Single Channel Broadband-SSH
Single Channel Broadband
A local network scheme in which the entire spectrum of the cable is devoted to a single transmission path ; frequency-division multiplexing is not used. Also known as carrierband.
Single Channel Transmitter
A transmitter used to process only one television channel.
Single Day Assignment
A call center term . A method of automatic assignment (of employees to Master File schedules) that operates only on schedules of exactly one workday in length. Unlike multi-day assignment (which operates on schedules of any length), this makes it possible for each assigned employee to be scheduled for different hours each day.
Single Digit Dialing
Provides for single-digit dialing to reach a preselected phone or group of phones.
Single Ended Terminal Device
A device which terminates only one line at a given time.
Single Fiber Cable
A plastic-coated fiber surrounded by an extruded layer of polyvinyl chloride, encased in a synthetic strengthening material and enclosed in an outer polyvinyl chloride sheath.
Single Frequency Signaling
SF Signaling. The use of one tone ” typically 2600 Hz ” to indicate if the phone line is busy or idle (supervision) and to convey dial pulse signals from one end of a trunk or line to the other, using the presence or absence of a single specified frequency. The conversion into tones, or vice versa, is done by SF signal units. See also Frequency, Inband Signaling, Signal.
Single Gang Receptable
See Back Box.
Single In Line Memory Modules
Basically memory packaged so it can be slipped into a PC or laptop PC much easier than present methods of installing memory ” which typically consist of pushing memory chips with legs into printed circuit boards . The problem with memory with legs is that you're likely to bend one of the legs and thus have the installation go awry.
Single Line Instrument
A telephone set normally used to access only one line. However when used with advanced telephone systems, additional lines can be accessed by dialing specific codes rather than by depressing keys.
Single Master Domain
A relationship in a domain or amongst domains in which trusts are set up so that management control is centralized in one domain. See Trust Relationship.
Single Mode Fiber
See SMF.
Single Number Service
-
Allows callers to dial a single number to reach a company with multiple local stores. For instance, a pizza chain might advertise a single number. The approximate physical location of the caller can be determined by the network by virtue of the originating number. Based on that data, the location can be compared to a network database defining the location of the closest pizza parlor. The caller, therefore need not sort through the phone book for this information, which can be especially difficult without a knowledge of the area. Additionally, all calls are routed automatically and without error to the outlet in closest proximity, ensuring that the pizza arrives quickly, as well as hot and fresh.
-
An optional feature for 800 IN-WATS Services which allows a subscriber who has or wants to have both intrastate and interstate 800 service to use the same 1-800 number for both services. If you'd like to buy another copy of this dictionary, call 1-800-LIBRARY. That phone number will be answered at our office in New York City. It will work for calls from inside and from outside New York State.
Single Party Revertive Ringing
A central office feature. Single-Party Revertive Ringing provides enhanced flexibility to residential subscribers' existing telephone service by turning extension phones into intercoms. This feature creates a type of home intercom system with which subscribers can reach people in other rooms in their home and/or on a remote part of their property (i.e., barn, garage, greenhouse, etc.). To initiate a home intercom call, the subscriber dials his own number and hangs up. All extension phone rings. The intended party picks up the extension and is connected.
Single Point of Contact
SPOC. A way of handling a multi-vendor sale and implementation in which one vendor or consultant handles contacts with the other vendors and/or departments and presents a unified proposal and project management to the customer, so that the customer needs to deal with only one person or team.
Single Point of Failure
A single "point," or "element" at which a failure, or "hard fault," could bring down an entire network or subnetwork. The "point" could be a circuit if all traffic in the network or subnetwork passes through it. Similarly, the "point" could be a hub, switch or router if all traffic passes through it. The "point" also could be an application software system, if the operation of the network depends on it. Optical fiber networks are highly redundant in order to minimize the risk of catastrophic failure from "backhoe fade." Nonetheless, optical fiber networks sometimes suffer multiple cuts which render them out of service. Signaling System 7 (SS7) systems have occasionally suffered from software bugs which have resulted in the broadcasting of error messages which have overwhelmed all SS7 connected switches, causing entire networks to shut down. Similarly, Frame Relay networks have sometimes suffered from software bugs which shut them down. Paging networks have completely crashed because of software errors or because a satellite "disappeared" for several hours. Full redundancy is the only real protection against such catastrophic failures, but it's generally considered too expensive for all but the most mission-critical, time-sensitive applications or networks. ARPANET, the predecessor to the Internet, originally was designed so that there was no single point of failure. The idea with ARPANET was that every transmission would be sliced into packets. Each packet would travel whichever route was available at that time, there always being multiple routes between two routes. If one route crashed, the packet would go another way. ARPANET (Advanced Research Projects Agency Network) was a network in support of government and military research projects. It was conceived and build in the late 1960s, during the Cold War. The United States designed ARPANET to avoid the risk that a nuclear strike aimed at a Single Point of Failure might take down the entire network. See also ARPANET and Internet. See Back Hoe Fade.
Single Protocol Router
A communications device using the same mix of protocols which is designed to make decisions about which of several paths a packet of information will take. The packets are routed according to address information contained within the packet.
Single Sideband
SSB. An Amplitude Modulation (AM) technique for encoding analog or digital data using either analog or digital transmission. SSB suppresses one sideband of the carrier frequency at the source. As only one sideband is used and as the carrier signal is suppressed (i.e., carries no information), less power is used and less bandwidth (one- half) is required than is the case with DSBSC (Double SideBand Suppressed Carrier). Carrier synchronization is lost. See also Amplitude Modulation, DSBSC, DSBTC, and VSB.
Single Sideband Transmission
A system of transmission which suppresses one side- band of the carrier frequency at the source. Also applied to receiving systems designed to reproduce such transmissions.
Single Sign-On
SSO. An authentication and authorization mechanism that requires that a user identify himself only once. Thereafter, the user is authorized to access other connected system resources, based on his level of access privilege. The most common identification, of course, is the username / password combination. Users who access many systems often have to remember a different username/password combination for each. That results in more forgotten passwords, and more calls to the help desk. It also results in more users writing their ID information down on those little sticky notes, which they then stick to their monitors , which causes a total breakdown in security. SSO helps solve all these problems.
Single Slot
-
Current standard for coin phone construction that uses one slot for the deposit of all acceptable coins .
-
Cards that fit into one slot inside a Wintel (Windows/Intel) PC are called single slot cards. The significance of calling them single slot is that in the old days individual cards couldn't do very much. To build something ” like an interactive voice response system ” you often needed several cards. But with time, components have shrunk and cards have gotten more capabilities. Complete computer telephony systems can now be built with one single slot PC card. Thus the significance of this definition.
Single Use Batteries
Batteries that aren't rechargeable ” in other words, the Duracell and Eveready batteries at your local supermarket .
Single Wire Line
A transmission path which uses a single conductor and a ground return to complete a circuit. Used a lot in rural areas.
Sinister
Ancient Romans always entered the home of a friend on their right foot . The left side of the body was thought to portend evil. The Latin word for "left" is sinister, from where the English word "sinister" originates, meaning anything threatening or malevolent.
Sink
That part of a communications system which receives information.
SIO
-
Serial Input/Output. The electronic methodology used in serial data transmission.
-
Scientific or Industrial Organization. An ITU (International Telecommunications Union) term. Any organization, other than a governmental establishment or agency, which is engaged in the study of telecommunication problems or in the design or manufacture of equipment intended for telecommunication services. Examples of U.S. SIOs are ADTRAN, Advanced Micro Devices, ASCEND Communications, Cisco Systems, 3Com Corporation, and Hewlett-Packard.
SIP
-
Single Inline Package. A type of silicon chip in which all of the pins are lined up in a row. See also DIP, PGA, and SIMM.
-
SMDS Interface Protocol.
-
Session Initiation Protocol. SIP is the emerging standard for setting up telephone calls, multimedia conferencing, instant messaging and other types of real-time communications on the Internet. SIP is touted as much faster, more scalable and easier to implement than H.323. An array of network gear including IP phoes, IP PBXs, servers, media gateways and softswitches support SIP. SIP is the Application Layer (Layer 7 of the OSI Reference Model) protocol for the establishment, modification and termination of conferencing and telephony sessions over an IP-based networks. SIP uses text-based messages, much like HTTP. SIP was developed within the IETF MMUSIC (Multiparty Multimedia Session Control) working group, and is defined in the IETF's RFC 2543. SIP is touted as being much faster, more scalable and easier to implement than H.323.SIP addressing built around either a telephone number or a Web host name. In the latter case, for example, the SIP address would be based on a URL (Uniform Resource Locator), and might look something like SIP:Harry_Newton@TechnologyInvestor.com, which makes it very easy to guess a SIP URL based on an e-mail address. The URL is translated into an IP address through a DNS (Domain Name Server). SIP also negotiates the features and capabilities of the session at the time the session is established. For example, a caller might wish to establish a call using G.711 audio and H.261 video. The codecs embedded in the two endpoints (i.e., originating and terminating multimedia terminals) negotiate a common set of voice and video compression algorithms (which might not include G.711 and H.261), prior to establishing the session. This advance negotiation process, which relies on the Session Description Protocol (SDP), is touted as greatly reducing the call setup time required for H.323 sessions. If the called party is not available, or does not wish to accept the call, it can be redirected (e.g., to voice mail or to an administrative assistant), with the negotiation process taking place in consideration of that endpoint. Once the session is established, the designated capabilities can be modified during the course of the call. For example, whiteboarding can be added if both terminals are capable and can negotiate a common compression algorithm. In addition to the uni- cast (i.e., one-to-one) session described above, SIP supports multicast (i.e., one-to-many) communications. See also CPL, H.323 and SDP.
SIP for Instant Messaging and Presence Leveraging Extensions
See SIMPLE.
SIP Forum
The SIP Forum is a nonprofit industry association whose mission is to promote awareness and provide information about the benefits and capabilities enabled by SIP. The SIP Forum also works to facilitate the integration of SIP with other areas of development on the Internet. The SIP Forum has become the meeting place for service providers, vendors and researchers developing commercial SIP services. SIP Forum members are offering the new services enabled by SIP, such as consumer broadband phone and IP Centrex, and are developing new technology, such as IP phones, PC clients , SIP servers and IP telephony gateways. www.SipForum.com.
SIP L2_PDU
Standard Interface Protocol Level 2 Protocol Data Unit. An SMDS term. The 53-octet unit of information processed by the second level of the SIP. This process takes place once the SIP L3_PDU is presented.
SIP L3_PDU
Standard Interface Protocol Level 3 Protocol Data Unit. An SMDS term. A variable-length (up to 9,220 octets long) unit of information processed by the third layer of the SIP. At this level, the SMDS SDU (Service Data Unit) of up to 9,188 octets is surrounded by a header and a trailer, before being passed to SIP Level 2 for further processing. See also SIP L2_PDU.
SIP SMDS Interface Protocol
An SMDS term. The protocol defined at the interface between the SMDS network and the end user. See SIP L2_PDU.
SIR
-
Speaker Independent Recognition.
-
Sustained Information Rate. A SMDS term. SMDS requires that customers using access lines operating at DS-3 rates to predict the SIR, which is the level and duration of traffic flow. SIR is determined at the time of service subscription, and is enforced through a Credit Manager resident in the SMDS network switches. Five Access Classes are defined: Access Class 1 supports SIR of 4 Mbps and is intended for 4-Mbps Token Ring (802.5); Access Class 2, 10 Mbps and is intended for 10-Mbps Ethernet (802.3); Access Class 3, 16 Mbps and is intended for 16-Mbps Token Ring (802.5); Access Class 4, 25 Mbps; and Access Class 5, 34 Mbps.
Sirius
Sirius is the name of the second SDARS ” Satellite Audio Receiver Service ” provider. The other one is called XM. See XM for a full explanation.
SISO
Soft Input-Soft Output. An technique used in certain Forward Error Correction (FEC) error detection and correction algorithms, such as Extended Hamming and Turbo Coding. SISO actually is used by the decoders on the receiving (Forward) side of the data transmission. FEC provides the receiving decoder with enough information to make exceptionally accurate judgements as to the integrity of a data block (e.g., packet or frame) of data. Further, FEC provides the receiving decoder with enough information to isolate the errored bit(s) in a data block, and to correct them without the requirement for a retransmission. Using Extended Hamming as an example, data to be transmitted are organized into what is viewed logically as a two-dimensional data block. The block might, for example, be 11 bits horizontal (wide) by 11 bits vertical (deep). The coding algorithm describes each 11- bit data sequence through a 5-bit parity code, or Extended Hamming code, which is appended to each 11-bit data word prior to transmission. At the receiving (Forward) decoder, the appended 5-bit descriptor is re-calculated, and the two descriptors are compared. This process takes place, both horizontally and vertically, for each 11-bit data word in a block of data, which might be 11x11 data bits, and 16x16 total bits. If there is a difference in value between the descriptors, an error has been detected . If the decoder views and evaluates each individual bit in a data block, it makes a "hard decision" on each bit. SISO is an iterative decoding technique in which the decoder not only determines the most likely transmitted sequence of data bits, but also develops a "soft decision" metric (i.e., measurement) of the confidence level (i.e., likelihood ) of the value each bit in that sequence. The yield of this more involved soft decision is that each subsequently evaluated block has the advantage of the lessons learned in the previous evaluations. SISO logic is much more complex and, therefore, increases both the cost of the decoder and the time required to accomplish the process. However, SISO yields better results. See also Forward Error Correction, Hamming, and Turbo Coding.
SIT Tones
-
Standard Information Tones. These are tones sent out by a central office to a pay phone to indicate that the dialed call has been answered by the distant phone, etc.
-
Special Information Tones. These are tones for identifying network provided announcements. Here's Bellcore's explanation: Automated detection devices cannot distinguish recorded voice from live voice answer unless a machine-detectable signal is included with the recorded announcement. The ITU, which specifies signals that may be applied to international circuits, has defined Special Information Tones for identifying network provided announcement. The SIT used to precede machine-generated announcements also alerts the calling customer that a machine-generated announcement follows . Since SIT consists of a sequence of three precisely defined tones, SIT can be machine-detected, and therefore machine-generated announcements preceded by a SIT can be classified . At least four SIT encodings have been defined: Vacant Code (VC), Intercept (IC), Reorder (RO) and No Circuit (NC). With the exception of some small stored Program Control Systems (SPCSs) and some customer negotiated announcements, Bell operating companies in North America now precede appropriate announcements with encoded SITs to detect and classify announcements.
SITA
Society of International Aeronautical Telecommunications. The international data communications network used by many airlines.
Sitcom
SITCOMs. What yuppies turn into when they have children and one of them stops working to stay home with the kids . Stands for Single Income, Two Children, Oppressive Mortgage.
Site Controller
An industrial grade PC located at MCI terminals and junctions. It provides the operator local visibility into alarm and performance information from the Extended Superframe Monitoring Unit and 1/0 DXC, as well as enabling the operator to interact with both devices.
Site Event Buffer
See SEB.
Site Hosting
See Hosting.
Site License
Companies that buy software for multiple computers typically buy one copy of the program and a license to reproduce it up to a certain number of times. This is called a site license, though it may apply to its use throughout an organization. Site licenses vary. Some require that a copy be bought for each potential user ” the only purpose being to indicate the volume discount and keep tabs. Others allow for a copy to be placed on a network server but limit the number of users who can gain simultaneous access. This is called a concurrent site license. And many network administrators prefer this concurrent license, since it gives them greater control. For example, if the software is customized, it need be customized only once.
Site Survey
This is the process which communications companies must perform to insure that there is ample space in the telephone room D-Mark area to install their equipment.
Sitekeeper
See IPTC.
SIVR
Speaker Independent Voice Recognition. See Speaker Independent Voice Recognition.
Six Digit Translation
We have a long distance number 212-691-8215. The ability of a switching system to do six digit translation means that it can "look at" 212- 691 and figure how to route the phone call. The criterion of choosing which way to send the call is, most often, the least expensive way. Six digit translation is often an integral part of Least Cost Routing programs within the phone system which tell the calls to go over the lines perceived by the user to be the least cost way of getting the call from point A to point B. There are typically two types of "least cost routing" translation ” that which examines the first three digits of the phone number (i.e. just the area code) and the first six digits of the phone number (i.e. the area code and the three digits of the local central office). Six digit translation is preferred because it allows you more flexibility in routing, particularly to big area codes, like 213 in LA, where there are long distance calls within the area code. See also Least Cost Routing and Alternate Routing.
Six in a can
A technique of disguising cell antennas, this would be three dipole antennas in a tube or can that looks like the top of a flagpole , or a chimney on a building.
Six Nines
See Five Nines.
Sizing
A telephone company term. The Network Switching Engineering activity of determining the types and quantities of equipment needed for relief. Also see Relief.
Skew
-
The deviation from synchronization of two or more signals.
-
A computer imaging term. A tool that slants a selected area in any direction.
-
In parallel transmission, the difference in arrival time of bits transmitted at the same time.
-
For data recorded on multichannel magnetic tape, the difference in time of reading bits recorded in a single line.
-
In facsimile systems, the angular deviation for the received frame from rectangularity due to asynchronism between scanner and recorder. Skew is expressed numerically as the tangent of the angle of deviation.
See also Skew Ray and Skewed Distribution.
Skew Ray
In a multimode optical fiber, any bound ray that in propagating does not intersect the fiber axis (in contrast with a meridional ray). In a straight, ideal fiber, a skew ray traverses a helical path along the fiber, not crossing the fiber axis. A skew ray is not confined to the meridian plane.
Skewed Distribution
The mean and standard deviation describe many distributions quite well. However, a few distributions are markedly lopsided or skewed. When it is necessary to specify a distribution more precisely, the coefficient of skewness may be computed. It is sometimes expressed as the mean minus the mode divided by the standard deviation. That is, it is the spread between the mean and the mode as related to the spread or scatter of the total distribution.
Skid Marks
American toilets have far more water in their bowls than European toilets. The reason, according to a ex-senior Kohler executive, Leo Carlin, is that "Americans don't like skid marks."
Skills-Based Routing
A call center term for routing incoming calls based on the type of service requested , assuring that calls go to agents with the skills to provide the highest quality of service to the calling customer. In other words, someone calling about a broken refrigerator should be directed to a refrigerator expert, not a vacuum cleaner expert. Skills-Based Routing takes advantage of the routing capabilities of the automatic call distributor, in consideration of the unique skills of individual agents or agent groups and the requirements of individual callers. In this manner, privileged customers with special needs can be afforded special treatment. For example, a Platinum credit card holder with a past due account balance and who prefers to conduct business in Cantonese can be directed to an agent skilled in collections involving privileged customers and who speaks fluent Cantonese. The routing process may be accomplished on the basis of a client profile stored in a database on an adjunct computer systems linked to the ACD. Prior to completing the call, the database would be queried, with the query process being initiated on the basis of the caller's touchtone entry of his account number or on the basis of Caller ID. See also Source/Destination Routing, Calendar Routing, and End-of-Shift Routing.
Skimmer
See Magnetic Card.
Skin
Surface layer in a sandwich structure.
Skin Effect
The tendency of an electrical current to pass through the outer portion, or "skin" of a metallic conductor, rather than through the center, the skin effect is a phenomenon associated with high frequency signals (i.e., over 50 kHz or so. The higher the frequency, the greater the effect.
SKIP
Simple Key management for Internet Protocols. A specification that defines the way that an encryption key is exchanged between devices over an IP (Internet Protocol) network such as the public Internet. SKIP is a proprietary specification developed by Sun Microsystems. See also ISAKMP.
Skip Key
Use "skip keys" wherever possible. Skip keys are single key-presses that take the caller to the most commonly sought places, including information message boxes. For example, a skip key is Dial 1 for Books. Dial 3 for subscriptions. Dial 4 for our fax number. Ron Acher invented this term. Or thinks he did.
Skip Route
A control application that causes traffic to bypass a specific route and advance to another route.
Skip Tracers
People who use their knowledge of databases, motor vehicle license records, credit card records and purchases to track down people who own money.
Skip Zone
a ring-shaped region within the transmission range wherein signals from a transmitter are not received. It is the area between the farthest points reached by the ground wave and nearest points at which reflected sky waves come back to earth.
SKU
Stock-Keeping Unit. An e-commerce term for a stock number, or inventory number. When you order something over the WWW (World Wide Web), you will reference a SKU. The SKU is unique to the product, which could be a book, a part, a complete system like a PC, or just about anything. The SKU will be compared to a database, and will match the item which you are buying, which will be pulled from stock and shipped to you. Congratulations, you have just accomplished an e-commerce transaction.
Skunkworks
Term for usually-secret high-pressure / high-tech research group in a company or government, often populated by people who work 24-hours a day under much pressure, don't see much sunlight, and don't have much time for washing. Hence the name, skunkworks, as in skunk, an animal which can smell big time. Original usage was from the comic strip, L'il Abner. Lockheed, the maker of the stealth airplane, had a top-secret project which it set up in a defunct airplane hangar in Burbank, California next to what is now the Burbank-Glendale-Pasadena Airport (but everyone just shortens it to Burbank Airport) but then it was owned by Lockheed and run by the legendary Kelly Johnson,. There they built thousands of the great B-17s and P-38 fighters in addition to dozens of secret projects including the Stealth fighter but also the SR-71 and U-2 spy planes. Now, it is a vacant lot without even a plaque to commemorate its place in American aviation history. Later Ben Rich, who ran the operation for a while, wrote a great book called Skunkworks.
Sky Station
Sky Station International Inc. (Washington, D.C.) intends to deliver wireless broadband services through solar- powered communications platforms measuring approximately 200 feet in both length and width. The platforms will be held aloft by tethered balloons floating at altitudes of about 14 miles. Each communications platform will serve an area of about 465,000 square miles, providing up to 150,000 channels of 64 Kbps; the theoretical maximum, according to Sky Station, is 650,000 channels. As many as 250 of the airships are planned, with the total cost estimated at $7.5 billion. Subject to approvals from the FCC and the ITU-R, the first test is scheduled for October 1997. Commercial service is planned for the New York City area in 1999, with coverage intended for 95% of the world's population by 2005. Company officials include former U.S. Secretary of State and NATO commander Alexander M. Haig.
Skycraper Ad
Unlike the more common banner ads, which you see on web sites and which are bars placed across a Web page, these are advertisements that appear as vertical bars, typically down the right-hand side of the visible area, often containing snazzy Flash animations and other tricks. Sometimes also called tower ads.
Skype
Skype, which rhymes with "hype" and has no particular meaning, allows free voice phone calls over the Internet between any two users who have downloaded the software to their PCs ” desktops or laptops (but not Macs, so far). It is simple to use and provides amazingly clear phone calls to anyone with a broadband Internet connection. Skype uses a technology called "voice over Internet protocol," or VoIP. By routing calls over the Internet, VoIP essentially turns computers into phones. It is the core technology driving a number of small phone companies, e.g. Vonage, and is causing headaches for traditional phone companies who are trying to fend off the new VoIP rivals even as they attempt to integrate VoIP into their own systems. Skype uses Peer-to-peer ("P2P") technology which was first widely deployed and popularized by file-sharing applications such as Napster and KaZaA. In this context, P2P technology allows users to share, search for and download files and to find users who are presently online. The following are some of the techniques that Skype employs to deliver IP-based telephony (these come from Skype's web site):
-
Firewall and NAT (Network Address Translation) traversal: Non-firewalled clients and clients on publicly routable IP addresses are able to help NAT'ed nodes to communicate by routing calls. This allows two clients who otherwise would not be able to communicate to speak with each other. Because the calls are encrypted end-toend, proxies present no security or privacy risk. Likewise, only proxies with available spare resources are chosen so that the performance for these users is not affected.
-
Global decentralized user directory: Most instant message or communication software requires some form of centralized directory for the purposes of establishing a connection between end users in order to associate a static username and identity with an IP number that is likely to change. This change can occur when a user relocates or reconnects to a network with a dynamic IP address. Most Internet-based communication tools track users with a central directory which logs each username and IP number and keeps track of whether users are online or not. Central directories are extremely costly when the user base scales into the millions. By decentralizing this resource-hungry infrastructure, Skype is able to focus all of our resources on developing cutting-edge functionality.
-
Intelligent routing: By using every possible resource, Skype is able to intelligently route encrypted calls through the most effective path possible. Skype even keeps multiple connection paths open and dynamically chooses the one that is best suited at the time. This has the noticeable effect of reducing latency and increasing call quality throughout the network.
-
Security: Skype encrypts all calls and instant messages end-to-end for privacy. Encryption was necessary since all calls are routed over the public Internet. See VoIP. www.skype.com.
Skyplex
Skyplex is an on board multiplexer used on DVB (Digital Video Broadcasting) satellite transmission. It means that several satellite uplink stations can transmit in SCPC (single channel per carrier) mode. On the transponder this SCPC flows have multiplexed by skyplex in TDM and then, in the downlink you have an high rate DVB stream (27.5 million symbols per second). This flow is modulated in QPSK mode. The Digital Video Broadcasting Group is a European organization which publishes its work through ETSI that has authored many specifications for satellite and cable broadcasting of digital signals. See DVB and SCPC.
SLA
See Service Level Agreement.
Slab on Grade
Concrete floor placed directly on soil, without basement or crawl-space.
Slam Dunk
A sure thing. Something easily done. "The customer desperately needs our product. This sale is a slam dunk." The expression comes from the basketball expression where the shooter, lacking any opposition , jumps up, grabs the bar and pushes (i.e. slams) the ball into the hoop with great force.
Slamming
Slamming is the practice of switching a telephone customer's long distance supplier without obtaining permission from the customer. It is illegal. A long distance company might do slamming to get itself some easy revenues . Slamming has become increasingly common in recent years as the long distance industry has seen its revenues per minute drop and dishonest telemarketing companies hired by the major long distance companies have slammed telephone users in order to get themselves some easy revenues. Often these telemarketers are paid by the long distance company on the basis of customers switched. In a "60 Minutes" TV show of December 16, 2001, Richard Blumenthal, the Connecticut Attorney General, said "Competing by cheating has become a way of life for the telecommunications industry for many of these corporations, many of the most reputable of them." According to co-host, Steve Croft, "Blumenthal has sued AT&T for billing people who aren't their customers and Qwest for a practice called slamming, stealing their competitors ' customers by forging their signatures on authorization forms." Blumenthal said, "We've seen cases where AT&T continued sending people bills after they sought to terminate the service. We've seen companies like Qwest send people bills for service that was never ordered or requested."
In December, 2001 I asked Verizon for their advice to consumers to protect themselves against slamming. Here is the advice I received:
-
Review your phone bill thoroughly. (That seems obvious but, as you pointed out, many people just give the bill a cursory glance.)
-
Don't divulge personal information such as your telephone number, credit card number or social security number on any sweepstakes or raffle tickets. This information can be misused.
-
Read the fine print on all contracts, applications and contest entry forms you sign. Avoid filling out contest entries that seem vague. (Sometimes these items contain fine print that authorizes a switch of your long distance carrier.)
-
You may contact your telephone company's business office and put a PIC (primary interexchange carrier) freeze on your choice of long distance (and local and regional) carrier. That prevents future changes from being made without your authorization.
-
Slamming is prohibited by state and federal laws. Victims of slamming are entitled to be switched back to the company of their choice at no charge and to have any disputed charges billed at the original company's rate. If you want to verify your carrier, a pre-recorded message will tell you the name of your carrier. For Interexchange Carriers (IXCs), dial 1-700-555-4141. For Local Exchange Carriers (LECs), dial 1-your area code-700-4141.
SLARP
Serial Line Address Resolution Protocol. A proprietary Cisco protocol used in mapping IP (Internet Protocol) addresses. SLARP is used in the initialization of new routers and servers in situations where a serial line interface is involved. The initialization process requires that the router or server discover the IP addresses of the various networked devices, and map internal IP addresses, including subnet masks, to registered IP addresses. Alternative protocols used include BOOTP and RARP. See also ARP, BOOTP, and RARP.
Slashdot Effect
A sudden increase in load on a web server that results in either tremendous slowdown or total failure of the server. The slashdot effect occurs when a site is "backlinked" by a much more popular site. Originated from the website Slashdot (www.slashdot.org), a site with millions of visitors daily. People began to observe that once a site was linked on Slashdot, traffic would explode, often overwhelming the unprepared servers. If this happened , you were "Slashdotted". Someone wrote a paper formalizing and studying the "Slashdot Effect". Ironically, this link was posted on Slashdot and the site fell victim to the Slashdot Effect.
Slave
A device which operates under the control of a master ” another device or system. Slave switching systems are common in rural areas. The master central office might be in town A. Twenty miles away there's a smaller town. It makes no economic sense to serve those subscribers each on single local dedicated loops from Town A. Best solution: place a "slave" central office in that distant town and drive its software, diagnostics and changes from the main central office in Town A. See also Remote Concentrator.
Slave Unit
A Bluetooth term. All devices in a piconet that are not the master. See Bluetooth.
SLC
-
Subscriber Line Charge. A charge on the monthly bill of a phone subscriber in the United States, which produces revenues for the local telephone company. The money collected from the subscriber line charge is used to compensate the local telephone company for a part of the cost of the installation and maintenance of the telephone wire, poles and other facilities that link your home to the telephone network. These wires, poles, and other facilities are referred to as the "local loop." The SLC also is known variously as the Access Charge, CALC, and EUCL. See also Access Charge.
-
Schools and Libraries Corporation. See that term for a full explanation.
-
Subscriber Line Carrier, or Subscriber Loop Carrier. See SLC-96 and SLCC.
SLC-96
Subscriber Line Carrier 96. Pronounced "Slick 96." A short haul multiplexing device which enables up to 96 analog telephone customers to be served over a single four- wire digital circuit. SLC-96 essentially functions as a remote concentrator for up to 96 analog local loops. Here's how it works: A neighborhood of 96 residential and small business telephone customers normally would require 96 analog local loops from the LEC (Local Exchange Carrier) CO (Central Office), with each requiring a two-wire circuit all the way from the CO to the premises. That's very facilities- intensive , which translates into "expensive." SLC-96 allows the LEC to run a four-wire digital circuit to the neighborhood. That circuit is a T-2 circuit, which is a digital T-carrier circuit supporting 96 digital voice-grade channels. The SLC-96 concentrates the 96 voice-grade local loops, digitizing them in the process. SLC-96 is much more cost-effective than the original approach since it uses fewer wire pairs, even though it does require special electronics to accomplish this minor feat. On the other hand, SLC-96 limits each subscriber to a voice-grade circuit of 64 Kbps, which fact absolutely kills DSL (Digital Subscriber Line) technologies currently being deployed in support of high-speed Internet access. See also Digital Subscriber Line, T-2, and T-carrier. See SLCC.
SLCC
Abbreviation for Subscriber Line (or Loop) Carrier Circuit, and pronounced "slick." It's a system that allows one pair of wires, that would normally provide one phone line, to carry multiple conversations. Various models are available, with capacity ranging from 2 to 96 lines. A SLCC is used between phone company central offices and areas where there are too many customers for the cable that is in place. It's much less expensive to install SLCCs than new cable, but the SLCC provides lower-than-normal line voltage, which may cause some phones to malfunction.
SLED
Single Large Expensive Disk. The opposite of RAID (Redundant Array of Inexpensive Disks). See Raid and Redundant Array of Inexpensive Disks.
SLEE
Service Logic Execution Environment. An AIN term. See AIN.
Sleep Mode
-
A means of increasing the battery life of portable computers. When you are using your laptop and are running on battery power, the computer will "go to sleep," if you are not actively using it for some the system "times out." When you move the mouse or touch a key, the system springs back into life. See also Hibernation.
-
A feature of digital cellular phones, allowing the phone to remain active, but not "on," when you are not engaged in a call. The phone sleeps most of the time, awakening every few milliseconds to check for incoming calls. Sleep Mode extends battery standby time by 300% or so.
Sleep Tight
In Shakespeare's time, mattresses were secured on bed frames by ropes. When you pulled on the ropes the mattress tightened, making the bed firmer and more comfortable to sleep on. That's where the phrase, "good night, sleep tight" came from.
Sleeping RSU
When a remote service unit goes into a sleep mode when the tap gets too hot and is unable to reset, thus causing NDT (no dial tone). Load was taken off the RSU and then turned back on, thus resetting the RSU.
Sleeves
Short lengths of conduit, usually made from rigid metal pipes, used to protect cables entering a premises through a building wall or running through concrete floors between vertically aligned riser closets. Sleeves also provide for easy pulling of cable.
SLI Code
See CLLI Code.
SLIC
Subscriber's Line Interface Circuit, a device that interfaces the SLC series of Lucent's products of local subscriber pair gain or multiplexing devices. See SLC-96.
Slideware
Slideware is hardware or software whose reason for existing (eventually) has been explained in 35-mm slides, foils, charts and/or PC presentation programs. Slide is best described as "virtual vaporware." Vaporware is software which has been announced, perhaps even demonstrated, but not delivered to commercial customers. Hyperware is hardware which has been announced but has not yet been delivered. Slideware is less real than vaporware or hyperware. Classic slideware is the ISDN deployment strategies of many of the telephone companies in the United States. See also Hookemware, Hyperware, Meatware, Podiumware, Shovelware, and Vaporware.
Sliding Window Flow Control
Method of flow control in which a receiver gives the transmitter permission to transmit data until a window is full. When the window is full, the transmitter must stop transmitting until the receiver advertises a larger window. TCP, other transport protocols, and several data link layer protocols use this method of flow control.
SLIP
-
Serial Line Internet Protocol. An Internet protocol which is used to run IP datagrams over serial lines such as telephone circuits. Defined in the IETF's RFC 1055, SLIP essentially is a framing convention that identifies the end of each IP datagram, and the end of the IP session. As SLIP is not an Internet Standard protocol, specific implementations may vary. CSLIP (Compressed SLIP), defined in RFC 1144, is an enhancement that compresses the TCP/IP headers for transmission over low-speed serial lines. SLIP largely has been superseded by PPP (Point-to-Point Protocol). See IETF, Internet, IP, and PPP.
-
Slip, as in timing. See Timing.
SlipKnot
A graphical browser developed by Peter Brooks and offered as restricted shareware, SlipKnot became popular among dial-up UNIX users in the early days of the Internet and World Wide Web. SlipKnot offered the advantage of not requiring SLIP (Subscriber Line Internet Protocol), PPP Point-to-Point Protocol), SLIP/PPP emulators, or TCP/IP software on the client side. All SlipKnot users required was a modem and a dial-up UNIX shell account with an ISP. SlipKnot is largely a thing of the past, as are dial-up UNIX accounts. SLIP, PPP, TCP/IP and Winsock are virtually ubiquitous today. SlipKnot now is considered to be way underpowered, as it is a 16-bit only solution that lacks the feature content embedded in contemporary browsers.
Slip Multiplication
See Network Slip.
Slip Sleeve
An oversized conduit that moves easily along an inner conduit and covers a gap or missing part of the smaller conduit.
Slip/Slip Rate
The loss (or rate of loss) of a data bit on a T-1 link due to a frame misalignment between the timing at a transmit node and timing at a receive node. See Timing.
Slip-Controlled
The occurrence at the receiving terminal of a replication or deletion of the information bits in a frame.
Slip-Uncontrolled
The loss or gain of a digit position of a set of consecutive digit positions in a digital signal resulting from an aberration of the timing processes associated with the transmission or switching of the digital signal. The magnitude or the instant of the loss or gain is not controlled.
Slist
Connected to a NetWare network? Type Slist in DOS on your PC and you will get a list of all the NetWare servers you are connected to.
SLM
-
System Load Module.
-
Service Level Management. See Service Level Management.
Slope
-
See Chromatic Dispersion.
-
Often refers to the slope of an amplifier curve.
Sloppy Clicker
Someone who always manages to move Windows icons on his screen whenever he or she clicks on the icons. This makes the icons move and your computer screen look sloppy.
Slot 1
The specification that addresses the form factor (i.e., physical shape and size ) and the physical and electrical interface for some of Intel's Pentium processors. Slot 1 it is the specification for one or more slots on the PC motherboard that accept a 242-contact daughterboard in the form of a microprocessor cartridge. Intel intends for Slot 1 to replace Socket 7. See also Socket 7.
Slot Antenna
An antenna composed of a dipole across a slot shaped aperture.
Slot Sizes
PCMCIA cards come now in three standard physical slot and card sizes: Type I: 3.3 mm thick, mostly for memory cards. Type II: 5 mm thick, fits most of the current cards on the market, including communications and networking cards. Type III: 10.5 mm, used for cards that have rotating hard disks in them. Toshiba, in its T4600, came out with a fourth size that is 16 mm thick. There is more to compatibility than just fit. The size of the slot is independent of the version of firmware that supports it. Some cards may only work with certain operating systems, BIOS, and drivers. Apple's Newton has a Type II slot but only supports cards that have been designed specifically for it. See Card Services, PCMCIA Standards, Socket Services and Slot Sizes.
Slots
Openings, typically rectangular, in the floor of vertically aligned riser closets that enable cable to pass through from floor to floor. A slot accommodates more cables than an individual sleeve.
Slotted
A Medium Access Control (MAC) protocol is slotted of attempts to transmit can only be made at times that are synchronized between contending devices. A cellular radio term.
Slotted Aloha
An access control technique for multiple-access transmission media. The technique is the same as ALOHA, except that packets must be transmitted in well- defined time slots.
Slotted Ring
A LAN architecture in which a constant number of fixed-length slots (packets) circulate continuously around the ring. A full/empty indicator within the slot header indicates when a workstation or PC attached to the LAN may place information into the slot. Think of a slotted ring LAN as an empty train that constantly travels in a circle, being filled and emptied at different terminals (workstations).
Slotting
The process of assigning a circuit to available channel capacity across the network during the circuit design process. When a circuit is slotted,it has an assigned path from one end of the network to the other.
Slow Switching Channel
A sequencing GPS (Global Positioning System) receiver channel that switches too slowly to allow the continuous recovery of the data message.
SLP
Service Location Protocol. Described in the IETF's RFC 2165, SLP is a TCP/IP-based protocol which allows a computer to automatically discover and make use of network resources available over a corporate Intranet. Such resources might include printers, e-mail servers, Web servers and fax servers. It works like this. The client workstation makes use of a "user agent" to seek out the appropriate server based on its attributes, as "advertised" by "server agents." "Directory agents" serve an intermediary function between the user agents and server agents, aggregating advertisements in order to minimize the amount of time spent searching for the services across all networks and subnetworks in the enterprise Intranet.
SLR
Send Loudness Rating.
SLSA
Single Line Switching Apparatus.
SLT
Single-Line Telephone, as opposed to a phone that has buttons to select from several lines.
SM
-
Switch module.
-
Service Module. An ADSL term for a device which performs terminal adaption functions for access to the ADSL network. Examples of terminal such devices include set-top boxes for TV sets, PC interfaces, and routers for LAN access. See ADSL.
SMG
Wireless-Special Mobile Group. A standards body within ETSI that develops specifications related to mobile networking technologies, such as GSM and GPRS.
SGML
Standard Generalized Markup Language. SGML is basically a standard to take ASCII text and give it meaning in order that many different computers can understand the bits and pieces of it in a standard way ” i.e. all the same. Formally SGML is a document markup language. It was the beginning of a language called HTML which is now on every web page in the world. SGML is not in itself a document language, but a description of how to specify one. It is, in formal language, metadata. SGML is based on the idea that documents have structural and other semantical elements that can be described without reference to how such elements should be displayed. The actual display of such a document may vary, depending on the output medium and style preferences. Some advantages of documents based on SGML are:
They can be created by thinking in terms of document structure rather than appearance characteristics (which may change over time). They will be more portable because an SGML compiler can interpret any document by reference to its document type definition (DTD). Documents originally intended for the print medium can easily be re- adapted for other media, such as the computer display screen. The roots of SGML go back to the late 1960s when there was no GUI (graphical user interface). All computers displayed was text. After companies started using computers for document processing, it soon became obvious that a storage format should contain not only formatting codes interpreted by computer itself, but also descriptive human-legible information about the nature and role of every element in a document. The best use of SGML is generally made in big corporations and agencies that produce a lot of documents and can afford to introduce a single standard format for internal use.
XML is a simplified subset of SGML. See HTML and the World Wide Web.
S2M
A European term for PRI ISDN, more commonly called PRA in Europe.
SMA
-
Subscriber Carrier Module-100A; same as SCM-100A.
-
Spectrum Management Agency. Former Australian agency established in 1993 to manage access and use of the radio spectrum. The SMA merged with AUSTEL on July 1, 1997, to form the Australian Communications Authority (ACA).
SMA 905/906
(Subminiature type A). A former microwave connector modified by Amphenol to become the "standard" fiber optic connector. The 905 version is a straight ferrule design, where as the 906 is a stepped ferrule design and uses a plastic sleeve for alignment.
Small Computer System Interface
SCSI. Pronounced scuzzy, SCSI is a bus that allows computers to communicate with any peripheral device that carries embedded intelligence. The standard is covered by the American National Standards Institute (ANSI) and has developed into from SCSI-1 into SCSI-2 and, now SCSI-3. Different types of device can be connected in a daisy chain via a 50-pin cable (68-pin for SCSI-3), both ends of which must be terminated . All signals on the cable are common to all devices. To avoid bus contention , each device (up to a maximum of seven) connected to the bus is given a unique "SCSI" address with each address being allocated a degree of priority. The SCSI-1 bus carries 8-bit data, 1-bit parity and 9-bit control lines, to provide a maximum synchronous data transfer rate of 5 Mbyte/s.
The maximum bus length is dependent upon the type of bus driver/receiver used. For single-ended devices, the length is restricted to 6 meters, but you wouldn't want to go that far. A desktop is about the maximum distance for an un-amplified SCSI-1 bus. The 6 meters can be extended to 25 meters through the use of differential driver/receivers. SCSI-2 has been extended to increase the data rate to 10 Mbyte/switch via either 16 or 32-bit processors. The maximum data rate is thus nearer to 40 Mbyte/s. The protocol has also been expanded to include tagged commands. This allows the execution of queued control commands according to a prescribed sequence. For a bigger explanation, see SCSI, SCSI-2 and SCSI Transfer Rate.
Small Fortune
The only sure way to make a small fortune ” in telecommunications, networking, computing, or in anything ” is to start with a large one. After the Nasdaq Bubble burst in the Spring of the year 2000, many investors made small fortunes by losing a lot of their large fortunes. It was called the Tech Wreck of 2001.
Small Vocabulary
A voice recognition term. Vocabularies containing fewer than 50 words.
Smart Agent
A software tool that acts like you. It is your agent and it acts intelligent on your behalf. For example, you might ask assign it a series of tasks to do on your behalf every day, or even throughout the day. For example, "Which orders that I sold today have been shipped today?" See Intelligent Agent and Smart Messaging.
Smart Antenna
A fancy name for a new type of cellular base station antenna. The technology replaces conventional cell-site antennas with a multibeam antenna array that allows network operators to target the transmission and reception of calls more precisely and therefore reduce the amount of spectrum consumed and the amount of interference. The basic benefit of a "smart antenna" is to allow a cell phone provider to serve more cell phone customers without a new investment in basic cell site radio and electronics.
Smart Battery
A type of battery that uses electronic circuitry to provide its host device (phone or notebook) with status power information so the system can conserve power intelligently.
Smart Battery Data
SBD. The information accessible across the System Management Bus between the smart battery and the device.
Smart Border
Name given to a new initiative to upgrade border surveillance technologies and procedures after terrorist traffic between Canada and the US.
Smart Building
Also referred to as the "intelligent" building. A centrally managed structure that offers advanced technology and perhaps shared tenant services. Central to the early ideas of a smart building was the concept of one gigantic phone system shared by all the tenants. The idea was that you needed a big switch to get lots of features and all the benefits of cheap long distance. That's no longer true. Small switches offer much the same benefits. Now buildings are often smart, but frequently they're smart, using those smarts to save energy and insure safety and less to share telephone service among the tenants, who have shown a tendency to fend for themselves.
Smart Card
A credit card- sized card which contains electronics, including a microprocessor, memory and a battery. The card can be used to store the entire repair and maintenance history on the family automobile or the health history of a member of the family. Since smart cards are tamper-resistant hardware devices that store your private keys and other sensitive information, they can be used for security applications. There is no direct contact between the "smart card" and the device which reads it. This avoids the problem of wear that afflicts traditional credit cards ” both their embossed numbers on the front and their magnetic strip on the back. According to the Smart Card Industry Association, a smart card is any card with a microprocessor. Non-smart chip cards are simple memory cards and hardwired logic cards. As the smart card has developed, we see new and specialized versions of it. Memory cards store information or values, such as debit or credit information. Processor cards perform calculations, complex processing and security applications. Contact cards read information when a card is inserted into a reader. Contactless cards wirelessly read information. Combicards uses both a card reader and a wireless device. See also Satellite Television Smart Cards.
Smart Chip
This is a chip used by GSM cell phones (also called mobiles) that stores information about the calling network. Phones that use a smart chip (also referred to as a SIM) can be easily upgraded to use different networks (such as a European GSM system). The chips also store personal information, such as your phone book, making it easy to transfer your information to a new phone. See also SIM Card.
Smart Display
A flat screen touchscreen display with processing intelligence and communications. One idea is that you carry this device around your house and use it as a portable, fast-starting, simple PC ” to look up recipes, to check your email, etc.
Smart Dust
The Economist of February 2, 2002 wrote, "When peripatetic futurologists such as John Gage of Sun Microsystems really want to impress their audience, they talk about 'smart dust'. The concept is indeed intriguing. The dust in question is made up of tiny, wireless sensors that could be dispersed anywhere ” say, over a battlefield to find out where enemy troops are, or whether chemical or biological weapons have been used. This is not science fiction . Researchers at the University of California at Berkeley led by Kris Pister, a professor of electrical engineering, are already working on a smart-dust prototype the size of a small nailhead. A klunkier version can already be bought from a Silicon Valley start-up, Crossbow Technology. It may be decades before smart dust is dispersed over real battlefields, but the tiny devices are at the forefront of an important technological trend that is often underestimated: the spread of sensors and tags. New manufacturing processes, wireless technology and intelligent software are making them ever smaller, smarter and, most important, cheaper. As with microprocessors and lasers in earlier decades, the novelty is not that these sensors exist at all, but that they have suddenly become cheap enough to be used in ordinary everyday products, says Paul Saffo, director of the Institute for the Future, a Silicon Valley think-tank."
Smart Home
The 1990's catch phrase was "smart home," for houses with Internet- linked appliances that could, for example, tell when you ran out of milk and automatically order more, or chill the wine while you were still on the expressway. It never quite happened that way, though some early adopters have had fun testing the latest electronic gizmos. But by the early 2000s, the smart home began to center around the centralized home entertainment system, with personal video recorders , with "digital plumbing" for Internet and television connections hidden behind walls, and just enough equipment to make tapping into video, images (photos of the kids) and audio (Bob Dylan's latest and greatest). The backbone of any networked home is "structured wiring," a bundle of high- speed cables put in the walls before the drywall goes on or wireless links put in after the walls are closed. More builders are including such cables automatically. They add to the resale value of the house.
Smart Hub
A concentrator, used in Ethernet or ARCnet networks, with certain network-management facilities built in to firmware that allow the network administrator to control and plan network configurations; also known as an intelligent hub. In token-ring networks
Smart Hunt Groups
Picture a call center with people answering the phone from customers. The people answering the phone have different skills, know different things about the company's products, and are thus better able to answer some questions better than others. Now picture that the phone system the people is using is "smart" and somewhere in it and in the databases attached to it, it knows who of the people (also called agents) is good at what. What skills they have. What they know about which products, etc. Then, by asking questions of incoming callers through a combination of an attached interactive voice response system, the incoming caller's phone number and the number the caller dialed, it is able to route the call to the exact correct person. If that correct person is not available, it routes the caller to another person. And to another, etc. There may be many smart hunt groups, each consisting of the same people. If you think of a call center with several hundred people you can easily see it's possible to have potentially thousands of "smart hunt groups." Just depends on how complex your product line is and how sophisticated you want to get. The term was coined by Rick Luhmann, editor of Computer Telephony Magazine, New York, NY.
Smart Jack
Industry term for the device to test integrity of T-1 circuits remotely from the central office. Installed on the customer premises in the form of a semi-intelligent demarcation point (demarc), the smart jack is completely passive until activated remotely by a digital code, typically something like "FACILITY 2," sent down the T-1. This code activates a relay that breaks the T-1 circuit and closes a receive-to-transmit loop across the T- 1 at the customer end, sending the signal back to the central office (CO). This allows the CO to confirm the integrity of the loop without having to dispatch a technician to the site. Once the loopback test is completed, the relay automatically resets. The advantage of a smart jack is that the carrier can accomplish the loopback without engaging the DSU/CSU, which typically is in the CPE (Customer Premise Equipment) domain (i.e., it is customer- owned and, therefore, can possess uncertain attributes). As a result, the smart jack does not short when disconnected from the DSU/CSU; therefore, it always is available to the carrier for purposes of conducting such a loop test. The smart jack commonly has the same appearance as does a RJ48 jack; indeed, a RJ48 cable can connect the smart jack and the DSU/CSU to provide a hard-wired shorting function. The smart jack also may be rack- mounted. See also CSU, Demarc, DSU, Loopback, and RJ48C.
Smart label
A label that contains an RFID tag. It's considered "smart" because it can store information, such as a unique serial number, and communicate with a reader. See RFID.
Smart Mob
Coined by cyberpundit Howard Rheingold to describe mass social movements coordinated through wireless communications. In other words protests coordinated by cell phones.
Smart Phone
A generic term for a phone with PC-like intelligence and perhaps a slightly larger screen which could display stock price information, bank balances , etc.
Smart Radio
Also referred to as a software radio. An advanced radio in which frequencies, tuning, and protocols are defined using software programming, rather than fixed hardware. Such a radio might be used for a wireless handset or base station, giving it the capability of utilizing various previously incompatible protocols interchangeably, such as AMPS, GSM, and CDMA.
Smart Retries
A term used in the fax blasting industry to refer to doing different retries based on the status of the failed fax. For example, you might receive a busy and then retry 3 times 10 minutes apart, then 2 times more eight hours later. Another smart retry might be to restart sending a multi page fax at the page that the failed fax stopped at. This feature might also have an alternate cover page that can say that this fax is a continuation of a previous fax that didn't make it fully.
Smart Terminal
A data terminal capable of operating in either a conversational or a block mode; containing a full set of local editing capabilities without reliance on a controlling external computer.
Smart T-1
What some companies call metered T-1 or fractional T-1.
Smart Web Browsers
A Web Browser is a piece of software which allows you to search the World Wide Web for information. A smart Web Browser will contain a modicum of intelligence, allowing it to find what you're looking for faster, easier and less time consuming.
SmartHouse
The National Society of Home Builders has registered SmartHouse. BellSouth has trademarked SuperHouse. And GTE has registered SmartPark. One day, the theory is, fiber optic will snake to everyone's house, bringing the potential of immense information services. Until that day comes, there'll be neat demonstrations at trade shows. See also Picturephone, another product that made great demonstrations .
Smartphones
The term came into being in 2003 when some manufacturers started joining PDAs (personal digital assistants) with cell phones. And various people called the result "smartphone." Smartphones can be used to store addresses and phone numbers, which can then, with the touch of a stylus, be dialed with the cell phone. Smartphones can play games , music and jot down short messages to transmit and receive. Some smart- phones also sport tiny keyboards.
SMAS
Switched Maintenance Access System.
SMATV
Satellite Master Antenna Television. A distribution system that feeds satellite signals to hotels, apartments, etc. Often associated with pay-per-view.
SMB
-
Server Message Block. The protocol developed by Microsoft, Intel, and IBM that defines a series of commands used to pass information between network computers. The redirector packages SMB requests into a network control block (NBC) structure that can be sent over the network to a remote device. The network provider listens for SMB messages destined for it and removes the data portion of the SMB request so that it can be processed by a local device. In short, SMB is basically a protocol to provide access to server-based files and print queues. SMB operates above the session layer, and usually works over a network using a NetBIOS application program interface. SMB is similar in nature to a remote procedure call (RPC) that is specialized for file systems.
On June 13, 1996, Microsoft said, "The SMB protocol is an open technology widely available on UNIX, VMS and other platforms. It has been an Open Group (formerly X/Open) standard for PC and UNIX interoperability since 1992 (X/Open CAE Specification C209), and it is supported in products such as AT&T Advanced Server for UNIX, Digital's PATHWORKS, HP Advanced Server 9000, IBM Warp Connect, IBM LAN Server, Novell Enterprise Toolkit, and 3Com 3+Share, among others. SMB is also the featured file and print sharing protocol of Samba, a popular freeware network file system available for LINUX and many UNIX platforms."
The above Microsoft words came in a press release announcing something called CIFS, which is essentially an enhanced version of SMB. See CIFS.
-
Small and medium business.
SMBus
System Management Bus. A two-wire bus for more intelligent handling of rechargeable batteries in portable stuff, like laptops.
SMC
Standard Management Committee. Directs specialized working groups of the Architecture and Standards Steering Council.
SMDA
Station Message Detail Accounting. Another name for telephone call accounting. See Call Accounting System.
SMDI
Station Message Desk Interface or Simplified Message Desk Interface. The SMDI is the data link from the central office if you have ESSX, Centrex or Centron (etc.) that gives you your stutter dial tone or message waiting light. In essence, SMDI is a data line from the central office containing information and instructions to your on-premises voice mail box. With SMDI, the calling person is not required to re-enter the called phone number (or in any other way identify the called party) once the call terminates to the messaging system.
SMDR
Station Message Detail Reporting. Another name for telephone call accounting. See SMDR PORT and Call Accounting System.
SMDR Port
Modern PBXs and some larger key systems have an Station Message Detail Recording (SMDR) electrical plug, usually an RS-232-C receptacle, into which one plugs a printer or a call accounting system. The telephone system sends information on each call made from the system to the outside world through the SMDR port. That information ” who made the call, where it went, what time of day, etc. ” will be printed by the printer or will be "captured" by the call accounting system on a floppy or a hard magnetic disk and later processed into meaningful management reports . See Call Accounting System.
SMDS
Switched Multimegabit Data Service. A connectionless high-speed data transmission service intended for application in a Metropolitan Area Network (MAN) environment. SMDS is a public network service designed primarily to for LAN-to-LAN interconnection. An offshoot of the Distributed Queue Dual Bus (DQDB) standard defined by the IEEE 802.6 standard, SMDS owes its commercial success to Bellcore, which refined and commercialized it at the request of the RBOCs as a MAN service appropriate for RBOC offering within the confines of a LATA. SMDS offers bandwidth up to T-3 (45 Mbps) and the critical advantage of excellent congestion control, which virtually ensures that data arrives intact and as transmitted. SMDS supports asynchronous, synchronous and isochronous data. Although intended as a MAN service offering, it is possible to extend its reach over the WAN. SMDS is a cell-switched service offering, based on a 53-octet cell with a 48-octet payload similar to that of ATM. SMDS involves a process of converting data into cells before presentation to the network. Each set of data in its native form can be as much as 9,188 octets in length, constituting what is known as a Protocol Data Unit (PDU). At the point of SMDS processing, that PDU becomes known as a SMDS Service Data Unit (SDU), which is then appended with a header and trailer which contain network control information. The SDU, with header and trailer, is then segmented into units of 48 octets, each of which is prepended with a header and appended with a trailer before presentation to the SMDS network in the form of a 53-octet cell. Prepended means preceded as part of the same data unit (generic "packet"), whereas appended means succeeded as part of the same data unit. In fact, SMDS was designed with ATM in mind, providing a smooth transition path to ATM by virtue of the size of both the overall cell cell and the payload, although the specifics of the cell structure and other elements of the specific protocols are quite different. SMDS garnered a good deal of interest during the early 1990s, although broad support never developed. SMDS is not widely available and is highly unlikely to ever gain a broad level of acceptance; Frame Relay and ATM, in particular, have and will continue to overshadow SMDS. See The SMDS Interest Group.
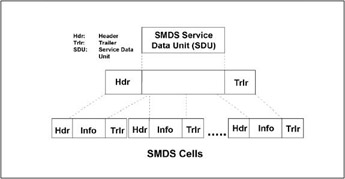
SMDS Interest Group
A defunct consortium of vendors and consultants who were committed to advancing worldwide SMDS as an open, interoperable solution for high- performance data connectivity. On June 16, 1997, the Board of Trustees announced that the group was disbanded, turning over all responsibilities to regional organizations. The Board declared that its mission had been fulfilled.
SMDSU
Switched Multimegabit Data Service Unit. See DSU.
SME
-
Small to medium enterprises . Commonly used by EC & EDI folks.
-
Security Management Entity.
Smear
The undesirable blurring of edges in a compressed image, often caused by the DCT (Discrete Cosine Transform) which tends to eliminate the high-frequency portions of an image which represent sharp edges. See also Discrete Cosine Transform.
Smell-O-Vision
Hans Laube was a Swiss professor of osmics, which is the science of smells. He invented a process for reproducing smells in movie theaters, which process he named "Scentavision," and which later became known as Smell-O-Vision prior to its introduction in the 1960 film "Scent of Mystery." According to articles written at the time, this development had been long awaited. Movies (moving pictures) were introduced in 1895, "talkies" (talking pictures) in 1927, and "smellies" (smelling pictures) finally in 1960. The name "Smell-O-Vision" was coined by Michael Todd, Jr. (son of Michael Todd Sr., who was one of Elizabeth Taylor's many husbands). The squirters that blasted the smells into the theater were queued from the soundtrack. Apparently, the smells were awful , and became worse as they lingered. The copycat technique of AromaRama was equally unsuccessful . Vibrating chairs were introduced for the cult classic film "The Tingler," but fared no better. Smellies were revived briefly in the film "Odorama" (1981), which relied on scratch n' sniff cards that were handed out to audience members, who were instructed to scratch 'n sniff them at special moments during the film. The concept has now been revived with the introduction of "iSmell," as in "internet Smell," introduced by Digiscents. Digiscents indexes various scents according their chemical compositions, and their place in the scent spectrum. The desired scent index is then described in a small file, which can be attached to any kind of Web content, interactive games, e-mail, movies, music, or other IP (Internet Protocol) file. The intended scent is recreated by your computer through personal scent synthesizers, which plug into your computer much like audio speakers . The personal scent synthesizers connect to your computer through your computer's serial port or USB (Universal Serial Bus) port, and are locally powered. They emit smells on command, such as a mouse click or a timed response triggered by a DVD or CDROM. The scents are recreated by an indexed combination of over 100 basic scents that are selected from a palette of scented oils, with the scent cartridges being refillable. Refills will be available from www.snortal.com, if this idea ever takes off. "Snortal," of course, is a contraction of the words "snort" and "portal."
SMF
Single Mode Fiber. Also known as monomode fiber, SMF has a much thinner inner core (8-10 microns, or so) than MultiMode Fiber (MMF). The thin inner core allows light pulses to propagate along only a single mode, or physical path, which significantly reduces the potential for various forms of dispersion. As dispersion causes signal distortion, SMF is used in applications that cover long distances at high speeds. SMF types include Non Dispersion Shifted Fiber (NDSF) and Dispersion Shifted Fiber (DSF). See also DSF, MMF, and NDSF.
SMF-PDM
The ANSI X3T9.5 PDM standard which defines the requirements for the transmission of data over single mode fiber in an FDDI topology. Also refers to the ANSI working group responsible for the development and perpetuation of the standard.
SMF
Single Mode Fiber: Fiber optic cable in which the signal or light propagates in a single mode or path. Since all light follows the same path or travels the same distance, a transmitted pulse is not dispersed and does not interfere with adjacent pulses. SMF fibers can support longer distances and are limited mainly by the amount of attenuation. Refer to MMF.
SMI
Structure of Management Information. The set of rules and formats for defining, accessing and adding objects to the Internet MIB. SMI was elevated to full standard status in May 1990.
SMIL
Synchronized Multimedia Integrated Language. Pronounced "SMILE." A recommendation from the World Wide Web Consortium (W3C) for a stylized layout language for the creation of Web-based multimedia presentations. SMIL, which is compliant with XML (eXtended Markup Language), defines the mechanism by which authors can compose a multimedia presentation, combining audio, video, text, graphics. SMIL allows the synchronization of these multimedia elements in terms of their presentation on screen, as well as the timing of their delivery to the client. The resulting SMIL file (.smi) offers the advantage of being in the form of a simple, markup text file that can be created with any text editor. Current members of the W3C Working Group developing SMIL Boston (the latest version) are key international industry players in Web multimedia, interactive television and audio/video streaming: Canon, Compaq, CSELT, CWI, France Telecom, Gateway, GLOCOM, INRIA, Intel, Macromedia, Microsoft, Oratrix, NIST, Nokia, Panasonic, Philips, RealNetworks and WGBH.
SMIL 1.0 is the W3C standard for Web-based multimedia first implemented by RealNetworks with the advent of RealSystem G2 in June of 1998. RealNetworks coauthored the SMIL 1.0 specification. SMIL 1.0 enables the delivery of long format, Web- based multimedia to a broad range of audiences, from modems to T-3 Internet connections. As an open XML-based language, SMIL enables a wide range of audio-visual presentation authoring environments,ranging from simple text editors to graphical editing tools such as RealNetworks RealSlideshow. The SMIL Boston Working Draft proposes several extensions to SMIL 1.0, such as integration with TV broadcasts, animation functionality, improved support for navigation of timed presentations, and the possibility to integrate SMILmarkup in other XML-based languages. See also W3C and XML.
Smiley Face
:) The "smiley face is probably the most popular emoticon, from Emotional Icon. The original smiley face (the one that you see on T-shirts and buttons) was created by commercial artist Harvey Ball in 1963 as part of an in-house friendship campaign for state Mutual Life Assurance, a Massachusetts insurance company. Ball received $45 for the creation, which he failed to patent. Ball died on April 13, 2001, at the age of 79. :( See also Emoticon.
SMM
System Management Mode. See APM.
Smoke Test
Test of new or repaired equipment by turning it on. If there's smoke, it doesn't work!
Smokeware
When manufacturers announce new products, sometimes the products are not ready. Smokeware derives from the expression "smoke and mirrors."
SMOP
Small Matter of Programming. A little software and it will all work. Yeah!
Smooth Call Arrival
A call center term. Calls that arrive evenly across a period of time. Virtually non-existent in incoming environments.
Smooth Handoff
See Mobile IP.
SMP
-
Symmetric MultiProcessing. The use of several CPUs (i.e. several Intel Pentium chips) inside a PC or (more typically) a server to achieve a performance boost. This is achieved by an operating system that lets CPUs run operations in parallel. This is not a "normal" PC operating system. Normal PC operating systems ” MS-DOS, Windows, etc. ” expect that their work will be done on one processor, not on more than one. See also Symmetric Multiprocessing.
-
SCSA Message Protocol.
-
Simple Management Protocol.
SMPI
SCSA Message Protocol Interface.
SMPP
Short Message Peer-to-Peer Protocol. SMPP. A protocol, developed by Logica Aldiscon, that provides the capability to deliver email and voicemail between wired and wireless networks.
SMPTE
Society of Motion Picture & Television Engineers. An international society dedicated to advancing the theory and application of motion-picture technology including film, television, video, computer imaging and telecommunications. Founded in 1916 as the Society of Motion Picture Engineers , the "T" was added in 1950 in recognition of the emerging television industry. The SMPTE is an accredited ANSI Standards Developing Organization, and is recognized by both the ISO and the IEC. Current membership numbers about 8,500 in 72 countries . www.smpte.org
SMPTE Time Code
A video term. Time code that conforms to SMPTE standards. It consists of an eight-digit number specifying hours:minutes:seconds:frames. Each number identifies one frame on a videotape. SMPTE time code may be of either the drop-frame or non-drop frame type. In GVG editors, the SMPTE time code mode enables the editor to read either drop-frame or non-drop frame code from tape and perform calculations for either type (also called mixed time code). SMTPE is a standardized edit time code adopted by SMPTE, the Society of Motion Picture and Television Engineers.
SMR
Specialized Mobile Radio. Also known as PAMR (Public Access Mobile Radio), PMR (Private Mobile Radio), TMR (Trunked Mobile Radio), and TRS (Trunked Radio System). A two-way radio telephony service making use of macrocells covering an area of up to 50 miles in diameter. The first SMR system was placed in service by the Detroit Police Department in 1921. The first commercial SMR service was offered in 1946 in St. Louis by AT&T. Subsequently, private SMR was widely used, and still is, in dispatch applications by truck and taxi fleets. Eventually, SMR took the form of IMTS (Improved Mobile Telephone Service), which used smaller frequency channels in support of many more conversations through improved efficiency. Many SMR operators have converted their SMR networks to digital so they can deliver both voice and data to a single device with improved efficiency and security, and thus compete with cellular and PCS radio providers. SMR systems have far less radio spectrum than cellular has, but the signal can reach 25 times farther, which means it's cheaper to build a national network. In the U.S., the frequency bands used by SMR include 220 MHz, 800 MHz, and 900 MHz. See also ESMR.
SMRP
Simple Multicast Routing Protocol. Apple Computer's specialized network protocol for routing multimedia data streams on AppleTalk networks.
SMRT
Single Message-unit Rate Timing. USA telephone company tariff under which local calls are timed in 5-minute increments ” with a single message unit charge applied to each complete or partial increment.
SMS
-
Service Management System, a term coined by Bellcore (now called Telcordia Technologies) for the Intelligent Network. The SMS allows provision and updating of information on subscribers and services in near-real time for billing and administrative purposes. See SMSC.
-
Short Message Service. A means to send or receive, short alphanumeric messages to or from mobile telephones. See Short Message Service.
SMS-R
Subscriber Carrier Module-100S REmote.
SMS/800
The national database Service Management System that retains all 800 records. This database provides long distance carriers a single interface for 800 number reservations and record maintenance. Developed by Bellcore, the database has been in use by various Regional Bell Operating Companies (RBOCs) since 1988. The FCC mandated that a neutral third party administer the database after 800 portability, which occurred in May, 1993. That administration responsibility now lies with the SMS/800 Number Administration Committee (SNAC), which is part of the OBF (Ordering and Billing Forum), which operates under the auspices of the Alliance for Telecommunications Industry Solutions (ATIS). See also ATIS, OBF and SNAC.
SMSA
Standard Metropolitan Statistical Area. A metropolitan area consisting of one or more cities as defined by the Office of Management and Budget and used by the FCC to allocate the cellular radio market.
SMSC
Short Messaging Service Center. On a wireless network, SMSC allows short text messages to be exchanged between mobile cell telephones and other networks. Sample message: "Honey, I'll be home late tonight." It is the entity that stores and forwards Short Message Service (SMS) messages. SMSC supports message storage, point-to-point, mobile terminated short message service (SMS-PP/MT). SMSC is being enhanced to support mobile originated messages also. The product can be interfaced with multi-vendor mobile switching centers (MSCs) over an SS7 link; it can work with Gateway as well as non- Gateway MSCs. See SMS and SMSCH.
SMSCH
Short Message Service CHannel. Specified in IS-136, SMSCH carries signaling information for set up and delivery of short alphanumeric messages from the cell site to the user terminal equipment. SMSCH is a logical subchannel of SPACH (SMS (Short Message Service) point-to-point messaging, Paging, and Access response CHannel), which is a logical channel of the DCCH (Digital Control CHannel), a signaling and control channel which is employed in cellular systems based on TDMA (Time Division Multiple Access). The DCCH operates on a set of frequencies separate from those used to support cellular conversations. See also DCCH, IS-136, SMS, SPACH and TDMA.
SMT
-
Surface Mounting Technology.
-
Station Management. The part of FDDI that manages stations on a ring.
-
Simultaneous MultiTasking. The idea of SMT is to mix instructions from different threads or programs (known as "processes") together in the same CPU pipeline. Normally in a microprocessor, a pipeline executes an instruction stream from a single process at a time, just as a car factory assembly line manufacturers one type of vehicle at a time. The
SMTA
Single-line Multi-extension Telephone Apparatus.
SMTP
Simple Mail Transfer Protocol. SMTP is a TCP/IP protocol for sending e-mail between servers. Virtually all e-mail systems that send mail via the Internet use SMTP to send their messages. Typically, you will send your email via SMTP to a POP3 (Post Office Protocol) server, from where your addressee will retrieve your message. Because of SMTP and POP3, you need to specify both your POP3 server and your SMTP server when you configure your e-mail client application, e.g. Microsoft Outlook, Eudora. Your email system will ask you for your SMTP server. Mine is mail.technologyinvestor.com while my POP3 server is mail.technologyinvestor.com. SMTP is actually an application-level protocol which runs over TCP/IP, supporting text-oriented e-mail between devices supporting Message Handling Service (MHS). You can send complex attachments, however, with SMTP, by simply using MIME, which stands for Multipurpose Internet Mail Extension. MIME is an SMTP extension supporting compound mail, which is integrated mail, including perhaps e- mail, a Word document, an Excel spreadsheet, an image, a voice WAV file and perhaps also a video clip in an AVI format. The SMTP is used as the common mechanism for transporting electronic mail among different hosts within the Department of Defense Internet protocol suite. Under SMTP, a user SMTP process opens a TCP connection to a server SMTP process on a remote host and attempts to send mail across the connection. The server SMTP listens for a TCP connection on a well-known port (25), and the user SMTP process initiates a connection on that port. When the TCP connection is successful, the two processes execute a simple request/response dialogue, defined by the SMTP protocol, in which the user process transmits the mail addresses of the originator and the recipient(s) for a message. When the server process accepts these mail addresses, the user process transmits the message. The message must contain a message header and message text formatted in accordance with RFC 822. See also POP3.
SMU
-
Subscriber Carrier Module-100 URBAN.
-
System Management Unit. The card or equipment in an xDSL unit that takes care of the management of the unit.
Smurf Attack
A category of Denial of Service Attack on a computer system. The New York Times defines a smurf attack as involving the use of many spoofed machines "but it also employs a large third party network of computers to "amplify" the data used in the attack and greatly increases the effectiveness of the assault. See Denial of Service Attack and Smurfing.
Smurfing
A Denial of Service (DoS) attack by a hacker, usually a very young hacker hence, the origin of the term. Such an attack involves the sending of a stream of diagnostic "ping" messages to a list of IP servers, each of which forwards them to all LAN-attached workstations, each of which responds. The return address, however, is forged to reflect that of the target of the attack. The resulting stream of responses, which is magnified many times as the pinged servers and attached devices try over and over again to respond, effectively shuts down the targeted server. The targeted server might be a single server or it might be a complete Web site. See also Hacker and www.mcs.net/smurf. See also Smurf Attack.
SN
An ATM term. Sequence Number: SN is a 4 octet field in a Resource Management cell defined by the ITU-T in recommendation 1.371 to sequence such cells. It is not used for ATM Forum ABR. An ATM switch will either preserve this field or set it in accordance with 1.371.
SN Cell
An ATM term. Sequence Number Cell: A cell sent periodically on each link of an AIMUX to indicate how many cells have been transmitted since the previous SN cell. These cells are used to verify the sequence of payload cells reassembled at the receiver.
SNA
Systems Network Architecture. An IBM product. The most successful computer network architecture in the world. See IBM and Systems Network Architecture.
SNAC
SMS/800 Number Administration Committee. SNAC is responsible for administering the Service Management System/800 (SMS/800) database for 800 and other toll-free numbers in the U.S. The SMS/800 database is the central repository for toll-free numbers, identifying the carriers to which they have been assigned, or to which they have been transferred at the request of the user. The SMS/800 database comprises all toll-free numbers, which are defined as 8NN, where NN is a set of two identical numbers (e.g., 800, 888 and 877). SNAC is a committee of the Ordering and Billing Forum (OBF), which operates under the auspices of the Alliance for Telecommunications Industry Solutions (ATIS). See also ATIS, OBF and SMS/800.
SNADS
SNA Distribution Services. An IBM protocol that allows the distribution of electronic mail and attached documents through an SNA network.
SNAFU
Situation Normal All Fouled Up. World War II military slang, that often describes frustrating facets of the telecom industry. Actually, the GIs used a much less genteel word than "Fouled." Actually, most of us still do. See FUBAR and TARFU.
Snagless
RJ-11 and RJ-45 cables have this little plastic piece sticking out. It has a nasty habit of breaking off when it gets caught in something. Some manufacturers of cables make something they call "snagless." Their snagless cables have a boot over their connector lock to keep it from getting caught on things.
Snail Mail
A term used to reference delivery of messages by your local postal service. In short, mail that comes through a slot in your front door or a box mounted outside your house. See also Missile Mail.
Snake
A flexible strip of metal, typically 1/4 to 1/2" wide and 10 to 100' long, used to pull or push wire and cable through conduit, ceilings, walls or crawl spaces where it is difficult or impossible for a human to fit.
SNAP
Subnetwork Access Protocol. A version of the IEEE local area network logical link control frame similar to the more traditional data link level transmission frame that lets you use nonstandard higher-level protocols. The Subnet Access Protocol is an Internet protocol that operates between a network entity in the subnet and a network entity in the end system and specifies a standard method of encapsulating IP datagrams and ARP messages on IEEE networks. The SNAP entity in the end system makes use of the services of the subnet and performs three key functions: data transfer, connection management, and quality of services selection.
Snapshot
A view of something at an instant in time, rather than over time. A snapshot of a network, for instance, might be a view of the network configuration, in both physical and logical terms, as of midnight, January 1, 2000.
Snarf
-
To grab, esp. to grab a large document or file for the purpose of using it with or without the author's permission. This term was mainstream in the late 1960s, meaning 'to eat piggishly'. It may still have this connotation in context. "He's in the snarfing phase of hacking ” FTPing megs of stuff a day." It also means to acquire, with little concern for legal forms or politesse (but not quite by stealing). "They were giving away samples, so I snarfed a bunch of them."
-
System Normalized And Reset Flags.
SNC
Subnetwork Connection: In the context of ATM, an entity that passes ATM cells transparently , (i.e., without adding any overhead). A SNC may be either a stand-alone SNC, or a concatenation of SNCs and link connections.
SND
Cellular language for SEND. You punch the digits for the phone number you want to dial into your phone. Check them on the screen. If they're fine, hit the SND button. Bingo, your call goes through.
SNDCF
Subnetwork Dependent Convergence Function.
SNDCP
Subnetwork Dependent Convergence Protocol. A Network Layer protocol that supports subnetwork convergence.
Snd Format
Sound resource format. A digital audio sound resource utilized by many Macintosh applications and by the Mac OS. Double-clicking on a snd file enables playback of the sound. Also called a System 7 sound.
Sneak Current
A low-level current that is of insufficient strength to trigger electrical surge protectors and, therefore, is able to pass through them undetected. These currents may result from contact between communications lines and AC power circuits or from power induction, and may cause equipment damage unless secondary protection is used. See Sneak Currents.
Sneak Currents
Unwanted but steady currents which seep into a communication circuit. These low-level currents are insufficient to trigger electrical surge protectors and therefore are able to pass them undetected. They are usually too weak to cause immediate damage, but if unchecked could potentially create harmful heating effects. Sneak currents may result from contact between communications lines and AC power circuits or from power induction and may cause equipment damage due to overheating . See Sneak Current.
Sneak Fuse
A fuse operated by a low-level current and capable of preventing sneak currents on communication lines. See also Sneak Currents.
Sneaker
A person who is hired to hack into (i.e., break into) systems to test the effectiveness of their security. See also Cracker, Hacker, Phreak, Script Kiddies and Sneaker Brigade.
Sneaker Brigade
You sign a consulting contract for a big job ” say a complete re-do of your website and your entire computer operations. You sign the contract with the "big cheese," the president of the consulting company. He then disappears off the scene and sends in the sneaker brigade ” the young children consultants in the firm who will actually do the job. They're called the sneaker brigade because they wear sneakers.
Sneakers-up
A dotcom that's gone belly-up, derived from the fact that most of the employees came to work in sneakers.
Sneakernet
A "network" for moving files between computers. It is the oldest "network." It consists of copying a file to a floppy disk, walking to another machine, loading it on that machine. The term "sneakernet" refers to the fact that the main method of moving the disks is by feet, presumably clad in sneakers.
Sneakerware
A fully manual interface which relies on personnel to do the processing.
Snell's Law of Refraction
See Refraction.
SNET
Southern New England Telephone Corporation. Originally an independent telephone company serving a substantial portion of Connecticut, SNET stock was partially held by AT&T at the time of the Modified Final Judgement (MFJ). As SNET was not a wholly - owned subsidiary of AT&T at the time, it was not affected directly by the limitations imposed on the Bell Operating Companies (BOCs) and it was able to enter the long distance business. In January 1998, SBC Communications, Inc. (Southwestern Bell) announced an agreement to acquire SNET. According to company practice, SNET is pronounced S-N-E-T, with each letter being spelled out. See also MFJ and SBC.
SNI
-
Subscriber Network Interface. SMDS term describing generic access to a SMDS network over a dedicated circuit which can be DS-0, DS1 or DS3.
-
Systems Network Interconnection.
SNIA
Storage Networking Industry Association.
Snickelway
A narrow footpath in a medieval city where merchants sold their wares and villagers came to shop. The company which tried
Sniff and Hold
A term specific to the Bluetooth wireless specification. Sniff and Hold mode is the mode in which synchronized devices on a piconet (little-bitty network) can enter battery power-saving modes (i.e., "sleep" modes) during periods when device activity is lowered . See also Bluetooth and Piconet.
Sniffer
-
Sniffer is a registered trademark owned by Network General Corporation. The Sniffer Network Analyzer is a member of the family of Network General products, that monitors traffic on a network and reports on problems on the network. The company is sensitive about the word Sniffer being used as a generic term for network monitoring. If you do use it as a generic term, their VP and General Counsel, Scott C. Neely, will write you a letter telling you about trademarks, etc. See next definition.
-
Sadly Scott's worst nightmare came true. Sniffer is now a generic term used to describe a piece of software which runs on a 802.11(b) equipped PC. The software snifs out (as in smells out) the existence of an 802.11(b) WiFi hotspot ” a small geographic area which will receive and transit data according to the 802.11(b)
Sniglet
Any word that does not appear in the dictionary, but should. A term invented by Rich Hall of the HBO Television program "Not Necessarily The News". An example of a sniglet is the definition of "Hozone." It's obviously where socks go when they don't come back from the laundry.
Sniping Software
Software that allows a high bid to entered in an eBay auction a millisecond or so before the auction ends ” thus ensuring that you win the bidding for that glorious thing ” without payhing too much and being outbid by someone else.
Snips
Heavy duty scissors, used for cutting metal.
SNMP
-
Signaling Network Management Protocol.
-
Simple Network Management Protocol. SNMP is the most common method by which network management applications can query a management agent using a supported MIB (Management Information Base). SNMP operates at the OSI Application layer. The IP-based SNMP is the basis of most network management software, to the extent that today the phrase "managed device" implies SNMP compliance. RMON and RMON-2 use SNMP as their method of accessing device MIB information. In 1988, the Department of Defense and commercial TCP/IP implementors designed a network management architecture for the needs of the average Internet (a collection of disparate networks joined together with bridges or routers). Although SNMP was designed as the TCP's stack network management protocol, it can now manage virtually any network type and has been extended to include non-TCP devices such as 802.1 Ethernet bridges. SNMP is widely deployed in TCP/IP (Transmission Control Protocol/Internet Protocol) networks, but actual transport independence means it is not limited to TCP/IP. SNMP has been implemented over Ethernet as well as OSI transports. SNMP became a TCP/IP standard protocol in May 1990. SNMP operates on top of the Internet Protocol, and is similar in concept to IBM's NetView and ISO's CMIP. In 1991, Microsoft started referring to SNMP as SubNetwork Access Protocol. In November of 1993 Cisco Systems announced that its internetwork routers will support version 2 of the Simple Network Management Protocol (SMNP) and it has licensed SNMP v2 developed by SNMP Research, Inc. of Knoxville, TN. See CMIP, MIB, RMON, RMON-2 SNMP-2.
SNMP-2
A major revision of the original SNMP, SNMP-2 is currently a proposed standard covered by RFC 1902 through RFC 1908. The SNMP-2 MIB ”a superset of MIB-2 ” addresses many performance, security, and manager-to-manager communication concerns about SNMP. For example, SNMP-2 supports encryption of management passwords. See MIB, MIB-2, SNMP.
Snob
In England, neighborhood lists would show ” next to each name ” the craft and rank of the person. This is why, next to the names of simple burghers the words "sine nobilitate" (without nobility) would appear. Often these words were abbreviated to "s.nob." which is how our modern word "snob" made its appearance.
Snoop
See Berkeley Snoop Protocol, Snooping and Snoopware.
Snooping
Looking into a packet to obtain information. See also Snoopware.
Snoopware
Snoopware is software which records all the keystrokes made on your PC. Snoopware can be software which your company installs to do things like monitoring your employees' Web browsing and e-mail traffic. Snoopware can also be software which law enforcement agencies sneak into your computer to capture all your keystrokes and thus learn if you're the evil one, or not. Snoopware has wonderfully named software that includes names such Disk Tracey, Spector, LittleBrother, InternetWatchDog, NetSnitch and Snoopware. There are variations of snoopware. Spector, for example, takes snapshots of a PC's display screen at specified intervals during the day. Later, systems administrators or supervisors can replay the photo sequence and identify every web site visited, every application loaded and every e-mail chat.
Some nifty gumshoe programs like Webroot's WinGuardian also provide a search function through which suspicious bosses can fish for specific hot items ” such as job application, or Curriculum Vitae ” an employee might have typed into the computer during the day. Other software such as SurfCONTROL's LittleBrother and SuperScout software, even filter Internet traffic to block non-work-related instant messages and intercept attempts to access forbidden web sites. After nabbing someone goofing off on the Web at work, employers in some European countries could use this as reason to legally dismiss an employee since evidence obtained in this way is admissible in court. Sacked in 1998 for using her office computer to conduct some 150 Internet searches for her next vacation trip, an English Information Technology manager took her employer to court for unfair dismissal. The industrial tribunal that tried the case ruled in favor of the company and found the employee guilty of misconduct . In the U.S. mass dismissals of cyberslackers are already a reality: 40 Xerox employees lost their jobs last year after a snooping program called WebSense ” currently used by thousands of companies worldwide ” detected their office surfing activities. Some "consultants" have estimates billions of dollars lost by companies to web surfing by employees on company time.
Snortal
A contraction of "snort" and "portal," a snortal is a Web site from which you will be able to order refillable scent cartridges so you snort your Internet experience. In other words, you can make it smell. The concept is based on that of "Smell-O-Vision," an dubious enhancement of the moving picture experience. The snortal is the invention of Digiscents, which has introduced"iSmell," as in "internet Smell". Digiscents indexes various scents according their chemical compositions, and their place in the scent spectrum. The desired scent index is then described in a small file, which can be attached to any kind of Web content, interactive game, e-mail, movie, music, or other IP (Internet Protocol) file. The intended scent is recreated by your computer through personal scent synthesizers, which plug into your computer much like audio speakers. The personal scent synthesizers connect to your computer through your computer's serial port or USB (Universal Serial Bus) port, and are locally powered. They emit smells on command, which might take the form of a mouse click or a timed response triggered by a DVD or CD-ROM. The scents are recreated by an indexed combination of over 100 basic scents that are selected from a palette of scented oils, with the scent cartridges being refillable. Refills will be available from www.snortal.com, if this smelly idea ever takes off. See also Smell-O-Vision.
Snow
Random noise or interference appearing in a video picture as white specs . In short, video noise.
Snowshoe
A snowshoe shaped gadget that is used to maintain a minimum bend radius for installed fiber optic cable.
SNPA
Subnetwork Point of Attachment.
SNPP
Simple Network Paging Protocol. An IETF (Internet Engineering Task Force) protocol defined in RFCs 1645 (v2, which is one-way) and 1861 (v3, which is two-way, supporting " acknowledgement paging"), SNPP is used for sending messages (numeric and alphanumeric) between the Internet and wireless pagers through the use of a shim. The pagers must support the TAP/IXO (TAP is the Telocator Alphanumeric input Protocol, which was based on the IXO protocol, named for the company that allegedly invented it) protocol. Based on the philosophy of other Internet protocols, SNPP is based on a series of commands and replies between the client (i.e., pager) and the server. SNPP offers many advantages over SMTP (Simple Mail Transfer Protocol), including the ability to store and forward messages in the event that the client pager is temporarily out of touch. SNPP is widely used, and is based on TAP/IXO. Plans are to replace SNPP with TME (Telocator Message Entry protocol). See also IXO, Shim, and TAP.
SNR
-
Saved Number Redial. A phone system memory feature that allows the user to store a number for as long as it is useful, as opposed to other numbers that are stored more permanently. Some phones have two buttons ” one for redial and one for SNR. Redial will dial the last phone number you called. Saved Number Redial will dial one you dialed earlier and chose to save because you're going to call it back, e.g. an airline that's always busy.
-
See Signal-to-Noise Ratio.
Snuggling
Snuggling is a method used by operators of surveillance equipment. A surveillance equipment operator, when building radio transmitters, will select a transmitter frequency close to that of a nearby high powered transmitter, usually, a commercial radio station. Most ordinary radio gear will automatically tune into the stronger of the two signals. The operator must use a specially modified receiver capable of detecting and isolating the weaker signal. "Snuggling" will be difficult to detect by low quality RF receivers when making a countermeasure sweep.
SO
Serving Office. Central office where IXC (IntereXchange Carrier) has POP (Point Of Presence).
Soak
A means of uncovering problems in software and hardware by running them under operating conditions while they are closely supervised by their developers. See also Alarm Soaking.
Soak Period
Alarm soaking is the allowing of an error condition to persist before action is taken. Alarm holdoff is another term for it. The term "soak period" is used for the holdoff period before some action is taken.
SOAP
-
Simple Object Access Protocol. An XML-based (Extensible Markup Language) protocol that defines a framework for passing messages between systems over the Internet. SOAP typically is used for establishing RPCs (Remote Procedure Calls) between Web servers and clients, for the purposes of initiating and controlling processes on remote or distributed computer systems. SOAP simplifies the process of packaging the application data associated with the RPC, and sending it across the Internet. XML tags the content to ensure that both sender and recipient can easily interpret message contents, and SOAP provides specific instructions that allow a network node to remotely invoke application objects and return results. The data typically is encapsulated into HTTP (HyperText Transport Protocol), although SMTP and other transport protocols also can be used. Because SOAP is based on XML, it's compatible with all programming models and allows businesses to exchange data with each other over the Internet.
Developed by Microsoft as the successor protocol to its proprietary DCOM (Distributed Component Object Model), SOAP is an open protocol that has the potential to become a defacto standard if a sufficient number of programmers adopt it. Microsoft sees it as leveling the playing field between Windows and development strategies based on Java. Instead of being forced to choose one model, companies will be free to select whichever is best suited to solving the problem at hand, Microsoft argues. At issue is the slugfest between Microsoft and its competitors over the programming models software developers use. Microsoft has its own programming model based on the Windows operating system, called the Component Object Model (COM). Its competitors support Enterprise JavaBeans (EJBs) and Common Object Request Broker Architecture (CORBA), two programming models that are tightly integrated with each other. See also COM, CORBA, DCOM, EJB, HTTP, RPC, SMTP, and XML.
-
Soap was considered a frivolous luxury of the British aristocracy from the early 1700s until 1862, and there was a tax on those who used it in England. Some wags believe it's still a luxury in England, used rarely and sparingly.
Soap Opera
Endless daytime serials are called soap operas because their original sponsors were manufacturers of soap. In fact, in the beginning, the soap companies wrote the scripts, hired the actors and simply paid the TV station money for it broadcasting the show.
SOC
System-On-a-Chip. If you can put digital signal processing, microprocessing, network, memory-and maybe even some analog-functionality on one chip, you can dramatically lower power, cost, and real estate. And increase performance. Telecosm companies like Broadcom, Texas Instruments, Analog Devices and National Semiconductor are leaders at integrating components for the cable, DSL, LAN and mobile phone markets. Altera has just introduced field programmable gate arrays with up to 114,000 logic elements, 28 DSP blocks, and 10 megabits of RAM, all on a single chip.
SoC places the contents of many integrated circuits ” microprocessors, memory, logic and embedded software ” onto a single semiconductor chip. In more technical language, a SoC is a silicon integrated circuit which combines generic functions (e.g., microcontrollers, UARTs, memory, FIFOs, and other analog and digital logic functions) with custom design elements to create a device that contains all major elements of a system on one integrated chip. This is one method of increasing design productivity. The SoC designer collects and integrates pre-defined (and pre- tested ) components similar to the way hardware designers collect and interconnect integrated circuits on a circuit board design. The final implementation of an SOC may be in an ASIC or FPGA. See ASIC and FPGA. Thanks to Ken Coffman for help on this definition.
Social Computing
A term that emerged in the summer of 1993. Defined by Peter Lewis in the New York Times of September 19, 1993, social computing is a "communications-rich brew," which is "expected to create new ways for businesses and their customers to communicate, over new types of wireless as well as wired pathways , using new types of computers called personal communicators ." According to Peter Lewis, "The rise of social computing is expected to shift the emphasis of computing devices away from simple number crunching and data base management to wider-ranging forms of business communications...Where client server broke away from mainframe-based systems and distributed computing power to everyone in the organization, social computing goes the next step and extends the distribution of computing power to a company's customers."
Social Contract
An arrangement between the local telephone company and its local regulatory authority whereby the telephone company's services are detariffed, but cannot be priced at less than cost. Quality of service standards apply.
Social Engineering
Gaining privileged information about a computer system (such as a password) by skillful lying ” usually via a phone call. Often done by impersonating an authorized user.
Socket
-
A synonym for a PC port, a socket in is an opening or slot into which something plugs. The socket serves as the physical and electrical interface between the PC and its components (e.g., a processor or motherboard), or peripherals (e.g., a PCMCIA card, a.k.a. a PC card). See also Slot 1, Socket 7, and Socket 370.
-
A technology that serves as the endpoint when computers communicate with each other.
-
An operating system abstraction which provides the capability for application programs to automatically access communications protocols. Developed as part of the early work on TCP/IP.
Socket 370
The specification that addresses the form factor (i.e., physical shape and size) and the physical and electrical interface for some of Intel's motherboard processors. Socket 370 is a square socket with 370 pins, or leads. The Socket 370 is designed to accept motherboards designed in a FC-PGA (Flip Chip Pin Grid Array) configuration. See also FC-PGA.
Socket 7
The specification that addresses the form factor (i.e., physical shape and size) and the physical and electrical interface for some of Intel's Pentium processors, and compatibles manufactured by others. Socket 7 is the specification for one or more slots on the PC motherboard that accept a daughterboard in the form of a microprocessor cartridge with leads arranged in a 37x37 or 19x19 configuration. Intel is phasing out Socket 7 in favor of Slot 1, although its competitors have announced Slot 1 enhancements. See also Slot 1.
Socket Interface
The Sockets Interface, introduced in the early 1980s with the release of Berkeley UNIX, was the first consistent and well-defined application programming interface (API). It is used at the transport layer between Transmission Control Protocol (TCP) or User Datagram Protocol (UDP) and the applications on a system. Since 1980, sockets have been implemented on virtually every platform.
Socket Number
In TCP/IP, the socket number is the joining of the sender's (or receiver's) IP address and the port numbers for the service being used. These two together uniquely identifies the connection in the Internet.
Socket Services
The software layer directly above the hardware that provides a standardized interface to manipulate PCMCIA Cards, sockets and adapters. Socket Services is a BIOS level software interface that provides a method for accessing the PCMCIA slots of a computer, desktop or laptop (but most typically a laptop). Ideally , socket services software should be integrated into the notebook's BIOS, but few manufacturers have done so to date. For PCMCIA cards to operate correctly you also need Card Services, which is (not are) a software management interface that allows the allocation of system resources (such as memory and interrupts) automatically once the Socket Services detects that a PC Card has been inserted. You can, however, happily operate PCMCIA cards in your laptop without using socket and card services. You simply load the correct device drivers for those cards. Such drivers always come with PCMCIA cards when you buy the cards. You will, however, have to load new drivers every time you change cards and allocate the correct memory exclusions. You will have to reboot if you disconnect your network card. Theoretically, with socket and card services loaded, you do not have to reboot every time you change cards. My experience is that this works, except with network cards, which cannot be hotswapped. See PCMCIA.
Sockets
An application program interface (API) for communications between a user application program and TCP/IP. See Socket and Socket Number.
SOCKS
A circuit-level security technology developed by David Koblas in 1990 and since made publicly available by the IETF (Internet Engineering Task Force. SOCKSv5, the current version, provides security in a client/server environment, running at the Session Layer, Layer 5 of the OSI Reference Model. SOCKSv5 supports multiple means of authentication, negotiated between client and server over a virtual circuit, and on a session-by-session basis. SOCKSv5 also supports the transfer of UDP data as a stream, avoiding the need to treat each packet of UDP data as an independent message. SOCKSv5 also allows protocol filtering, which offers enhanced access control on a protocol-specific basis. For example, a network administrator can add a SMTP (Simple Mail Transfer Protocol) filter command to prevent hackers from extracting from a mail message information such as a mail alias. Reference implementations exist for most UNIX platforms, as well as Windows NT. The cross-platform nature of SOCKS offers portability to Macintosh and other operating systems and browsers. According to Network World Magazine, September 27, 1999, "the latest version of SOCKSv5 offers network managers an easier way to run videoconferencing and video and audio streaming through firewalls, which has been difficult and time-consuming . Socksv5 does this by providing a single and powerful method of authenticating users and managing security policies for all Internet applications, including multimedia." SOCKSv5 also interoperates on top of IPv4, IPsec, PPTP, L2TP and other lower-level protocols.
SOF
Start Of File
Soft Copy
-
A copy of a file or program which resides on magnetic medium, such as a floppy disk, or any form that is not a hard copy ” which is paper.
-
Old legacy systems term reapplied to distributed computing in which reports are created on-screen from data residing within different applications.
Soft Decision
See SISO.
Soft Ferrite
Ferrite that is magnetized only while exposed to a magnetic field. Used to make cores for inductors, transformers , and other electronic components. See Barium Ferrite, Ferrite and Hard Ferrite.
Soft Font
A font,usually provided by a font vendor, that must be installed on your computer and sent to the printer before text formatted in that font can be printed. Also known as downloadable font.
Soft Handoff
-
A cellular radio term. A soft handoff is a handoff between cell sites that involves first making the connection with the new cell site before breaking the connection with the previous cell site. A hard handoff, or "break and make" handoff, is not noticeable in a voice conversation, but has disastrous impact on a data communication. Here's a longer explanation: What happens during a Hand-Off Sequence? Hand-off occurs when a call has to be handed from one cell to another as the user moves between cells. In traditional hard hand-off, the connection to the current cell is broken and then the connection to the new cell is made. In CDMA technology, however, it is possible to make the connection to the new cell before leaving the current cell since all cells in CDMA use the same frequency. This is known as a "make-before-break," or "soft hand-off." Soft hand- off requires less power, which reduces interference and increases capacity.
-
A satellite term. The process of transferring a circuit from one beam or satellite to another without interruption of the call.
Soft Input-Soft Output
See SISO.
Soft Key
There are three types of keys on a telephone: hard, programmable and soft. HARD keys are those which do one thing and one thing only, e.g. the touchtone buttons 1, 2, 3, * and # etc. PROGRAMMABLE keys are those which you can program to do produce a bunch of tones. Those tones might be "dial mother." They might be "transfer this call to my home for the evening." They might be "go into data mode, dial my distant computer, log in and put in my password." SOFT keys are the most interesting. They are unmarked buttons which sit below or above on the side of a screen. They derive their meaning from what's presently on the screen. And what's on the screen will change based on where the call is at that moment ” in a conference call, about to set up a conference call, about to go into voice mail, into voice mail, programming a speed dial number, etc.
Soft Modem
Soft modem is short for software modem. The modem consists of a small phoneline interface card and software that uses the PC's main CPU (e.g. a Pentium) for the main communications tasks. Such modem are cheaper than ones based on hardware, ones we're all used to. But they can be slower than one based mostly on hardware ” depending on what else the main processor is doing. Many laptops presently have software modems.
Soft Phones
A PC or PC-type device that emulates a telephone and sits behind a PBX and acts as telephone, with the prompts and commands appearing on the PC's screen, not the phone, and the PC's keyboard acting as the telephone's keys. The voice conversation could be transmitted via the PC's sound system or it could be transmitted via an attached, cheap single line analog phone.
Soft Sectored
A floppy disk whose sector boundaries are marked with records instead of holes. Soft-sectored disks have typically one hole. Hard sectored disks have many holes. A soft-sectored disk won't work on disk drives which use hard-sectored drives and vice versa ” even though the disks might be the same size. Soft-sectored disks are now much more common.
Soft Selectable/Soft Strappable
Refers to an option that is controllable through software rather than hardware.
Softkey
See Soft Key.
Softkey Mapping
See ADSI.
Softswitch
Someone described a "softswitch" as basically anything you want it to be. The Softswitch Consortium
A type of switch developed in the late 1990s as a replacement for the CO (Central Office) circuit switches used in the traditional PSTN (Public Switched Telephone Network). Traditional COs can be characterized as "hard" switches, as their logic is hard-coded to support voice-grade telephone service on a circuit-switched basis, only. Further, COs are proprietary and closed in nature, as opposed to supporting open standards and open APIs (Applications Programming Interfaces). As packet-based IP and ATM networks began to develop in the 1990s, it became clear that COs were obsolete in such networks, especially in support of data and multimedia traffic, and the wide variety of data and multimedia services that needed to be developed and delivered in very short periods of time. Softswitches offload call processing functions to industry-standard server hardware, and support open APIs which allow carriers and service providers to considerably shorten the "time to market" for new services. Further, softswitches allow service providers to choose best-of-breed , industry- standard products across the software and hardware domains, integrating them into a multi- vendor service solution. Softswitches also tend to be much less expensive and to have a much smaller footprint (i.e., occupy much less physical space) than do traditional COs. Softswitches typically support multiple protocols, including IP and ATM, and multiple QoS (Quality of Service) and GoS (Grade of Service) levels, and can serve as gateways between the circuit-switched PSTN and the packet-switched network of the service provider, resolving any protocol issues internally. The various elements in a softswitch architecture network include: Call agent (a.k.a. media gateway controller, softswitch); Media gateway; Signaling gateway: Feature server; Application server; Media server; and Management, provisioning and billing interfaces. See also Softswitch Consortium.
Softswitch Consortium
An international organization for global cooperation and coordination of internetworking technologies in the field of Internet-based, real-time, interactive communications and applications. This consortium was formed in May 1999 to promote the formation of interoperability standards in support of IP-based voice and multimedia communications. www.softswitch.org. See also Softswitch.
Software
The detailed instructions to operate a computer, differentiating instructions (i.e., the program) from the hardware. The term was coined by John W. Tukey, who first used it in a 1958 article for American Mathematical Monthly. See Firmware, Hardware, Program, and Tukey.
Software Data Compression
As an ISDN term, it means the ability to compress data before it arrives at the serial port of the ISDN terminal adapter. Can improve performance by as much as 400%
Software Defined Network
SDN. Generically, a software defined network refers to a virtual private network. Specifically, it refers to AT&T's Software Defined Network Service, which was introduced in 1985 for AT&T's largest customers and provided only dedicated access services. In 1989, AT&T extended its SDN Network to switched access. Currently, SDN is the most commonly resold of all long distance services. The AT&T Software Defined Network Service Description of July 1986 describes SDN as a service developed for multi-location businesses which allows network managers to tailor their network to their own specific communications needs. Call processing information is stored in a database that is accessed during a call. Calls are transferred over AT&T facilities to either a location that is a dedicated part of the network (for "on-net calling") or to non-dedicated facilities that are part of the network ("off-net" calling). Any company location can become part of a network through SDN dedicated access lines to an AT&T SDN serving office. Here is further explanation of SDN by Siemens Information Systems, whose Saturn PBX has the capability to interface to and mesh neatly with an AT&T SDN network. Here is Siemens' explanation (it's good): When a company establishes an SDN, each phone on the network has a unique seven digit number. This number may or may not be the same as the Listed Directory Number (LDN). When a call is placed at one PBX, it is sent over a dedicated access line to the long distance network. The call is received by the SDN Serving Office and digits are sent via a CCIS (Common Channel Interoffice Signaling) link to the Network Control Point (NCP) for analysis and routing. There is one NCP per SDN network. The NCP contains the unique database for the company using the SDN. The NCP analyzes the digits received against the database, determines whether it is an on-net or off-net call, and sets up the path over which the call will be rerouted on the long distance network. If it is an on-net call, the NCP translates the unique seven digit locator code to one that will be recognized by the AT&T network, sends the call over the network to another SDN Serving Office, and completes the call over dedicated lines to the PBX being called. There is a discount for any call which remains on-net throughout. If the call is off-net, the digits dialed are sent over the long distance network to a Central Office that is not part of the SDN. The call is then completed to the corporate PBX over DID (Direct Inward Dial) lines. Since the introduction of route selection features in PBXs, the caller now has the ability to dial the 10-digit LDN (Long Distance Number) and have the PBX make the decisions on the route and make the decisions on any digit translation or deletion that is necessary to route the call. The CCIS network which carries SDN call signaling is a packet switching network operating at 4,800 bits per second. It will eventually be replaced by ITU 7 Signaling, a more powerful internationally-accepted signaling system. See Signaling System 7.
Software Defined Radio
SDR. As defined by the FCC (Federal Communications Commission), SDR is a generation of radio equipment that can be reprogrammed quickly to transmit and receive on any frequency within a wide range of frequencies, and using virtually any transmission format and any set of standards. The FCC began hearings on SDR in March 2000, with the thought that SDR could promote more efficient use of spectrum, expand access to broadband wireless communications, and increase competition among service providers. SDR is promoted by the Software Defined Forum. www.mmitsforum.org.
Software Engineering
A broadly defined discipline that integrates the many aspects of programming, from writing code to meeting budgets , to produce affordable software that works.
Software Interfaces
Language between programs which allows one program to call upon another for assistance in processing.
Software Metering
Software that monitors the use of applications ” such word processing, spreadsheets, databases, etc. All metering programs tend to take advantage of a software feature called "concurrency." Concurrency means that a company need only buy as many licenses to a program as it has people using the program at one time ” concurrent users, in other words.
Software Modem
Also called soft modem. Basically it's a modem which consists of a small phoneline interface card and software that uses the PC's main CPU (e.g. a Pentium) for its main communications tasks. Such modem is typically cheaper than one based on dedicated hardware (chips), i.e. ones we're all used to.
Software Only Video Playback
A multimedia term. Video software playback displays a stream of video without any specialized chips or boards. The playback is done through a software application. The video is usually compressed to minimize the storage space required.
Software MPEG Playback
See MPEG.
Software Radio
See Smart Radio.
Software Supervision
"Answer Supervision" is knowing when the person at the other end answers the phone. The main reason for wanting to know this is so that a phone company can start billing the call. There are two ways of doing answer supervision. You can get it from the nation's phone system, i.e. the distant office signals back across the country when the called person picks up the phone. Or you can fake it with "software supervision." Essentially this means there's electronics which "listens" to the call. If it "hears" voice or something like voice, it assumes the conversation has started and it's time to start billing the call. Software supervision is not accurate. But when you haven't got access to real answer supervision (for whatever reason) it's better than the previous alternative, which was "timeout." In timeout answer supervision, the carrier simply assumed the call had begun after a certain number of seconds ” like 30 ” had elapsed with the calling person hanging up. This meant , for example, if you called Grandma and she wasn't there, but you left it ringing, 'cause you knew she took time to answer the phone, then you'd be charged for the call ” even though she didn't answer phone!
SOH
Start Of Header. A transmission control character used as the first character of the heading of an information message.
2. Section Overhead. SONET frames include 9 octets of SOH for maintenance of SONET links. SOH information includes transport status, messages and alarm indication. Without SOH data, you are SOL.
SOI
See Service Order Image.
SOHO
-
Small Office Home Office. An acronym for a new market which is part work at home, part commute from home. It's getting larger as companies downsize and their workers become "consultants" or small businesspeople. It's getting larger as companies close their distant sales offices ask their salespeople to work out of home.
-
In New York City, there's an area called SOHO. It stands for South Of HOuston Street. See Silicon Alley.
SOL
Shit Out Of Luck.
Solder
-
An alloy of lead and tin having a low melting point.
-
To unite or join by solder.
Solenoid
A coil consisting of a number of turns in cylindrical form.
Solid State
Any semiconductor device that controls electrons, electric fields and magnetic fields in a solid material ” and typically has no moving parts .
Solid State Applications Interface Bridge
Solid's State Systems' PBX to external computer link. See Open Application Interface.
Solid State Transfer
An uninterruptible power supply (UPS) definition. Many UPSes use "mechanical relays" to switch from AC power to battery power. This technology requires 12 milliseconds switching time ” slow enough to cause data loss. Solid state switching is faster and eliminates this type of problem.
Solitons
Solitons are light pulses that maintain their shape over long distances. The origin of the term "soliton" dates to the 19th century, when Scottish engineer John Scott Russell discovered solitary waves while he was conducting experiments to develop a more efficient design for canal boats. In early 1993, scientists at AT&T Bell Labs announced that they had transmitted error-free solitons at 10 gigabits per second over one channel and at 20 gigabits per second more than 13,000 kilometers using two channels. To accomplish this feat, they used sliding-frequency guiding filters. See also Rare Earth Doping.
On April 27, 1998, MCI (before it became Worldcom) said that it was using soliton technology to carry voice and data traffic triple the distance without costly gegeneration equipment. MCI announced a trial using solitons, a technology based on a scientific theory formulated back in 1834 and adapted for modern use by Pirelli Cables and Systems. MCI officials say the technology has the potential to reduce transmission costs by as much as 20 percent. MCI demonstrated the ability to send a single stream of data traffic at 10 gigabits per second more than 900 kilometers over existing installed fiber without regenerators ” triple the distance that 10 Gbps traffic can be transported today. MCI also successfully transmitted soliton data streams using dense wavelength-division multiplexing technology, carrying four data streams at 10 Gbps each, traveling more than 450 kilometers without regenerators.
Here is MCI's explanation of how the Soliton technology works: A Soliton is a type of wave or, in the case of optical fiber, a narrow pulse of light that retains its shape as it travels long distances along the fiber. The soliton's ability to keep its shape helps to overcome the problem of lightwave dispersion, and the consequent loss of data integrity, as the data- carrying lightwave travels over long distances. Modern soliton technology is based on a phenomenon first documented in 1834 by a Scottish engineer named John Scott Russell who, while watching a boat being drawn along a canal by a pair of horses, noticed that when the boat stopped suddenly, the wave of water created by the bow continued forward at great velocity without losing speed or shape. Russell was convinced that the soliton was an important scientific discovery. But his theory wasn't fully borne out until the 1960s when scientists began to learn that many phenomena in such fields as physics, electronics and biology can be explained by solitons. The key elements of Pirelli's 10 Gbps wavelength division multiplexed systems are the soliton converters, which transmit and receive traffic. The Soliton transmitter generates a pulse with the proper shape and power to allow for the transmission of data and voice traffic over very long distances without electronic regenerators.
Solution
IBM-speak to solve, as in "We've got to solution this problem if we're going to make the sale."
Solution Assembler
Another name for a system integrator. A vendor who puts together a collection of products which purport to be the solution/s to your IS problem.
SOMO
Acronym for Small Office Medium Office.
SON
Service Order Number. The SON is the number issued by the local exchange carrier to confirm the order for the ISDN service. It provides a matching number for cross referencing the order to the phone company.
SONAR
-
SOund Navigation And Ranging. A system for underwater detection and location of objects through the use of acoustics. An active SONAR acoustical transmitter emits an acoustical "ping" signal at a frequency of 3500 Hz (Hertz). If the signal strikes a solid object, some of the acoustical energy is reflected in the form of an echo. Since the acoustical signal travels at approximately 1500 meters per second, the transmitter/receiver can calculate the distance of the solid object that caused the return. Further, the strength of the return ping can be calculated to provide information relative to the size and physical composition of the target object. As this acoustical echolocation technique is overt, the target object may be able to sense that it is being "pinged." Passive SONAR devices simply listen for acoustical signals, thereby remaining covert, which can be a decided advantage for an attack submarine , destroyer or other warship. Fish finders are active SONAR devices, but the fish don't seem to react to the fact that they have been "pinged." See also Ping.
-
A service that, when presented with a list of IP (Internet Protocol) addresses, attempts to order that list according to the proximity from the SONAR server. SONAR can be of value in assisting networked applications to make reasonable choices between alternative hosts in consideration of their proximity, as a "nearby" application server offers better service than a "distant" one. SONAR does not attempt to gauge the relative service levels offered by networked applications at different addresses in terms of round-trip time, hop count or available bandwidth. Rather, SONAR attempts to offer a "good" choice without consuming significant network or host resources in making that choice. Essentially, SONAR ranks host availability according to various speed-of-response service metrics, which can be affected by route distance, hop count, bandwidth availability, and application availability. While SONAR is not widely implemented at this time, it offers the advantage of avoiding the embedding of complex proximity algorithm logic in network clients. "SONAR" is intended as a pun on the "ping" utility that uses ICMP (Internet Control Message Protocol) packets to determine if an IP address has a working (i.e., installed and online) IP protocol stack. See also ICMP and Ping.
SONET
Synchronous Optical NETwork. A family of fiber optic transmission rates from 51.84 million bits per second to 39.812 gigabits (billion, or thousand million) per second (and going higher, as we speak), created to provide the flexibility needed to transport many digital signals with different capacities , and to provide a design standard for manufacturers. SONET is an optical interface standard that allows interworking of transmission products from multiple vendors (i.e., mid-span meets). It defines a physical interface, optical line rates known as Optical Carrier (OC) signals, frame format and an OAM&P protocol (Operations, Administration, Maintenance, and Provisioning). The OC signals have their origins in electrical equivalents known as Synchronous Transport Signals (STSs). The base rate is 51.84 Mbps (OC-1/STS-1), which is a DS-3 (specifically, a T-3) payload of 44.736 Mbps, plus a considerable amount of overhead for network management (largely signaling and control) purposes. Higher rates are direct multiples of the base rate. Note that SONET is based in large part on T-carrier. SONET is a TDM (Time Division Multiplexed) technology, therefore, just as is T-carrier.
SONET development began at the suggestion of MCI to the Exchange Carriers Standards Association (ECSA). Bellcore then took over the project, and it ultimately came to rest at the American National Standards Institute (ANSI). Much of the development was carried out by ECSA under the auspices of ANSI. Work started on the SONET standard in the ANSI accredited T1/X1 committee in 1985, and the Phase 1 SONET standard was issued in March 1988. SONET has also been adopted by the ITU-T (International Telecommunications Union- Telecommunications Standardization Sector), previously known as the CCITT. The ITU-T version is known as SDH (Synchronous Digital Hierarchy), which varies slightly and most obviously in terms of the fact that the SDH levels begin at the OC-3 rate of 155 Mbps. In SDH, the fundamental building blocks are known as STMs (Synchronous Transport Modules) and are equivalent in rate to three SONET STS-1s. SONET is intended to attain the following goals: Multi-vendor interworking, to be cost effective for existing services on an end-to-end basis, to create an infrastructure to support new broadband services and for enhanced operations, administration, maintenance and provisioning (OAM&P). SONET offers many advantages over asynchronous transport including: Opportunity for back-to-back multiplexing, digital cross-connect panels; Easy evolution to broadband transport; Compatibility with evolving operations standards; Enhanced performance monitoring and extension of OAM&P capabilities to end users. SONET/SDH offers the critical advantage of a standard to which manufacturers can build fiber optic gear in order to ensure interconnectivity and (at least some level of) interoperability. Thereby, carriers can safely acquire and deploy multi-vendor networks without being wed to a single manufacturer. This last point was, in fact, the primary impetus for SONET development. SONET transmission equipment interleaves frames of data in simple integer multiples to form a synchronous high speed signal known as a Synchronous Transport Signal (STS). This permits easy access to low speed signals (e.g., DS-O, DS-1, etc.) without multi-stage multiplexing and demultiplexing . The low speed signals are mapped into sub-STS-1 signals called Virtual Tributaries (VTs), or Virtual Containers (VCs) in SDH. SONET uses a 51.84 Mb/s STS-1 signal as the basic building block. Higher rate signals are multiples of STS-1 (e.g. the STS-12/OC-12 signal has a rate of 12 x 51.84 Mb/s or 622.080 Mb/s). The frame format consists of 90 x 9 bytes. The SONET frame format is divided into two main areas: Synchronous Payload Envelope (SPE) and Transport Overhead (TOH). The SPE contains the information being transported by the frame. The TOH supports the OAM&P functions of SONET, and includes a data communication channel that provides an OAM&P communication path between multiple interconnected SONET network elements. The Synchronous Payload Envelope can handle payloads in any of three ways:
-
As a continuous 50.11 Mb/s envelope for carrying asynchronous DS-3, and other payloads requiring up to 50.11 Mb/s capacity in asynchronous (byte invisible) or byte visible format;
-
In a VT (Virtual Tributary) structured envelope to accommodate DS-1, DS-1C, DS-2, European CEPT1, or future VT-based services (see chart below). These signals can have either an asynchronous or byte visible format; and
-
As concatenated payloads to accommodate services requiring more than 50.11 Mb/s capacity. For example, three STS-1 SPEs may be concatenated to transport a broadband ISDN signal of 135 Mb/s. According to AT&T, the main SONET characteristics are: A family of rates at N x 51.84 Mbps; Optical interconnect allowing mid-span meet; intraoffice mixed vendor interconnects; Overhead channels for OAM&P functions and Synchronous networking. SONET rates are
| OC Level | Line Rates | Capacity |
|---|---|---|
| OC-1 | 51.84 Mbps | 28 DS1s or 1 DS3 |
| OC-3 | 155.52 Mbps | 84 DS1s or 3 DS3s |
| OC-9 | 466.56 Mbps | 252 DS1s or 9 DS3s |
| OC-12 | 622.08 Mbps | 336 DS1s or 12 DS3s |
| OC-18 | 933.12 Mbps | 504 DS1s or 18 DS3s |
| OC-24 | 1.244 Gbps | 672 DS1s or 24 DS3s |
| OC-36 | 1.866 Gbps | 1,008 DS1s or 36 DS3s |
| OC-48 | 2.488 Gbps | 1,344 DS1s or 48 DS3s |
| OC-96 | 4.976 Gbps | 2,688 DS1s or 96 DS3s |
| OC-192 | 9.953 Gbps | 5,376 DS1s or 192 DS3s |
| OC-768 | 39.812 Gbps | 21,504 DS1s or 768 DS3s |
In North America, SONET rates have been limited to OC-1 plus those compatible with European SDH. Thus only OC-3, OC-12, OC-48, OC-192, and OC-768 which are equivalent to SDH-1, SDH-4, SDH-16, and SDH-64, and SDH-256, respectively; are standard.
SONET/SDH networks typically are deployed in a physical ring topology, with multiple fibers providing redundancy. In the event that a given fiber suffers a catastrophic failure, one or more other fibers are available. The rings are of two types: Line-Switched and Path- Switched. SONET also may be deployed in a physical linear topology, in which case the system operates as a logical ring.
SONET/SDH has been incredibly successful in the carrier domain, although it lately has been challenged by DWDM (Dense Wavelength Division Multiplexing). The considerable advantages of SONET have been detailed above, and at some length. The criticisms of SONET include its TDM nature, which is considered inappropriate for IP traffic; its bandwidth limitations, even at 40 Gbps; and its high level of overhead, which directly reduces user data payload, although it yields considerable network management capabilities advantages. Perhaps the greatest criticism is SONET's high cost, especially considering that an increase in bandwidth (e.g., OC-48 to OC-192) requires that the transmitting laser diode, the receiving light detector, and all intermediate optical repeaters be upgraded. DWDM is an optical transmission technique that allows multiple light signals operating at different wavelengths (i.e., frequencies of light) to share a single fiber. Thereby and for example, eight or more (eight is the point at which DWM becomes DWDM) wavelengths can each operate at 10 Gbps. As a result, DWDM offers higher aggregate speeds than SONET. DWDM also is far less expensive. On the downside, DWDM does not offer the same inherent network management capabilities and does not offer the same level of standards development, which translates into lack of interconnectivity and interoperability between network elements of disparate origin. Further, each wavelength in a DWDM system is, in essence, a separate circuit. Therefore, all traffic riding over that wavelength is transported and switched as a single entity, from point of origin to point of termination. As a result, a wavelength must carry traffic of the same type (e.g., circuit-switched voice, packet voice, IP packet data, ATM, or Frame Relay), with the same QoS (Quality of Service) requirements, originating at the same place, and destined for the same place. All of that means that each wavelength must be filled to capacity, or that there must be enough available wavelengths that capacity can afford to be underutilized . The arguments over SONET vs. DWDM rage, and will continue to do so for many years. Either approach is correct, and even optimal, depending on the applications focus of a given carrier. In fact, SONET and DWDM can, and often will, coexist, with SONET-framed data riding over DWDM wavelengths. That's my view, at least. See also ADM, DWDM, Line-Switched Ring, Path Switched Ring, SONET Interface Layers , SONET Ring, STM, Stratum Level, STS, and WDM.
SONET Head
A device on the end of a boring machine. Such machine is used to bore holes under highways, rivers and sundry obstructions. The SONET head contains sensors which can help determine what it is about to strike as it moves ahead underground . The SONET head will signal the person operating the boring machine what lies ahead and hopefully, the operator, is sufficiently intelligent to move the boring machine up or down or sideways in order to miss the potential obstruction ” which might be anything from a rock to another fibre cable to a high voltage AC power line.
SONET Interface Layers
The SONET standards define four interface layers. Each layer requires the services of all lower-level layers to perform its functions. While conceptually similar to layering within the Open System Interconnection (OSI) reference model, SONET itself corresponds only to the OSI Physical Layer. The SONET interface layers are:
-
Physical Layer: Handles bit transport across the physical medium; primarily responsible for converting STS (electrical) signals to and from OC (optical) signals. Once the signal has been expressed optically, this layer is sometimes referred to as the photonic layer. Electro-optical devices communicate at this layer;
-
Section Layer: Transports STS-N frames and Section Overhead (SOH) across the medium; functions include framing, scrambling , and error monitoring. Section Terminating Equipment (STE) communicate at this layer;
-
Line Layer: Responsible for the reliable transport of the Synchronous Payload Envelope (SPE) (i.e., user data) and Line Overhead (LOH) across the medium; responsibilities include synchronization and multiplexing for the Path Layer and mapping the SPE and LOH into an STS-N frame. An OC-N-to-OC-M multiplexer is an example of Line Terminating Equipment (LTE); and
-
Path Layer: Handles transport of services (e.g., DS-1, DS-3, E-1, or video) between Path Terminal Equipment (PTE); the main function is to map the services and Path Overhead (POH) information into the PTE includes SONET-capable switches with an interface to a non-SONET network, such as a T1-to-SONET multiplexer.
SONET Ring
SONET transmission systems ideally are laid out in a physical ring for purposes of redundancy. In practice, the topology often is that of a linear ring, which is linear in its physical appearance, but which operates as a logical ring. See also SONET, Physical Topology, Logical Topology, Line-Switched Ring, and Path-Switched Ring.
SONIA
A group of technology vendors which advanced a profile for NCs (Network Computers), also known as "thin clients." SONIA is derived from the names of the members of the group: Sun Microsystems, Oracle Corp., Netscape Communications Corp., IBM, and Apple Computer Inc. See also NC and Thin Client.
Sony
Akio Morita, who died in October 1999, named Sony after a combination of the Latin word for "sound" and the English words "sonny boy."
Sony Mini Disc
A 2 1/2 inch silvery CD (compact Disc) that can record and play 74 minutes of sounds, almost as much as its five-inch forebear. To record on this disc, a laser momentarily heats a tiny spot on the disk to 400 degrees Fahrenheit, while a magnetic head writes the signal into the heated part of the magnetic layer. To play the disk an optical pickup analyzes the polarity of the light reflected from each spot.
SOP
Standard Operating Procedure.
Sort
To order a collection of records ” for example, a telephone directory ” in some specified way, say, in alphabetical order. Computers can sort in virtually any way you ask them to. Most companies don't produce sufficient "sorts" on their telephone directories.
Sort Scheme
A call center term. A list of fields that tells the program how to sort a report or a list of records. This can be simple scheme that sorts by only one field or a complex scheme consisting of sorts within sorts.
SOS
SOS is the international distress signal. SOS was officially adopted in 1908, and was transmitted on the 500kHz emergency radio wavelength. Contrary to popular belief, "SOS" does not stand for "Save Our Souls," "Save Our Ship," or anything else. Rather, it was adopted simply because of its easy radiation and unmistakable character (... ”- ...) in Morse code telegraphy. In an emergency when sending SOS, it was defined to alternate between the S letter and the O letter continuously. It was sent like this: dididit dahdahdah dididit dahdahdah dididit dahdahdah dididit dahdahdah dididit etc..., continuously with pauses for words. Prior to the adoption of SOS, the generally accepted distress call was "CQD," which was suggested by the Marconi company. "CQ" was the signal used in England for an "all stations" general call on a landline telegraph network. "D" indicated a "distress" call. Therefore, "CQD" means "all stations ”distress." Confusion reigned for some time, while the transition was made from SOS to CQD. Also, the English telegraphers favored CQD. In fact, the original distress call from the Titanic (April 15, 1912) was "CQD," sent by First Radio Officer Jack Phillips six times in rapid succession, followed by "MGY," the call letters of the Titanic. Later, and at the suggestion of Harold Bride, Second Radio Officer, Phillips interspersed his "CQD" transmissions with "SOS." That didn't help much. A few extra lifeboats would have helped a great deal more. (Bride survived, while Phillips died of hypothermia.) SOS was officially retired on February 1, 1999 by the International Maritime Organization (IMO). It was replaced by the Global Maritime Distress and Safety System (GMDSS), which uses much improved digital radio technology. See also Morse Code.
Soul
According to an article published in The Lancet, a respected British medical journal, a Dutch medical research team claims to have proof that humans have a soul that exists independently from the body. The team did a two-year study of near-death experiences, investigating the experiences people clinically dead at the moment claim having had. The doctors reported there were no psychological, neurophysiological, or physiological factors that could account for these experiences. Conclusion? The mind ” or soul ” survives death.
Sound
Sound is the sensation perceived by the sense of hearing. Acoustics is the science of sound. Sound is transmitted by the vibration of molecules in the air. The parameters of sound are amplitude and frequency. Amplitude, or volume, is the intensity of the acoustical signal. The louder the sound, the more intensely the molecules in the air vibrate. Frequency, or pitch or tone, is the frequency with which the molecules in the air vibrate. Recording means getting something else (e.g., a diaphragm in a microphone) to vibrate in sympathy, and turning those vibrations into electrical signals (which can then be stored as grooves on a disk, say). A loudspeaker does the reverse: electrical signals are turned into wobbles of a usually cone-shaped piece of material that batters the molecules of the air to recreate the sound. Audible sound spans a huge range of frequencies from around 20 Hertz (vibrations per second) to 20 kHz. Most loudspeakers need two to three cones of different sizes to cover this range. Moreover, like bells and wine glasses , cones have their own natural frequencies at which they vibrate when hit. They overrespond to electrical signals close to those frequencies. As a result, sound always loses something when being electronically regurgitated, although careful loudspeaker and amplifier design can make up for a lot. See also Speakerphone.
Sound Files
Files on PCs have their own extensions ” the three letters which follow the name of the file. For example, a sound file of jungle noises might be called jungle .wav. Here are the typical extensions on sound files of various computers:
Microsoft Windows ” .wav
Apple ” .aif
NeXT ” .snd
MIDI ” .mid and .nni
Sound Blaster ” .voc
Intel Indeo Video Movie clips ” .avi
Sound Powered Telephone
A telephone in which the operating power is derived from the speech input only. See Sound.
Sound Waves
The waves given off by a vibrating body, which are transmitted by an elastic material medium (such as the air) and which can be detected by the ear. See Sound and Sound Files.
Source
That part of a communications system which transmits information.
Source Address
The part of a message which indicates who sent the message. Just like the top left-hand address on the envelope.
Source Code
A set of instructions, written in a programming language, that must be translated to machine instructions before the program can be run on a computer. The program which finally runs on that computer is known as the object code.
Source Explicit Forwarding
A feature that allows MAC-layer bridges on local area networks to forward packets from only source address specified by the network administrator.
Source-Quench Messages
Source-quench messages are Used by receiving devices to help prevent their buffers from overflowing, these messages tell the transmitting device that the receiving device is dropping segments.
Source Route
A hierarchically complete source route. See Source Routing.
Source Route Bridging
Method of bridging originated by IBM and popular in Token Ring networks. In an SRB network, the entire route to a destination is predetermined, in real time, prior to the sending of data to the destination. See Source Routing.
Source Routing
A method used by a bridge for moving data between two networks. Originally developed by IBM's token ring network, it relies on information contained within the token to route the packet between the two networks. Since the information in the token is supplied by the computer that sent the data packet, that computer must know on which network the destination computer is located. IBM developed a special protocol that lets computers discover that information. For source routing to work, every computer and every bridge on all networks must support this protocol. If some computers do not use this protocol, they will not receive packets from bridges that use source routing. See Bridge. Compare to Transparent Routing.
In IBM's method of routing local area network data across bridges, IBM's bridges can be configured as either single-route broadcast or all-routes broadcast. The default is single- route broadcast. Single-route broadcasting means that only one designated single-route bridge will pass the packet and only one copy of the packet will arrive at its destination. Single-route broadcast bridges can transmit both single-route and all-routes packets. All- routes broadcasting sends the packet across every possible route in the network, resulting in as many copies of the frame at the destination as there are all-routes broadcasting bridges in the network. All-routes broadcast bridges only pass all-routes broadcast packets.
Source-Quench Messages
Used by receiving devices to help prevent their buffers from overflowing, these messages tell the transmitting device that the receiving device is dropping segments. This definition is from the Cisco Certified Network Associate book.
Source Routing Protocol.
SRP. See Bridge.
Source Routing Transparent
SRT. See Bridge.
Source Traffic Descriptor
An ATM term. A set of traffic parameters belonging to the ATM Traffic Descriptor used during the connection set-up to capture the intrinsic traffic characteristics of the connection requested by the source.
Source/Destination Routing
A term used in call centers for routing calls based on where they originate or terminate. See also Skills-Based Routing, Calendar Routing and End-of-Shift Routing.
Source/Sink Device
A source/sink device is byte-synchronous with a byte orientation. Source devices originate; sink devices terminate.
South Sea Bubble
In the 18th century, the promise of foreign trade excited Britain. A company called the South Sea Co. was given a monopoly on trade with the Spanish Empire. Shares of the South Sea Co. soared on London's stock market. According to the Wall Street Journal, trade eventually made fortunes for some people, but not for the South Sea Co. which became a disaster dubbed the South Sea Bubble and helped throw the British economy into a slump.
Southern New England Telephone Corporation
SNET. Pronounced S-N-E-T, not SNET. Originally an independent telephone company serving a substantial portion of Connecticut, SNET stock was partially held by AT&T at the time of the Modified Final Judgement (MFJ). As SNET was not a wholly-owned subsidiary of AT&T at the time, it was not affected directly by the limitations imposed on the Bell Operating Companies (BOCs) and it was able to enter the long distance business. In January 1998, SBC Corporation (Southwestern Bell) announced an agreement to acquire SNET. See also MFJ and SBC.
Southwestern Bell Corporation
One of the seven Regional Holding Companies formed at Divestiture. It includes Southwestern Bell Telephone Co., Southwestern Bell Mobile Systems, Southwestern Bell Yellow Pages, Southwestern Bell Telecom and SBC International. In early October, 1994, Southwestern Bell Corporation changed its name to SBC Communications Inc., apparently feeling as though the "Bell" name no longer was of value. (The old Bell Operating Companies (BOCs) fought to retain the exclusive use of the "Bell" name at divestiture. Since that time, most have abandoned it.) In 1996, SBC announced its plan to acquire Pacific Telesis, the holding company for Pacific Bell and Nevada Bell; that merger was completed in April 1997. In January 1998, SBC announced its intent to acquire SNET (Southern New England Telephone). On May 11, 1998, SBC announced its intention to acquire (Whoops, merge with) Ameritech. Now you know why the company changed its name to SBC. And by the time you read this, it will probably have bought some more phone companies, if the U.S. government allows it.
SOW
Statement Of Work. When you employ a consultant, he or she should give you a SOW ” a list of all the things he or she is going to do for you, God willing.
SP
-
Support Processor.
-
Sending Program.
-
Signal Present.
-
Signal Processor.
-
Signaling Point.
-
Service Provider.
SPA
-
Software Publishers Association. A not-for-profit organization formed in 1984, SPA is a principal software industry trade association which represents leading publishers, as well as start-ups. SPA supports "companies that develop and publish software applications, components, tools and digital content for use on the desktop, client-server networks and on-line." SPA's MPC (Multimedia PC) Working Group has published several versions of MPC standards over the years, with the current version being MPC3. SPA's headquarters is in Washington, DC; it also has offices in Paris, France. Membership totals over 1,200. www.spa.org. See also MPC3.
-
Shared Printer Access. An ISDN term for the sharing of a printer by multiple users. With a Terminal Adapter (TA) on the PC's serial port and another on the serial printer, a remote worker using ISDN BRI can send a print job over the 16 Kbps D channel. Once the transmission is complete, the call is terminated and the printer is available for another remote worker who is similarly equipped.
Space
-
In digital transmission, the space is equated to the zero (0) and the mark is equated to the one (1). In telecommunications, space is the absence of a signal. It is equivalent to a binary "O".
-
Space also stands for Service Creation and Customization.
-
What other people call marketplace, Microsoft calls space. You and I would say, "This product fits into the computer telephony marketplace ." Microsoft would say "This product fits in the computer telephony space."
Space Brokers
Companies that provide all the facilities needed to start a 976 or 900 service. Those facilities include offices, computing equipment, voice processing software, telephone lines and numbers.
Space Control Technology
A euphemism for antisatellite military weaponry. See Hyperspectral Imaging.
Space Diversity
Protection of a radio signal by providing a separate antenna located a few feet below the regular antenna on the same tower to assume the load when the regular transmission path on the same tower fades because of rain, a bird flying through it, etc.
Space Division Multiplexing
Each distinct signal or message travels over a separate physical path such as its own wire or wire pair within a cable.
Space Division Switching
Method for switching circuits in which each connection through the switch takes a physically separate path.
Space Hold
A no traffic line condition where a steady space is transmitted.
Space Junk
See Iridium.
Space Parity
In data transmission, setting the parity bit so it is always zero.
Space Segment
-
The part of a satellite system that is in space.
-
This is also the imprecise term used to describe the band of frequency purchased by the satellite customer. The customer can purchase a portion of the bandwidth of a single transponder or the customer can purchase one or more entire transponder bandwidths.
Spacecraft Switched Time Division Multiple Access
SSTDMA. A method of sharing the capacity of a communications satellite by on-board switching of signals aimed at earth stations.
SPACH
SMS (Short Message Service) point-to-point messaging, Paging, and Access response CHannel. A digital wireless term defined by IS-136, the Interim Standard for digital cellular networks employing TDMA (Time Division Multiple Access). SPACH is a logical channel which is part of the FDCCH (Forward Digital Control CHannel) used to send signaling and control information downstream from the cell site to the user terminal equipment. SPACH is further subdivided into three logical subchannels : ARCH, SMSCH, and PCH. See also ARCH, FDCCH, IS-136, PCH, SMSCH and TDMA.
Spade Lug
A metal connector attached to the end of a piece of wire, typically by soldering or by pressure. The metal spade lug is shaped like a "U." The idea is to slide the flat "U" shaped metal piece under a screw and then tighten the screw, thus making a connection. In the old days, all phones came with spade lug connectors. These days, there are other faster, more efficient ways of connecting phones ” including modular jacks and punchdown tools.
SPAG
-
Europe's Standards Promotion and Application Group.
-
Standards Promotion and Application Group. A group of European OSI manufacturers which chooses option subsets and publishes these in a "Guide to the Use of Standards" (GUS).
Spaghetti Code
A program written without thought, logic or structure. And whose "logic" is therefore very difficult to follow. Some would say this definition covers most software written today. That's unfair.
Spam
-
Hormel's ever popular spiced processed pork product, consisting of leftovers from the processing of pork, plus lots of additives . Spam actually is an acronym for Shoulders, Pork And Ham.
-
Unsolicited commercial email. Unwanted e-mail. The term is derived from Hormel's pink, canned spiced ham that splatters messily when hurled. A milder form of spamming is called crossposting. See Dictionary Attack, Spam Filter, Spambulance Chasing and Spamming .
-
Message posted to numerous Usenet newsgroups to which it has absolutely no relevance (also a verb). See Spamming.
Spam Filter
Software which keeps out spammed email, also called an anti-spam solution. The filter is typically based on certain criteria, like what words the email contains ” like Viagra or horney women ” or who the sender is. The only way to eliminate 100% of your spam email is to allow only emails from email addresses you approve ” one at a time. See Spam.
Spam Mail
See Spam and UBE.
Spambuluance Chasing
More than half the states in the U.S. now have local laws against sending spam email to people who don't want it. The laws typically say that you must have a pre-existing busiess relationship before you can send spam email. The laws spell out financial penalties, some severe. If you receive unsolicited spam from a spammer you can find, you can hire a lawyer and go after the spammer with a class action suit and collect monies from them, either in court or settle your case "on the courtroom's steps." This business is called spambulance chasing, which is a play on the term ambulance chasing ” a term applied to personal injury lawyers who represent people who have been hurt in accidents that can be traced to an organization's neglect.
Spamdexing
A contraction of "spamming the index." The term came from the days when the AltaVista search engine reigned supreme. Back then, people could improve their position in results by including many words many times on their web site. People who ran pornographic sites put entire dictionaries (with tens of thousands of words) on their Web pages in an attempt to increase their hits. That technique doesn't work with Google, since it employs different searching techniques.
Spamming
Random indiscriminate posting of items (often advertisements) on computer bulletin boards. The term is derived from a brand of pink, canned meat that splatters messily when hurled. A milder form of spamming is called crossposting.
Span
-
Refers to that portion of a high speed digital system than connects a C.O. (Central Office) to C.O. or terminal office to terminal office.
-
Also called a T-Span Line. A repeated outside plant four-wire, two twisted-pair transmission line.
-
A call center term. The total duration of a schedule from start time to stop time, including all breaks.
-
SPAN. Service Providers Action Network. Australian industry group of service providers.
-
A single computer file that will explode into or comes from many media ” for example, several floppy disks or zip disks. See Spanned Archive.
Span Line
A T-1 link.
Span Powered
In T-1, refers to the application of a varying voltage (+130V to - 130V) to the digital cable pairs to maintain a 60mA DC current at each repeater and at the customer premises (this power is generally used for regeneration, loop backs, keep alive signals and alarms).
Spanned Archive
A spanned archive is typically a .ZIP or self-extracing .EXE files that was created and spans across multiple removable media, e.g. floppy disks
Spanning Explorer Packet
Follows a statically configured spanning tree when looking for paths in an SRB network. Also known as a limited-route explorer packet or a single-route explorer packet.
Spanning Tree
Spanning Tree (802.1d) is a protocol that is resident on network bridges and switches that allows each device to communicate with all other Spanning Tree Protocol (STP) enabled devices on a port-by-port basis to detect and manage redundant links within a network.
Spanning Tree Algorithm
STA. An algorithm, the original version of which was invented by Digital Equipment Corporation, used to prevent logic loops in a bridged network by creating a spanning tree. The algorithm is now documented in the IEEE 802.1d specifications, although the Digital algorithm and the IEEE 802.1d algorithm are not the same, nor are they compatible. When multiple paths exist, says PC Magazine's Frank Derfler, STA lets a bridge use only the most efficient one. If that path fails, STA automatically reconfigures the network to make another path become active, sustaining network operations. This algorithm is used mostly by local bridges; it is not economical for use over leased telephone circuits connecting remote bridges.
Spanning Tree Protocol
STP. Inactivation of links between networks so that information packets are channeled along one route and will not search endlessly for a destination. See Bridge and Spanning Tree.
SPAP
Secure Password Authentication Protocol.
SPARC
Sun Microsystems' RISC-based (Reduced Instruction Set Computer) architecture for microprocessors. SPARC is the basis for Sun's own computer platforms.
SPARCengine
Sun Microsystems' standard microprocessors supporting SBus expansion modules and I/O. 50Mhz and above speeds. Up to 512 MB memory on-board.
Sparklies
Small stars in a television picture which result from interference.
Spare Pairs
In existing distribution systems, twisted pairs that are not being used and can be used to serve new communications devices. Spare pairs are exactly what they sound like ” spare pairs of cables. Best to install as many spares as you can when you initially wire up a building or office. Remember Newton's Rule: You'll always need twice as much cabling as you ever dreamed in your wildest dreams you'd need.
Sparing
A method of providing redundancy, or fault tolerance, in systems or networks through a design which includes one or more spare elements. Thereby, a spare element (e.g., a system processor or network circuit) is available in the event of a failure. A common approach is "N+1 Sparing," which adds one backup element to the number required at full anticipated load. While sparing is expensive, it is essential in mission-critical applications environments, where system and network resiliency demands 100% up-time. See also N+1 Sparing.
Spark
An arc of very short duration.
Spark Gap
Terminals or electrodes designed to permit spark discharges to take place across a gap.
Spark Test
A test designed to locate pin-holes in a wire's insulation by application of an electrical potential across the material for a very short period of time while the wire is drawn through an electrode field with one end of the wire grounded.
Sparse Network
-
A network concept describing an environment in which the intelligence of the End Offices (Central Offices) largely is stripped away in favor of the placement of relatively few centralized computer platforms which perform the majority of call processing. The dumb switches make calls to the centralized processors which consult associated databases, providing the switches with instructions. The concept of a Sparse Network is fundamental to that of the Advanced Intelligent Network (AIN).
-
A network concept involving many fewer End Offices than are currently deployed. Rather than a user gaining access to a local End Office, traffic would be concentrated at local points and shipped to a larger and more capable office serving a much larger geographic area. Advances in transmission technology, namely fiber optics, make this concept feasible as the cost of transmission bandwidth is dropping precipitously, while the cost of switches (particularly intelligent switches) is not. Hence the concentration of switches and switch intelligence.
SPATA
SPeech And daTA. Watch for this expression to pick up steam once true integration of voice and data occurs. The expression does not come from the sentence : "Spata to integrate today than tomorrow."
Spatial Data Management
A technique which allows users access to information by pointing at picture symbols on the screen.
SPC
-
Stored Program Control. All phone systems these days are SPCs. There's stored software, which is the program, which controls the computer or microprocessor which in turn controls the operation of the switch. Thus switches are stored program control.
-
Signal Processing Component.
SPC Allocation Service
An SCSA definition. A service which allocates SPCs (Signal Processing Components) to Groups.
SPCAS
SPC Allocation Service.
SPCS
Stored Program Controlled Switch. A digital switch that supports call control, routing, and supplementary services provision under software control. Pretty well switches made after 1970 in North America are SPCSs.
SPCL
SPectrum CeLlular error-correction protocol.
SPE
-
Switch Processing Element or Signal Processing Element.
-
Synchronous Payload Envelope. A SONET term describing the envelope which carries the user data, or payload. The SPE comprises 783 octets, organized into 87 columns and 9 rows. Three different payload structures are defined to address different input requirements:
-
Direct-to-STS-1 line rate multiplexing takes 28 DS-Is, 14 DS-ICs or 7 DS-2s directly into the 51.84 Mbps rate. Each is uniquely transported within the SPE;
-
Asynchronous DS-3 Multiplexing takes a complete asynchronous DS-3 bundle (the output of an M13 for example) into the SPE;
-
Synchronous DS-3 Multiplexing maps a Syntran DS-3 signal to the SPE. See also VT.
-
Semiconductor production equipment. SPE is used on Wall Street.
Speaker Adaptive
Speech recognition which improves with use. See Speech Recognition.
Speaker Dependent Voice Recognition
Technology capable of recognizing speech from a given user or others who sound like this user after completion of an enrollment procedure. It is not voice verification although it is sometimes confused with this technology.
Speaker Identification
Speaker identification is used to determine the identity of a known speaker. It is accomplished by taking spoken input and searching a database of all known system users for a match. Due to its speaker dependent recognition characteristics, you must first be enrolled as a user prior to using the system. To enroll as a user, an individual is required to speak one or more password phrases which are recorded. These phrases create a reference templates which are stored in the system user database for later use during identification sessions. When in operation, the individual using the system is prompted for a specific password or password phrase. When speaking the prompted password as input it creates a new template. This template is then compared to all reference templates in the system for that particular password. The reference template with the closest match is selected. The uniqueness of each user's voice and the finite number of users of the system makes the identification accuracy quite high. With speaker identification the speaker does not claim to be a particular individual. He or she is identified from a group of common users. For the most part, this technology is used for hands free operation of a system where messages and other information specific to that identified individual are pulled-up for use at that time.
Speaker Independent Voice Recognition
SIR or SIVR. Technology capable of recognizing any user's voice without prior training or knowledge of the user. SIR converts speech to accurate and meaningful textual information (typically ASCII). SIR is used to accept input from callers to voice processors where the callers are using rotary dial phones instead of touchtone phones. SIR can substitute for the numbers on the DTMF keypad and can add the benefit of a few basic voice commands, e.g., Yes, No, Help, etc. Because computer processing demands are formidable with speaker independent recognition, accurate speaker independent products are created with limited vocabularies. In contrast, trainable or speaker dependent recognizers can feature larger vocabularies at lower prices. SIR has been slowly gaining acceptance in telephone applications. SIR is increasingly used in automated operator assistance applications. SIR will see increased use as system builders respond to pressures to provide voice processing functions to the enormous rotary phone installed base domestically and abroad.
Speaker Recognition
Having a machine recognize human voice. This is an imprecise term.
Speakerphone
A telephone which has a speaker and microphone for hands free, two-way conversation. Western Electric (now Lucent Technologies) invented the loudspeaker. Western Electric was a very big name in the sound business prior to the 1956 Consent Decree. Watch the credits at the end of old movies, and you'll see "Sound by Western Electric." The original speakerphone was called the "loud-speaking telephone." Originally, a telephone loudspeaker was a peripheral device which connected to the telephone set. It wasn't until the late 1970s that they were integrated into the telephone to become speakerphones. See also Sound.
Special Access
The lease of private, dedicated circuits along the network of an ILEC or CAP, which run from or to the long distance carriers POP. Examples of special access services are telecommunications lines running between POPs of a single long distance carrier, from one long distance carrier POP to the POP of another long distance carrier, or from an end-user to its long distance carrier POP. Special access services do not require the use of switches.
Special Access Code
See Service Area Code.
Special Area Code
See Service Area Code
Special Assembly
When a phone company builds or engineers something into a circuit or circuits which is not spelled out in their tariffs and which you, the customer, want, for whatever reason. They may sell you the special assembly at a high price, or at a low price. "Special assemblies" were, in the old days, ruses to avoid the strict pricing of the tariff and allow the phone company to drop its rates. These days they could be for anything.
Special Billing Number
-
A phone number assigned to certain customers for billing purposes. It cannot be called. It may be given to an operator as the calling number on an outgoing paid call, or it may be used as a "third number billed" number. It's designed as a measure of security and accounting convenience.
-
A Verizon definition. A Customer Record Information System (CRIS) account number, in the form of a fictitious billing telephone number (BTN), which is used for non-WTN (working telephone number) specific products and services, such as unbundled loops and billable directory listings.
Special Characters
Microsoft calls special characters that ones not found on your computer's keyboard. In Windows, these characters are accessible through Character Map, an application in the Accessories folder.
Special Distribution
A call center term. A half-hourly or quarter-hourly call volume or average handle time distribution created for a day in which calling patterns differ significantly from those normally occurring on that day of the week.
Special Grade Access Line
An AUTOVON access line specially conditioned, usually by providing amplitude and delay equalization, to give it characteristics suitable for handling special services; e.g., lower signaling rates of 600 to 2400 bits per second.
Special Grade Network Trunk
A trunk specially conditioned by providing amplitude and delay equalization for the purpose of handling older special services such as "medium-speed" data (600 to 2400 bps); rapidly being made archaic by improvements in transmission facilities.
Special Information Tone
SIT. A series of tones played by the telephone company at the beginning of a recorded announcement, such as indicating the telephone number dialed is no longer in service, has been changed, and so on. Automatic dialers may have the capability of recognizing the different sets of tones, allowing the user to decide whether to pass certain ones through to the agents or filter them out.
Special LATA Access
An LEC (Local Exchange Company) -tariffed service offering that provides for a non-switched communications path (access link) between an long distance company Point of Presence (POP) and the premises of its end users, or to an LEC central office for centrex services. It includes all LATA access services that do not use an LEC switching system (end office or access tandem).
Special Mobile Group
See SMG.
Special Night Answering Position
Provides either a console or a preassigned single extension phone to answer all incoming night calls.
Special Routing Code
A 3-digit code in the form 0XX and 1XX available for use within a network and used to modify routing or call-handling logic. End users are prevented from using system codes by the arrangement of the switching equipment to block all customer-dialed calls with a 0 or a 1 in the fourth digit of a 10-digit number, as well as 7- digit calls with a 0 or 1 in the first digit.
Special Service Circuit
A circuit used to provide a special service to a specific customer.
Special Services
A variety of services that are separate from the public switched network.
Special Temporary Authority
See STA.
Specialized Common Carrier
A company providing domestic long distance telecommunications services other than AT&T. See Other Common Carriers.
Specific Absorption Rate
See SAR.
Specific Gravity
The ratio of the weight of any volume of substance to a weight of an equal volume of some substance taken as a standard, usually water for liquids and hydrogen for gases.
Specific Inductive Capacity
The direct measure of the ability of a substance to store up electrical energy when used as a dielectric material in a condenser. See also Dielectric Constant.
Speckle
The bright and dark spots on the end face of a fiber caused by the interference of modes.
Spectral Bandwidth
In telecommunications, the spectral bandwidth for single peak devices is the difference between the wavelengths at which the radiant intensity is 50% (or 3dB) down from the maximum value.
Spectral Efficiency
The efficiency of a radio system in its use of the radio spectrum, usually expressed in bits per Hz for digital radios and KHz per voice channel in analog radios.
Spectrogram
A basic research tool for the speech scientist which provides a three- dimensional visual representation of speech.
Spectronics
Technology seen from the point of view of the electromagnetic spectrum. Examples include 60 hertz power lines, 400 megahertz microprocessors, and 190 terahertz fiber optics.
Spectrum
A continuous range of frequencies, usually wide in extent within which waves have some specific common characteristics. See Spectrum Designation of Frequency.
Spectrum Analyzer
Tunable RF instrument which displays a portion of the RF spectrum with amplitude of signals on the vertical axis and frequency on the horizontal axis on a screen. Used in TSCM to analyze transmissions for the characteristics of an illegitimate transmitter (radio bug).
Spectrum Buffer
The slice of radio spectrum required by the FCC to stop adjacent radio and TV stations from interfering with each other.
Spectrum Cap
The spectrum limit imposed by the FCC on companies to promote competition. On November 8, 2001, the FCC rule to eliminate the spectrum cap (some- times referred to as the CMRS spectrum cap) to become effective on January 1, 2003. In the interim, the cap will become 55 MHz for all markets (up from 45 MHz in metropolitan areas).
Before November 2001, the spectrum cap was determined by MSA/RSA boundaries, and was 45 MHz in urban areas (MSAs) and 55 MHz in rural areas (RSAs). For PCS to PCS overlaps or cellular to PCS overlaps, the PCS property must have at least 10% of its population in the MSA/RSA to hit the cap. For cellular properties, the cross-interest rule prohibits a company from owning one band and having more than a 20% interest in the other band. As a part of the November 2001 ruling , the FCC has changed the cross interest requirement to apply to Rural Statistical Areas (RSAs) only.
Spectrum Designation Of Frequency
A method of referring to a range or band of communication frequencies. In American practice the designator is a two- or three-letter abbreviation for the name. In ITU practice, the designator is numeric. These ranges or bands are:
| FREQUENCY RANGE | TYPICAL AMERICAN DESIGNATOR | ITU FREQUENCY BAND DESIGNATOR |
|---|---|---|
| 30 - 300 Hz | ELF (Extremely Low Frequency | 2 |
| 300 - 3000 Hz | ULF (Ultra Low Frequency | 3 |
| 3 - 30 kHz | VLF (Very Low Frequency) | 4 |
| 30 - 300 kHz | LF (Low Frequency) | 5 |
| 300 - 3000 kHz | MF (Medium Frequency) | 6 |
| 3 - 30 MHz | HF (High Frequency) | 7 |
| 30 - 300 MHz | VHF (Very High Frequency) | 8 |
| 300 - 3000 MHz | UHF (Ultra High Frequency) | 9 |
| 3 - 30 GHz | SHF (Super High Frequency) | 10 |
| 30 - 300 GHz | EHF (Extremely High Frequency) | 11 |
| 300 - 3000 GHz | THF (Tremendously High Frequency) | 12 |
| FREQUENCY RANGE | ITU FREQUENCY BAND DESIGNATOR |
|---|---|
| 3 - 30 THz | 13 |
| 30 - 300 THz | 14 |
| 300 - 3000 THz | 15 |
| 3 - 30 PHz | 16 |
| 30 - 300 PHz | 17 |
| 300 - 3000 PHz | 18 |
| 3 - 30 EHz | 19 |
| 30 - 300 EHz | 20 |
| 300 - 3000 EHz | 21 |
| THz = Terahertz (10 to the 12th power hertz) | |
| PHz = Petahertz (10 to the 15th power hertz) | |
| EHz = Exahertz (10 to the 18th power hertz) | |
cell business. It is the process of managing the radio spectrum" for purposes of imparting efficiency and intelligence to the spectrum as well as monitoring the spectrum. Spectrum management not only reduces the factors that will hinder the optimal efficiency of the allocated spectrum but also improves the overall performance of each cell and consequently the overall cellular network. Spectrum Management is based on network management principles, the difference being that instead of network elements, it is the spectrum that is being managed. Spectrum management takes into account variables like co-channel and adjacent channel interference, RSSI (Received Signal Strength Indication) values, power levels, frequencies etc. Spectrum Management involves the gathering and using such information proactively to improve network performance. The collected data can be used to generate information that is smart, concise and meaningful. This type of information will help in quicker and smarter decisions thus reducing the delay significantly and supply the carriers with an advantage that not reduces their cost but also adds value to their networks by making them smart, more reliable and proactive.
Spectrum Management Agency
See SMA.
Spectrum Swarming
The overuse of a range of radio frequencies.
Speech API
See MIcrosoft Speech API.
Speech Application Language Tags
See SALT.
Speech Concatenation
A term used in voice processing for economical digitized speech playback that uses independently recorded files of phrases or file segments linked together under application program control to produce a customized response in natural sounding language. For example, order status, bank balances, bus schedules or lottery results, etc. Concatenation is done for speed and economy. It lends itself to limited and structured vocabularies that are best stored in RAM (Random Access Memory) or speedily accessible from disk. Concatenation does not replace Text-To-Speech (TTS) as a method of getting the voice processor to deliver its responses. Concatenation, however, can be an excellent complement to TTS when a voice application demands broad, real time vocabulary production. See Text-to-Speech.
Speech Digit Signaling
Signaling in which digit time slots used primarily for encoded speech are periodically used for signaling (as, optionally , in ISDN). See also ISDN.
Speech Enabled Telephony
In the old days you used a telephone by rotary dialing or pushing buttons. In the new "speech enabled" telephony you talk, not dial. "Please call mother." The phone system understands you. It dials your mother. Speech enabled telephony makes heavy use of speech recognition and text-to-speech ” in order to talk to you. You see these technologies embodied in "personal assistants," pseudo-assistants that understand your commands over the phone. Typically they find phone numbers, dial them, read you your voice and email messages, allow you to respond and then send your message over the Internet or over your corporate intranet. Speech enabled telephony allows your customers to call in, ask for and hear information specific for them. As speech recognition over the phone has improved by leaps and bounds in recent years, we'll see speech enabled telephony become more and more powerful and its uses broaden dramatically. It'll never be as intelligent as a full-time , intelligent secretary. But it will get close, or at least, appear to get close.
Speech Recognition
Voice recognition is the ability of a machine to recognize your particular voice. This contrasts with speech recognition, which is different. It is the ability of a machine to understand human speech ” yours and everyone else's. Voice recognition needs training. Speech recognition doesn't. In the August/September, 1996 issue of a magazine called Speech Technology, David L. Basore talked about recent advantages which are making speech recognition systems much more natural. He wrote, "Speech recognition technology currently supports a wide range of viable applications, from voice controlled VCR remotes to sophisticated call center IVR applications. It can be separated conveniently into the following three categories:
-
Isolated word and phrase recognition in which a system is trained to recognize a discrete set of command words or phrases and to respond appropriately.
-
Connected word recognition in which a system is trained on a discrete set of vocabulary words (for example, digits), but is required to recognize fluent sequences of these words such as credit card numbers.
-
Continuous speech recognition in which a system is trained on a discrete set of subword vocabulary units (e.g., phonemes), but is required to recognize fluent speech. For more advanced applications, the vocabulary can be unlimited and the job of the recognizer is to understand the meaning of the spoken input.
A speech recognition system usually is made up of an input device, a voice board that provides analog-to-digital conversion of the speech signal, and a signal processing module that takes the digitized samples and converts them into a series of patterns. These patterns are then compared to a set of stored models that have been constructed from the knowledge of acoustics, language , and dictionaries. The technology may be speaker dependent (trained), speaker adaptive (improves with use), or fully speaker independent. In addition, features such as barge -in capability, which allow the user to speak at anytime , and key word spotting, which makes it possible to pick out key words from among a sentence of extraneous words, enable the development of more advanced applications.
For an explanation of when to and when not to use speech recognition, see Microsoft Speech API.
Speech Recognition Grammer Format
See SRGF.
Speech Synthesis Markup Language
See SSML.
Speed Bumps
When your host system processes information faster than your network can handle and forces you to slow down.
Speed Calling
An optional feature of a telephone system which allows the placing of calls to frequently called numbers though the use of an abbreviated number of dial digits. For example, call mom by dialing *123. Also called abbreviated dialing.
Speed Dial
A feature that enables a PBX or PBX phone to store certain telephone numbers and dial them automatically when a code is entered. See Speed Dialing.
Speed Dialing
Permits fast dialing of frequently used numbers. A repertory of numbers may be stored in the instrument and/or in the telephone switch. Usually a button or one, two or three digits are dialed to activate speed dialing.
Speed Number
A one, three, or four digit number that replaces a seven or ten digit telephone number. These numbers are programmed into the switch in the carrier's office or in a PBX.
Speed Of Light
See Velocity of Light.
Speed Of Light In A Vacuum
See Velocity of Light.
Speed Matching
Feature that provides sufficient buffering capability in a destination device to allow a high-speed source to transmit data at its maximum rate, even if the destination device is a lower-speed device.
Speech Digit Signaling
Signaling in which digit time slots used primarily for encoded speech are periodically used for signaling (as, optionally, in ISDN). See also ISDN.
Speech Enabled Telephony
In the old days you used a telephone by rotary dialing or pushing buttons. In the new "speech enabled" telephony you talk, not dial. "Please call mother." The phone system understands you. It dials your mother. Speech enabled telephony makes heavy use of speech recognition and text-to-speech ” in order to talk to you. You see these technologies embodied in "personal assistants," pseudo-assistants that understand your commands over the phone. Typically they find phone numbers, dial them, read you your voice and email messages, allow you to respond and then send your message over the Internet or over your corporate intranet. Speech enabled telephony allows your customers to call in, ask for and hear information specific for them. As speech recognition over the phone has improved by leaps and bounds in recent years, we'll see speech enabled telephony become more and more powerful and its uses broaden dramatically. It'll never be as intelligent as a full-time, intelligent secretary. But it will get close, or at least, appear to get close.
Speech Recognition
Voice recognition is the ability of a machine to recognize your particular voice. This contrasts with speech recognition, which is different. It is the ability of a machine to understand human speech ” yours and everyone else's. Voice recognition needs training. Speech recognition doesn't.
In the August/September, 1996 issue of a magazine called Speech Technology, David L. Basore talked about recent advantages which are making speech recognition systems much more natural. He wrote, "Speech recognition technology currently supports a wide range of viable applications, from voice controlled VCR remotes to sophisticated call center IVR applications. It can be separated conveniently into the following three categories:
-
Isolated word and phrase recognition in which a system is trained to recognize a discrete set of command words or phrases and to respond appropriately.
-
Connected word recognition in which a system is trained on a discrete set of vocabulary words (for example, digits), but is required to recognize fluent sequences of these words such as credit card numbers.
-
Continuous speech recognition in which a system is trained on a discrete set of sub- word vocabulary units (e.g., phonemes), but is required to recognize fluent speech. For more advanced applications, the vocabulary can be unlimited and the job of the recognizer is to understand the meaning of the spoken input.
A speech recognition system usually is made up of an input device, a voice board that provides analog-to-digital conversion of the speech signal, and a signal processing module that takes the digitized samples and converts them into a series of patterns. These patterns are then compared to a set of stored models that have been constructed from the knowledge of acoustics, language , and dictionaries. The technology may be speaker dependent (trained), speaker adaptive (improves with use), or fully speaker independent. In addition, features such as barge-in capability, which allow the user to speak at anytime, and key word spotting, which makes it possible to pick out key words from among a sentence of extraneous words, enable the development of more advanced applications.
For an explanation of when to and when not to use speech recognition, see Microsoft Speech API.
Speech Recognition Grammer Format
See SRGF.
Speech Synthesis Markup Language
See SSML.
Speed Bumps
When your host system processes information faster than your network can handle and forces you to slow down.
Speed Calling
An optional feature of a telephone system which allows the placing of calls to frequently called numbers though the use of an abbreviated number of dial digits. For example, call mom by dialing *123. Also called abbreviated dialing.
Speed Dial
A feature that enables a PBX or PBX phone to store certain telephone numbers and dial them automatically when a code is entered. See Speed Dialing.
Speed Dialing
Permits fast dialing of frequently used numbers. A repertory of numbers may be stored in the instrument and/or in the telephone switch. Usually a button or one, two or three digits are dialed to activate speed dialing.
Speed Number
A one, three, or four digit number that replaces a seven or ten digit telephone number. These numbers are programmed into the switch in the carrier's office or in a PBX.
Speed Of Light
See Velocity of Light.
Speed Of Light In A Vacuum
See Velocity of Light.
Speed Matching
Feature that provides sufficient buffering capability in a destination device to allow a high-speed source to transmit data at its maximum rate, even if the destination device is a lower-speed device.
Speech Synthesizer
A device that produces human speech sounds from input in another form.
Speech Transmission Index
STI. A measure with a range from 0 to 1.0; 1.0 represents the best possible understanding of a given message. It measures how much of the message can be lost in transmission and still be understood .
Speeds and Feeds
In the telecom world, speeds and feeds means the various technical characteristics of the various transmission services it offers. Speeds and feeds covers everything from the speed of the circuit to what media you need for it work ” coaxial, copper wire, fiber, etc. The telecom industry has been widely criticized for its fixation on speeds and feeds and, consequently, paying little attention to user applications ” what the speeds and feeds are used for.
Speedsync
See Laplink.
SPF
Shortest Path First.
Spherical Semiconductor
An integrated circuit, developed by BALL Semiconductor, created on the surface of a one-millimeter silicon sphere, and designed to compete with conventional integrated circuits.
SPI
-
Service Provider Interface. See Windows Telephony.
-
Serial Peripheral Interface. SPI is a Motorola specification for a full-duplex synchronous serial data link supporting high-speed connectivity at 1 Megabaud between microprocessor CPUs and other devices. The physical connection to the "Mini Board" printed circuit boards supporting SPI is in the form of a four-wire RJ-11 telephone jack. The SPI essentially is a shift register, serving to convert from parallel to serial transmission across a standard twisted-pair telephone connection over very short distances. Parallel transmission is used internal to computing systems, but generally is considered to be impractical over longer distances, even between adjacent devices, or sometimes between circuit boards housed in the same system chassis. SPI uses the each of the four wires of the RJ-11 connection for different specific purposes, with two used for data transfer and two for signaling and control. One is used for output data from the master device to the slave(s), one from a slave to the master (one slave active at a time), one for clocking in order that the transfer of the data bits is synchronized, and one for turning the individual slaves on and off. SPI is used in a number of Motorola handheld devices and other mobile platform systems. See also RJ-11 and Shift Register.
-
Stateful Packet Inspection . A firewalling technique that builds upon packet filtering technology by taking into account the state (i.e. context) of the session involved in order to decide whether to block or permit a given packet.
SPID
Service Profile IDentifier. When you order an ISDN line, your phone company will give you a SPID for every terminal device (e.g., telephone port , computer port, and fax machine port) you have connected to an ISDN line for circuit-switched (not packet- switched) network access. The SPID does not relate to an ISDN line or even an ISDN B (Bearer) channel. The SPID can be the 10-digit DN (Directory Number, which is a fancy way of saying telephone number), although it usually includes a four-digit suffix or prefix. That suffix or prefix may be the same as the carrier's OCN (Operating Carrier Number), but it doesn't have to be. In any event, the SPID format is determined by the carrier, and is sensitive to the specific CO switch manufacturer, generic software load, and the carrier's local practices. Once programmed into both the customer equipment (e.g., PBX or Terminal Adapter, or TA), the SPID provides the appropriate service mode (a fancy way of saying services and features) for each device communicating over the ISDN line and B channel. By the way, your SPID changes when your area code changes. When your telephone company assigns you a SPID, you should write it down. Otherwise, you'll have a devil of a time getting them to tell you what it is in the event that you have to reprogram your TA (Terminal Adapter). Trust me, as I speak the truth. By the way, you don't have to worry so much about writing down the SPID, if you are set up for AutoSPID, which automatically negotiates the SPID between your terminal equipment and the CO.
Spider
A program that prowls the Internet, attempting to locate new, publicly accessible resources such as WWW documents, files available in public FTP archives, and Gopher documents. Also called wanderers or robots (bots), spiders contribute their discoveries to a database, which Internet users can search by using an Internet-accessible search engine.
In January, 1998, I received a solicitation for Bull's Eye Gold, which bills itself as the premier email address collection tool. "This program allows you to develop targeted lists of email addresses. Doctors, florists, MLM, biz opp...Our software uses the latest in search technology called "spidering". By simply feeding the spider program a starting website it will collect for hours. The spider will go from website to targeted website providing you with thousands upon thousands of fresh targeted email addresses. When you are done collecting, the spider removes duplicates and saves the email list in a ready to send format. No longer is it necessary to send millions of ads to get a handful of responses." See also Bot.
Spidering
See Spider.
SPIE
Society of Photometric Industry Engineers or Society of PhotoOptical Instrumentation Engineering.
Spiff
A telemarketing term. An award that forms the prize for a quick motivational incentive. Spiffs can include movie tickets, pizza parties, gifts selected from a catalog and other such prizes.
Spike
An in-phase impulse causing spontaneous increases in voltage. Spikes are very fast impulses, less than 100 microseconds, of high-voltage electricity ranging from 400 volts to 5,600 volts superimposed on the normal 120V AC electrical sine wave. See also Metal Oxide Varistor.
Spike Markets
A term developed by Apple. By "spike," the company means software and hardware combinations that allow Apple to rise (spike) through a noisy marketplace. By doing this, Apple hopes to grab attention in some reasonably horizontal niche markets and show people why a Mac is worth a few (hundred) extra bucks. The first of these spikes is a foray into home video editing, using Apple's new Performa 6400 and a piece of software called Avid Cinema.
Spike Mike
Contact microphone for listening through walls.
Spikes
Electrical anomalies represented as short duration, instantaneous, very high voltage fluctuations on an electrical service.
Spill-Forward Feature
A service feature, in the operation of an intermediate office, that, acting on incoming trunk service treatment indications , assumes routing control of the call from the originating office. This increases the chances of completion by offering the call to more trunk groups than are available in the originating office.
SPIN
Service Provider Identification Number. A number that identifies the telecommunications service provider from which schools and libraries obtain discounted service through the Schools and Libraries Universal Service Program. The program, which was created by the Telecommunications Act of 1996 and which is funded by the Universal Service Fund, provides for discounted telecommunications services, Internet access and internal connections . The Schools and Libraries Corporation approves applications for such discounted rates, which are known collectively as "E-rate."
Spin a Board
When people say "spin a board," they mean to take a given printed circuit card and do a re-layout of the components and traces, In short, to do a board revision. This is typically associated with an ECO (Engineering Change Order).
Spin Stabilization
A method of preventing a satellite from tumbling by spinning it about its axis.
SPINA
Subscriber Personal Identification Number Access. A term identified in the TIA IS- 53 (Interim Standard 53), addressing security in cellular telephone networks. SPINA requires the user to enter a PIN in order to gain access to the network. Access is granted for a specified period of time or until the occurrence of some event, such as the terminal's being turned off. The PIN is transmitted "in the clear," i.e. unencrypted; therefore, it is susceptible to interception. See SPINI.
SPINI
Subscriber Personal Identification Number Intercept. A term identified in the TIA IS- 53 (Interim Standard 53), addressing security in cellular telephone networks. Unlike SPINA, SPINI may require that the user enter a PIN before each call in order to gain access to the network. Both SPINI and SPINA typically require a 4-digit PIN. The PIN is transmitted "in the clear," i.e. unencrypted; therefore, it is susceptible to interception. See SPINA.
Spindle
A spindle is metal rod serving as an axis for something that spins around it. Lapops are typically called one, two or three spindle machines. A one spindle machine would be a laptop with only a hard disk. A two spindle machine means that the laptop typically has a hard disk and a floppy disk or a hard disk and a CD or DVD drive. A three spoindle machine that the laptop an internal floppy drive, a hard disk and a CD/DVD drive, i.e. three rotating media sources.
Spindle Synchronization
A process that coordinates all hard disks in a RAID array to use a single drive's spindle synchronization pulse.
Spinner
A name given to people in the United States who regularly change their long distance carrier. Several million people each year switch their long distance carriers. The problem and cost of churn has become fairly major for the long distance industry.
Spinning
The practice of allocating shares in hot IPOs personally to executives as an inducement to win their company's investment banking business. If they sell their newlyacquired shares the instant the company's stock starts to trade on the stock exchange, this practice is called flipping. For a longer explanation, see Flipping.
Spiral Life Cycle
A term used in COM development. Another term used to describe the iterative development process. Opposite of waterfall life cycle.
Spiral Wrap
A term given to describe the helical wrap of a tape or thread over a core.
SPIRIT
European consortium focused on standardizing telecom operators' procurement processes.
SPIROU
Signalisation Pour I'Interconnexion des R seaux OUverts (ETSI ISUP V3 modified by ART).
Spitting Dollar Bills
When a cell site goes on the air, it is now worth money ” it spits dollar bills ” as opposed to being a construction project and demanding dollar bills.
Splash Tone
Distinctive sound used on some phone systems to indicate that a command has been received, or that something has to be done. Vaguely resembles water being splashed.
Splashing
A "splash" happens when an Alternate Operator Service (AOS) company, located in a city different to the one you're calling from, connects your call to the long distance carrier of your choice in the city the AOS operator is in. Splashing does not imply backhauling, but it often happens. For example, let's say you're calling from Hotel Magnificent in Chicago. You ask AT&T to handle your call. The AOS, located in Atlanta, "splashes" your call over to AT&T in Atlanta. But you're calling Los Angeles. Bingo. Your AT&T call to LA is now more expensive than it would be if you had been connected directly to AT&T from Hotel Magnificent in Chicago.
Splat
A slang expression for the asterisk character (*) that you can yell across a crowded room without fear of being misunderstood.
Splice
Verb. The joining of two or more cables together by splicing the conductors pair- to-pair.
Splice Box
A box, located in a pathway run, intended to house a cable splice.
Splice Closure
A device used to protect a cable or wire splice.
Splice Tray
A place where you splice fiber optic cables and then leave them in the splice tray. It's an elaborate connector.
Splicing Chamber
An underground concrete vault in which cables may be spliced, and transmission equipment may be located.
Spline
A curve shape produced on a computer or video device by connecting dots or points at various intervals along the curve. In digital picture manipulators, each key frame becomes a point on a curve and the user can control how straight or curved the path of the transformed image is as it travels through the key frame points.
Splint
A pejorative word for Sprint, the third largest interexchange carrier. The word was created by William G. McGowan, the driving force behind MCI for so many wonderful years.
Split
-
A call center term. Split is an ACD routing division that allows calls arriving on specific trunks or calls of certain transaction types to be answered by specific groups of employees. Also referred to as gate or group. Same as Group. See ACD or Automatic Call Distributor.
-
See Overlay Area Code.
Split Access To Outgoing Trunks
Two separate trunk groups provided for direct outward dialing which can be accessed by dialing the same trunk access code. Controlled on class of service basis.
Split Area Code
See Overlay Area Code.
Split Channel Modem
A modem which divides a communications channel into separate send and receive channels. Most modems which use the dial-up phone network are split channel ” meaning they can transmit and receive simultaneously over a two wire circuit. See also Split Stream Modem, which is another term for the same thing.
Split Horizon
The view a router has of a wide area network interface in a partial mesh environment where an incoming packet may need to be sent out the same interface over which it is received to reach its ultimate destination. Split horizon is normally disabled to ensure that this cannot occur and that routing loops are not created. This posed a problem with frame relay because packets should be sent back out the same physical interface over which they have been received, but not the same logical interface. Router vendors have now solved this problem, enabling routers to support partially meshed frame relay networks.
Split Link
When one multiplexer uses two links to communicate to two separate multiplexers.
Split Pair
Something that happens in cable splicing when one wire of a pair gets spliced to the wire of an adjacent pair. It's more accurate to call it a mistake. This error cancels the crosstalk elimination characteristics of using twisted pair wiring in which the two conductors necessary for the circuit are twisted around each other. When you have a split pair, the two conductors come from two different pairs.
Split Resplit Method
Split Resplit is an inductive wiretap. Telephone wires are twisted in bundles so as to reduce crosstalk between telephone lines. The Split-resplit method involves crossing the target line pair with an unused pair of telephone lines with the goal of increasing crosstalk with the operator's line. The operator's line can then inductively pick up conversations on the target line. Because the signal levels are low in the pick up line, audio amplifiers have to be used to clearly hear intercepted audio.
Split Seeks
A process by which Novell NetWare SFT III splits multiple read requests between the two servers' disks for simultaneous processing and faster disk rads. Disk reads are split between both servers, with only one server doing a particular read and sending the data read over the MSL (if necessary) to the other server. MSL is the Mirror Server Link.
Split Stream Modem
A modem which can handle multiple, independent channels over a single transmission path.
Split System
A switching system which implements the functions of more than one logical node.
Split Tunneling
Let's start with tunneling. Tunneling typically means to secure a secure, temporary path for your communications via the Internet. For example, a telecommuter might dial into an ISP (Internet Service Provider), which would recognize the request for a high-priority, point-to-point tunnel across the Internet to a corporate gateway. The tunnel would be set up, effectively snaking its way through other, lower-priority Internet traffic. Now imagine a a corporate network that uses both the Internet and a private Intranet or a VPN (Virtual Private Network). Split tunneling simply means the ability to send material securely (that's the critical word) over both networks. You need a device to do the switching and some software. Some devices enable simultaneous connections through the VPN and to the Internet.
Splitter
-
A network that supplies signals to a number of outputs which are individually matched and isolated from each other. See also Power Divider and Frequency Splitter.
-
A coaxial cable TV device. Imagine a single coaxial cable carrying TV signals. You want to connect two subscribers or two TV sets to this single cable. You insert a splitter, a small cheap (under $10) device. You screw the incoming cable in one side of the splitter. The other side has two screw terminals into which you can screw two coaxial cables ” one for each subscriber, or for each TV set. Splitters are passive devices that simply split the incoming signal to create two or more identical outgoing signals, each of which travels across a tail circuit to a terminal device in the form of a TV set. Since coax splitters don't require external electricity to work, they are unaffected by power outages, although your TV set is. As non-powered passive devices, they also don't boost the power level of the signal, which means that the signal naturally loses some strength.
-
xDSL is the generic name for technology that puts several megabits of a data transmission on a local loop ” from the phone company's central office to your home. A subscriber, like you or I, would use that phone line for two purposes ” first, to get onto the Internet and the Web, and second, to speak on the phone. This means that at our house we'd need a xDSL box into which we'd plug our computer and our various analog phones and fax machines. The industry refers to this box as a "splitter," meaning that it splits the incoming bit stream into voice and data. This is a stupid name for it, since the device is really a multiplexer. And typically such a device would have to be installed by a phone company technician and would replace the demarcation box outside the house. It gets worse. The phone companies have created an adjective called "splitterless" to describe a xDSL box that still splits between voice and data but doesn't require a visit from a telephone company technician. In other words, you'll be able to go down to your friendly local electronics discount store, buy a splitter box, take it home, plug one side into your phone line (your female RJ-11 jack), and into the other side you'll plug your PC and your analog phone instrument or instruments. You won't need a visit from your friendly phone company technician. In short, the concept of "splitterless" refers to whether the phone company needs to send a technician to install the box or not. Splitter means it must send a technician. Splitterless means it doesn't have to. A splitterless box typically contains the electronics for a splitter (to split out voice and data), while a splitter box would still require a DSL modem. By the way, splitterless xDSL technology is not trivial. My friend Paul Sun talks about a splitterless xDSL box as needing to contain five million transistors and have the horsepower of a 1,000 MHz Pentium PC. See also G.Lite, G.990, NIU, and xDSL.
Splitterless
For a detailed explanation, see Splitter immediately above. See also G.Lite and G.990.
Splitterless ADSL
A variation of ADSL in which a splitter is not needed at the customer's premises. Sometimes referred to as G.Lite.
Splitting
-
A filter which splits or separates signals on the basis of their transmission frequency. For example, a splitter can be incorporated into an ATU-R (ADSL Termination Unit-Remote) located at the subscriber premise. The splitter would serve to separate the high-frequency data transmission from the low-frequency POTS voice transmission. The data transmission would then be delivered to a TV set or PC, while the POTS transmission would be delivered to the telephones. See also Filter.
-
A splitter is a telephone console device which permits an operator to consult privately with one party on a call without the other party's hearing. Or permits a three-party telephone conference user to consult privately with one side of the conference while the other is effectively put on hold. Jumping from one party to the other is called "Swapping."
-
See also Splitter.
SPM
-
Subscriber Private Meter.
-
Service Provider Messages.
-
Spectrum Peripheral Module, and is an optical interface. The capacity of SPM is much higher than DTCs (an electric interface), i.e., 2016 channels vs. 480 on DTCs. They take up less physical space and eliminate the need for echo cancellers and various other equipment. These terms are used when referring to all Nortel's products.
SPN
Subscriber Premises Networks.
SPNI
Service Provider Network Identifier.
SPOF
Single Point of Failure. See Single Point of Failure.
SPOI
Signaling Point Of Interface. The demarcation point on the SS7 signaling link between a LEC network and a Wireless Services Provider (WSP) network. The point established the technical interface and can designate the test point and operational division of responsibility for the signaling.
Spoke
An organization that is traditionally doing EDI (Electronic Data Interchange) as a result of a request from one of its customers. Generally has only a few trading partners .
Spontaneous Networking
See Jini.
Spoofing
Spoofing is another word for impersonation. Spoofing happens when someone on a network pretends to be someone else. For example, a person can pretend to have the email address HarryNewton@harryNewton.com when it's not me. Or a computer could pretend to be and identify itself as the Internet site www.HarryNewton.com. Spoofing is done for any number of reasons ” lying, cheating and stealing are good beginnings. You might spoof a computer system in order to access to a computer system and find out my credit card number. You might spoof my email to convince my wife that I was going to buy her a million dollar necklace for her birthday. (She should be so lucky.) See also Public Key Encryption.
SPOOL
Simultaneous Peripheral Operation On Line. A program or piece of hardware that controls a buffer of data going to some output device, including a printer or a screen. A spool allows several users to send data to a device such as a printer at the same time, even when the printer is busy. The spool controls the transmission of data to the device by using a buffer or creating a temporary file in which to store the data going to the busy device. See Spooler and Spooling.
Spooler
A program that controls spooling. Spooling, a term mostly associated with printers, stands for Simultaneous Peripheral Operations On Line. Spooling temporarily stores programs or program outputs on magnetic tape, RAM, or disks for output or processing.
SPOOLING
Simultaneous Peripheral Operations On Line. Spooling means temporarily storing programs or program outputs on magnetic tape, RAM or disks for output or processing. The word "Spooling" is mostly associated with printers. Here's an example: Pretend that a lot of people on your Local Area Network all want to send their reports to the printer today. Instead of each person having control of the printer and relinquishing it only when they're through, each user tells the print Spooler what file they want printed. The program, called the spooler, places the print request in the print queue. When your request reaches the top of the queue, your report is printed out. Using a PC as print spooler slows it down. Best not to use it for much else.
Spot Beam Antenna
A satellite antenna capable of illuminating or focusing on a narrow portion of the earth's surface.
Spot Frame
Single Point Of Termination Frame. See Dedicated Inside Plant.
SPOX
An operating system for digital signal processors from Spectron Microsystems, Goleta, CA, now owned by Dialogic in Parsippany, NJ. Spox is a real-time, multitasking operating system that is optimized for use with fixed and floating point digital signal processors in both single- and multiprocessor systems. The SPOX environment is implemented as a library of relocatable, C-callable modules.
SPP
-
Sequenced Packet Protocol. XNS (Xerox Network Systems) protocol governing sequenced data.
-
Signal Processing Platform.
-
Standard Parallel Port.
SPRE
Special PREfix code. Special digits dialed in order to access features of a telephone system, like a PBX or a Centrex. For example, in order to invoke the Call Pickup feature, a PBX user might pick up the handset, dial a three-digit SPRE code specific to the PBX, and answer the call.
Spread Spectrum
Also called frequency hopping , spread spectrum is a modulation technique used in wireless systems. The data to be transmitted are packetized, and spread over a wider range of bandwidth than demanded by the content of the original information stream. Spread spectrum takes an input signal, mixes it with FM noise and " spreads " the signal over a broad frequency range. Spread spectrum receivers recognize a spread signal, acquire and "de-spread" it and thus return it to its initial form (the original message). A large number of transmissions can be supported over a given range of frequencies, with each transmission comprising a packet stream and with each packet in a stream being distinguished by an ID contained within the packet header. The receiver is able to distinguish each packet stream from all others by virtue of that ID, even though multiple transmissions share the same frequencies at the same time, with the potential for the overlapping of packets. Spread spectrum is highly secure. Would-be eavesdroppers hear only unintelligible blips. Attempts to jam the signal succeed only at knocking out a few small bits of it. So effective is the concept that it is now the principal antijamming device in the U.S. Government's Milstar defense communications satellite system. Spread spectrum technology also is used extensively in wireless LANs and in CDMA (Code Division Multiple Access), the access technique used in many PCS (Personal Communications Systems) cellular systems.
There are two versions of spread spectrum. Direct Sequence Spread Spectrum (DSSS) spreads the signal over a wide range of the 2.4 GHz frequency band. Frequency Hopping Spread Spectrum (FHSS) involves the transmission of short bursts of information over specific frequencies, with the frequency-hopping carefully coordinated between transmitter and receiver. See also CDMA, DSSS and FHSS.
Hedy Lamarr, the actress, created the concept of spread spectrum in 1940 and, two years later, received a U.S. patent for a "secret communication system." The patent was issued to her and George Antheil, a film-score composer, to whom Ms. Lamarr had turned for help in perfecting her idea. Spread spectrum was used extensively by the Allies during the World War II in the Pacific Theater, where it solved the problem of Japanese jamming of radio-controlled torpedoes. World War II electronics were pretty primitive, and Hedy's system used a mechanical switching system, like a piano roll, to shift frequencies faster than the Nazis or the Japanese could follow them. More recently, spread-spectrum has been combined with digital technology, for spy-proof and noise-resistant battlefield communications. In 1962, Sylvania installed it on ships sent to blockade Cuba. Ms. Lamarr never received one penny for her invention. Ms. Lamarr was quite an innovator. She delighted and shocked audiences in the 1930s by dancing in the nude in the movie "Ecstasy," which, sadly, I've never seen.
Spreading Loss
See Free Space Loss.
Sprint
The third largest IXC (IntereXchange Carrier), behind AT&T and MCI, Sprint also is a LEC (Local Exchange Carrier) of significance. Sprint began as a venture of Southern Pacific Railroad, which had the clever idea of using its right-of-way to lay a fiber optic cable network. Subsequently, Southern Pacific sold the network to GTE, at which point it became know as GTE Sprint. The company became known as US Sprint when GTE and United Telecom decided to form a (50/50) joint venture from US Telecom (United's long distance company), GTE Sprint and GTE Telnet. United Telecom bought GTE's interest, acquiring the final 19.9% in 1992. Now it's just called Sprint Corporation. Through its acquisition in 1993 of Centel, Sprint currently operates as a LEC (local exchange carrier) in at least 19 states.
Sprite
As used in computer graphics refers to a graphic image that can move over a background and other graphic objects in a non-destructive manner.
SPS
-
Signaling Protocols and Switching.
-
Standard Positioning Service. The normal civilian positioning accuracy obtained by using the single frequency C/A code in the GPS (Global Positioning System) system.
-
Solution Provider, also called Microsoft Solution Provider. See Microsoft Solution Provider.
-
Standby Power System. A SPS is a form of uninterruptible power supply. It monitors the power line and switches to battery power as soon as it senses a problem. The switch to battery, however, can require several milliseconds, during which time the computer (or whatever else is connected to it) does not receive any power. Standby Power Systems are sometimes called Line-interactive UPSes. See also UPS.
SPTS
Single Program Transport Stream: An MPEG-2 Transport Stream that consists of only one program.
Spud
A special long-handled shovel used to loosen soil in a hole into which you're going to put a telephone pole.
Spudger
Shaped like a dental pick, it's a gadget phone technicians use to find their way through a multi-paired telephone cable in their hunt for one single pair.
Spurious
A term used in voice recognition. A spurious error is said to occur when a sound that is not a valid spoken input is incorrectly accepted as an input speech utterance.
Spurious Emission
Emission on a frequency or frequencies which are outside the necessary bandwidth and the level of which may be reduced without affecting the corresponding transmission of information. Spurious emissions include harmonic emissions, parasitic emissions, intermodulation products and frequency conversion products, but exclude out-of-band emissions.
Spurring Out
Spurring out happens when a telephone company worker is up a telephone pole working on the wires, and his or her spurs come loose from the pole. A related term is pole hug, which is what said technician does after he or she spurs out. Pole hugs usually result in nasty splinters and an awful scare. According to Scott Davis, who contributed this definition, "my impression is that spurring out is a rite of passage for new field techs.
Spurs
-
The sharp metal devices on the climbers used by telephone line-persons (people who climb telephone poles). Such climbing spurs make a mess of wooden telephone poles. See Spurring Out.
-
The cowboy devices awarded by US WEST to privileged persons who have done US WEST some nice favor or are otherwise deserving of honor .
Sputnik
Sputnik was the world's first artificial satellite. It was launched by the Russians on October 4, 1957. It freaked out the Americans and started the space race, which the Americans later won.
SPVC
Soft Virtual Circuit. Or Smart Virtual Circuit.
SPX
Sequenced Packet eXchange.
-
An enhanced set of commands implemented on top of IPX to create a true transport layer interface. SPX provides more functions than IPX, including guaranteed packet delivery.
-
Novell's implementation of SPP for its NetWare local area network operating system.
SQE
Signal Quality Error. The 802.3 specification defines this for signals from the MAU to the NIC. Also referred to as heartbeat, is a signal sent by transceivers after a frame is transmitted in order to verify the connection, and is also used by the transceiver to notify the station that a collision was detected. The SQE is primarily used in 10Base-5 environments as a test signal to reassure the station that the transceiver is still operating properly. Some older network devices will not operate properly unless SQE is enabled; almost all new devices do not require SQE. SQE should always be disabled when a transceiver is connected to a repeater (including a 10BASE-T hub), or if it is not required.
SQL
Structured Query Language. A powerful query language for defining, maintaining, and viewing information in a relational database. The original version, invented by IBM in 1974, was known as SEQUEL (Structured English QUEry Language) and was intended for use in IBM's System R. SQL was first commercialized by Oracle in the early 1990s. SQL has evolved into a complete language for the definition and management of persistent and complex data objects. A favorite query language for DBMSs (DataBase Management Systems) running on mainframes, SQL now also widely runs on PCs and LANs. SQL been standardized by ANSI, although there also exist multiple non-standard dialects that include extensions to that standard. SQL versions have been developed by Access, Informix, Microsoft, Oracle, Sybase, and others. See also ODBC, QBE and SQL Server.
SQL Server
Microsoft SQL Server. A Microsoft retail product that provides distributed database management. Multiple workstations manipulate data stored on a server, where the server coordinates operations and performs resource-intensive calculations.
Square Key System
A square key system is one that has all telephone lines appearing on every telephone and each telephone has a separate button or "key" for each line. See Squared Key System for a longer explanation.
Square Operation
If there are fewer than eight lines in a Merlin system, all users can access all lines. See Squared Key System.
Square Shoes
Toward the end of the 15th century, men's shoes had a square tip, like a duck's beak, a fashion launched by Charles VIII of France to hide the imperfection of one of his feet, which had six toes.
Square Wave
A term used to refer to a digital signal, which is binary in nature. This is in marked contrast to an analog "sine wave," which varies continuously in terms of its amplitude and frequency. In other words, digital signals involve only two values: "1" and "0." Computer systems speak digital. Every value (i.e., letter, number, punctuation mark, and control character) is expressed in terms of a specific and unique combination of 1s and 0s of a specific length according to a particular coding scheme. Not only do computers create and store information in such form, they also output information in that form and they expect to see information presented to them in that form. One advantage of digital communications in the form of a bit stream, or stream of 1 and 0 bits, is that computer communications is supported without the need for conversion to analog and back again for transmission across the network. The bit stream is transmitted in the form of a square wave, which consists of discrete values representing these 1s and 0s.
Within the CPE (Customer Premise Equipment) domain and in an electrically-based mode of operation, this representation generally involves a positive voltage for a "1" and a null voltage (0 voltage) for a "0" ” this is an "on" and "off" approach. Alternatively, a "1" can be represented as a relatively high level of positive voltage such as +3.0 volts, and a "0" as a relatively low level of positive voltage such as +1.5 volts: in this approach, the electrical circuit continues to flow energy in waves of discrete voltage values. Further still, a "1" can be in the form of a positive voltage such as +1.5 volts, and a "0" can be a negative voltage such as -1.5 volts: again, a "wave" approach. Regardless of the approach, within your own domain you can play the square wave game anyway you (and your manufacturer) choose; after all, it's your game and you pay for the privilege of setting your own rules.
In a public network, it is quite a different matter. T-carrier systems, for instance, require that 1s be represented as alternating positive and negative voltages, while 0s are null voltages. Numerous devices in the public network depend on this electrical coding scheme to maintain synchronization. Further and as the public network serves vast numbers of users, there must be uniformity in order for the network to function at all.
In a radio system, the approach is different still, with the square wave taking the form of radio waves of relatively high and relatively low amplitude.
In an optical network, several approaches can be used. One approach calls for the square wave to take the form of light waves of different levels of intensity (i.e., bright and brighter) ”which essentially differences in amplitude, or power level. The second approach calls for the laser light source to pulse on and off, with the presence of light indicating a "1" and the absence of light indicating a "0."
In any event, there are two discrete values represented in the form of "on and off," or "high" and "low," or "plus" and "minus." Digital networks, which use square waves for transmission, offer clear advantages. Most especially, they're much cleaner. Any noise they picked up on their travels across the network is disregarded as the signal is received, boosted and recreated. This is in marked contrast to an analog signal, which simply is amplified, along with any noise which might be present. Square waves are also cheaper to produce. That's good. But if you send a square ringing "wave" to a device like a high-speed modem that's expecting an analog sine wave, that high-speed modem will not respond as it does- n't speak digital at that side of the connection. See also Sine Wave.
Squared Key System
A "squared" key system is one that has all telephone lines appearing on every telephone and each telephone has a separate button or "key" for each line. No one quite knows where the word "squared" came from. So if our explanation bears no relation to the word "squared," sorry. But it goes like this (we think): In the old days there were 1A2 phone systems. These 1A2 phones had buttons on them. These buttons could correspond to trunks ” any trunk. These were called non-squared systems. Then came electronic key systems. Each trunk had to "appear" (i.e. be) the same button on each phone. These electronic key systems were called squared systems. There are advantages and disadvantages. Squared systems are portrayed as having one advantage: You can go to any phone anywhere in the system and punch any button for any trunk and know it to be the same button for the same trunk. Thus less confusion. But this means you can only have as many trunks on your key system as you have trunk buttons on your key telephones. In a non-squared system ” a 1A2, the newer hybrids or some of the newer programmable key systems ” you can have more trunks than you have buttons on each phone. Some phones will have trunks that others don't have and vice versa. Thus you can have more trunks on your phone system than you have buttons on your phones. This means, for example, that four executives can have each have private lines and access to four trunks on a six button phone. (The other button is for Hold.)
Squatter
See Cybersquatting.
Squeaky Clean
I had my bicycle cleaned by the bike shop. When it came back, the brakes squeaked. My bike was squeaky clean.
Squelch
A circuit function that acts to suppress the audio output of a receiver. See also squelching.
Squelching
Referring to the "Rerouting of Pass-Through Traffic During Node Failures", Nortel's "Introduction to SONET Networking" tutorial handbook says, "While tributaries terminating at the failed node cannot be protected, traffic passing through that node is automatically redirected. ... In an action referred to as "squelching," nodes adjacent to the failure replace non-restorable traffic with a path layer alarm indication signal (AIS) to notify the far end of the interruption in service. The squelching feature employs automatically generated squelch maps that require no manual record keeping to maintain." See also AIS.
Squid
A high-performance, full-featured proxy cache server protocol developed for use in the Web. Squid supports the caching of requested Internet objects (data available via HTTP, FTP, and other protocols) on proxy servers that are more proximate to the user than the origin server. Hence, Internet network resources are used more efficiently . Squid comprises a main server Squid program, a Domain Name System (DNS) program and associated database, and management tools. Squid supports caching protocols including CARP, HTCP. and ICP. Squid runs in a number of UNIX Operating System (OS) environments, including AIX, BSD, Linux, HP-UX, and SunOS/Solaris. Squid was funded by the National Science Foundation (NSF). It is free software copyrighted by the University of California San Diego, and is licensed under the terms of the GNU General Public License. "Squid" isn't an acronym, and it really doesn't mean anything: Harris' Lament states "All the good ones are taken."
Squirt the Bird
To transmit a signal up to a satellite. "The crew and talent are ready; when do we squirt the bird?"
SR
-
Speech Recognition. See Speech Recognition.
-
Source Routing: A bridged method whereby the source at a data exchange determines the route that subsequent frames will use.
SRAM
Static Random Access Memory. A form of RAM that retains its data without the constant refreshing that DRAM (Dynamic RAM) requires. SRAM is generally preferable to DRAM because it offers faster memory access times, and can retain data without power. However, it is more expensive to manufacture because it has more electrical components. The most common use for SRAM is to cache data traveling between the CPU and a RAM subsystem populated with DRAM. This improves your PC's performance by reducing the number of DRAM accesses needed. See also DDR-SDRAM, DRAM, EDO RAM, Flash RAM, FRAM, Microprocessor, RAM, RDRAM, SDRAM, and VRAM.
SRC
-
Strategic Review Committee (ETSI).
-
Stupid Rich Customer. One who will buy anything.
SRDC
SubRate Digital Cross-connect.
SRDM
SubRate Data Multiplexer. The Europeans call it SDM. An SRDM typically subdivides DS-0 of 64 Kbps, into a number of circuits, each less than 64 Kbps.
SRF
-
Specifically Routed Frame: A Source Routing Bridging Frame which uses a specific route between the source and destination.
-
Special Resource Function. Another term for an IP (Intelligent Peripheral) in the context of an AIN (Advanced Intelligent Network). The term IP became confusing with the advent of network and services based on the IP (Internet Protocol). See AIN and IP for more detail.
SRGF
Speech Recognition Grammer Format is a VXML (Voice eXtensible Markup Language) language for writing voice recognition grammar. See also VXML.
SRL
Structural Return Loss. A measure of cable impedance uniformity relative to its own impedance.
SRM
-
Sub-Rate Multiplexing. SRM. A technique used to combine data from a number of different digital sources into a basic rate channel, efficiently using the bandwidth on the primary rates for data circuits and/or digitized voice.
-
Storage Resource Management. SRM provides a central view of a company's storage resources and their usage. SRM includes capacity management, configuration management, event and alert management and policy management.
SRMS
Service Request Management System.
SRP
-
Source Routing Protocol. See Bridge.
-
Suggested Retail Price.
SRS
-
Statistics Repository System.
-
Shared Registry System. A neutral, shared, and centralized repository containing the database of Internet domain name information. In conjunction with the expansion of the Domain Naming System (DNS), the Council of Registrars (CORE) has contracted with Emergent Corporation to build, maintain and operate the SRS. SRS supports up to 90 registrars, independent organizations which are authorized to assign the new TLDs (Top Level Domains), comprising .arts, .firm, . info , .nom, .rec, .shop, and .web. See also CORE, DNS, Domain, and URL for longer explanations .
-
Stimulate Raman Scattering. An optical fiber transmission term. Stimulated Raman Scattering (SRS) results from the interaction between the optical transmission signal and the silica molecules in the fiber. SRS affects broadband optical fiber transmission, and affects the overall optical spectrum involved in a DWDM (Dense Wavelength Division Multiplexing) transmission system. The SRS phenomenon manifests itself as a transfer of power from the shorter wavelengths to the longer wavelengths, resulting in a tilt of the optical spectrum. The effect increases as the power of the signal increases, and as the width (density) of the DWDM spectrum increases. See also DWDM.
SRT
-
Station Ringing Transfer.
-
Source Routing Transparent, a token ring bridging standard that is jointly sponsored by the IEEE and IBM. It combines IBM Source Routing and Transparent Bridging (IEEE 802.1 ) in the same unit. This provides a way for universal bridging of token ring LANs supporting IBM and all non-IBM LAN protocols. An SRT bridge examines each data packet on the ring to discover whether the packet is using a source routing or non-source routing protocol. It then applies the appropriate bridging method. See also Bridge, Source Routing and Transparent Routing.
-
System Response Time. It is widely recognized that system response time (SRT), the time between the user's input and the computer's response, is one of the strongest stressors during human-computer interaction. Assessments of the effects of SRT have been conducted for personal computer use in a variety of contexts. As early as 1982, researchers determined that SRT and SRT variability act in concert to increase the stress levels of some personal computer users. With increased SRTs, users rate their general well-being as lower. Also accompanying longer delays are self-reports of annoyance, frustration, and impatience.
SRTS
Synchronous Residual Time Stamp: A clock recovery technique in which difference signals between source timing and a network reference timing signal are transmitted to allow reconstruction of the source timing at the destination.
SS-CDMA
Spread Spectrum Code Division Multiple Access.
SS1
See Signaling System Number 1.
SS2
See Signaling System Number 2.
SS3
See Signaling System Number 3.
SS4
See Signaling System Number 4.
SS5
See Signaling System Number 5.
SS6
See Signaling System Number 6.
SS7
See Signaling System 7.
SSA
In 1993, IBM, working with a committee of other major manufacturers (Conner, Western Digital, Micropolis, etc), announced an architecture, named Serial Systems Architecture (SSA). This SSA removed some of the constraints of SCSI, particularly the limitation on the attachment of storage devices. Where SCSI allows seven devices to be attached on a string, SSA attaches 127 devices on a loop. SCSI uses bulky and expensive straps where SSA employs low-cost thin cabling. Data rates are also increased from 10MB/s on SCSI to 80MB/s on SSA which is expected to increase to 160 MB/s in 1995. The use of SSA will enable faster data transfer, increase the maximum storage capacity and procedure smaller devices, all at lower costs than today's equivalents. In May of 1994, 17 companies issued a joint press release announcing their commitment to SSA. The number of companies working quietly on the development of SSA products and devices exceeds that figure. See also Fibre Channel, Firewire and SCSI.
SSAP
Source Service Access Point.
SSB
Single SideBand. See Single Sideband.
SSB-SC
Single-SideBand Suppressed Carrier.
SSCF
Service Specific Coordination Function: SSCF is a function defined in Q.2130, BISDN Signaling ATM Adaptation Layer-Service Specific Coordination Function for Support of Signaling at the User-to-Network Interface.
SSCOP
Service Specific Connection Oriented Protocol: An adaptation layer protocol defined in ITU-T Specification: Q.2110.
SSCP
-
System Services Control Point. A host based network entity in SNA that manages the network configuration, coordinates network operator and problem determination requests, maintains network address and mapping tables and provides directory support and session services.
-
Service Specific Convergence Sublayer: The portion of the convergence sublayer that is dependent upon the type of traffic that is being converted.
SSD
Shared Secret Data. A secret key defined in the ANSI-41 (formerly IS-41C) standard, the SSD is used in cellular networks. In conjunction with the A-key (Authentication key), the SSD provides an authentication mechanism for cell phone security. Both keys are encrypted through the CAVE algorithm, and both are known only to the cell phone and the AC (Authentication Center). See also A-key, AuC and CAVE.
SSH
Secure Shell (SSH) is a UNIX-based command interface and protocol for securely getting access to a remote computer. Network administrators use it to control Web and other kinds of servers remotely. SSH is a suite of three utilities ” slogin , ssh, and scp - that are secure versions of the earlier UNIX utilities, rlogin, rsh, and rcp. SSH commands are encrypted and secure in several ways. Both ends of the client/server connection are authenticated using digital certificates and passwords are protected by being encrypted. SSH uses RSA Laboratory's public key cryptography for both connection and authentication. Encryption algorithms include Blowfish, DES, and IDEA. IDEA is the default. SSH2, the latest version, is a proposed set of standards from the Internet Engineering Task Force (IETF).