Attack
| | ||
| | ||
| | ||
Now that we have attack profiles created for each of our systems, we have the ability to conduct our series of mock attacks to find vulnerabilities within the infrastructure. If you remember from Chapter 13, the sequence conducted during our attack is
-
Attack
-
Validate results
-
Prioritize findings
-
Prepare for remediation
VA tools are generally used to conduct the bulk of the automated attacks during vulnerability assessments. The VA tools are configured based on the attack profiles built to maximize effectiveness. Once those attacks are complete, other tools (as well as human interpretation) are used to validate what has been found. All of this work allows you to find your vulnerabilities and prepare yourself for remediation tactics.
Vulnerability Assessment Tools
Vulnerability assessment tools are used to assist in automating the lengthy host analysis that must be conducted on each host. Most comprehensive VA tools include checks for over 2500 vulnerabilities. It is important to build and maintain accurate attack profiles before using VA tools because it would be extremely inefficient to check all vulnerabilities against every system (since many vulnerabilities are specific to certain platforms). As seen in the attack profiling section, narrowing your attack to only pertinent applications and services significantly reduces the amount of time required to complete host analysis with VA tools.
Most VA tools also contain other tools as well as port scanners and other information-gathering tools. Many VA tools build upon each other when included as packages. For example, Nessus contains support for NMAP to complete port scans and also has the ability to configure and run Nikto, a scanner specializing in testing web servers for vulnerabilities.
| Note | In the near future, we expect leaps and bounds to be made in the area of interoperability between vulnerability assessment tools through the introduction of (and compatibility with) OVAL, the Open Vulnerability and Assessment Language. You can find out more about OVAL at http://oval.mitre.org. |
Unfortunately, there are simply too many VA tools to describe here. We recommend you evaluate them all and select the right one for your environment. A number of commercial tools exist with varying levels of sophistication. For the purposes of this chapter, the theory is more important than the implementation, so we'll be using a ubiquitously available VA tool, Nessus.
Nessus
Nessus is an open source vulnerability scanner. As already mentioned, Nessus contains support for NMAP (or a built-in mechanism) to conduct preliminary port scanning. This feature is included to make the information-gathering phase more efficient. The Nessus vulnerability scanner is provided as a framework and has modular "plug-ins" that are used for checking vulnerabilities on target hosts . The plug-ins are written in Nessus Attack Scripting Language (NASL). The scanner is configured for the appropriate IP addresses to scan, the number of simultaneous connections, type of port scan, aggressiveness of scan, attack options to use, and more. Nessus is rated as one of the top vulnerability scanners available and can be used free of charge.
Recently, the maintainers of Nessus changed the policy on obtaining plug-ins. There are now three options for obtaining plug-ins:
-
Direct Feed This feed is commercially available and allows access to the latest vulnerability plug-ins. This feed is a pay-for-use feed with an annual maintenance cost.
-
Registered Feed This feed is free for public use; however, vulnerability plug-ins are available on a seven-day delay after being made available to the Direct Feed. The Registered Feed requires organizations to register with the Nessus maintainers and provide a signed agreement (providing contact information and agreement to the terms of use).
-
GPL Feed There is no cost and no registration required for organizations using the GPL feed. The plug-ins included in the GPL feed include those from the user community (which are also included in the Direct and Registered Feeds).
With an estimated 75,000+ organizations using Nessus, it is no wonder the package is endorsed by some of the largest security firms in the world. There are several other vulnerability assessment tools available through open source licensing as well as commercially. Several product comparison reviews conducted state that Nessus is very competitive in providing functionality, features, and stability.
Nessus server runs natively on various UNIX platforms and is not immediately available (to compile/build) on Windows (although Nessus clients are available for Windowsthey connect to a Nessus server running on another operating platform). The following options are available when running Nessus:
root@scanner:~# nessus - -help nessus, version 2.0.12 Common options : nessus [-vnh] [-c .rcfile] [-V] [-T <format>] Batch-mode scan: nessus -q [-pPS] <host> <port> <user> <pass> <targets-file> <result-file> List sessions : nessus -s -q <host> <port> <user> <pass> Restore session: nessus -R <sessionid> -q <host> <port> <user> <pass> <result-file> Report conversion : nessus -i in. [nsrnbe] -o out. [htmlxmlnsrnbe] General options : -v : shows version number -h : shows this help -n : No pixmaps -T : Output format: 'nbe', 'html', 'html_graph', 'text', 'xml', 'old-xml' 'tex' or 'nsr' -V : make the batch mode display status messages to the screen. -x : override SSL "paranoia" question preventing nessus from checking certificates. The batch mode (-q) arguments are : host : nessusd host port : nessusd host port user : user name pass : password targets : file containing the list of targets result : name of the file where nessus will store the results -p : obtain list of plugins installed on the server. -p : obtain list of server and plugin preferences. -S : issue SQL output for -p and -P (experimental). root@scanner:~#
In most cases, the command line options available in Nessus are not going to provide enough flexibility to conduct attacks based on your attack profiles. Nessus has the ability to build attack configurations and save them in configuration files. In doing so, you have much more flexibility and many more options than you would conducting the attack scans from a command line only.
There are some potential concerns when using Nessus even with configuration files. One of the main concerns is configuring the Nessus modules you will use for your attack(s). There are literally thousands of modules, each with a unique NessusID for tracking. The configuration file uses the NessusIDs to enable and disable modules. Without knowing these module IDs, you will have to have some sort of reference to them.
The simplest form of configuring Nessus is through the client's graphical user interface. Client/graphical user interfaces are available in several different UNIX flavors (to include options such as Gnome and MacOS X). Additionally, there is a Windows client available that can be used to access any Nessus server (remember, the Nessus server cannot run on Windows natively). The name of the Windows client, shown here, is NessussWX and it is also developed by the Nessus maintainers and available under open source licensing.
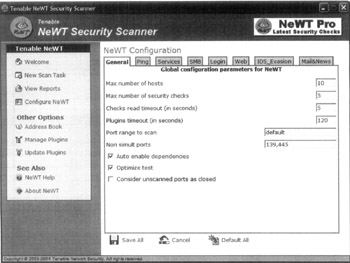
For stringent Windows users, there is a Windows build/version of Nessus called NeWT (Nessus Windows Technology). It is developed by Tenable, who is also responsible for the Nessus open source project. The basic NeWT package can only scan the subnet to which the host machine belongs (and is limited to a /24 net block or 255 addresses). This is designed for personal and small business use. NeWT Pro is a commercial version that does not contain scanning limitations but also requires purchase. This version is intended for enterprise vulnerability scanning, security firm usage, and other uses where NeWT may be limited. In addition to scanning capabilities, NeWT (or NeWT Pro) also includes the ability to provide login information (by providing proper credentials during prescan configurations) and check system patch levels on many of the more popular operating systems. The following illustration shows the NeWT user interface.
Whatever your background (and need), Tenable will most likely have a product to fit your needs. Even if you are a "Windows shop" and do not use UNIX, Nessus (through the use of NeWT) can be your main VA tool used during your attack(s).
A Nessus configuration file has been created to complete the analysis of the Acme web server used as the example during our mock assessment. We have configured Nessus to conduct another port scan (better safe than sorry as long as we can afford the additional time and resource allocations ). Also, since we know the server is acting as a web server, in addition to the various configuration options and Nessus modules we have chosen , we also have decided to run the Nikto plug-in included with Nessus (again, Nikto is a VA tool specifically designed for testing/analyzing web servers).
Validation Tools
Once you have conducted various attacks and scans with your VA tool, you will need to research its findings and validate any vulnerabilities found. The human interpretation of the VA tool findings is one of the most important aspects of your vulnerability assessment. False positives must be found and research conducted to determine what is causing them. Actual vulnerabilities must be validated and remediation plans set into action. In order to validate findings, several of the tools already discussed can be used.
There are obviously too many vulnerabilities (and false positives) to discuss each one here; however, the important thing to remember is that if your VA tool found a problem, there is something causing it to flag that problem. Research the finding, determine its validity (or root cause analysis), and set a course of action (to include prioritizing and eventually remediation). Some of the toolssuch as LFT, hping2, nemesis, AMAP, and morecan be used to continue validations based on VA tool findings.
| | ||
| | ||
| | ||
EAN: 2147483647
Pages: 120