Lab 30: Configuring Dynamic Access Lists and Traffic Filters by Using Named Access Lists-Part I
| < Free Open Study > |
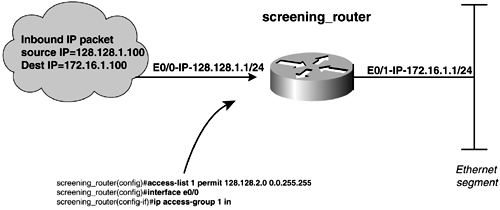
Access Lists, Wildcard Masks, and Binary MathEverything digital speaks the language of ones and zeros, and access lists are no exception. Standard and extended access lists use the concept of a wildcard mask, a binary number expressed in dotted -decimal notation. In an access list, the address bits, or the first address entry, are compared to a corresponding wildcard mask. If the wildcard mask has a 0 bit, it means that the corresponding bit location in the access list address must match the bit value of the compared packet. This is sometimes called a care bit. If the wildcard mask has a 1, it means that this bit value will not be compared to anything; sometimes it is called a don't care bit. The concept of the care and don't care bits becomes clear only when everything is broken down into binary form. Figure 14-1 shows a simple access list configured on the router's Ethernet 0/0 port. The text following the figure provides a step-by-step look at how this works. Figure 14-1. Simple Access List Example The first step in understanding the access list is to write out both of the lines of the access list in binary. Figure 14-1 shows the following access list: access-list 1 permit 128.128.2.0 0.0.255.255 Writing out the first part of the list in binary yields the following:
You will use the first part of the access list as the comparison bits. The second half of the access list tells what bits you should care about or must match from the comparison bits. Writing the second half of the access list in binary yields this result:
Now, if you lay the two together, you can see directly what bits are significant. In this case, you can see that you care about every bit in the first two octets only because every value in them is set to 0.
Essentially, the first bit of whatever address you compare this access list to must be a 1, and the next 7 bits must be 0. The second octet says the same thing. In the third and fourth octet, there are all 1 bits in the wildcard mask. Therefore, you don't care whether these bits match because you're basically ignoring the last two octets; this means that these bits can be either a 1 or a 0. This example uses a standard access list, so the router will use the source IP address of the incoming packet for its comparison. Breaking out the source address, you have the following:
Examining the first bit, you can see that it is a 1. From the previous comparison, you know that you care about this bit and that it has to be a 1. The second bit is 0; again, the wildcard mask indicates that you care about this bit and that it has to be a 0. Stepping through the rest of the example, it becomes apparent that this comparison will yield a true or positive result. The process that the router uses is called a logical OR, or a Boolean OR. Much as a router uses a logical AND between the destination packet's address and the mask on the router's interface to find out whether a particular address resides on that subnet, a logical OR is used in access lists. A logical AND states that when comparing two binary numbers , the result will yield a 1 if, and only if, both bits are 1. For example, performing a logical AND on two addresses, 128.128.1.1 and 255.255.255.0, would yield 128.128.1.0.
A logical OR is just the opposite . It states that when comparing two binary numbers, the result will yield a 0 if and only if both bits are 0. For example, performing a logical OR on the same address pair (128.128.1.1 and 255.255.255.0) yields 255.255.255.1.
You can now apply the concept of the logical OR to access lists. All access lists, standard or extended, yield a true result if a logical OR is performed between the wildcard mask and the test address, and if this result equals the result of performing a logical OR between the address and mask pair of the access list. For example, assume the use of the following standard access list: access-list 1 permit 128.128.0.0 0.0.255.255 You are given two packets with the source addresses of 128.128.1.1 and 128.192.1.1. Which address will pass the access list? Performing a logical OR on the test address and the wildcard mask, 128.128.1.1 and 0.0.255.255, yields 128.128.255.255. Next, you can perform a logical OR on the address and mask pair of the access list. Performing a logical OR on 128.128.0.0 and 0.0.255.255 yields 128.128.255.255. Notice that the results are the same, so the access list yields a true result for the address 128.128.1.1. Using the second address, you perform a logical OR of 128.192.1.1 and 0.0.255.255, which yields 128.192.255.255. Compare this result with a logical OR of the access list address and mask pair. A logical OR of 128.128.0.0 and 0.0.255.255 yields 128.128.255.255. Notice this time that the results of 128.128.255.255 and 128.192.255.255 do not equal each other, so, in this case, this address of 128.192.1.1 would yield a false result. In this example, the bit boundaries are set cleanly to highlight the example, and performing the logical OR might seem like a lot of work. But when you start performing the same exercise with access lists such as access-list 1 permit 64.35.100.150 0.4.10.254, breaking down the numbers in binary form and using the logical OR is the only way to understand which bits are significant and which ones are not. | ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| < Free Open Study > |
EAN: 2147483647
Pages: 283