Problem Areas for VoIP Security Security concerns exist whenever you have something that others consider valuable or something that others want to disrupt. If the cost of obtaining something is low relative to the value, then more than likely it needs to be secured. A thief is more likely to steal a car with the doors unlocked and the keys in the ignition than a car with the doors locked and an active car alarm system. When the security system is active, the potential risk to the thief is probably above the value of stealing the car. In a VoIP deployment, you have something of value: phone service and information. In addition, you have something that others may want to disrupt—your phone service is a business-critical application. For VoIP security, you want to identify vulnerable areas, and then make the cost to the attacker higher than the value. It is not possible to list all of the problem areas in this chapter, but broad classifications are provided so that you can think about where to look for problems. When thinking about VoIP security, it helps to begin with what you are trying to accomplish. What are you trying to avoid, prevent, protect, or secure? Here are some examples: -
You want to avoid disruptions to your VoIP phone service. -
You want to prevent unauthorized calls. -
You want to protect sensitive phone conversations and records. -
You want to secure VoIP servers and other network devices. The next area to think about is what others (attackers) are trying to accomplish. What are people after? Who might the hackers be: internal employees, corrupt administrators, external terrorists, script kiddies? Here are some examples: -
They want to disrupt your business by disrupting the IP network or causing phone outages. -
They want to obtain long-distance phone calls free (that is, at your cost). -
They want to hear confidential, proprietary, or insider information. -
They want to hack into VoIP servers to redirect calls or obtain call details. There are many different reasons why hackers do what they do. Sometimes there is a financial component. If someone can make unauthorized calls on your network, they can save money. Sometimes there is a personal aspect. A disgruntled employee or competitor may seek to damage your company through disruption of key business services. In many cases, the potential attackers could be end users, internal or external invaders, and possibly corrupt administrators. Or, as a colleague noted, some people are just sick jerks who find satisfaction in making trouble for others. The next sections present some of the potential security problem areas for a VoIP implementation. These are areas that you want to make sure to secure. Toll Fraud Financial motive can be strong incentive to hackers who are looking for free phone calls. VoIP presents unique problems, because VoIP phones operate over your IP network. Easy Access With the traditional PSTN, someone had to have physical access to a phone in your company to make phone calls. Because VoIP can make it easy to perform "action at a distance," a freeloader doesn't necessarily need to be physically present to use a VoIP phone. Where are the vulnerable points in a VoIP deployment? Consider a few of these access points: -
Network access points— Any place in your network where an IP device can plug in. Because IP phones generally use DHCP to request an IP address, consider locking down by hardware address those phones that can receive an address. -
Wireless access points— Many enterprises have wireless access points liberally available around their campus. Can IP devices roam freely onto your network through these access points? Authentication is needed to make sure only authorized users are allowed access. -
Remote access points— You may have set up remote access for your users, as more people work on the road and from home. How do your users log in to your network remotely? Is it through a virtual private network (VPN)? Do you have user authentication in place, to ensure that hackers can't get onto your network remotely? Network access needs to be secure. You want to avoid situations where someone can plug a phone into the network and make a call—with the charges going to your VoIP system. VoIP Server Configuration Arguably, the most important components in a VoIP system are the VoIP servers that handle call processing. If a hacker can get into your VoIP servers, there are several areas where toll fraud can occur: -
Account fraud can happen when someone makes calls without proper billing. In a VoIP system, call detail records (CDRs) are frequently stored in a relational database system. Often, the database system is an off-the-shelf application, with its inherent security vulnerabilities. Access to the CDRs could allow a hacker to change the billing information to gain free calls. -
Some VoIP servers have a feature that lets unknown phones download a generic configuration to get them started. You want to disable this feature for your day-to-day operations. Unauthorized access to VoIP server configuration lets a hacker enable this feature and use an unknown phone to make calls. -
An incorrectly configured call routing plan could allow the IP phone in your lobby to make international phone calls. Routing plan configurations are usually configured on the VoIP server and stored in a database. Access by a hacker can allow calls from certain locations to any other location. Softphones IP phones come in software and hardware versions. The hardware IP phones are considered by some to be more secure, because they typically run embedded operating systems. Softphones present a unique challenge, in that someone can potentially install a software phone on any computer on your data network. Now there is web server software that is integral to both IP phones and softphones. Web servers that are running with your phones offer many vulnerabilities and access points to potential hackers. You may be careful to lock down the hardware IP phones, but you must consider softphones, as well. A hacker could install a softphone on any exposed computer and obtain free calls. In addition, softphones have all the vulnerabilities associated with off-the-shelf operating systems and web servers, including exposure to viruses and worms. The financial appeal of free phone calls provides some incentive to hackers. However, there is another, bigger problem area for VoIP security: the private, confidential, and proprietary phone call information that is now traveling on your data network in a VoIP implementation. Accessing Private Information Keeping sensitive information private has long been a security issue for data networks. Web browsers use special encryption protocols to keep private the credit card numbers that you type into online order forms. Corporations use VPNs to provide secure network communications. The security issues are similar when you add voice conversations to your data network. Voice conversations now flow on the data network with your web and e-mail traffic. A VoIP system has many pieces of information that need to be protected. The conversation itself, voice mail, call activity records, and phone lists are some examples of the kinds of information you must keep private. Overhearing Conversations What if you could listen in on the CFO's conversations the week before quarterly results are announced? How about listening to your lead engineers discuss a new proprietary technology? How valuable is that information to you or your competitors? You can see that one incentive to hack into a VoIP network is to overhear conversations. A VoIP conversation is only as secure as the network that it is carried on. In a VoIP system, voice data is transferred between phones by using the RTP protocol. The RTP header of each packet has a standard format; anyone can tell how the payload is encoded by looking at RTP's Payload Type field. (See Figure 8-1.) VoIP payloads use standard codecs such as G.711 and G.729. RTP streams can be captured, reconstructed, and replayed. In fact, on the Internet, a tool known as Voice Over Misconfigured Internet Telephones (VOMIT) is available that can take a capture of an RTP stream and construct a WAV file that can be replayed on a Windows computer.[7] So, as you can imagine, you don't want people capturing your VoIP conversations and playing them back or distributing them to others. Figure 8-1. RTP Header with Payload and Sequence Information 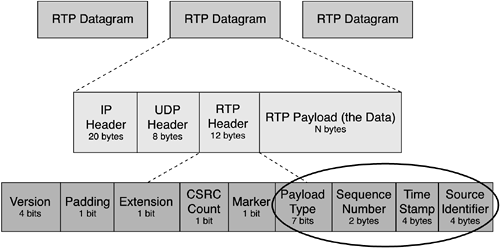
Consider this scary thought. With an analog phone system, if a hacker taps an analog line, he gets access to a single call. In a VoIP system, if a hacker taps into a data segment, he can see all the packets flowing in either direction. (See Figure 8-2.) Depending on the bandwidth of the network link, there might be dozens or hundreds of voice calls in progress at the same time. IP taps can be difficult to notice because unauthorized devices can capture packets unnoticed. When deploying VoIP, your goal is to prevent the unauthorized interception and decoding of conversations. Figure 8-2. VoIP Phone Conversations Are Easy to Reconstruct if You Can Capture the RTP Frames (Image Taken from http://www.sonicspot.com/soundwave97/soundwave97.html) 
VoIP is also vulnerable to the use of rogue servers and spoofing. If a hacker sets up a rogue VoIP server or gateway, calls could potentially be diverted and captured. In addition, a hacker could masquerade as a valid IP phone and intercept calls that were intended for the real phone. Unified messaging offers much appeal to VoIP users. The idea of accessing messages anywhere, anytime, is leading to many deployments of this feature. However, unified messaging is not without security problems. Unified messaging integrates closely with your e-mail servers. Voice mail is stored as sound files on your e-mail server and can be accessed as e-mail messages. A hacker who can break into your e-mail server can obtain not only private e-mail information, but also private voice mail information. While phone conversations are some of the most sensitive information on your network, there is call detail information in the VoIP system that is just as sensitive and should be kept private as well. Call Detail and Phone List Information CDRs are logged as calls occur. The CDRs contain information about who made calls, where they called, and how long the calls lasted. The CDRs contain information similar to what you see on a typical phone bill. In the wrong hands, this information could show competitors (for example, what customers you are calling and how often). The CDRs are stored in standard databases on VoIP servers, so they face the vulnerabilities associated with these database systems. Most IP phones contain built-in web servers for simple management services. A hacker who cracks the IP phone's web server can potentially get access to such information as recently called phone numbers and address book information. Where is your company phone list stored? Is it secure? Telemarketers love to get new phone lists to call for various solicitations. A new trend that is starting is fax spammers. After obtaining a list of fax numbers, automated faxes are sent out at an annoying rate. There is lots of private information pertaining to your phone system that you need to protect. Another problem that you must deal with is that of hackers who don't want your information but who do want to disrupt or damage your enterprise. Disrupting, Corrupting, and Doing Damage Perhaps the most disconcerting area of data network and VoIP security is the fact that there are attackers out there who want to disrupt, corrupt, or flat-out damage your organization. You see this often in the Internet, where a DoS attack is launched against certain websites. If a website provides online ordering of merchandise, and a hacker can prevent real customers from accessing the site, the site owner loses money. DoS attacks can be distributed (DDoS) in a way that many different computers over a network are participating in the attack. Denying Service Imagine the problems that may arise if a DoS attack is launched against your VoIP phone service. Phone service disruptions can have huge costs because of the business-critical nature of the phone system. In attempts to deny your phone service, an attacker usually focuses on crashing or inhibiting phones, VoIP servers, or the network—all in an attempt to create problems with availability, call setup, and call quality. A DoS attack usually consists of a flood of spurious connection attempts. The attacker sends to the server a connection request, but never responds to the acknowledgment of the request. A good example for VoIP is an attack that bombards a call-processing server with many invalid session initiation or call-setup requests. The VoIP server may become so busy trying to respond to the invalid requests that it cannot process the valid call setup requests. In the worst case, the DoS attack creates an availability outage of the service. Another common way to reduce system availability is with computer viruses or worms. Viruses take advantage of vulnerabilities in applications or operating systems. Because most VoIP servers run on off-the-shelf operating systems with off-the-shelf applications, virus writers can potentially disrupt VoIP service with a strategically placed virus. Traditional private branch exchange (PBX) systems have not had this problem because they are closed systems, so there just are not a lot of viruses out there on these systems. Call Hijacking Hijacking is generally thought of in terms of cars or airplanes, but it applies to other situations as well. Someone takes control of something and uses it for his or her purposes or redirects it to another location. In a VoIP system, a potential for hijacking calls can cause security concern. There are several ways in which this can happen: -
Rogue VoIP server or gateway— If a hacker can get access to phone configurations, calls can be redirected to rogue VoIP servers or gateways. -
Call-forwarding control— Some IP phones have vulnerabilities that allow call-forwarding settings to be manipulated remotely. A hacker could potentially use this to forward all calls to another location. In some cases, the user may not even be aware that the call was forwarded to someone else. -
Controlling a conversation— Although technically challenging, a hacker could take control of a VoIP conversation. The RTP packets that comprise the conversation each contain a sequence number. If a higher sequence number is sent to a phone during a conversation, the previous sequence numbers are discarded. A hacker could play out their own conversation on the receiving phone. -
Message integrity— How do you ensure that the message received is the same as the message sent? Redirected calls could potentially pass through a hacker's control and the packets could be altered or manipulated to control the call. Annoyances Nearly everyone has faced the telemarketers: Those annoying calls that always seem to occur when we are just sitting down for dinner. How does VoIP deal with these kinds of calls? You would like to have features such as call screening and anonymous call rejection in place to help protect your users. What about prank calls? Sometimes people make calls to have fun or joke with others. With unified messaging in VoIP implementations, voice mail is more closely tied to e-mail. Just as software developers have rushed to address the issues of e-mail spam, there will likely follow software that deals specifically with prank voice mails that may show up in your e-mail. Change Management Who can change the equipment configurations in your VoIP system? Router configurations are especially sensitive. Some routers have built-in wiretap features. If a hacker were to enable this feature, packets could be redirected to another server. What about QoS changes and policy? Someone could make changes so that he or she receives higher priority than other users during periods of high usage. Change control is especially important for VoIP servers. The installation of any applications on these critical computers should be carefully controlled. For example, installing a new application may create shared drives—which are notorious for being susceptible to virus propagation. In addition, you don't want everyone to have the ability to change private account or billing information for your phone system. |