A PRIMER ON DATA INPUT VALIDATION ATTACK CISCO HTTP EXPLOITATION
| | ||
| | ||
| | ||
A PRIMER ON DATA INPUT VALIDATION ATTACKCISCO HTTP EXPLOITATION
We have now examined numerous venues for attacking Cisco services. The never-ending quest for the precious enable continues! As with any other software, the web server supplied with many Cisco devices has a history of disclosed vulnerabilities that will allow an attacker to view or modify system settings, execute arbitrary commands with privileged user , or cause nongeneric DoS to the device. In this section, you will find the introduction to web-based configuration of Cisco devices as well as the ways of exploiting Cisco httpd services and various countermeasures to defend your devices against such attacks. Initially, we look into the simple input validation attacks that can provide a cracker with an easy-to-get control of the targeted system. Then we examine more complex methods of attacking devices in the next section.
Basics of Cisco Web Configuration Interface
The HTTP service is helpful if you prefer an easy, GUI-style configuration of Cisco devices. It is used mainly by novice system administrators who have little or no experience using CLI configuration means; however, an experienced system administrator can also use this service to allow an easy-to-visualize configuration of the device that can be demonstrated to newbies or management.
In the default router/switch configuration, the web configuration interface is disabled. Enabling and accessing the HTTP interface is quite easy. You will need to be logged in with privileged user rights and execute the following commands:
Cisco IOS based device: Router(config)# ip http server Cisco CatOS based device: set ip http server enable Catalyst(enable)
For extended features, you can change the default authentication methods (local, AAA, TACACS+), apply required access lists to disable access by unwanted parties, or enable the service over Secure Sockets Layer (SSL). Depending on your IOS/CatOS versions, some features might not be available or might require that you update the running operating system. As the scope of this book does not include the detailed configuration of various router devices and concentrates on various security issues instead, we will not get into the configuration and various features of the HTTP configuration interface. For more information on this topic, consult the Cisco web site http://www.cisco.com/en/US/products/sw/iosswrel/ps1835/products_configuration_guide_chapter09186a00800ca734.html provides details on how to set up various HTTP-based features of IOS version 12.2 and later.
Once you get the HTTP service running, fire up your web browser and go to the URL of the device by specifying its IP address or hostname.
| Note | Some devices, such as PIX firewalls, require the use of a Java plug-in that can be easily obtained from http://www.java.sun.com/ or from http://www.blackdown.org depending on your philosophy. |
Depending on the device in question, you should see something similar to Figure 7-10, provided you've supplied the right credentials when prompted.
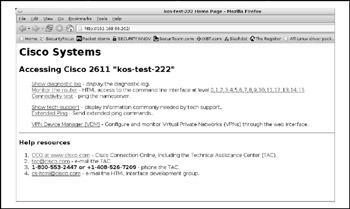
Figure 7-10: Cisco web-based management configuration
Feel free to browse the web configuration interfaceit is quite intuitive. The interface will allow you to monitor some aspects of the device and execute the majority of commands available via CLI. Once you've become familiar with the HTTP configuration interface, have a look at the methods of exploiting this service to gain access to the devices running such services.
Data Input Validation Web Interface Attack Basics
The techniques of input validation attacks have been known for years, and unfortunately due to the lack of security awareness and knowledge by coders or simply because of the laziness of some software developersthey are likely to stay with us for many years . A proper input validation should be implemented in every single piece of code that expects to receive any data (input) for processing.
Nowadays, programmers are more aware of various techniques of fiddling with the input data; however, it is still common to see these mistakes in the code over and over again. The classical example of input validation vulnerability is the famous ../../../ method used to escape the root directory of the web server and browse system files that are otherwise inaccessible to the web client.
If you are a software developer, the Open Web Application Security Project ( http://www.owasp.org ) makes the following recommendations on developing and properly implementing data input validation.
A good way to deal with parameter alteration is to make sure that all parameters are carefully checked and validated before being used by the program engine. The most common and effective way is to create a centralized validation checking library or routine that contains all required methods in one place. These methods should include a strict format that identifies all allowed values and variables being used in the program and discards the rest of the values. The common list of values that should be verified and checked are as follows :
-
Data type (string, integer, real, and so on)
-
Allowed character set
-
Minimum and maximum length
-
Whether null is allowed
-
Whether the parameter is required
-
Whether duplicates are allowed
-
Numeric range
-
Specific legal values (enumeration)
-
Specific patterns (regular expressions)
Cisco Systems HTTP server is known to have had various issues related to input validation vulnerabilities. The majority of the attacks using input validation bugs are useless if an attacker wants to obtain a privileged access, as most of such vulnerabilities will cause a DoS to the whole device or to the HTTP service.
In this chapter, we do not address the DoS attacksthis topic belongs in Chapter 11. Instead, let's take a look at the bugs in Cisco IOS that can be classified as critical input validation vulnerabilities. Some researchers might argue that these are classical bugs in the access control mechanism that are not related to the input validation. For now, let's leave these arguments behind.
Cisco IOS HTTP Administrative Access
| Attack |
|
The Cisco IOS HTTP configuration arbitrary administrative access vulnerability was disclosed to the public in the middle of 2001. Even though you might argue that this is an ancient attack, you might be surprised to find the amount of unpatched Cisco devices on the Net that can be abused using this old issue. To find out if the device in question is vulnerable, open up your favorite browser and enter the URL http://www.<deviceIPaddress>/level/<number>/ exec /show/version/cr , where <number> is an integer between 16 and 99 and <device IP address> is obviously an IP address of the Cisco device. If your system is vulnerable you will see the output similar to Figure 7-11.
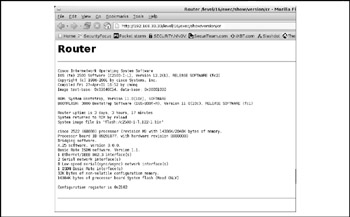
Figure 7-11: This Cisco device is vulnerable to arbitrary administrative access vulnerability.
This can be further used to extract sensitive information from the device by running a command such as this:
http://<deviceIPaddress>/level/<number>/exec/show/config/cr
This will present to an attacker the running router configuration that contains login credentials, information about other networks related to the device, and a wealth of other sensitive data.
Once the vulnerable device has been identified, the malicious actions that can be performed using this system are limited only to the hardware itself, software configuration, and the imagination of an attacker.
Countermeasures to IOS HTTP Administrative Access
| Attack | The best way of mitigating this issue is to update the vulnerable device to the latest available IOS version, which can be downloaded from the Cisco web site. |
Alternatively, limit the access to the web configuration interface to the IP addresses used by the system administrators. It is also highly advisable that you implement proper login authentication methods, such as AAA or TACACS+. In such instances, the devices using these methods are not affected by this vulnerability.
Cisco ATA-186 HTTP Device Configuration Disclosure
| Attack |
|
The Cisco ATA-186 analog telephone adapter is a hardware device designed to interface between analog telephones and Voice over IP (VoIP). The device provides the functionality of web-based configuration that is vulnerable to excessive information disclosure. The information that can be obtained from such a device includes administrative passwords and a lot of other sensitive data. The attacker who is interested in taking control of the analog telephone adapter can run the following command to obtain details:
$ curl -d a http://ata186.example.com/dev
Countermeasure to Device Configuration Disclosure
| Attack | According to the Cisco advisory, all versions prior to 020514a are vulnerable to such disclosure and should be upgraded. Download and update the new firmware version to fix this vulnerability. |
VPN Concentrator HTTP Device Information Leakage
| Attack |
|
The Cisco VPN series concentrator provides the means of secure communication by using virtual private networks. The VPN 3000 series devices with firmware versions prior to 3.5.4 are vulnerable to excessive information leakage. Under some conditions, a remote user can gain access to sensitive device information. This condition can be triggered when an erroneous page is visited by a remote client. The SSH banners provide information about the device, including the SSH version numbers . The FTP banners leak information about the device and its local time, whereas the incorrect HTTP page requests reveal further details about the device, including the name of the person who compiled the software and the compilation date. This could lead to intelligence gathering and leverage a directed attack against network resources by a malicious user.
Countermeasure to Information Leakage
| Attack | Cisco has released firmware fixes that solve the excessive information leakage. For Cisco VPN 3002 Hardware Client, this issue is addressed in versions 3.5.5 and 3.6.1 of the firmware. |
| | ||
| | ||
| | ||
EAN: 2147483647
Pages: 117