10.4 Incident handling procedures
|
10.4 Incident handling procedures
The flowchart in Figures 10.1 10.3 show the basic steps you should take to build your incident handling response system.
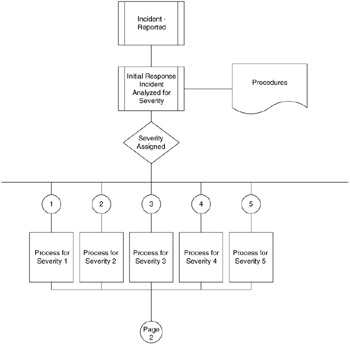
Figure 10.1
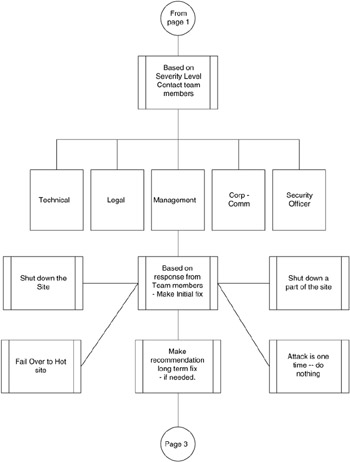
Figure 10.2
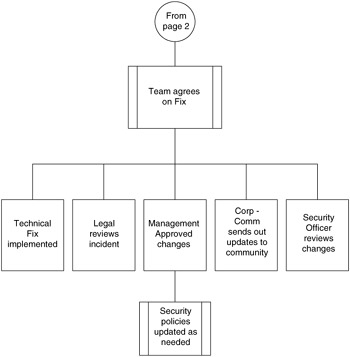
Figure 10.3
-
We start out with an incident. The incident is detected or reported into the system.
-
A focal point contact will review the incident and decide on the severity of the incident (may consult with other members on the needed course of action).
-
A severity will be assigned. The level of response will reflect the severity of the incident.
-
The required team members will be contacted and the needed action will be implemented.
-
An initial fix may be required. If so, the fix will be attempted. If not, a permanent solution will be developed and implemented.
-
One step that is missing is the analysis of the cost impact to the company. This will need to be considered and reported. The cost analysis can impact the "lessons learned" part of the process.
-
Finally, the security policies need to be updated from what was learned from the incident.