Part VII: Enhanced Network Protocols
| < Free Open Study > |
Extended IP Access ListsExtended IP access lists apply the same concepts that you just learned; however, they have much more control over whether to filter off a source and destination address, along with IP protocol type filtering. The general syntax for extended IP access lists is shown here: access-list { 100-199 2000-2699 } { permit deny } protocol_type Source_address Source_address_wildcard destination_address destination_address_wildcard [ protocol specific options ] [ precedence precedence ][ tos tos ][ log ][ established ] The access list range is 100 to 199 and has an extended range of 2000 to 2699 in Cisco IOS Release 12.0.0 and later. The protocol_type keyword is a special value that will cause the access list to look for a match in the Protocol field of the IP header. Table 14-2 lists the values as of Cisco IOS Release 12.0. Table 14-2. Extended IP Access List protocol_type Values for Cisco IOS Release 12.0
As you can see, the protocol_type field grows with every release of Cisco IOS Software. Specifying the protocol type can be a simple way to avoid complex filters. For example, specifying the protocol type when filtering routing protocols such as IGRP, EIGRP, and OSPF instead of filtering by the individual IP multicast messages that these routing protocols use can simplify your configuration when using the protocol_type keyword. Table 14-3 lists the currently supported TCP port numbers under Cisco IOS Release 12.0. Table 14-3. Extended IP Access List TCP Port Numbers Supported Under Cisco IOS Release 12.0
Table 14-4 lists the currently supported UDP port numbers under Cisco IOS Release 12.0. Table 14-4. Extended IP Access List UDP Port Numbers Supported Under Cisco IOS Release 12.0
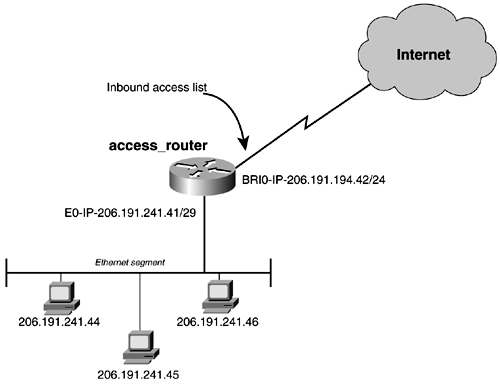
Another enhancement in extended access lists that is not offered by standard access lists is that you can specify a match on where traffic originates and where it is destined. At the end of the access list, you can set precedence and type-of-service (TOS) values. Here, the router examines the IP packet header for these values. The precedence values range from 0 to 7, while the TOS values range from 0 to 15. The established keyword is used to check for the ACK or RESET flags in the TCP header. If one flag is set, a match occurs. This command is used to pass existing data streams through the access list. Let's take a look at an extended access list that will be used on a connection to the Internet. In this example, an extended access list is configured on the inbound BRI interface to the Internet. Figure 14-3 illustrates the network topology for the next example. Figure 14-3. Extended Access List Example Now, let's add the syntax in Example 14-7 to the access_router. Example 14-7 Applying an Extended Access List to the access_routeraccess_router(config)# access-list 199 permit tcp any any established access_router(config)# access-list 199 deny ip 206.191.241.40 0.0.0.7 any access_router(config)# access-list 199 deny ip host 206.191.194.42 host 206.191.194.42 access_router(config)# access-list 199 permit icmp any any echo access_router(config)# access-list 199 permit icmp any any echo-reply access_router(config)# access-list 199 permit tcp any 206.191.241.40 0.0.0.7 eq www access_router(config)# access-list 199 permit tcp any 206.191.241.40 0.0.0.7 eq smtp access_router(config)# access-list 199 permit tcp any 206.191.241.40 0.0.0.7 eq domain access_router(config)# access-list 199 permit udp any 206.191.241.40 0.0.0.7 eq domain access_router(config)# access-list 199 deny tcp any 206.191.241.40 0.0.0.7 lt 1024 access_router(config)# access-list 199 deny tcp any 206.191.241.40 0.0.0.7 gt 1023 access_router(config)# access-list 199 permit udp any 206.191.241.40 0.0.0.7 gt 1023 access_router(config)# access-list 199 deny udp any 206.191.241.40 0.0.0.7 gt 50000 access_router(config)# access-list 199 deny udp any 206.191.241.40 0.0.0.7 lt 1024 Now, apply the access list to the BRI interface with the following commands: access_router(config)# int bri 0 access_router(config-if)# ip access-group 199 in The first line of the access list in Example 14-6 invokes the established keyword. This keyword looks for the ACK or the RESET bits set in the TCP header. This inherently allows existing data streams to qualify as a match. The established keyword should be used on any TCP traffic that is user-interactive, such as WWW. The second line and third lines in Example 14-6 are straightforward. In the next subset of lines, you have the following: access-list 199 permit tcp any 206.191.241.40 0.0.0.7 eq www access-list 199 permit tcp any 206.191.241.40 0.0.0.7 eq smtp access-list 199 permit tcp any 206.191.241.40 0.0.0.7 eq domain access-list 199 permit udp any 206.191.241.40 0.0.0.7 eq domain The first entry allows TCP from any source address or network to go to just the subnet of 206.191.241.40. This would include addresses .41, .42, .43, .44, .45, and .46 only if the TCP port is 80 for HTTP or WWW traffic. The second and third lines allow for the same subnet to inbound access from Simple Mail Transport Protocol (SMTP), port 25, and POP3 mail, port 110. Finally, we have two DNS entries: One allows for DNS that might be operating on TCP port 53, and the other allows for DNS, UDP port 53 access, the more common transport for DNS services. In the last subset of lines in Example 14-6, you see these lines: access-list 199 deny tcp any 206.191.241.40 0.0.0.7 lt 1024 access-list 199 deny tcp any 206.191.241.40 0.0.0.7 gt 1023 access-list 199 permit udp any 206.191.241.40 0.0.0.7 gt 1023 access-list 199 deny udp any 206.191.241.40 0.0.0.7 gt 50000 access-list 199 deny udp any 206.191.241.40 0.0.0.7 lt 1024 The first line of this subset of entries denies TCP traffic on ports less than 1024 and from any source network to the specific subnet of 206.191.241.40/29. The next line does the same for ports greater than 1023. The next line allows UDP ports greater then 1023 to pass, while the last two lines deny UDP ports greater then 50000 and deny UDP ports less than 1024. Basically, this subset is filtering some of the well-known UDP TCP ports. The implicit deny any would have caught all of these ports and the entry may seem redundant; however, sometimes it is desirable to "see" the actual ports being denied in the configuration and being logged when someone is trying to access them. In this example, you could also filter inclusive ports with a range statement. For example, these two lines could be combined into single entry: access-list 199 deny tcp any 206.191.241.40 0.0.0.7 lt 1024 access-list 199 deny tcp any 206.191.241.40 0.0.0.7 gt 1023 or: access-list 199 deny tcp any 206.191.241.40 0.0.0.7 range 1 65535 CAUTION Enhancements to the access-list commands are backward compatible; migrating from earlier releases to Release 11.1 will convert your access lists automatically. Releases earlier than Release 11.1 are not upwardly compatible with these enhancements. If you save an access list with these images later then Release 11.1 and then use software earlier than Release 11.1, the resulting access list will not be interpreted correctly. This can cause severe security problems. In other words, access lists from Cisco IOS Releases 11.1 and later are backward and forward compatible. Releases earlier than 11.1 are not backward or forward compatible. So, your lists run the chances of being destroyed if the router would come up under a different Cisco IOS Release image or was downgraded somehow. |
| < Free Open Study > |
EAN: 2147483647
Pages: 283
- Using SQL Data Definition Language (DDL) to Create Data Tables and Other Database Objects
- Using SQL Data Manipulation Language (DML) to Insert and Manipulate Data Within SQL Tables
- Understanding Transaction Isolation Levels and Concurrent Processing
- Working with Ms-sql Server Information Schema View
- Working with Stored Procedures