SASL Overview
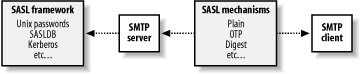
SASL is a general method to add or enhance authentication in client/server protocols. Its primary purpose is to authenticate clients to servers. When you configure SASL, you must decide on both an authentication mechanism, for the exchange of authentication information (commonly referred to as user credentials), and an authentication framework for how user information is stored. The SASL authentication mechanism governs the challenges and responses between the client and server and how they should be encoded for transmission. The authentication framework refers to how the server itself stores and verifies password information. Figure 12-1 illustrates these two processes. Once an authentication is successful, the server knows the user's identity and can determine which privileges the identified user should have. In the case of Postfix, it is the privilege to relay mail. You can also optionally limit identified users to using a particular sender address when they relay mail.
Figure 12-1. SASL authentication frameworks and mechanisms
12.1.1 Choosing an Authentication Mechanism
The client and server must agree on the authentication mechanism they'll use. (See the Cyrus documentation for currently supported mechanisms.) Some of the more common mechanisms are listed below:
PLAIN
The PLAIN mechanism is the simplest to use, but it does not include any encryption of authentication credentials. You may want to use TLS (see TLS information in Chapter 13) in conjunction with the PLAIN mechanism. The login and password are passed to the mail server as a base64 encoded string.
LOGIN
The LOGIN mechanism is not an officially registered or supported mechanism. Certain older email clients were developed using LOGIN as their authentication mechanism. The SASL libraries support it in case you have to support such clients. If you need it, you must specify support for it when you compile the libraries and Postfix. See Appendix C if you are building your own Postfix. If you are using a packaged distribution and you need LOGIN support, check the documentation with your distribution to make sure it includes it. If it is used, the authentication exchange works the same as the PLAIN mechanism.
OTP
OTP is an authentication mechanism using one-time passwords (formerly S/Key). The mechanism does not provide for any encryption, but that may not be necessary since any captured password is good for only a single session. SMTP clients must be able to generate OTP authentication credentials.
DIGEST-MD5
With the DIGEST-MD5 mechanism, both the client and server share a secret password, but it's never sent over the network. The authentication exchange starts with a challenge from the server. The client uses the challenge and the secret password to generate a unique response that could be created only by somebody who has the secret password. The server uses the same two pieces, the challenge and secret password, to generate its own copy, and compares the two. Since the actual secret password is never sent across the network, it's not vulnerable to network eavesdropping.
KERBEROS
Kerberos is a network-wide authentication protocol. Unless you are already using Kerberos on your network, you probably don't need to support the KERBEROS mechanism. If you are using Kerberos, using SASL is a nice way to fit SMTP authentication into your existing infrastructure.
ANONYMOUS
SASL includes an ANONYMOUS mechanism, which might make sense for some protocols, but has no benefit for SMTP. An open relay is essentially using an anonymous mechanism, and the purpose of SMTP authentication is to eliminate open relays.
When a client connects to a mail server, the server typically lists all of the password mechanisms it supports, in order of preference. The client tries the first one it supports. If that fails, it may be configured to try additional mechanisms until it can authenticate successfully. If the client and server cannot successfully negotiate over a common mechanism, authentication fails.
Once the server and client agree on a mechanism, they begin the authentication process, consisting of one or more challenges and responses that are governed by the agreed-upon mechanism. The protocol also specifies how these exchanges should be encoded.[1]
[1] Note: that's encoded, not encrypted. A particular mechanism may or may not include encryption of the client's credentials.
12.1.2 Choosing an Authentication Framework
The SASL authentication framework can use your existing Unix system passwords (for example, passwd, shadow, or PAM) or a separate password file just for authenticating SMTP users. Other options include Kerberos or even a new scheme of your own.
Ultimately, your choice comes down to where and how you want to store your authentication information. Consider your network and how your users currently authenticate to decide which framework works best for you. If your mail users already authenticate on your network through PAM, for example, then you probably want to configure SASL to use your existing system. If, on the other hand, most of your SMTP users are virtual accounts (without system logins), you should opt for a separate password database for SMTP users. Often your POP/IMAP server can share the same user database, making this a convenient option for virtual mail accounts.
Introduction
- Introduction
- Postfix Origins and Philosophy
- Email and the Internet
- The Role of Postfix
- Postfix Security
- Additional Information and How to Obtain Postfix
Prerequisites
Postfix Architecture
- Postfix Architecture
- Postfix Components
- How Messages Enter the Postfix System
- The Postfix Queue
- Mail Delivery
- Tracing a Message Through Postfix
General Configuration and Administration
- General Configuration and Administration
- Starting Postfix the First Time
- Configuration Files
- Important Configuration Considerations
- Administration
- master.cf
- Receiving Limits
- Rewriting Addresses
- chroot
- Documentation
Queue Management
Email and DNS
Local Delivery and POP/IMAP
- Local Delivery and POP/IMAP
- Postfix Delivery Transports
- Message Store Formats
- Local Delivery
- POP and IMAP
- Local Mail Transfer Protocol
Hosting Multiple Domains
- Hosting Multiple Domains
- Shared Domains with System Accounts
- Separate Domains with System Accounts
- Separate Domains with Virtual Accounts
- Separate Message Store
- Delivery to Commands
Mail Relaying
- Mail Relaying
- Backup MX
- Transport Maps
- Inbound Mail Gateway
- Outbound Mail Relay
- UUCP, Fax, and Other Deliveries
Mailing Lists
Blocking Unsolicited Bulk Email
- Blocking Unsolicited Bulk Email
- The Nature of Spam
- The Problem of Spam
- Open Relays
- Spam Detection
- Anti-Spam Actions
- Postfix Configuration
- Client-Detection Rules
- Strict Syntax Parameters
- Content-Checking
- Customized Restriction Classes
- Postfix Anti-Spam Example
SASL Authentication
- SASL Authentication
- SASL Overview
- Postfix and SASL
- Configuring Postfix for SASL
- Testing Your Authentication Configuration
- SMTP Client Authentication
Transport Layer Security
Content Filtering
External Databases
Appendix A. Configuration Parameters
Appendix B. Postfix Commands
Appendix C. Compiling and Installing Postfix
- Appendix C. Compiling and Installing Postfix
- C.1. Obtaining Postfix
- C.2. Postfix Compiling Primer
- C.3. Building Postfix
- C.4. Installation
- C.5. Compiling Add-on Packages
- C.6. Common Problems
- C.7. Wrapping Things Up
Appendix D. Frequently Asked Questions
EAN: 2147483647
Pages: 130
- Using SQL Data Manipulation Language (DML) to Insert and Manipulate Data Within SQL Tables
- Working with Comparison Predicates and Grouped Queries
- Writing External Applications to Query and Manipulate Database Data
- Retrieving and Manipulating Data Through Cursors
- Working with Ms-sql Server Information Schema View
