Configuring NAT with iptables
Configuring NAT with iptablesA packet-filter firewall, as just described, has the capacity to deliver or stop delivery of packets based on criteria such as the source and destination IP addresses, port numbers , and so on. This is an extremely useful feature, but it's not the limit of iptables ' capabilities. One feature of iptables that's particularly useful in certain situations is the ability to program the Linux kernel to perform Network Address Translation (NAT). NAT allows you to modify certain parts of a TCP/IP packet to increase the flexibility of your network addressing. Basic NAT configuration is relatively straightforward, but before you configure it, you should know what it is and what you can do with it. What Is NAT?NAT allows a router to modify the contents of TCP/IP packets. In particular, NAT enables changes to the source and destination addresses of the packets. Why would you want to do this? There are several possibilities:
This final option is probably the most common use of NAT in Linux, and it's frequently referred to by another name : IP masquerading. For this reason, this is the use of NAT upon which this chapter focuses, but it's not the only use of NAT. NAT requires the use of a router. This router need not be very sophisticated by router standards, but the router does need NAT support. The Linux kernel, as configured through iptables , is perfectly capable of filling this role. A Linux computer configured as a NAT router usually has two external network interfaces ”typically two Ethernet interfaces or an Ethernet interface and a PPP interface. NOTE
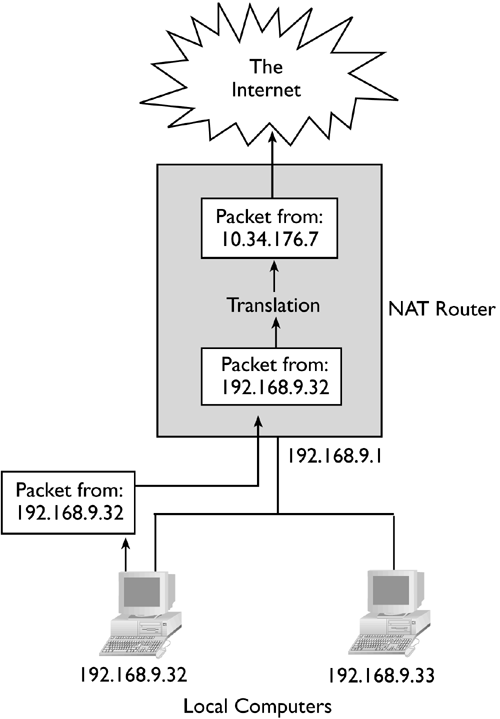
To understand NAT, consider a network transaction through a NAT router. This transaction begins with a client on the NAT-protected network, such as a Web browser. The user tries to connect to an external site (say, at 172.18.127.45). The browser generates an HTTP request packet, addressed from its local IP address (say, 192.168.9.32). The client sends this request to its local gateway system, which is the NAT router. Upon receipt of the packets that make up this request, the NAT router examines the packets and changes the source IP address to that of the NAT router's own external address (say, 10.34.176.7) and sends the packets on their way. The Web server believes that the packets came from the NAT router, and so addresses its reply to the NAT router. When the NAT router receives this reply, it recognizes it as a reply to the request from 192.168.9.32, and so it reverses the process, changing the destination address of the reply packets and passing them on to the client. This process is illustrated in Figure 25.3. If all goes well, neither the client nor the server knows that NAT was involved, so network programs don't need to be rewritten to support NAT. Some forms of NAT, and in particular IP masquerading, provide an added benefit: automatic firewall-like protection of the private network. Because the outside world sees just one IP address, outside systems cannot initiate normal direct connections to the internal computers. Only reply packets to connections initiated by clients within the NAT network can reach the clients . For this reason, some NAT products, particularly for home broadband users, are marketed as firewalls, but the two are slightly different. Figure 25.3. NAT involves modifying TCP/IP packets so that addresses are altered in one way or another. NAT does have certain drawbacks, as well as advantages:
Although it's not strictly a disadvantage of NAT, you shouldn't rely upon its security features too much. A virus, worm, Trojan horse, or other local security problem can still launch attacks from within your network, or use an outgoing connection to allow an outsider access. On the whole, NAT is a very useful tool for connecting many computers to a wider network using a single IP address, or for performing other tricks that involve the shuffling of IP addresses. Setting iptables NAT OptionsLinux's NAT features are contained within a separate table from the filter table described in earlier sections of this chapter. In particular, NAT resides in the nat table. This table, like the filter table, consists of three chains: PREROUTING , POSTROUTING , and OUTPUT . Despite having the same name, the OUTPUT chain in the nat table is different from the OUTPUT chain in the filter table. Enabling NAT can be done by typing two commands: # iptables -t nat -A POSTROUTING -o external-interface -j \ MASQUERADE # echo "1" > /proc/sys/net/ipv4/ip_forward NOTE
In the first command, external-interface is the name of the external network interface, such as ppp0 or eth1 . This command tells Linux to perform IP masquerading on all routed network traffic. The second command enables routing in the Linux kernel (you'd use the same command to enable non-NAT routing features). It's common to enable firewall features, as described earlier in this chapter in the section "Configuring a Firewall with iptables," on a NAT router. Protecting computers behind the NAT router from direct attacks isn't much of an issue in this situation, but you should protect the NAT router from attacks on itself, and you should also limit external access from within your network. Even if you're the only user, it's possible that a virus, worm, or Trojan horse could try to initiate an undesirable external access, so you should limit outgoing packets. You can also use stateful inspection to block attempts to hijack connections made from inside your network. You can enter the NAT commands in the same script you use to activate your firewall features. If at all possible, your NAT router should run no servers. If a server running on a NAT router is compromised, it can be used to compromise the rest of your network. In fact, you can install Linux on an old computer and use it as nothing but a NAT router for a small network. Even an old 80486 system should suffice. |
EAN: 2147483647
Pages: 203
- Key #1: Delight Your Customers with Speed and Quality
- Beyond the Basics: The Five Laws of Lean Six Sigma
- Making Improvements That Last: An Illustrated Guide to DMAIC and the Lean Six Sigma Toolkit
- The Experience of Making Improvements: What Its Like to Work on Lean Six Sigma Projects
- Six Things Managers Must Do: How to Support Lean Six Sigma