| Sound security practices and settings are essential to successful systems administration. One way to set security policy is to use security templates. Understanding Security Policies and Administration Tools Security templates provide a centralized way of managing security-related settings for workstations and servers. You use security templates to apply customized sets of group policy definitions that are security- related . These policy definitions generally affect -
Account policies Settings control security for passwords, account lockout, and Kerberos. -
Local policies Settings control security for auditing, user rights assignment, and other security options. -
Event log policies Settings control security for event logging. -
Restricted groups policies Settings control security for local group membership administration. -
System services policies Settings control security and startup mode for local services. -
File system policies Settings control security for the local file system. -
Registry policies Settings control the values of security-related registry keys. Security templates are available in all Windows Server 2003 installations and can be imported into any group policy. Templates are stored in the %SystemRoot%\Security\ Templates directory and you can access them using the Security Templates snap-in, shown in Figure 4-10. You can also use the snap-in to create new templates. The standard templates distributed with Windows Server 2003 include -
dc security Contains the default security settings for domain controllers -
setup security Contains the default security settings for member servers -
securedc Contains moderate security settings for domain controllers -
securews Contains moderate security settings for workstations -
hisecdc Contains very stringent security settings for domain controllers -
hisecws Contains very stringent security settings for workstations Tip After you select the template that you want to use, you should go through each setting that the template will apply and evaluate how the setting will affect your environment. If a setting doesn't make sense, you should modify or delete it as appropriate.
Figure 4-10. Use the Security Templates snap-in to view and create security templates. 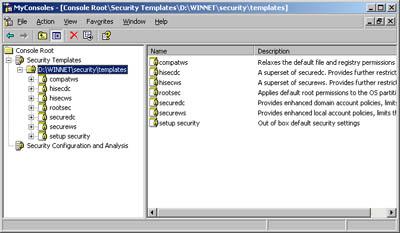 You don't use the Security Templates snap-in to apply templates. You apply templates using the Security Configuration And Analysis snap-in. You can also use Security Configuration And Analysis to compare the settings in a template to the existing settings on a computer. The results of the analysis will highlight areas where the current settings don't match those in the template. This is useful to determine if security settings have changed over time. You can access the security snap-ins by completing the following steps: -
Open the Run dialog box by clicking Start and then clicking Run. -
Type mmc in the Open field and then click OK. This opens the MMC. -
In MMC, click File, and then click Add/Remove Snap-In. This opens the Add/Remove Snap-In dialog box. -
In the Standalone tab, click Add. -
In the Add Standalone Snap-In dialog box, click Security Templates, and then click Add. -
Click Security Configuration And Analysis, and then click Add. -
Close the Add Standalone Snap-In dialog box by clicking Close, and then click OK. Applying Security Templates As stated previously, you use the Security Templates snap-in to view existing templates or to create new templates. Once you've created a template or determined that you want to use an existing template, you can then configure and analyze the template by completing the following steps: -
Access the Security Configuration And Analysis snap-in. -
Right-click the Security Configuration And Analysis node and then select Open Database. This displays the Open Database dialog box. -
Type a new database name in the File Name field and then click Open. -
The Import Template dialog box is displayed next . Select the security template that you want to use, and then click Open. -
Right-click the Security Configuration And Analysis node, and then choose Analyze Computer Now. When prompted to set the error log path, type a new path or click OK to use the default path . -
Wait for the snap-in to complete the analysis of the template. Afterward, review the findings and update the template as necessary. You can view the error log by right-clicking the Security Configuration And Analysis node and choosing View Log file. -
When you're ready to apply the template, right-click the Security Configuration And Analysis node and choose Configure Computer Now. When prompted to set the error log path, click OK. The default path should be fine. -
View the configuration error log by right-clicking the Security Configuration And Analysis node and choosing View Log File. Note any problems and take action as necessary.  |
