Defenses and Remediation Tools
| | ||
| | ||
| | ||
The tools available for conducting assessments help you find vulnerabilities, but there are also tools available to help remediate vulnerabilities once they are identified (or be proactive and use the tools before vulnerabilities are found). Many of these tools are used for a very specific purpose and it would be impossible to list all of them here, but a few have been chosen that should be well known to most security analysts.
Patch Management Software
Without mentioning specific software packages, patch management software should be capable of keeping systems up to date with vendor-supplied system and/or application patches. There are commercial packages as well as many free packages available with a multitude of options available. For more information on patch management, please see Chapter 12.
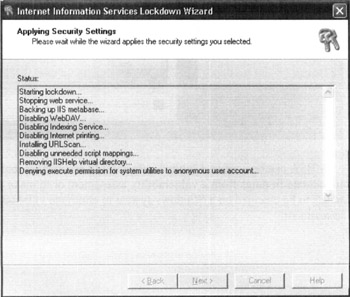
IISLockDown
IISLockDown is a free tool provided by Microsoft to assist analysts in "locking down" Microsoft Internet Information Server (IIS) Versions 4.0 and 5.0. The tool uses a wizard to ask administrators questions about the web server being locked down in order to determine its basic role. Once the web server's role is defined, the tool then runs a series of hardening steps (based on the input regarding type of web server role) to reduce the web server's risk footprint. The screenshot at right was taken of the IISLockdown tool as it was in the process of locking down a basic web server serving static content (one of the template options).
Microsoft Baseline Security Analyzer (MBSA)
This tool is used to analyze all Microsoft products loaded on a Windows host. In addition to the operating system (Windows 2000 or above), the Microsoft applications such as Microsoft Exchange, SQL, Sharepoint, and others all are checked for various patch levels, permissions, and other security checks. This tool can be run on multiple systems, but the source host must be within the same Windows domain or workgroup as its remote targets. The following is a screenshot of MBSA showing its output once it has completed a scan of a single host. To demonstrate critical vulnerability reporting, two Microsoft Office patches were not installed on the target system.
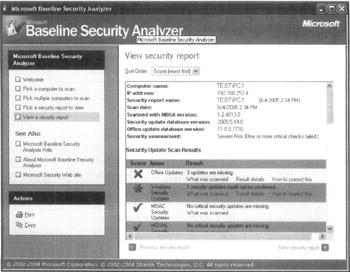
MBSA can be used as a limited vulnerability assessment tool but also can be used to validate findings from a vulnerability assessment or to make determinations of what needs to be changed on a Windows system to eliminate vulnerabilities found during an assessment.
| | ||
| | ||
| | ||
EAN: 2147483647
Pages: 120