Virtual Private Networks
| |
Although the Internet can't quite do our laundry yet (or even cook a decent meal for that matter), it has changed the way we are able to transact business. One of its latest offerings for organizations that are motivated to reduce costs and increase services is the Virtual Private Network, or VPN.
In a nutshell , a VPN is a private connection between two machines or networks over a shared or public network. In practical terms, VPN technology lets an organization securely extend its network services over the Internet to remote users, branch offices, and partner companies. In other words, VPNs turn the Internet into a simulated private WAN.
The appeal is that the Internet has a global presence, and its use is now standard practice for most users and organizations. Thus, creating a communications link can be done quickly, cheaply, and safely.
How It Works
To use the Internet as a private wide area network, organizations may have to overcome two main hurdles. First, networks often communicate using a variety of protocols, such as IPX and NetBEUI, but the Internet can only handle IP traffic. So, VPNs may need to provide a way to pass non-IP protocols from one network to another.
Second, data packets traveling the Internet are transported in clear text. Consequently, anyone who can see Internet traffic can also read the data contained in the packets. This is clearly a problem if companies want to use the Internet to pass important, confidential business information.
VPNs overcome these obstacles by using a strategy called tunneling. Instead of packets crossing the Internet out in the open , data packets are first encrypted for security, and then encapsulated in an IP package by the VPN and tunneled through the Internet (see Figure).
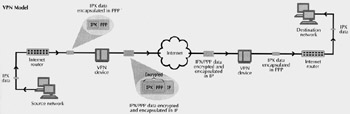
How Tunneling Works: When a VPN device receives instructions to transmit a packet over the Internet, it negotiates encryption with the VPN device on the destination network, then encrypts the packet accordingly . Next, it encapsulates the encrypted packet in an IP packet and sends it over the Internet to the destination network. Once the packet arrives, the receiving VPN termination device reverses the process and lets the packet continue to its destination on the internal network.
To illustrate the concept, let's say you're running NetWare on one network, and a client on that network wants to connect to a remote NetWare server.
The primary protocol used with traditional NetWare is IPX. So, to use a generic layer-2 VPN model, IPX packets bound for the remote network reach a tunnel initiating deviceperhaps a remote access device, a router, or even a desktop PC, in the case of remote-client-to-server connectionswhich prepares them for transmission over the Internet.
The VPN tunnel initiator on the source network communicates with a VPN tunnel terminator on the destination network. The two agree upon an encryption scheme, and the tunnel initiator encrypts the packet for security. (For better security, there should be an authentication process to ensure that the connecting user has the proper rights to enter the destination network. Most currently available VPN products support multiple forms of authentication.)
Finally, the VPN initiator encapsulates the entire encrypted package in an IP packet. Now, regardless of the type of protocol originally being transmitted, it can travel the IP-only Internet. And, because the packet is encrypted, no one can read the original data.
On the destination end, the VPN tunnel terminator receives the packet and removes the IP information. It then decrypts the packet according to the agreed upon encryption scheme, and sends the resulting packet to the remote access server or local router, which passes the hidden IPX packet to the network for delivery to the appropriate destination.
The Methods
Currently, there are a handful of VPN protocols rising to the surface in the industrynamely L2TP, IPsec, and SOCKS 5. Because they provide tunneling functions, these protocols are the building blocks used to create VPN links. Some of the protocols overlap in functionality, and some offer similar but complementary functionality. Each of the protocols requires further investigation when shopping for a solution. In the meantime, here's a quick summary of the protocols.
Also known as the Layer-2 Tunneling Protocol, L2TP is the combination of Cisco Systems' Layer-2 Forwarding (L2F) and Microsoft's Point-to-Point Tunneling Protocol (PPTP). L2TP supports any routed protocol, including IP, IPX, and AppleTalk. It also supports any WAN backbone technology, including frame relay, ATM, X.25, and SONET.
One key to L2TP is its use of PPTP. This Microsoft protocol is an extension of PPP and is included as part of the remote access features of Windows 95, Windows 98, and Windows NT. So, in the big picture, most PC clients come equipped with tunneling functionality. PPTP provides a consistent way to encapsulate Network-layer traffic for remote access transmission between Windows clients and servers. The protocol doesn't specify a particular encryption scheme, but the remote access functions included in the Microsoft stable of operating systems are supplied with Microsoft Point-to-Point Encryption (MPPE).
The L2F portion of L2TP lets remote clients connect and authenticate to networks over ISP and NSP links. Besides the basic VPN capability, L2TP can create multiple tunnels from a single client. In practice, a remote client can create tunneled connections to various systems simultaneously for instance, to a corporate database application and to the company's intranet.
As for IPsec, the full name for it is Internet Protocol Security, and it's basically a suite of protocols that provide security features for IP VPNs. As a layer-3 function, IPsec can't perform services for other layer-3 protocols, such as IPX and SNA. IPsec provides a means of ensuring the confidentiality and authenticity of IP packets. The protocol works with a variety of standard encryption schemes and encryption negotiation processes, as well as with various security systems, including digital signatures, digital certificates, public key infrastructures , and certificate authorities.
IPsec works by encapsulating the original IP data packet into a new IP packet that's fitted with authentication and security headers. The headers contain the information needed by the remote end, which took part in the security negotiation process to authenticate and decrypt the data contained in the packet.
The appeal of IPsec is its interoperability. It doesn't specify a proprietary way to perform authentication and encryption. Instead, it works with many systems and standards. IPsec can complement other VPN protocols. For instance, IPsec can perform the encryption negotiation and authentication, while an L2TP VPN receives the internal data packet, initiates the tunnel, and passes the encapsulated packet to the other VPN end point.
Another approach to VPNs is SOCKS 5, which was first developed by Aventail. SOCKS 5 is a bit different from L2TP and IPsec: It follows a proxy server model and works at the TCP socket level. To use SOCKS 5, systems must be outfitted with SOCKS 5 client software. Furthermore, your organization needs to be running a SOCKS 5 server.
Here's how the SOCKS 5 model works. First, a client request for services is intercepted by the SOCKS 5 client. The request is sent to the SOCKS 5 server, which checks the request against a security database. If the request is granted, the SOCKS 5 server establishes an authenticated session with the client and acts as a proxy for the client, performing the requested operations.
The upside to SOCKS 5 is that it lets network managers apply specific controls on proxied traffic. Because it works at the TCP level, SOCKS 5 lets you specify which applications can cross the firewall into the Internet, and which are restricted.
Why It's Appealing
VPN vendors can recite a litany of benefits that the technology provides, and more will emerge as VPN products mature.
Perhaps the biggest selling point for VPNs is cost savings. If you use the Internet to distribute network services over long distances, then you avoid having to purchase expensive leased lines to branch offices or partner companies. And, you escape having to pay for long distance charges on dial-up modem or ISDN calls between distant sites. Instead, users and systems simply connect locally to their ISP and leave the rest of the journey to the vast reach of the Internet. On another cost- related note, you can evade having to invest in additional WAN equipment and instead leverage your existing Internet installation.
Another benefit of VPNs is that they are an ideal way to handle mobile users. VPNs allow any user with Internet access and a VPN client to connect to the corporate network and to receive network services. Since Internet access is now widespread, you won't have to juggle users and locations when setting up remote, mobile access.
In the same vein, because Internet use is commonplace, you can deploy a network-to-network arrangement quickly and cheaply. There's no need to order and configure data lines and WAN interfaces for each site. Again, you just leverage each site's Internet connection to form the link. This is especially advantageous in the current business environment, where partner companies are connecting networks to improve the speed and efficiency of shared business operations.
This tutorial, number 123, by Lee Chae, was originally published in the October 1998 issue of Network Magazine.
| |
EAN: 2147483647
Pages: 193