Using Internet Connection Firewall
|
|
In networks, a firewall is any piece of computer software or hardware that protects a network from intruders. For example, suppose that you own a small company that uses 200 computers. Each user needs to access the Internet every day, so there is a primary Internet link going from your company to an ISP. Although you want to use the Internet each day, you do not want Internet users to get inside of your private network and steal information from you. What to do? The answer is a firewall.
Firewalls use various kinds of tactics to check traffic as it flows in and out of the network. Using rules that are configured by system administrators, certain kinds of traffic are allowed or not allowed, and some kinds of traffic can even be seen as threatening. In short, the firewall acts as a traffic cop who makes certain that no one gets inside of the private network. Firewalls are nothing new; they have been around for years, and most larger, private networks today use some kind of firewall technology. In addition, a number of server products provide firewall and caching services.
However, because of threats from the Internet, home PCs and small office environments also need firewall protection. Indeed, firewalls are not limited to protecting large networking environments. Windows XP includes its own firewall to help protect your computer from malicious users when you’re on the Internet. You can think of the firewall found in Windows XP as a “personal firewall,” and indeed, other companies even produce firewalls for the typical home or small office user. An example of such a product is Norton Internet Security.
| Note | Although the Windows XP firewall provides basic firewall protection, it does not have the flexibility and caching services provided by other third-party firewall products. Depending on your needs, you might consider a third-party firewall product for Windows XP instead of ICF. Of course, ICF is already built into Windows XP and it is free, so it is more convenient to use. |
Whenever you are using the Internet, your computer is open for potential attacks. With a dial-up connection, the attacks are limited because you are not connected to the Internet all of the time. However, with the explosive growth of broadband connections (DSL, cable, satellite), the need for a firewall becomes very important because computers with such connections are always connected to the Internet, and therefore always exposed to danger. In a network situation where ICS is used, the entire network is open to attacks from the Internet since all computers connect to the Internet through the ICS host. For this reason, ICF is included with Windows XP and is available for your use.
Understanding How ICF Works
ICF is a software solution in Windows XP. This means that ICF uses code built into the Windows XP operating system to monitor and manage traffic. ICF is considered a stateful firewall. This simply means that ICF works with your Internet connection to examine traffic as it is passing through the firewall both to and from your computer or network.
Because ICF is stateful, it examines Internet traffic in terms of its live use. If something attempts to enter the firewall that is not allowed, ICF simply steps in and blocks the traffic from entering. In other words, IP packets that are not allowed are simply dropped at the firewall. Thus no unallowed traffic ever enters the firewall. To use stateful inspection, ICF examines the destination of every piece of traffic coming from your computer or from computers on your network. Whenever something is sent to the Internet (such as a URL request), ICF keeps a routing table to track your requests. When data comes to the firewall, ICF inspects it to see whether it matches up with requests found in the routing table. If so, IFC passes the data onto your computer or the requesting computer on your network. If not, IFC simply blocks the data from entering the firewall. The end result is that any traffic you want from the Internet can enter the firewall, and anything you have not requested is blocked.
| Note | Dropped communication is done automatically without any intervention from you. In fact, ICF doesn’t even tell you when communication from the Internet has been dropped. |
As you might imagine, ICF control is very helpful, but it can be a problem with some applications and services. Fortunately, you can configure to meet your specific needs.
Troubleshooting: ICF and Virus Protection
ICF is a method for protecting your computer against attacks from the Internet, but it does not provide any protection against computer viruses or Trojan horses. Windows XP does not provide any software to protect against these very real and common threats, so it is imperative that you install antivirus software on all computers on your network and keep that software up to date at all times. I have had to solve countless virus-related problems on users' computers simply because those computers did not have antivirus software installed. The moral to this story is simply this: ICF provides you with protection against hacker attacks, but you must use antivirus software to protect against computer viruses. Be safe, rather than sorry!
Issues with ICF
Before getting into more detail about ICF configuration, you need to understand a few issues concerning ICF’s default behavior. You should keep these in mind as you are setting up Internet connections and home or small office networks.
-
ICF should be enabled on any shared Internet connection in your home or small office network. You do not have to use a home or small office network to use ICF; if you have only one computer and you want the additional protection, ICF works great on one computer too.
-
ICF works on a per connection basis. For example, suppose that your computer has a DSL connection and a modem connection. You use the modem connection in the event that the DSL connection goes down. You need to enable ICF on both the DSL and modem connections to have full protection. ICF is per connection—not per computer.
-
In a small network setting using Internet Connection Sharing (ICS), you should certainly enable ICF on the ICS connection. However, if other computers on the network have other ways to connect to the Internet (such as through modems), you need to enable ICF on each of those connections as well. Again, ICF is only good on a per-connection basis.
-
Any configuration changes that you make to ICF are only for that particular connection; they do not transfer from connection to connection. For example, if you have two connections and ICF is enabled on each of them, you must individually configure each connection as needed.
-
Outlook Express will work with ICF and will continue to check for and download mail automatically. Microsoft Office applications such as Outlook 2000 will not be able to check mail automatically when Microsoft Exchange Server is in use because Remote Procedure Calls (RPCs) are used with the mail server. The mail server must be able to contact the Outlook client—but ICF will block this kind of communication. If you are using Outlook 2000 to connect to ISP mail, you’ll not have any problems.
-
ICF should not be enabled on any computer’s network adapter card that is used to connect to local computers. Doing so will prevent connectivity. ICF should be used only for connections to the Internet—not connections between computers on your private network.
| Note | ICF, like ICS, is a home and small office solution. In environments where Windows XP is used with Microsoft DNS or DHCP and other large-scale networking services, ICF should not be used. |
Turning On ICF
You can enable ICF through the Internet connection’s Properties sheets, or when you run the Network Setup Wizard. If you have configured ICS, then you were prompted to enable ICF as well. If you right-click any Internet connection found in the Network Connections folder and click Properties, you will see the Properties sheets for that connection. Click the Advanced tab, and you see the ICF check box, as you saw in Figure 13-1.
ICF is designed to work with ICS in order to protect your shared Internet connection, therefore protecting the computers on your network. In most circumstances, the check box option that enables ICF is all you need to click in order to protect your network. However, there are some additional configuration options that you can use if necessary, and the next section takes a look at those settings.
Configuring ICF Settings
If you click the Settings button on the Advanced tab, you see advanced settings that govern how ICF works and what kinds of applications and services it allows. Again, you typically do not need to configure anything here if you are simply using the Internet and accessing Internet mail. However, if you are using certain applications or you are providing certain types of content to the Internet, then you may need to configure some of these settings.
The first tab is the Services tab. The Services tab provides you a list of check box options concerning services that are running on your computer or network that you are allowing Internet users to access. For example, suppose that you are running a web server on your Windows XP Professional computer. If ICF is in use, you need to check the Web Server (HTTP) and possibly the Secure Web Server (HTTPS) check boxes so that Internet users can access content on your web server. When you click these check boxes and click OK, ICF basically reconfigures itself to allow certain kinds of content to pass through the firewall in order to meet these needs. Or, suppose for example that you want to use Remote Desktop Sharing with someone on the Internet. By default, ICF will not allow this kind of communication, but if you enable it here, ICF understands that Remote Desktop Sharing should allow it.
If you want to enable one of the services listed on the Services tab, just click the desired check box. A Service Settings dialog box, shown in Figure 13-5, then appears where you must enter the name or IP address of the computer on your network that runs the service. Under most circumstances, you do not need to change any of the port information because Windows XP configures this information on its own. The computer name or IP address tells Windows XP which computer runs the service so that only that computer receives the service traffic—not other computers on your network. As you can see, this is an additional security feature that keeps service traffic from entering computers that do not offer the service.
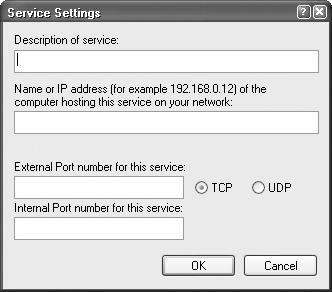
Figure 13-5: Service Settings dialog box
You can also configure services that are listed by default. Click the Add button and enter the service name and TCP/IP port numbers on which the service communicates. This is an advanced configuration, but the option is provided for networks that use custom applications or those who want to provide custom services to Internet users.
| Note | ICF is designed to keep your computer and network secure, but it can do its job only if you keep it enabled and configured effectively. For this reason, you should never make any changes to the Services tab that you do not clearly understand. For example, suppose that you enable the Web Server feature. This setting tells ICF that your computer is a web server and that it should allow web server request messages to pass through the firewall. However, if your computer is not really a web server, then you have opened the door for intruders to get into your computer or network. ICF is one of those great features where less is more. Do not enable anything extra unless absolutely necessary. |
The next tab is Security Logging. The Security Logging tab enables you to log unsuccessful inbound connections, unsuccessful outbound connections, or both. Keep in mind that ICF does not tell you when inbound communication is dropped from the firewall. However, if you are naturally curious or you believe there are regular Internet attacks on your computer, you can turn on the logging feature, then check out the log file periodically to see what is going on.
By default, the security log is stored in C:\Windows\pfirewall.log, but you can click the Browse button on the Security Logging tab, shown in Figure 13-6, to change the location. Also notice that the log file has a default maximum size of 4,096KB (4MB). You can increase or decrease this space if you like, but this is plenty of room. To enable logging for unsuccessful inbound or outbound connections, just click the applicable check boxes.
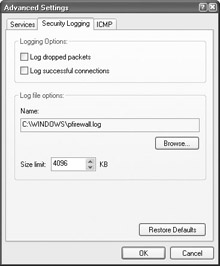
Figure 13-6: Security Logging tab
If you want to check out the log file, just browse to the location of the file and open it (it will open with Notepad). As you can see in Figure 13-7, the log file contains TCP addressing and port information and is not exactly easy to read. However, you can see how many firewall drops occurred over a period of time.
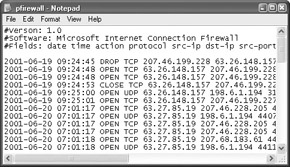
Figure 13-7: Firewall log
The final tab is the ICMP tab, shown in Figure 13-8. ICMP (Internet Control Message Protocol) is a protocol used on the Internet that enables computers to send information to and from each other about network problems or transmissions problems. For example, if one computer is sending information to another computer and an error occurs, that computer can use ICMP to tell the other what has happened. ICMP is a commonly used protocol and can be very helpful to computers on the Internet.

Figure 13-8: ICMP tab
However, some attacks from the Internet act like ICMP messages, so by default, no ICMP messages are allowed on your network. Depending on your needs, however, you may want to enable some (or all) of these ICMP message types. Just click the check boxes on the ICMP tab, shown in Figure 13-8, and you can select a message type and read more about it in the Description portion of the window.
|
|
EAN: N/A
Pages: 164