A Walkthrough of How NAP Works
Now that we understand a bit about NAP enforcement mechanisms and the architecture of the NAP platform, let’s walk through an example of NAP at work. Figure 10-2 shows a VPN NAP scenario that we’re going to analyze. (Other NAP scenarios such as DHCP and IPSec work a bit differently.) We’ll leave out a few elements, like Active Directory for performing authentication, so that we don’t complicate things too much, and some of the interactions between the different components are simplified. If you want a more detailed explanation of how NAP works, you can always look at some of the references listed under “Additional Resources” at the end of this chapter.
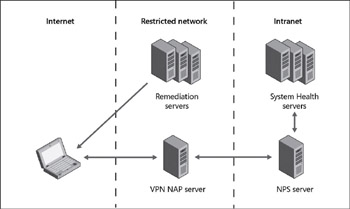
Figure 10-2: A VPN scenario showing NAP at work
Here’s a simplified description of what happens when a noncompliant laptop running Windows Vista tries to VPN into corpnet by connecting to a VPN server running Windows Server 2008 when a NAP infrastructure has been deployed:
-
The VPN client uses PEAP to try and establish an authenticated connection with the VPN server. Keep in mind that the VPN client is a NAP client and the VPN server is a NAP server in this scenario.
-
The VPN server, which is also a NAP server, relays the health status information provided by the client to the NPS. What’s happening under the hood is that each SHA running on the client performs a system health policy check to determine whether the client is healthy (with respect to the function being performed by the SHA-firewall on, AV enabled, and so on). The result of each check is a data blob, called a Statement of Health (SoH), that indicates compliance or noncompliance with policy. The QA caches these SoHs and consolidates them into a list. The QA then waits for an EC to request this health status information.
-
When the VPN client tries to connect to the VPN server, the server notifies the client that it needs information concerning the client’s health status before it will let the client into the corporate intranet. The way it works is that the ES component on the NAP server (the VPN server) communicates using PEAP with the EC component on the NAP client and requests the SoH information from the client.
-
Once the client has sent this SoH information to the NAP server, the NAP server then uses the RADIUS protocol to communicate with the NPS. Specifically, what’s happening here is that the SoH information (along with the other non-NAP user authentication stuff) is being sent from the SHAs on the client (where it was collected) to the corresponding SHVs on the NPS (where it is analyzed against the policy information obtained from the System Health Servers).
-
One of the SHVs on the NPS now determines that the client is noncompliant (for example, Windows Firewall is turned off on the machine). Each SHV produces a Statement of Health Response (SoHR) in response to its compliance analysis of the SoH information it received from the corresponding SHA. The QS uses these SoHRs to construct a System Statement of Health Response (SSoHR), which indicates that the noncompliant client should be denied network access until remediated. The QS then uses RADIUS to send this information from the NPS back to the NAP server.
-
The VPN (NAP) server now applies a set of packet filters to the client to quarantine the client. The client has now been authenticated but can access only the resources on the restricted network, which basically means the VPN server and the remediation servers. The NAP server passes the SoHRs to the NAP client, and the SHAs on the client perform their designated remediation actions (assuming auto-remediation is enabled). The result might then be that the client’s firewall is turned on, the client downloads the latest AV sig, or some other remediation action or actions are performed.
-
Once the SHAs on the client have determined that the client is now compliant, an updated list of SoHs is sent by the client to the NAP server and forwarded to the NPS to verify compliance. The procedure repeats as described here, only this time the VPN server recognizes that the client is now healthy, so it removes the restrictive filters from the client and allows it free access to the intranet.
EAN: 2147483647
Pages: 138