Migration Methodologies
| < Day Day Up > |
| In planning a migration, it's important to consider hardware upgrades in addition to all the migration tasks associated with upgrading the OS. Microsoft's HCL has changed dramatically for Windows Server 2003, compared to Windows 2000, so you might be forced to consider hardware upgrades prior to a migration to Windows Server 2003, and most certainly will need to upgrade if you are coming from Windows NT. This section lists some basic points to take into consideration when upgrading ProLiant servers, whereas Chapter 7, "ProLiant Server Installation and Deployment," delves into deployment in more detail. Table 3.4 shows the migration paths for the various Windows NT and Windows 2000 OSs to the corresponding Windows Server 2003 products. Determining which OS will fit your organization's needs is an important consideration in the initial phase of the migration. In fact, you will likely use more than one OS if you have some clustered systems or a datacenter system. In addition, Microsoft has split Web services into its own product, Windows Server 2003 Web Services, meaning you can't run a Web server on Enterprise or Standard edition like you could in Windows 2000. Table 3.4. Migration Paths
The options for migrating to a Windows 2003 forest haven't changed much from those available when migrating to Windows 2000. That is, the two basic methods are the in-place upgrade and restructure, which are detailed in this section. You accomplish an in-place upgrade by using a CD on each DC to upgrade the OS, or by using automated deployment methods to accomplish this. In the in-place upgrade, the OS of the server changes from Windows 2000 or Windows NT to Windows 2003. The restructure method requires that you create a new infrastructure ”new server hardware ”and install Windows 2003 from scratch to create a pristine environment, and then use a migration tool to move the users, groups, and computer accounts from the Windows NT or Windows 2000 forest into the new one. Each method has its advantages and disadvantages, and you might want to use a combination of methods. These methods are described in the sections "In-Place Upgrade" and "Restructure." ProLiant MigrationThere are a number of prerequisites to upgrading the ProLiant servers. Of course, this assumes you have carefully evaluated the servers and performed necessary upgrades to meet Windows Server 2003 requirements. Table 3.5 shows Microsoft's minimum requirements, which technically allow the OS to run. I have Windows Server 2003 Enterprise edition running on a 233MHz workstation with 200MB RAM, but it isn't realistic to put this in any kind of production environment. Microsoft has a tool called the AD Sizer that will help determine, among other things, the memory, disk, and CPU requirements based on your input. This tool is available at http://www.microsoft.com/windows2000/techinfo/planning/ activedirectory /adsizer.asp. HP also has configuration tools, online and offline, for the ProLiant hardware options in its Active Answers Web site. You'll find a plethora of information regarding ProLiant configurations, including application recommendations for Exchange, SQL, SAP, Netware, and many others. To access this information, go to the Active Answers Web site at http://www.hp.com/solutions/activeanswers. Click the Click here for AA Configurator and Sizing Tools link to go to the Active Answers Tools page. Under Solution Sizers, select the View Available Sizers link, and then select the appropriate application. Note that DC sizing is not included in Active Answers. However, you can configure the DCs by using Microsoft's AD Sizer tool and the ProLiant site index at http://www.hp.com/servers/siteindex. Table 3.5. ProLiant Recommended Minimum System Configuration Requirements
note There are no magic tools or formulas that will tell you the exact specifications needed for DCs and GC servers because of dynamic variables such as groups, users, computers, Group Policies, and so on. These tools will give you a good start, but make sure that you test the hardware configuration during the pilot. Applications such as SQL and Exchange can be sized fairly accurately using the Active Answers tools. With the hardware issues addressed, now turn your attention to issues regarding migration of the OS. In-Place UpgradeThe in-place upgrade is a good option if you have a small- or medium-sized environment. The simplistic version of this method is to put a CD in the drive of a DC and run Setup from the CD or off the menu. When you do this on a DC, after the final reboot on upgrading the OS, it runs DCPromo and allows you to create the new forest and domain on the first DC you upgrade. On subsequent DCs, it lets you add them as replica DCs in the appropriate domain. After the first DC is upgraded and DCPromo has run, you have a Windows 2003 forest. You can then upgrade the remaining DCs as time and resources permit. You won't get all the Windows Server 2003 benefits until you switch the forest to Windows Server 2003 mode, so after all the DCs in each domain are upgraded, raise the domain functional level to Windows Server 2003. When all the domains have been raised to Windows Server 2003 level, you can raise the forest functional level of the forest. The in-place upgrade's biggest advantages include
Of course, in-place upgrade has drawbacks, too:
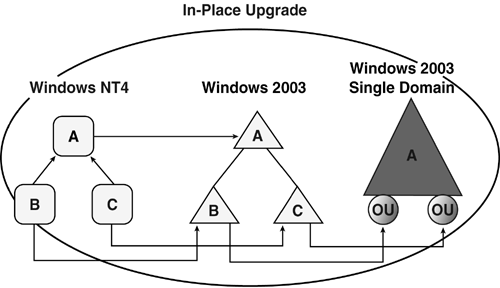
note A Windows 2003 DC can exist in a Windows 2000 native-mode domain or a Windows 2003 native-mode domain. However, the ADPrep utility must be run on a Windows 2000 native-mode domain to upgrade the schema before bringing a Windows 2003 DC into the domain either via an upgrade of a Windows 2000 DC or a newly installed server. The in-place upgrade keeps the domain model, so if you start with three domains, you'll end up with three domains after the upgrade. After the migration, you can collapse them into fewer domains and some Organizational Units (OUs) in separate operations. Figure 3.13 shows how domains A, B, and C in the Windows NT structure are migrated to a parent /child domain structure with domains A, B, and C. In the second step, domains B and C are migrated to OUs in domain A, and domains B and C are decommissioned. Restructure allows you to move from the Windows NT structure to a single domain and OUs in a single step. Figure 3.13. In-place upgrade process. Migrating from Windows 2000 to Windows Server 2003 is considered a fairly routine upgrade, and most companies I've interviewed have used the in-place upgrade method. There is no reason to redesign the domain structure unless changes have occurred since the Windows 2000 upgrade that required a new structure. However, with the Domain Rename and DC rename features, it seems unlikely to make a case for a new design. The In-Place Upgrade ProcessTo upgrade from a Windows NT domain to a Windows 2003 domain, follow this procedure:
To upgrade a Windows 2000 forest to a Windows Server 2003 forest, follow this procedure:
Preparing the Windows 2000 ForestThe first step in moving the Windows 2000 infrastructure to Windows Server 2003 is to determine the "readiness" state of the domain and forest. A pre-upgrade includes the following points:
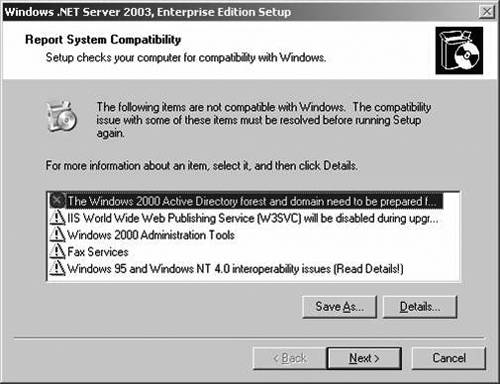
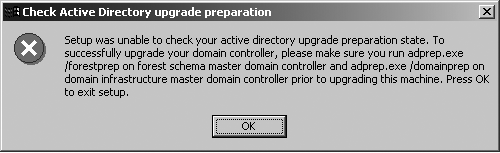
The ADPrep utility to prepare the domain and the forest modifies the Windows 2000 schema, adding classes, attributes, and permissions that Windows Server 2003 requires. You can find the ADPrep.exe program on the Windows Server 2003 CD in the \i386 directory. ADPrep has two phases, domainprep and forestprep, which you execute with two different commands: C:> ADPrep/Forestprep C:>ADPrep/Domainprep warning Don't confuse the Windows 2003 ADPrep utility with the ADPrep utility used to upgrade Microsoft Exchange. You still need to run the ADPrep utility for Exchange for an Exchange upgrade, in addition to the ADPrep for Windows Server 2003. They are different programs and are not interchangeable. You must run the ADPrep/Forestprep command first on the Domain Naming Operations Master. You can easily determine which DC holds this role by installing the Windows 2000 Support Tools from the Windows 2000 Server or Advanced Server CD and executing this command: C:> NetDom Query Fsmo Schema owner ATL-DC1.Company.com Domain role owner ATL-DC1.Company.com PDC role ATL-DC1.Company.com RID pool manager ATL-DC1.Company.com Infrastructure owner ATL-DC1.Company.com The command completed successfully. After that, the ADPrep/Domainprep command is run on a DC in each domain. If ADPrep is not run successfully, an error will pop up when you attempt the upgrade, as shown in Figure 3.14. After ADPrep has run, it will add and populate the Forest Update container to the AD. The Distinguished Name (DN) for this object is CN=ForestUpdates, CN=Configuration, DC=Company,DC=Com . Under this object there is an operations object: CN=Operations, CN=ForestUpdates,CN=Configuration, DC=Company,DC=Com . Under the operations object, there are a number of child objects, each with a Globally Unique Identifier (GUID) for a name. These objects represent various operations performed in the schema upgrade. Figure 3.14. Performing an upgrade without first successfully running ADPrep results in this error message and terminates the operation. There are basically three ways to determine whether ADPrep has been run:
The Windows 2000 schema version is version 13. The Windows 2003 schema is version 30. The Pile On IssueThe Pile On issue has been a known issue for a couple of years now, but it still seems to be unknown to most of the Windows NT community. It affects only an upgrade with the following characteristics:
The problem occurs because the default behavior of Windows 2000 Server, Windows 2000 Professional, and Windows XP is to attempt to use Kerberos for authentication. When authentication is required at startup or user logon, these clients attempt to find a Kerberos Distribution Center (KDC) to authenticate to. All Windows 2000 and Windows Server 2003 DCs are also KDCs. If a KDC is not found, authentication takes place via NTLM. After a KDC is found, a Registry change is made and the client will authenticate only via Kerberos and will not use NTLM until the client is unjoined from the domain (to a workgroup) and then rejoins the domain. The proper upgrade procedure for upgrading Windows NT domain to Windows 2000 or Windows Server 2003 domain is to upgrade the PDC first, and then upgrade the BDCs. However, as soon as the PDC is upgraded, client authentication across the enterprise ignores current Windows NT BDCs and authenticates to that single KDC. This happens because Net Logon, on the client, sends a DNS Query as part of the DC Locator process. That query locates the DNS that is authoritative for that domain to determine whether there is a Kerberos SRV record for a KDC. After the query finds the record and successfully contacts that KDC (domain controller), the client authenticates to that DC and will never failover to NTLM again. Thus, the clients all "pile on" the first Windows 2000 or Windows Server 2003 DC. The problems this causes are primarily the following:
The trick here is to upgrade all the BDCs as soon as possible to establish the local authentication as soon as possible. Microsoft attempted to help this problem with the addition of two Registry keys, documented in Microsoft KB 284937, "Windows 2000-Based Clients Connect Only to the Domain Controller that was Upgraded First in a Mixed-Mode domain:"
After each BDC is upgraded, the NT4 Emulation key must be set to prevent client authentication. After all BDCs are upgraded, you can remove these keys to let the clients authenticate. There are a few dependencies that you can take advantage of to give you time to get all the DCs upgraded before client authentication is allowed. These dependencies include
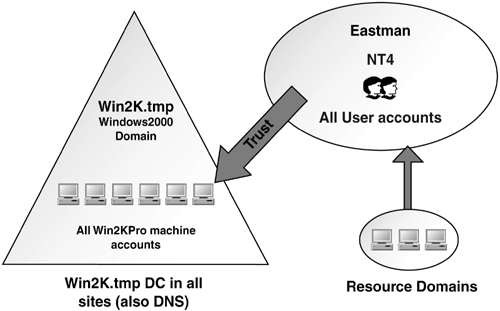
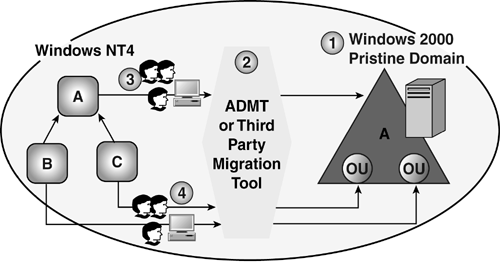
I worked with Eastman Chemical Company, whose migration is profiled later in this chapter, on its Windows NT 4.0 to Windows 2000 migration at the time when the Pile On issue was first discovered . At the time, Microsoft could not provide us with a single customer who had used the NT4 Emulation and Neutralize keys, which made us nervous. Through its own testing, Eastman Chemical discovered it had inadvertently solved the problem. Figure 3.15 shows Eastman's Windows NT 4.0 domain structure: a single Windows NT 4.0 domain called "Eastman" and several resource domains. One of the resource domains was a Windows 2000 domain, W2K.tmp, originally created just so Eastman could play with Windows 2000 to help the employees learn it, and in which Eastman had placed all their clients. The company's normal PC refresh program had gradually replaced the PCs with new ones installed with Windows 2000 Professional at the time ”a perfect candidate for the Pile On problem. Figure 3.15. The Eastman Chemical company domain structure. During testing, Eastman found that because a downlevel trust existed between W2K.tmp where the machine accounts existed, and the Eastman accounts domain, the clients couldn't use Kerberos to authenticate across that trust, and thus the company could upgrade the PDC without fear of a Pile On condition and without messing with the Registry keys. The upgrade was successful. We upgraded the PDC and several BDCs in the corporate hub site in one weekend and gradually upgraded the BDCs in the remote sites over the next several weeks. After they were all upgraded, the trust was converted to a Kerberos type trust and authentication switched from NTLM to Kerberos. The "Case Studies" section later in this chapter details how Eastman Chemical used an ingenious plan to shorten the time of the upgrade and mitigate the risk of failure with an in-place upgrade. RestructureThe restructure method is depicted in Figure 3.16. In step one in the figure, we get new servers and create a pristine Windows 2003 domain structure, including domains, OUs, Group Policies, security structure, and so on. Then, in step two, obtain a migration tool such as the Active Directory Migration Tool (ADMT) that Microsoft provides on the Windows 2003 Server CD, or one from a third-party company, and use it in step three to migrate the users and groups from the old domain structure (Windows NT or 2000) to the new. Step four shows migration of users and groups from resource domains to Windows 2002 OUs. This was not possible in the In-Place Upgrade method (that is, you had to migrate users and groups from the resource domains to Windows 2000 child domains and then migrate them to OUs in a single domain). Unlike the in-place upgrade, this method allows you to use the migration tools to stage the migration of users, groups, and computer accounts; select the destination as a particular domain or OU; migrate or change the users'passwords; and even test it to get a report of any errors encountered. Figure 3.16. The restructure method allows movement of users, groups, and computers directly into the Windows 2003 domain structure domains or OUs. The advantages of this method include
The disadvantages to the restructure method include
The process of restructure is pretty straightforward:
As you can see from the list of advantages and disadvantages, restructure is more appropriate when migrating from Windows NT to Windows Server 2003 than from Windows 2000 unless a restructure of the namespace is required in a case such as a merger or acquisition. In the "Case Studies" section later in this chapter, examples are given of organizations that used the restructure method and others that used the in-place upgrade method. ProLiant Post-Upgrade TasksThere are several points to consider in regard to the ProLiant server when upgrading to Windows Server 2003:
Some of the current known issues encountered during the upgrade on ProLiant servers include
Additional details on ProLiant deployment are provided in Chapter 7. Now let's look at migrations within a forest and between existing forests. Intra- and Inter-Forest MigrationsIn addition to changing the structure of the entire domain from Windows NT or Windows 2000 to Windows Server 2003, there is usually an ongoing need to change the structure of OUs, location of users, groups, and computers within a forest, or between domains in a forest. In the case of a merger or acquisition, you might need to perform a migration between Windows 2003 forests or from a Windows 2000 forest and a Windows Server 2003 forest. The tools noted in the previous section of this chapter are all capable of performing such migrations. In addition to those tools, other utilities are available that are native to Windows Server 2003 and in the Windows Server 2003 Support Tools that are handy for manipulating a small or large numbers of objects. These tools include
All these utilities are well documented in the Windows Server 2003 Help and Support in the Start menu, and in the command line online help by typing /? after the command. The additional power of these commands is realized by combining them in scripts. The ds* commands in the previous list are all new to Windows Server 2003. |
| < Day Day Up > |
EAN: N/A
Pages: 214