The Rationale
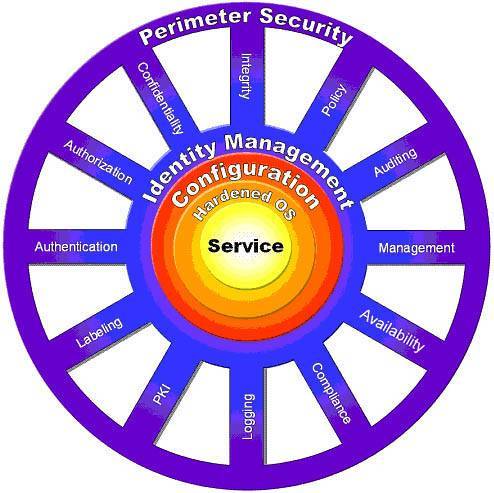
| An application or service may consist of a single functional component or multiple sets of disparate components that reside locally or over a network. Security is often considered as a complex process, encompassing a chain of features and tasks related to computer system security, network security, application-level security, authentication services, data confidentiality, personal privacy issues, cryptography, and so forth. More importantly, these features must be designed and verified independently and then made to work together across the system. Applying a security feature often represents a unique function that can be a safeguard or a countermeasure, which guarantees the application or service by preventing or reducing the impact of a particular threat or vulnerability and the likelihood of its reoccurrence. The Security WheelSecurity is represented as a set of features that fortifies the entire application or service with safeguards and countermeasures for potential risks and vulnerabilities. Each security feature is like a spoke in a wheel. This means that each functional component in the entire system must be secured or the wheel will not have structural integrity and may well break apart. In order to accomplish this, a methodical process must be put in place to ensure that security is addressed properly and integrated across all of these varying components. From the user who is accessing the application or service over the network to the routers and firewalls on the perimeter of the system and then up through the application or service and the OS on which it residesa security design must identify the risks and address the safeguards and countermeasures of the system holistically. Incorporating fundamental security principles plays a vital role during the software design and architecture, and it also helps identifying and eliminating the risks and threats in the early phases of the software development cycle. The concept of a Security Wheel provides the basis for verifying the fundamental security principles mandated for securing an application or service. Figure 8-1 illustrates the Security Wheel, which represents all of the fundamental principles of security. Figure 8-1. Security Wheel representing the fundamental security principles The Security Wheel is a logical representation of the fundamental security principles required for establishing Security by Default in an application or a service. It provides guidelines that need to be taken into consideration during the entire software development life-cycle, and it can be applied across all or selected components of an application or a service. The HubAt the core of the hub of the Security Wheel sits the service or application that you are building. In this representation, it refers more to the business logic than the application as a whole. The service resides in a secured server host with minimized and hardened OS. (OS Minimization refers to fewer software components on a server infrastructure, and Hardened OS refers to a reconfigured OS that applies security measures specified by the OS vendor and retains no non-essential programs, protocols, or services.) The secured host includes storage devices and accessories. Both the service and the target host environment must be configured and deployed through a secure configuration management and reliable provisioning mechanisms. The service makes use of a common identity management solution that provides repository and supporting mechanisms for verifying an entity and its associated credentials, for logging, and for reporting all activities. The SpokesThe spokes represent the following 12 core security services applicable to an application or a service.
The above-mentioned security services are the guiding security principles for providing a robust security architecture. Applications or services can be reviewed with these security measures during their design phases or at appropriate phases prior to deployment. The Wheel EdgeThe wheel edge represents the perimeter security: the network security components such as routers, firewalls, packet-filtering appliances, intrusion detection systems (IDS), crypto accelerators, and other devices that sit between the Internet and your network. They make up the solution for protecting the network perimeter from connection attacks based on IP addresses, TCP ports, protocols, and packet filters. Across the service and OS and all the way to the perimeter security, every security principle must be addressed as a service that contributes to the overall security architecture. In some cases, many of these security principles, represented as spokes in the wheel, are only applicable to a few components of the overall application or a service. Nevertheless, each component within the system must be examined to determine the associated risks and trade-offs. Adopting a structured security methodology helps to ensure that all security principles are addressed and captured during the software development life cycle or prior to production. |
EAN: 2147483647
Pages: 204