WebLogic Security Overview
Let s start our discussion of WebLogic Server security by looking at the different types of clients and how they can be used to access a WebLogic Server application. WebLogic Server supports many different types of clients and protocols that can be used to access the server, as shown in Figure 10.1. As far as security is concerned , two primary types of clients will be calling into the server.
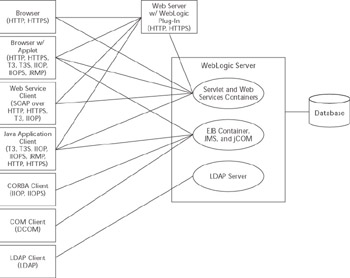
Figure 10.1: Client connectivity options.
The first type is typically a browser or a Web Services client that either calls directly into the server or accesses the server via an intermediate Web server running one of the WebLogic Web server plug-ins. Java or non-Java applications that make standard HTTP requests would also fall into this category. These clients generally authenticate themselves to the WebLogic Server using one of the standard HTTP authentication mechanisms: basic authentication or certificate-based authentication using two-way SSL.
The second type is the application client that typically calls directly into the server using a distributed object-based protocol like T3, IIOP, or JRMP. These clients generally authenticate themselves using the security mechanisms associated with the particular protocol or programming model, such as the Java Authentication and Authorization Service (JAAS) or the Common Secure Interoperability Version 2 (CSIv2) in the case of CORBA clients. Although HTTP tunneling of these protocols can allow these clients to communicate also through an intermediate Web server, authentication still uses the same mechanisms that it would if the protocols were not being tunneled.
With either type of client, the calls could be routed through one or more firewalls. We will talk about suggested firewall layouts later on in Chapter 14.
As these clients make calls into the various business applications on the server, these applications use the WebLogic Server Security Service to authenticate users, authorize their access to application functionality, audit security decisions, and perform other security- related tasks . This can include the J2EE security features as well as specialized WebLogic Server security features. When the WebLogic Server Security Service is called, it makes calls into the WebLogic Security Framework for security decisions. The WebLogic Security Framework defines a rich set of service provider interfaces (SPIs) that are called when security decisions must be made. Through these provider interfaces, the framework calls into one or more security providers that are configured for the server. Figure 10.2 shows the architecture and where each component fits into the big picture.
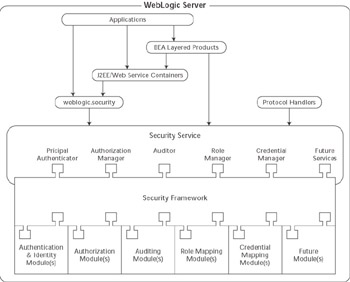
Figure 10.2: WebLogic Server security architecture.
If you are familiar with the older security realm interfaces in earlier releases of WebLogic Server, you can see right away that this security framework is much more comprehensive. The new framework provides backward compatibility with the older realm interfaces by running the security framework in compatibility mode. Compatibility mode, however, does not support any of the new features provided by the new security service. Therefore, you must make the decision either to continue to use the old security realms in compatibility mode or to switch to use the security framework. Throughout the rest of this chapter, we will assume that you re running the new security framework using the default security providers that ship with WebLogic Server.
EAN: 2147483647
Pages: 125