Lab 30: Configuring Dynamic Access Lists and Traffic Filters by Using Named Access Lists-Part II
| < Free Open Study > |
Standard IP Access ListsUntil this point, this chapter has have talked about access lists in a general sense. Now, you will learn about the specific types of IP access lists and how to configure them. A standard access list falls within the range of 1 and 99, and 1300 and 1999 in Cisco IOS Release 12.0. The log keyword can be added to the end of any access list. It causes an informational logging message about the packet that matches the entry to be sent to the console. The syntax for the standard IP access list is shown here: access-list x { deny permit } a.b.c.d wildcard_mask { log } The a.b.c.d argument is the IP address that the wildcard mask is OR'd with to yield a true or false result. The standard access list can be applied in a number of ways:
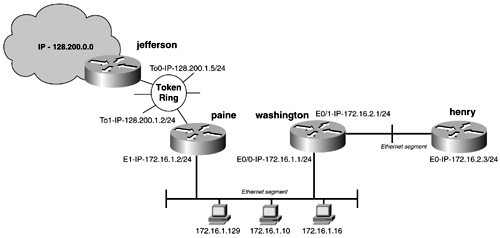
Of course, there are many more, and that is why you can't limit your use of access lists to packet filters. The example in this section uses standard access lists to filter routes, deny network access, and deny virtual terminal access. Figure 14-2 illustrates a simple network running EIGRP as its routing protocol. From this example, you can configure multiple access lists to accomplish the following: Figure 14-2. Standard IP Access List Example
Under normal circumstances, with the eigrp no auto-summary command added to each router, the route table of the jefferson router would look like Example 14-2. Example 14-2 Route Table of the jefferson Routerjefferson# show ip route Codes: C - connected, S - static, I - IGRP, R - RIP, M - mobile, B - BGP D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2 E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGP i - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, * - candidate default U - per-user static route, o - ODR T - traffic engineered route Gateway of last resort is not set 172.16.0.0/24 is subnetted, 2 subnets D 172.16.1.0 [90/297728] via 128.200.1.2, 00:00:31, TokenRing0 D 172.16.2.0 [90/323328] via 128.200.1.2, 00:00:18, TokenRing0 128.200.0.0/24 is subnetted, 1 subnets C 128.200.1.0 is directly connected, TokenRing0 jefferson # One way to prevent jefferson from having access to 172.16.2.0/24 is to use a standard access list called by a distribution list on the paine router. Example 14-3 demonstrates the addition of the access list to the paine router. Recall from the previous chapters on routing protocols that a distribute list is used to filter route updates. Example 14-3 Adding a Distribution List Calling a Standard Access Listpaine(config)# router eigrp 2001 paine(config-router)# distribute-list 1 out to1 paine(config-router)# exit paine(config)# access-list 1 deny 172.16.2.0 0.0.0.255 paine(config)# access-list 1 permit any paine(config)# exit paine# Example 14-4 lists the route table of the jefferson router after the access list has been applied. Example 14-4 Route Table of the jefferson Router jefferson# show ip route Codes: C - connected, S - static, I - IGRP, R - RIP, M - mobile, B - BGP D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2 E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGP i - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, * - candidate default U - per-user static route, o - ODR T - traffic engineered route Gateway of last resort is not set 172.16.0.0/24 is subnetted, 2 subnets D 172.16.1.0 [90/297728] via 128.200.1.2, 00:00:31, TokenRing0 C 128.200.1.0 is directly connected, TokenRing0 jefferson# Following the guidelines listed at the beginning of the chapter, you filter the most specific address first and then permit the general address. There is an implicit deny any at the end of the access list, so you need to permit routing updates that you are not filtering before the implicit deny. Table 14-1 lists access list shortcuts. Table 14-1. Access List Shortcuts
To limit Telnet access on the henry router, you can apply a standard access list to the vty ports on the routers. Recall from Chapter 1, "The Key Components for Modeling an Internetwork," that a show line command lists the vty or the Telnet access ports. Use the following command to apply an access list to a port on a router: access-class access-list_number { in out } In this case, you want to allow the address 172.16.1.129 Telnet access to henry while denying access to all the others. To accomplish this, you need to locate the absolute line numbers of the vty sessions. This can be done with the show line command. Then apply an access group , calling an access list only to those line numbers. Example 14-5 lists the commands needed to limit Telnet access to one address on the router henry. Example 14-5 Controlling Telnet Access with Standard IP Access Listshenry# show line Tty Typ Tx/Rx A Modem Roty AccO AccI Uses Noise Overruns * 0 CTY - - - - - 0 0 0/0 1 AUX 9600/9600 - - - - - 0 0 0/0 2 VTY - - - - - 2 0 0/0 Finally, you must stop all users on subnet 172.16.1.0/24 from accessing the Token Ring network. To accomplish this, you will use the most common application of an access list by applying it with an IP access group. Access groups are used to apply an access list to an interface. When you configure an access group, it is applied in an in or out fashion. The in or out options represent how the access list will be applied from the perspective of the interface. out applies the access list to all outgoing packets, whereas in applies the access list to all incoming packets. The out option will not filter packets that originate on the router itself. As mentioned previously, if no access list is defined, when an access group is applied to an interface, the default action of the router is to filter all traffic. You can apply only one outbound and one inbound access list per interface. Use the following command to apply an access list to an interface on a router: ip access-group x { in out } Example 14-6 illustrates the commands needed to accomplish denying the 172.16.1.0/24 subnet access to the Token Ring. Example 14-6 Controlling Network Access with Standard IP Access Listspaine# conf t Enter configuration commands, one per line. End with CNTL/Z. 01:42:01: %SYS-5-CONFIG_I: Configured from console by console paine(config)# access-list 5 deny 172.16.1.0 0.0.0.255 paine(config)# access-list 5 permit any paine(config)# int to1 paine(config-if)# ip access-group 5 out paine(config-if)# ^Z |
| < Free Open Study > |
EAN: 2147483647
Pages: 283