledgment (ACK) flags set indicates the port is closed. If a SYN/ACK is received it indicates that the port is open and listening. The intruder will then respond with an ACK to complete the connection followed by a RST/ACK to immediately close the connection. This aspect of the scan makes it easily detectable because the connection attempts error messages will be logged.
Figure 8.1 shows the attacker, 192.168.0.9, sending SYN packets to the target, 192.168.0.99. Most ports respond with a RST/ACK packet, however the highlighted packets show the SYN/ACK response, and subsequent ACK followed by the RST/ACK, exchanged on the domain name system (DNS) port. You will also notice that the intruder’s source port increases by one for each attempted connection.
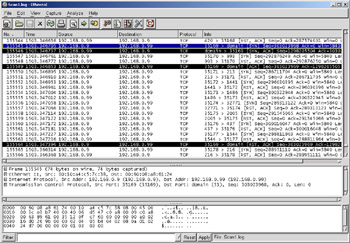
Figure 8.1: TCP Connect Scan
Figure 8.2 shows the active ports on the target device. You can find these by using a filter such as tcp.flags.syn==1&&tcp.flags.ack==1 or tcp.flags==18, to view packets with the SYN and ACK flags set. The filter will show multiple responses for each port, as several scanning methods were used. We removed the duplicates by saving the marked packets to a file.
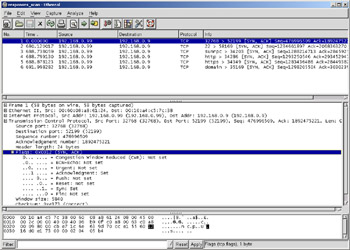
Figure 8.2: SYN/ACK Responses
| Note | The filter tcp.flags==18 will display packets with the SYN and ACK flags set because the binary value of the TCP flags field of a SYN/ACK packet is 00010010, which equals 18 in decimal format. |
SYN Scan
The next scan that we will be analyzing is a TCP SYN scan, also known as a half-open scan because a full TCP connection is never completed. It is used to determine which ports are open and listening on a target device. An intruder sends a SYN packet and analyzes the response. If an RST/ACK is received it indicates the port is closed. If a SYN/ACK is received it indicates that the port is open and listening. The intruder will then follow with an RST to close the connection. SYN scans are known as stealth scans because not as many devices will notice or log them, as they never create a full connection. However, many current firewalls and Intrusion Detection Systems (IDSs) will notice this type of activity.
In Figure 8.3, the attacker, 192.168.0.9, is sending SYN packets to the target, 192.168.0.99. Most ports respond with an RST/ACK packet, however the highlighted packets show the SYN/ACK response, and subsequent RST exchange on the https port. You will also notice that the intruder is using a somewhat static pair of source ports, 52198 and 52199.
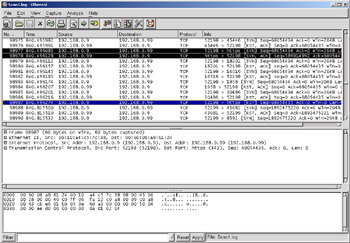
Figure 8.3: SYN Scan
Xmas Scan
The Xmas scan determines which ports are open by sending packets with invalid flag settings to a target device. It is considered a stealth scan because it may be able to bypass some firewalls and IDSs more easily than the SYN scans. This Xmas scan sends packets with the Finish (FIN), Push (PSH), and Urgent (URG) flags set. Closed ports will respond with an RST/ACK and open ports will drop the packet and not respond. However, this type of scan will not work against systems running Microsoft Windows, Cisco, BSDI, HP/UX, MVS, and IRIX. They will all respond with RST packets, even from open ports.
Notice in Figure 8.4 that the attacker, 192.168.0.9, is sending packets to the target 192.168.0.99 with the FIN, PSH, and URG flags set. Most ports respond with an RST/ACK packet, however the highlighted packet for the sunrpc port never receives a response. This is an indication that the port is open and has dropped the packet. You will also notice that the intruder is using decoy addresses of 192.168.0.1, 192.168.0.199, and 192.168.0.254. Decoy addresses are often used to obscure the real intruder’s Internet Protocol (IP) address making it harder to track down the real source of the scan. Looking closely at those packets reveals the same Media Access Control (MAC) address for all IP addresses. You will also notice that the intruder is using a somewhat static pair of source ports, 35964 and 35965.
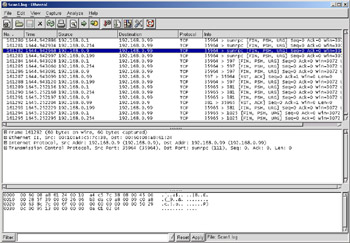
Figure 8.4: Xmas Scan
Null Scan
The Null scan determines which ports are open by sending packets with invalid flag settings to a target device. It is considered a stealth scan because it may be able to bypass some firewalls and IDSs easier than the SYN scans. This Null scan sends packets with all flags turned off. Closed ports will respond with an RST/ACK and open ports will drop the packet and not respond. However, this type of scan will not work against systems running Microsoft Windows, Cisco, BSDI, HP/UX, MVS, and IRIX. They will all respond with RST/ACK packets, even from open ports.
In Figure 8.5, the attacker, 192.168.0.9, is sending packets to the target 192.168.0.99 with all flags turned off, as indicated by the empty brackets []. Most ports respond with an RST/ACK packet, however the highlighted packet for the https port never receives a response. This is an indication that the port is open and has dropped the packet. Notice that the intruder is using a somewhat static pair of source ports, 42294 and 42295.
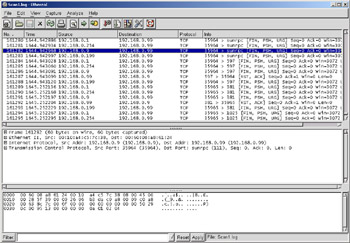
Figure 8.5: Null Scan
|
| < Day Day Up > |
|
EAN: 2147483647
Pages: 105