Summary
This chapter has fully detailed the necessary components required to process inject application memory. To keep the code as simple as possible, only bare minimum functionality has been implemented. A complete PGP monitor would need to include patterns for every possible version of the PGP SDK DLL as well as an additional hook for every version of the Self Decrypting Archive function found in the PGP SC DLL, and yet another hook for multi-file encryption using PGP version 9. Fortunately, with the tools provided, and a good understanding of IDA, this additional functionality can be added quickly. Figure 4-4 shows a complete PGP monitor.
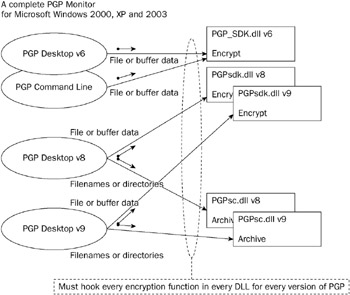
Figure 4-4
We now have a rootkit that does all of the following:
-
Hides its device driver entry
-
Hides its configuration file
-
Hooks the operating system kernel
-
Hooks selected processes loaded by the operating system
We’re getting close to a functional rootkit. Of course, we still can’t talk to the rootkit from a local application or control the rootkit from a remote application. We’ll need to understand the basic I/O system before we jump into these forms of communication. The next chapter introduces this crucial rootkit component: I/O processing.
EAN: 2147483647
Pages: 229