History and Versions
| | ||
| | ||
| | ||
Microsoft Windows traces its history back to a prior command linebased operating system, MS-DOS. Founded in 1975, Microsoft Corporation built several BASIC language interpreters for personal computer kits available at the time. After gaining some prominence in the PC marketplace , Microsoft purchased the rights to an operating system that became MS-DOS in 1981.
MS-DOS
MS-DOS provided a small footprint operating system that became the de-facto standard for IBM-compatible personal computers. Offered as part of the original IBM PC, the MS-DOS operating system became the baseline for business applications and home applications. MS-DOS was non-graphical and used the FAT file system exclusively. Mice were not part of a standard PC offered at the time, and the original versions did not support hard disks. As a result, forensics was a bit easier, although the tools were not as robust; the entire contents of an evidence floppy, all 360K of it, could be printed out and reviewed manually.
A few third-party Graphical User Interfaces (GUIs) were made available for MS-DOS, but they were released with limited success, largely because color monitors with capable graphics card were not broadly available, and mice were just beginning to appear on standard PCs. In 1985, Microsoft released a graphical shell for MS-DOS titled Windows 1.0.
Windows 1.x, 2.x, and 3.x
The initial public and corporate reaction to both Windows 1.0 and its successors, Windows 2.0 (released in 1987) and Windows 3.0 (released in 1991), was lukewarm at best. By the end of 1991, MS-DOS was still the predominate client operating system, and both Unix and Netware servers had a dominant place in the newly emerging corporate microcomputer server market.
In an effort to improve previous versions and broaden its appeal , Microsoft released two products in the 19921993 timeframe. They were tremendously successful. In the home market, Windows 3.1 sold millions of copies and included hundreds of enhancements in graphics, usability, and functionality. Sales were likewise increased by the release of Microsoft Office and Microsoft Works products for home users, and the new, easy-to-use Microsoft Visual Basic programming environment expanded the number of developers exponentially almost overnight.
| Note | Visual Basic built upon the BASIC language, the predominant language taught in schools at the time. As a result, Microsoft released its development tools to a pre-trained audience. The easy-to-use integrated development environment (IDE) likewise made Visual Basic more accessible to non programmers and new programmers, creating a plethora of new programs available and a resulting synergy in popularity. |
In the business world, the counterpart to Windows 3.1 was Windows for Workgroups 3.11 (WFW 3.11). Enabling remote access, networking, and collaboration, WFW 3.11 became an instant hit in the corporate workplace. At the same time, the introduction of a new Microsoft mouse and the incorporation of the product into most of the major OEM vendors to corporations ensured its continued success.
Windows 3.1 and WFW 3.11 are the oldest Windows products a forensic examiner is likely to encounter. Both products are now well beyond their support expiration, but a few point machines running legacy software still exist with each of these installed. From a forensic examination standpoint, Windows 3. x systems are MS-DOS systems with a GUI on top of them. File system support was for FAT, and any of the analyses mentioned later that are related to FAT drives are applicable . The introduction of virtual memory is also of note. Windows 3. x used a hidden file called 386SPART.PAR, which was an early virtual memory file. This file should be analyzed the same way as the swap files listed for later versions of Windows.
Following the success of Windows 3. x , Microsoft branched off its operating systems in two separate directions. The corporate environment had a new operating system built from the ground up given the moniker Windows NT (for New Technology) that would compete for both the server and workstation markets. The home environment had its own new release, Windows 95, which remained backward compatible with the older versions on Windows and DOS but had a substantially new look and feel built on an updated architecture.
Windows NT and 2000
Windows NT 3.51 and 4.0 proved to be more stable and secure than previous versions of Windows. Both made strong headway into the corporate environment, frequently replacing Netware and other systems on the server with its ease-of-use, and replacing WFW 3.11 on the desktop with increased stability, performance, and security. For the computer investigator , Windows NT introduced the new file system, which has since become the most prevalent : NTFS. A major improvement on the FAT file system, NTFS lessened the amount of slack space available on large drives but increased the ability to recover damaged drives through the use of file systems mirroring. Additions to NTFS such as Alternate Data Streams, file compression, and the new Recycling Bin formats required additional effort in a forensic analysis. For the examiner, negligible differences exist in the architectures of the server and workstations products, although analysis might differ greatly based on the type of investigation. Support for Windows NT 4.0 is now terminated with the exception of those with custom support contracts, but many corporate environments still have a large installed base of NT machines.
Following the success of Windows NT, the corporate line of products was renamed Windows 2000 and released as the upgrade path for Windows NT 4.0 in both the server and workstation markets. Windows 2000 provided even more stability and better performance on both the desktop and server environments, offering support for larger server deployments as well as a robust management of users through Active Directory, Microsoft's LDAP effort.
Windows 2000 introduced the Encrypting File System (EFS), presenting a new challenge for the computer investigator. Now entire drives could be encrypted with a few mouse clicks, and key escrow became an important consideration in corporate forensics. At the time of this writing, Windows 2000 is the predominant Windows server in operation but has been surpassed by Windows XP in popularity on the desktop.
At the same time Windows NT and 2000 were released for the corporate market, Windows 95, 95 OSR2, 98, 98SE, and ME were released for the home market. Starting with Windows 95, Microsoft revamped the Windows 3. x look and feel as well as the underlying architecture. Because backward compatibility remained a major consideration, remnants of the legacy DOS architecture existed on the home environment for a longer period than in the corporate space.
Windows 95, 98, and ME
Windows 95 was replaced in popularity by Windows 98, a cosmetic and functionality-based update. Interim OSR2 (for Windows 95) and SE (for Windows 98) editions offered mid-stream updates to networking functionality, security, and feature sets. Windows ME (Millennium Edition) introduced several enhancements to user-friendliness but never supplanted previous versions in market share.
Windows 9 x never integrated full support for the NTFS file system. As a result, permissions, compression, encryption, and other options were primarily limited to third-party products. Long file names and other additions to the original FAT specifications were included as part of FAT32, as were file recovery (Recycling Bin), networking, and registry features.
Although Windows 98 does exist in some corporate environments, it is still a predominantly personal-use operating system. The popularity of Windows 9 x has been diminishing with the increased push for security and stability in the home environment. There is still a reasonable likelihood of encountering Windows 9 x machines in a forensic investigation, although their usage will continue to decline rapidly as support wanes and users transition to newer operating systems.
Windows XP and 2003
In an effort to improve the security and stability of its home market while offering a competitive update for corporate users, Microsoft released Windows XP as its new client operating system. XP brought the previous features present in the Windows NT/2000 operating systems and the associated NTFS file system to the home market and introduced new usability features to the corporate market.
Windows XP SP2, the second service pack for the product, introduced further enhancements to the XP environment on security. The addition of an improved client firewall and integrated security management center increased the security of home machines and presented new challenges for the computer investigator (for example, the use of servlets and other remote analysis tools).
| Note | Although Microsoft dominates the personal computer market, embedded operating systems present on Programmable Logic Controllers (PLCs) and cell phones have more overall installations. |
Windows XP is the predominant operating system in use globally (see Figure 3-1 for prevalence information). It has the largest market share of any personal computer operating system. With the next Windows version not expected until late 2006 (Windows Vista, formerly named Longhorn), XP will remain the most important system for the forensic examiner in the near future. Likewise, given its stability and functionality, XP is the best candidate for a Windows analysis system as well. Unless otherwise noted, the commands and tools listed in this book will all run under the XP operating system.
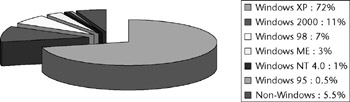
Figure 3-1: Windows client operating system usage
| Note | It is debatable whether *nix-based operating systems make better analysis environments when examining Windows machines. Any respectable examiner will have both environments available for analysis. |
Replacing Windows 2000 on the server side is Windows 2003. Windows 2003 is achieving growth in market share but many corporations continue to use Windows 2000 as their core server platform. Usage of 2003 is expected to increase slowly, and familiarity with the environment is of current and future value to the computer investigator.
| |
A new strategy computer investigators have to consider is the computer-equivalent of the SODDI defense, "Some Other Dude Did It." The defense has been tried successfully by three individuals in the United Kingdom, twice in child pornography cases and once in a denial-of-service attack. The basic defense comes in one of two forms:
-
"Some malicious code on my machine automatically downloaded the content without my being aware of it."
-
"A Trojan horse on my computer allowed another individual the ability to access my machine and they actually committed the crime."
The computer investigator may be called upon to prove or disprove claims such as the ones given previously. It is easier to prove them rather than disprove them, and this can be done by illustrating the following:
-
Malicious code that exhibits the behavior in question is known to exist.
-
The machine in question was not adequately protected against said code through anti-virus, spyware detection, a host firewall, or other tools.
-
The malicious code in question or remnants of it were found on the machine.
It is technically impossible to prove that malicious code was not responsible for a given action. The code may have been installed, ran, and then removed all reasonably obtainable traces of itself. Fortunately, the computer investigator does not need to prove beyond any doubt, only beyond a reasonable doubt. After all, aliens could have used a superior technology to magically plant the evidence, or a random re-alignment of the hard drive could have resulted in the creation of the images! In order to raise a reasonable doubt, the computer investigator should attempt to answer the following questions:
-
Is there existing malicious code that mimics the behavior claimed by the suspect?
-
Are the major anti-virus and spyware companies aware of similar code?
-
Do any of the locations visited by the suspect recently have the code present?
-
-
Was the subject's machine susceptible to the malicious code?
-
Is it the right operating system and version to be infected?
-
Was the machine patched at the time to the appropriate level?
-
Was antivirus or anti-spyware software installed and up to date?
-
-
Is the machine currently infected? If not, what did the suspect do to remove the code?
-
Does turning on the machine and mimicking the suspect's claimed actions duplicate the downloads?
-
Is there evidence of automatically running services or applications running on startup (for example, Run, RunOnce, or RunOnceEx in the registry)?
-
Does running the latest version of anti-virus software and antispyware software on the machine show this or other infections?
-
Did the suspect take any actions to remove the infection?
-
-
Is the behavior consistent with automated code or with human interaction?
-
Does it occur only at the times when the user is active, or does it occur at other times when the user is not present?
-
Is there consistent spacing between requests ?
-
In the case of downloads, were the files opened after downloading (for example, were they present in the Recent Docs lists of individual applications)?
-
Are there spelling or typographical errors in requests?
-
Is the activity corroborated by other electronic information (for example, typed emails, the TypedURL's registry key, and search engine queries)?
-
The SODDI defense strategy will likely be used again in court , and the computer investigator will need to work with legal and traditional investigators to take the possibility of malicious code into consideration. In a controlled, corporate environment, this may be easier to disprove, but in a home environment with multiple users on a computer, poor configurations, and open network connections, it becomes more difficult.
| |
| | ||
| | ||
| | ||
EAN: 2147483647
Pages: 71