Testing from the Outside-In
|
Testing from the Outside->InOf course this is typically what a firewall is all aboutmaking sure people cannot get back in. We use the exact same method as previously described in the INSIDE->OUT nmap scan but with the added dimension of looking at the nmap output itself. Obviously you need to have a host you can get to first, so if you're on the other side of the Internet, your options are limited. However, if you're on the same segment of the firewall, here is a neat trick that may help you identify weaknesses in your firewall. Set the firewall as your gateway. You'd be surprised at how many times we have managed to beat firewall rules by doing this. We realize it's a pretty brainless method, but it's often the simple things that get you into the most trouble. Figure 10.2. Setting the firewall as your gateway.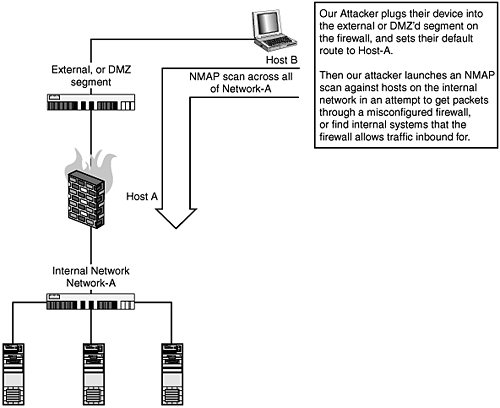 Host-A: Our firewall Host-B: The attacker Network-A: Internal Network Host-B connects to the "hard" or externally facing network in your office building (perhaps from a conference room on a "DMZ" network or wireless network). Host-B sets the default route to Host-A. Then it starts using nmap to scan out nonroutable IP address space (RFC1918) and watching their logs for ICMP or UDP messages of interest, and ultimately it discovers what the IP space for Network-A is. Another method of discovering what this IP space is would be to send email messages to email addresses that do not exist and look at the IP information in the headers of the messages to determine the IP space of Network-A. |
|