Example 6: Flush Request
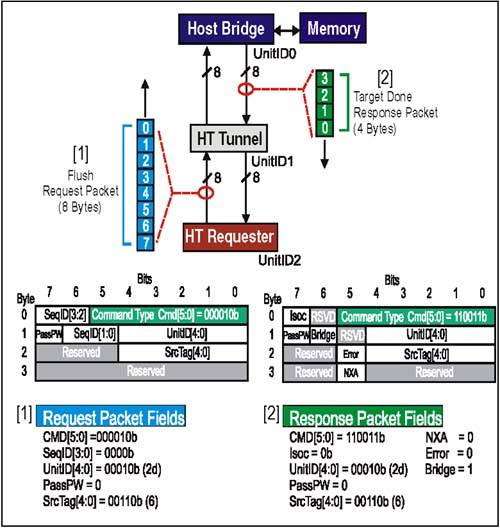
Example 6:Flush RequestProblem: Device 2 (UnitID2) in Figure 7-8 on page 174, issues a Flush request which causes all previous posted writes in the same transaction stream (sourced by UnitID2) to be forced to host memory. Figure 7-8. A Flush Request Issued By UnitID 2 Example 6:Flush Request Packet Setup(Refer to [1] in Figure 7-8 on page 174) Command[5:0] Field (Byte 0, Bit 5:0)This is the Flush request command code. There are no option bits. For this example, field = 000010b. SeqID[3:0] Field (Byte 0, Bit 7:6) and (Byte 1, Bit 6:5)This field is used to tag groups of requests that were issued as part of an ordered sequence. Flush requests are never part of an ordered sequence, so this bit should be cleared. Setting SeqID[3:0] to a non-zero value may have indeterminate results. For this example, field = 0000b. UnitID[4:0] Field (Byte 1, Bits 4:0)For both upstream and downstream requests, this field is programmed with the UnitID of the requester. UnitID is assigned during initialization by configuration software. In this example, the request originates at Device 2 (UnitID2). For this example, field = 00010b. PassPW Bit Field (Byte 1, Bit 7)This bit is cleared in a Flush request so that the request will perform its intended function: pushing earlier posted writes ahead of it. Setting this bit = 1 may have indeterminate results. For this example, field = 0b. Example 6:Flush Request, Sequence Of Events(Refer to Figure 7-8 on page 174)
Example 6: Flush Response Packet Setup(Refer to [2] in Figure 7-8 on page 174) When the Host Bridge has completed the Flush to memory (or downstream for peer-to-peer traffic) it prepares to return a Target Done response to the original requester (UnitID2). The purpose of the response is to inform the requester the operation is done and that it may take any action that may have been pending its completion. Command[5:0] Field (Byte 0, Bit 5:0)This is the command code for the Target Done Response. There are no option bits in this field. For this example, field = 110011b. UnitID[4:0] Field (Byte 1, Bits 4:0)Because this response is being issued by a Host Bridge and traveling downstream, the UnitID field carries the identity of the original requester (UnitID2). For this example, field = 00010b. Bridge Bit Field (Byte 1, Bit 6)Set by host bridges in responses they issue downstream (as in this example) so devices may distinguish upstream and downstream responses. For this example, field = 1b. PassPW Bit Field (Byte 1, Bit 7)This bit indicates whether this packet may pass packets in the posted request channel (for same transaction stream). This bit should be clear in Flush request and the subsequent Target Done response. For this example, field = 0b. SrcTag[4:0] Field (Byte 2, Bits 4:0)The field is set to the same value as seen in the Flush request. In our example, the Source Tag was 6. For this example, field = 00110b. Error Bit Field (Byte 2, Bit 5)In a read transaction, this bit in the response is set to indicate an error was encountered in obtaining requested data. In this example, there were no errors. See Chapter 10, entitled "Error Detection And Handling," on page 229 for a discussion of how response errors are handled in HyperTransport. For this example, field = 0b. NXA Bit Field (Byte 3, Bit 5)This response bit is only valid if the Error bit (Byte 2, Bit 5) is set. IF NXA and Error are both set, the original Flush request did not find the proper target at all, and the Target Done response is being returned by a device at the end of the chain. For this example, field = 0b. Example 6: Flush Response, Sequence Of Events(Refer to Figure 7-8 on page 174)
A Few Notes About Flush Operations
|
EAN: 2147483647
Pages: 182