Lesson 1:Overview of Secure Sockets Layer (SSL)
|
| < Day Day Up > |
|
SSL was developed by Netscape Communications Corporation in 1994 to secure transactions over the World Wide Web. Soon after, the Internet Engineering Task Force (IETF) began work to develop a standard protocol to provide the same functionality. SSL 3.0 was used as the basis for that work, which is known as the Transport Layer Security (TLS) protocol. The implementation of the SSL/TLS protocol in Windows Server 2003 closely follows the specification defined in RFC 2246, “The TLS Protocol Version 1.0.”
SSL is widely used because it provides strong authentication, message privacy, and data integrity. Unlike other proprietary techniques for improving communication security, SSL is an open standard that is widely deployed and supported by a variety of servers and clients. As a result of the wide adoption, the security community has carefully examined the SSL standards and popular SSL implementations. This close examination, combined with the relative maturity of the SSL standards, has resulted in a highly secure method for authenticating clients and servers and protecting the privacy of communications.
After this lesson, you will be able to
-
Describe how an SSL session is established.
-
Identify scenarios in which SSL should be used.
-
Understand the differences between IP Security (IPSec) and SSL.
-
List the changes required to allow SSL-protected communications through a firewall.
Estimated lesson time: 25 minutes
How SSL Works
SSL provides encryption, authentication, and data integrity by using a public key certificate. When the SSL session is established, the server’s public key certificate is used to encrypt and exchange a shared secret between the client and server. This shared secret is then used to encrypt communications for the rest of the session. The following describes the step-by-step procedures for establishing an SSL session:
-
The client requests the public key from the server.
-
The server sends the public key to the client.
-
The client sends the server a session key, encrypting it with the public key.
-
The server decrypts the session key received from the client by using the server’s private key.
The session key can then be used as a shared secret to encrypt and decrypt data exchanged between the client and server.
| Exam Tip | Remember that SSL uses both public key encryption and shared key encryption. Public keys are used for authentication and to transmit the shared key. The shared key is then used to encrypt the data, because encrypting and decrypting data with a shared key uses less processing time than public key encryption. |
Comparing SSL with IPSec
IPSec is commonly used to provide the same services as SSL: authentication, privacy, and message integrity. However, the approach IPSec takes is different from that of SSL. IPSec is implemented by the operating system and is completely transparent to the applications that use IPSec. As a result, IPSec can be used to protect almost any type of network communication. IPSec also provides a flexible authentication scheme. The Microsoft Windows implementation of IPSec allows clients and servers to authenticate each other by using either public key certificates or a shared secret.
SSL, on the other hand, must be implemented by individual applications. Therefore, you cannot use SSL to encrypt all communications between two hosts. Additionally, SSL is less flexible than IPSec because it only supports authentication by means of public key certificates. SSL does provide several distinct advantages, however. Most significantly, SSL is supported by a wide variety of servers and clients, and the maturity of the standard has practically eliminated interoperability problems.
Additionally, SSL allows one-way authentication, while IPSec requires both sides of a connection to authenticate. One-way authentication allows SSL to be used to authenticate the server without placing the burden of registering for a public key certificate on the client. This enables SSL to be used to encrypt communications with public Web sites while protecting the privacy of the end user by not revealing the details of a user certificate to the Web server. Table 11.1 summarizes the differences between SSL and IPSec.
| IPSec | SSL |
|---|---|
| Requires authentication for both the client and the server | Requires either the client or the server, or both, to be authenticated |
| Authenticates by using either public key certificates or a shared secret | Requires public key certificate–based authentication |
| Can be used to authenticate and encrypt communications for any application | Can be used only to authenticate and encrypt communications for applications that specifically support SSL |
| Is capable of tunneling communications between entire networks | Can be used only to encrypt traffic between two hosts |
| Is a relatively new technology that is not yet widely adopted | Is a mature technology that is widely adopted |
| Used primarily for intranet communications | Used primarily for Internet communications |
Obtaining SSL Certificates
To use SSL, the server must have a suitable public key certificate. Additionally, some SSL scenarios allow or require the client to use a public key certificate. SSL is one of the most common uses for public key certificates, and, as a result, you can obtain SSL certificates from a wide variety of places.
Any organization with a computer running Windows Server 2003 can deploy Certificate Services to issue SSL certificates without any additional cost. These certificates are suitable for intranet scenarios, in which both the servers and the clients are controlled by a single organization. These certificates should not be used for communications that cross organizations, however.
As with any public key infrastructure (PKI), SSL certificates can only be trusted if the root certification authority (CA) is trusted. You can use Group Policy objects (GPOs) to add your CA to the list of trusted root CAs on clients on an intranet, but it is much more difficult to configure clients on the public Internet. For this reason, if you do not control the client computers, you should obtain an SSL certificate from a public CA that is trusted by the client applications that will be establishing a connection to your server. If the server is a Web server, your clients will be Web browsers. As shown in Figure 11.1, Microsoft Internet Explorer is configured by default to trust a large number of public CAs.
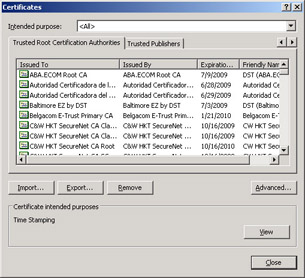
Figure 11.1: Internet Explorer’s trusted root CAs
| Exam Tip | Some CAs, including Verisign, offer free certificates for testing purposes. These certificates are generally not issued by the CA’s trusted root certificate and, as a result, will not be automatically trusted by client browsers. However, these testing certificates are a perfect way to gain experience with publicly issued certificates to prepare for the exam. |
If the client does not trust the CA that issued your certificate, the client will usually show a warning to the end user, as shown in Figure 11.2. This warning does not prevent the user from establishing an SSL-encrypted session with your server. However, the warning might cause the user to cancel the connection. Although establishing a connection to a server with an untrusted CA still provides encryption and message integrity, using an SSL certificate issued by an untrusted CA defeats the purpose of the authentication provided by SSL.
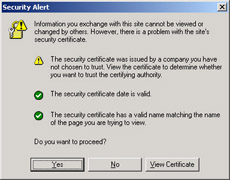
Figure 11.2: Internet Explorer warning regarding an untrusted CA
| Planning | If you decide to use public certificates for SSL, take some time to choose your CA carefully. The prices charged for certificates vary widely, from free to several thousands of dollars. More expensive CAs offer warranties providing coverage in the event that your certificate is cracked, seals that you can display on your Web site, certificate management services, and security services. Additionally, you should be sure that the CA will continue to actively pursue being trusted by common Web browsers. If you are curious about what a CA needs to go through to become trusted, read about the WebTrust for Certification Authorities program sponsored by The American Institute for Certified Public Accountants (AICPA) at http://www.webtrust.org/certauth.htm. |
Renewing SSL Certificates
Like any other public key certificate, each SSL certificate has a lifetime. At some point in the future, the certificate will expire. You should plan to renew the certificate three to six months prior to the expiration to ensure that there is no period during which the certificate is invalid.
The specific process you use for renewing the certificate will vary. If you are using a certificate issued by a public CA, the CA will provide a renewal process. If you are using a certificate issued by Certificate Services, you can renew the certificate by using Web enrollment, the Certificates snap-in, or the Web Server Certificate Wizard. The Web Server Certificate Wizard is described in Lesson 2.
| See Also | For more information about Web enrollment and the Certificates snap-in, refer to Chapter 7. |
Configuring Firewalls
Applications use a unique port number for SSL-protected communications. As a result, you must change your firewall configuration to allow the encrypted traffic.
There are two approaches to allowing SSL traffic through a firewall. The first approach is to open the firewall to allow all traffic with a designated port. The typical ports that various applications use for SSL are listed in Table 11.2. Although this will allow SSL sessions to be established through the firewall, the firewall will not be able to analyze the contents of the SSL-encrypted packets. As a result, the firewall will be able to use only the origin and destination of the packet to determine whether to let packets through.
| Protocol | Standard port | SSL port |
|---|---|---|
| Hypertext Transfer Protocol (HTTP) | 80 | 443 |
| Simple Mail Transfer Protocol (SMTP) | 25 | 465 |
| Post Office Protocol version 3 (POP3) | 110 | 995 |
| Internet Message Access Protocol (IMAP) | 143 | 993 |
| Network News Transfer Protocol (NNTP) | 119 | 563 |
| Lightweight Directory Access Protocol (LDAP) | 389 | 636 |
| Global catalog queries | 3268 | 3269 |
The second approach is to configure the firewall as a proxy server. In this case, the client actually establishes an SSL session with the firewall. The firewall, in turn, establishes an SSL session with the destination server. Although the client must trust the firewall to perform authentication and to protect the privacy of the communication, this is the only way to use SSL for encryption while allowing the firewall to examine the contents of the communications.
Lesson Review
The following questions are intended to reinforce key information presented in this lesson. If you are unable to answer a question, review the lesson materials and try the question again. You can find answers to the questions in the “Questions and Answers” section at the end of this chapter.
-
Which of the following is an advantage that SSL has over IPSec?
-
It can use a shared secret for authentication.
-
It can tunnel traffic between two networks.
-
It does not require the client to be authenticated.
-
It is transparent to the application.
-
-
Which of the following is an advantage of using an SSL certificate issued by a public CA?
-
You can use the certificate for free.
-
Browsers will trust the CA by default and will not warn the user.
-
It takes less time to obtain a certificate from a public CA.
-
You do not have to reveal personal information to the CA.
-
-
Which port should you open on a firewall to allow HTTP traffic protected by SSL?
-
80
-
110
-
443
-
995
-
-
Which port will you open on a firewall to allow POP3 traffic protected by SSL?
-
80
-
110
-
443
-
995
-
Lesson Summary
-
Applications can use SSL to provide authentication, data integrity, and encryption for network communications.
-
When an SSL session is established, the client retrieves the server’s public key and uses it to encrypt a shared secret. The shared secret is then used to encrypt the rest of the session.
-
SSL and IPSec provide similar functionality. However, SSL is more commonly used on the Internet because it does not require the client to have a public key certificate.
-
You can obtain SSL certificates from public CAs or issue them yourself by using Windows Server 2003 Certificate Services.
-
When SSL is used to protect a session, the communications use a different TCP port number. You will have to reconfigure your firewall to allow traffic on the different port number.
|
| < Day Day Up > |
|
EAN: 2147483647
Pages: 217