Migration Tools
| < Day Day Up > |
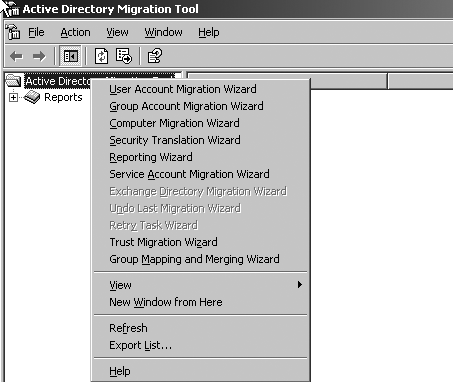
| Whether you are using the restructure method to migrate an entire domain structure or just need to migrate from another Windows 2000 or Windows Server 2003 forest, a number of tools are available. Microsoft provides the free ADMT included on the Windows 2003 CD. The following section identifies significant features in ADMT 2.0 that was released with Windows Server 2003. Other tools from third-party vendors are listed with a basic description and a pointer to the vendor's Web site. Because these tools change often, the vendor sites will be updated, whereas the printed information here will be quickly dated. ADMTWhen Windows 2000 was still in beta, Microsoft realized one of the major obstacles Windows NT customers would face would be migrating users, computers, and groups from the Windows NT environment to Windows 2000. Microsoft was up front in admitting it didn't have time or resources to develop sophisticated tools and partnered with several third-party developers to create those tools. Microsoft did provide some simplistic migration tools, including Cloneprincipal and ADMT. Mission Critical Software (now NetIQ ) created ADMT as a subset of its migration tool. Although ADMT was limited in functionality, it did have its place in small migrations and moving security principals between domains and forests. note ADMT v2 is available on the Windows Server 2003 CD in \i386\ADMT and from Microsoft's download site at http://www.microsoft.com/downloads. It's listed in the Tools and Add-Ins section. ADMT v2 can migrate security principals from Windows NT to Windows 2003, Windows 2000 to Windows 2003, Windows NT to Windows 2000, and within Windows 2000 or Windows 2003 forests. Like ADMT v1, ADMT v2 features a Graphical User Interface (GUI) that looks much the same as v1. Figure 3.17 shows the GUI, listing the various migration tasks you can choose from. Figure 3.17. ADMT options exposed in the GUI. ADMT v2 has added a number of features to correct serious limitations in ADMT v1. Some of these improvements include
In addition to the features listed here, scripting, command-line interface, and password migration are perhaps the most significant improvements in ADMT v2. The following sections examine them in detail. Scripting SupportScripting is an important feature in any migration tool and a severe limitation to ADMT v1. However, ADMT v2 offers a scripting interface that allows access to wizard functions using any scripting language that supports the Component Object Model (COM) interfaces. This feature makes ADMT v2 much more powerful by offering the Administrator the flexibility to
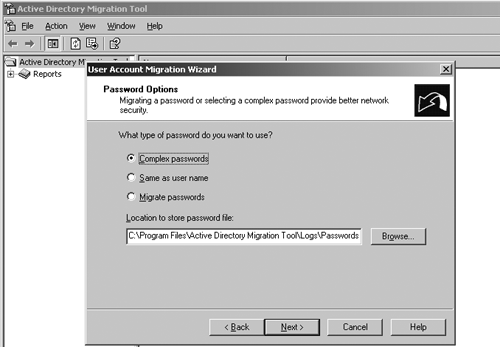
Scripting, however, has some drawbacks. It does require skilled programmers who are able to develop complex scripts to accomplish migration tasks, including configuration checking and error handling. Also, because not all operations are scriptable, there are some limitations as to what scripting can do. For example, you can perform only Exchange Directory Migration, Undo Last Migration, Retry Task, Trust Migration, and Group Mapping and Merging functions by using the wizards. Although Microsoft touts scripting migrations as mostly suitable for large organizations, I've seen smaller companies utilize it in other migration tools because of the capability to customize and perform multiple functions in a single operation. Command-Line InterfaceThe command-line functionality provides the Administrator with a quick and easy interface to perform simple migration operations such as moving users from an OU in one domain to an OU in another domain or forest. The interface uses input directly from the command line or from option files structured in .ini format, allowing the Administrator to create lists of groups, users, and so on in a file for input to the ADMT command-line interface. The command-line interface can also be called from a script or .bat file. Figure 3.18 shows a sample of the user migration option from the command line. Figure 3.18. Executing migration operations from the command-line interface in ADMT. In the example here, we used the following options: /f:"\admt\ntuser.ini" is the include file a text file of users to be migrated /tm:Yes (use test migration option) /IF:Yes (Inter-forest migration =Yes) /sd:Corpnt (NetBIOS name of the source domain is CorpNT an NT domain /td:CompanyX (NetBIOS name of the target domain is Corp a Win2K domain /to:stage1 (Target OU is Stage1) /po:complex (Password Option is Complex. This will generate a random complex password for Improved Password MigrationAlong with scripting and command-line support, password migration makes ADMT a viable migration tool. Specifically, ADMT v1 did not support inter-forest account password migration. ADMT v2 supports password migration with several options:
Other FeaturesJust like its third-party peers, although not as flashy, ADMT allows the Administrator to
ADMT's ValueHow good is ADMT v2.0? I queried a few of HP's consultants who have used ADMT v2 and asked what kind of an environment or size of migration ADMT realistically would support. When asked to compare ADMT's performance to third-party tools from companies such as BindView, Aelita, NetIQ, and Quest, the consultants indicated that performance is similar; that is, roughly 500 user objects per hour , and performance in re-ACLing (changing the security ACLs to reflect new security in the new domain) is acceptable. However, ADMT's capability to perform a migration should be judged on the complexity of the source environment. If you have to split up the migration into multiple tasks (for different locations, business units, and so on), ADMT will not make it easy. Also if you have shared resources that are ACL'd from multiple trusted domains, it will be difficult and time-consuming with ADMT v2. When asked what complexity limit they would recommend using with ADMT v2, the response was that a single source domain with 10,000 users could be done in a single batch over a weekend . It is possible that ADMT v2's scripting and command-line interface could make it possible to do multiple batches and increase this limit. When asked to name the operations they have used ADMT v2 for, the response was that they used it to interactively
When asked what their overall impression was of ADMT v2, the response was that, in general, it's very reliable and easy to use, and seems to work as documented. Scripting support is the biggest improvement in v2. If you were to take the time to build the framework, ADMT v2 could be enterprise-capable, assuming your environment is simple enough. note At this writing, ADMT v3 is being developed. Microsoft has indicated that this version will use a SQL database (presumably the Microsoft Data Engine [MSDE] will work) and will store information so the target and source don't have to be online at the same time. Monitor Microsoft's Web site for this new version of the tool. Third-Party ProductsA number of companies are selling AD migration tools. The most mature ones are listed here. These tools have been around a long time ”since Windows 2000 was released. I'm not selling or recommending them, but simply listing them here with a short feature list so you can be aware of what's out there. These products have clear advantages over ADMT, but they cost a lot more, too. Large migrations in terms of users, remote sites, and so on will benefit from these tools, where ADMT is probably sufficient for smaller organizations as noted in the previous section. These products all run from a separate member server and map credentials needed for the migration to accounts in the tool to give migrators proper permissions. That can all be safely removed after the migration so it doesn't mess with actual permissions, and running separately on a member server, they aren't intrusive into the domain. They all have an "undo" function so you can back out of an operation, they let you organize "projects" so you can design the stages of the migration autonomously, and they feature SIDHistory Cleanup and reporting to allow you to test a migration sequence and see the result, including errors, giving you a chance to correct them before the live migration. Quest SoftwareQuest features the Fastlane suite of products, including Fastlane Migrator and Fastlane NDS Migrator. Quest was one of the initial three vendors who worked with Microsoft in the beta days of Windows 2000, and the Fastlane products are as mature as any on the market. The easy-to-navigate Quest Web site at http://www.quest.com/solutions/allproductsatoz.asp lists all the products with quick links to the product information and a link to the trial download. The features of the Fastlane Migrator include
Aelita SoftwareAelita Software, http://www.aelita.com, markets a couple of interesting products in regard to migration. Aelita also has AD-management products. The Domain Migration Wizard has the following features:
Aelita also has a feature called ZeroImpact that aids in migration of the user profiles without Administrators visiting each workstation. The company also lays claim to being able to perform migrations much faster (elapsed time) than its competitors . A number of whitepapers are on Aelita's Web site at http://www.aelita.com/products/domainmigrationwizard/documentation.asp . BindViewBindView has several products that provide migration capability and are sold separately or bundled together as a suite. Details are noted on the BindView Web site at http://www.bindview.com/Products/DirAdminMig/Migration/index.cfm . The products include
BindView was one of the original migration tools developed for Windows 2000 and used by Compaq in its Windows NT to Windows 2000 migration. This tool offers all the features noted earlier in this section, such as Project-based management, rollback, and so on. NetIQNetIQ, also one of the original three migration tools for Windows 2000, offers three products in the migration arena as well as a number of products for AD administration. Microsoft's ADMT is actually a stripped-down version of NetIQ's Domain Administrator product; NetIQ wrote the original ADMT. NetIQ's suite of products, which can be purchased and used separately or as a suite, include
ProLiant ToolsA number of powerful ProLiant tools will be instrumental in a successful migration. Some of these include improvements to SmartStart, ProLiant Essentials Foundation Pack, Remote Deployment Utility (RDU), and Systems Insight Manager (SIM), which have all been described in Chapter 2. Chapter 7 includes further discussion on their utilization in the deployment phase. In addition, Chapter 9 is dedicated to the RDP, a powerful utility that greatly simplifies deploying software, including the OS on servers in your infrastructure. It is estimated that only about 13% of the ProLiant community is unaware of these tools and doesn't use them. These tools are state-of-the-art and without peers. If you have ProLiant systems and are not taking advantage of these tools, use the relevant chapters in this book to find out how they can help you. Let's now turn our attention to some actual case studies of companies that have performed migrations to Windows Server 2003 from Windows NT and Windows 2000. |
| < Day Day Up > |
EAN: N/A
Pages: 214