Understanding Server Roles
|
EXAM 70-293 OBJECTIVE 1
When Windows Server 2003 is installed on a computer, it provides a wide variety of tools and functionality. However, additional features may still need to be installed on the server to bring clients the services they need. The server may need to supply file and print services, authenticate users, or support a local intranet Web site. Until Windows Server 2003 is configured to supply these services, clients will be unable to use the server in a manner that is required by the organization.
Server roles are profiles that are used to configure Windows Server 2003 to provide specific functionality to the network. When you set up a server to use a specific role, various services and tools are enabled or installed, and the server is configured to provide additional services and resources to network clients. Roles are applied to machines using the Configure Your Server Wizard and managed using the Manage Your Server tool.
As shown in Figure 2.1, Manage Your Server provides information about the roles that are currently configured for a server, and it provides the ability to add and remove roles from a server. Depending on your server’s settings, this tool will start automatically upon logon. If you’ve checked the Don’t display this page at logon check box at the bottom of this window, Manage Your Server will not start automatically. You can start it manually by selecting Start | Administrative Tools | Manage Your Server.
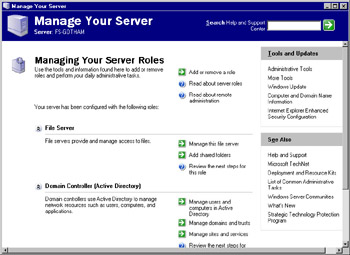
Figure 2.1: The Main Manage Your Server Window
As shown in Figure 2.1, there are a variety of items in Manage Your Server’s main window. The left side of the window lists the roles currently configured for the server. Beside each entry, there are buttons that relate to the corresponding role. These buttons differ from role to role, and they are used to invoke other tools for managing the role or to view information on additional steps that can be taken to configure, administer, and maintain the role.
Near the top of the Manage Your Server window are three buttons. Two of these are used to obtain additional information about roles and remote administration. The other button, labeled Add or remove a role, is used to invoke the Configure Your Server Wizard. You can also start the Wizard by selecting Start | Administrative Tools | Configure Your Server.
When the Configure Your Server Wizard starts, it informs you of possible preliminary steps that need to be taken before a new role is added. As shown in Figure 2.2, these steps include ensuring that network and Internet connections have been set up and are active for the server, peripherals are turned on, and your Windows Server 2003 installation CD is available. When you finish reading this information, click the Next button to have the Wizard test network connections and continue to the next step.
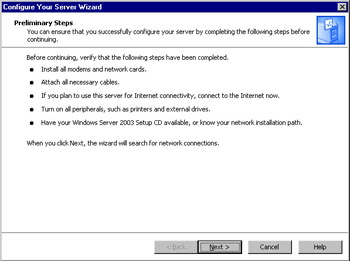
Figure 2.2: Preliminary Steps of the Configure Your Server Wizard
In the next window, shown in Figure 2.3, roles that are available to add and remove through the Wizard are listed in the Server Role column; the Configured column indicates whether the role has been previously installed. If you want to install a role that isn’t listed here, click the Add or Remove Programs link to open the Add or Remove Programs applet (in the Windows Control Panel), where you can configure additional services.
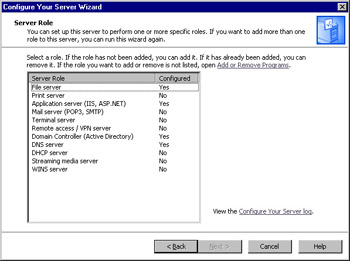
Figure 2.3: Configuring Server Roles
In Figure 2.3, you can see that there are 11 different roles that can be applied to Windows Server 2003 through the Configure Your Server Wizard. These roles are as follows:
-
Domain controller This role is used for authentication and installs Active Directory on the server.
-
File server This role is used to provide access to files stored on the server.
-
Print server This role is used to provide network printing functionality.
-
DHCP server This role allocates IP addresses and provides configuration information to clients.
-
DNS server This role resolves IP addresses to domain names (and vice versa).
-
WINS server This role resolves IP addresses to NetBIOS names (and vice versa).
-
Mail server This role provides e-mail services.
-
Application server This role makes distributed applications and Web applications available to clients.
-
Terminal server This role provides Terminal Services for clients to access applications running on the server.
-
Remote access/VPN server This role provides remote access to machines through dial-up connections and virtual private networks (VPNs).
-
Streaming media server This role provides Windows Media Services so that clients can access streaming audio and video.
After you select the role to add to the server, click Next to step through the process of setting up that role. Each set of configuration windows is different for each server role. Also, although multiple roles can be installed on Windows Server 2003, only one role at a time can be configured using the Configure Your Server Wizard. To install additional roles, you need to run the Wizard again.
Manage Your Server
The Manage Your Server tool is new to Windows Server 2003. It is similar to the Configure Your Server utility in Windows 2000 and provides a centralized location for administrators to access tools, view information, and launch programs used to maintain specific roles. In addition, servers with Internet access can benefit from this tool, because it can be used to invoke Windows Update to apply security patches, service packs, new drivers, and other updates. Manage Your Server also provides links to Web pages located on Microsoft’s site, which can assist administrators in understanding how to deal with specific problems and obtaining the latest information.
Manage Your Server also provides a way to launch the Configure Your Server Wizard, where you can add roles to a server or remove existing ones. Because the roles installed on a server can be modified at any time, administrators are able to change a server’s role on the network as needs within the organization change.
Before setting up a server role (as we will do in Exercise 2.1, later in this chapter), it is important to understand each of the roles that can be applied to Windows Server 2003. In the sections that follow, we will discuss these roles in greater detail and examine how they are installed with the Configure Your Server Wizard and other tools.
Domain Controllers (Authentication Servers)
Domain controllers are a fundamental part of a Microsoft network because they are used to manage domains. A domain is a logical grouping of network elements, including computers, users, printers, and other components that make up the network and allow people to perform their jobs. When a server is configured to be a domain controller (DC), it can be used to manage these objects and provide other capabilities for configuring and controlling your network.
An important function of a domain controller is user authentication and access control. Authentication is used to verify the identity of an object such as a user, application, or computer. For example, when a user logs on to a domain, he or she will enter a username and password, which is compared to information that is stored on the domain controller. If the information provided by the user matches data in the user account, the domain controller considers the person to be authentic. The process continues by giving an appropriate level of access, so the user can utilize resources on the network. Access control manages which services and resources users (or other objects) are permitted to use and how they can use them. By combining authentication and access control, a user is permitted or denied access to network services and resources.
Active Directory
To perform these functions, the domain controller must have information about users and other objects in a domain. In Windows 2000 and Windows Server 2003, this data is stored in Active Directory (AD), which is a directory service that runs on domain controllers. A directory serves as a structured source of information, containing data on objects and their attributes. Objects in the directory represent elements of your network (including users, groups, and computers). Attributes are values that define an object (such as its name, location, security rights, and other features). Using tools that access AD, an administrator can manage an object’s attributes to provide information that is accessible to users and control security at a granular level. By serving as a data store of information about a domain, AD is the means by which administrators achieve greater and more flexible control over a network.
When AD is installed, the server becomes a domain controller. Until this time, it is a member server that cannot be used for domain authentication and management of domain users or other domain-based objects. This does not mean, however, that AD can be installed on every version of Windows Server 2003. It can be installed on Standard Edition, Enterprise Edition, and Datacenter Edition, but servers running the Web Edition of Windows Server 2003 cannot be domain controllers. Web Edition servers can be only stand-alone or member servers that provide resources and services to the network.
| Exam Warning | A server without AD installed on it can still deliver a variety of services, file storage, and access to other resources. However, until AD is installed, the server cannot authenticate domain users or provide the other functions of a domain controller. Once AD is installed, the member server ceases to be a member server and becomes a domain controller. |
A Windows Server 2003 computer can be changed into a domain controller by using the Configure Your Server Wizard or by using the Active Directory Installation Wizard (DCPROMO). DCPROMO is a tool that promotes a member server to domain controller status. During the installation, a writable copy of the AD database is placed on the server’s hard disk. The file used to store directory information is called NTDS.dit and, by default, is located in %systemroot%\NTDS. When changes are made to the directory, they are saved to this file.
Each domain controller retains its own copy of the directory, containing information about the domain in which it is located. If one domain controller becomes unavailable, users and computers can still access the AD data store on another domain controller in that domain. This allows users to continue logging on to the network, even though the domain controller that is normally used is unavailable. It also allows computers and applications that require directory information to continue functioning while one of these servers is down.
Because a domain can have more than one domain controller, changes made to the directory on one domain controller must be updated on others. The process of copying these updates is called replication, which is used to synchronize information in the directory. Without replication, features in AD would fail to function properly. For example, if you added a user on one domain controller, the new account would be added to the directory store on that server. This would allow the user to log on to that domain controller, but he or she still could not log on to other domain controllers until the account was replicated. When a change is made on one domain controller, the changes need to be replicated, so that every domain controller continues to have an accurate copy of AD. This type of replication is called multi-master, because each domain controller contains a full read/write copy of the AD database.
Operations Master Roles
By default, all domain controllers are relatively equal. However, there are still some operations that need to be performed by a single domain controller in the domain or forest. To address these, Microsoft created the concept of operations masters. Operations masters serve many purposes. Some control where components of AD can be modified; others store specific information that is key to the healthy function of AD at the domain level. Because only one domain controller in a domain or forest fulfills a given role, these roles are also referred to as Flexible Single Master of Operations (FSMO) roles.
Some FSMO roles are unique to each domain; others are unique to the forest. A forest is one or more domain trees that share a common schema, Global Catalog, and configuration information. The schema is used to define which types of objects (classes) and attributes can be used in AD. Without it, AD would have no way of knowing what objects can exist in the directory or what attributes apply to each object. The Global Catalog is a subset of information from AD. It stores a copy of all objects in its host domain, as well as a partial copy of objects in all of the other domains in the forest.
There are five different types of master roles, each serving a specific purpose. Two of these master roles are applied at the forest level (forest-wide roles), and the others are applied at the domain level (domain-wide roles). The following are the forest-wide operations master roles:
-
Schema master A domain controller that is in charge of all changes to the AD schema. As mentioned, the schema determines which object classes and attributes are used within the forest. If additional object classes or attributes need to be added, the schema is modified to accommodate these changes. The schema master is used to write to the directory’s schema, which is then replicated to other domain controllers in the forest. Updates to the schema can be performed only on the domain controller acting in this role.
-
Domain naming master A domain controller that is in charge of adding new domains and removing unneeded ones from the forest. It is responsible for any changes to the domain namespace. This role prevents naming conflicts, because such changes can be performed only if the domain naming master is online.
In addition to the two forest-wide master roles, there are three domain-wide master roles: relative ID (RID) master, primary domain controller (PDC) emulator, and infrastructure master. These roles are described in the following sections.
Relative ID Master
The relative ID master is responsible for allocating sequences of numbers (called relative IDs, or RIDs) that are used in creating new security principles in the domain. Security principles are user, group, and computer accounts. These numbers are issued to all domain controllers in the domain. When an object is created, a number that uniquely identifies the object is assigned to it. This number consists of two parts: a domain security ID (or computer SID if a local user or group account is being created) and an RID. Together, the domain SID and RID combine to form the object’s unique SID. The domain security ID is the same for all objects in that domain. The RID is unique to each object. Instead of using the name of a user, computer, or group, Windows uses the SID to identify and reference security principles. To avoid potential conflicts of domain controllers issuing the same number to an object, only one RID master exists in a domain. This controls the allocation of RID numbers to each domain controller. The domain controller can then assign the RIDs to objects when they are created.
PDC Emulator
The primary domain Controller (PDC) emulator is designed to act like a Windows NT PDC when the domain is in Windows 2000 mixed mode. This is necessary if Windows NT backup domain controllers (BDCs) still exist on the network. Clients earlier than Windows 2000 also use the PDC emulator for processing password changes, though installation of the AD client software on these systems enables them to change their password on any domain controller in the domain to which they authenticate. The PDC emulator also synchronizes the time on all domain controllers the domain. For replication accuracy, it is critical for all domain controllers to have synchronized time.
Even if you do not have any servers running as BDCs on the network, the PDC emulator still serves a critical purpose in each domain. The PDC emulator receives preferred replication of all password changes performed on other domain controllers within the domain. When a password is changed on a domain controller, it is sent to the PDC emulator. If a user changes his or her password on one domain controller, and then attempts to log on to another, the second domain controller may still have old password information. Because this domain controller considers it a bad password, it forwards the authentication request to the PDC emulator to determine whether the password is actually valid. In addition, the PDC emulator initiates urgent replication so that the password change can propagate as soon as possible. Urgent replication is also used for other security-sensitive replication traffic, such as account lockouts.
This operations master is by far the most critical at the domain level. Because of this, you should ensure that it is carefully placed on your network and housed on a high-availability, high-capacity server.
Infrastructure Master
The infrastructure master is in charge of updating changes that are made to group memberships. When a user moves to a different domain and his or her group membership changes, it may take time for these changes to be reflected in the group. To remedy this, the infrastructure master is used to update such changes in its domain. The domain controller in the infrastructure master role compares its data to the Global Catalog, which is a subset of directory information for all domains in the forest and contains information on groups. The Global Catalog stores information on universal group memberships, in which users from any domain can be added and allowed access to any domain, and maps the memberships users have to specific groups. When changes occur to group membership, the infrastructure master updates its group-to-user references and replicates these changes to other domain controllers in the domain.
| Test Day Tip | FSMO roles are an important part of a domain controller’s function on a network. FSMO roles that are unique to a forest affect all domains within that forest. FSMO roles that are unique to a domain apply only to that domain. There is only one schema master and one domain naming master in a forest. There is only one RID master, PDC emulator, and infrastructure master in a domain. |
File and Print Servers
Two of the basic functions in a network are saving files in a central location on the network and printing the contents of files to shared printers. Each of these functions is vital to most environments. Most organizations require users to be able to save their work to a shared location on the network and to print hard copies of it for others to review and/or retain. When file server or print server roles are configured in Windows Server 2003, additional functions become available that make using and managing the server more effective.
Print Servers
Print servers are used provide access to printers across the network. A benefit of print servers for administrators is that they provide an added level of manageability for network printing. Print servers allow you to control when print devices can be used by allowing you to schedule the availability of printers, set priority for print jobs, and configure printer properties. Using a browser, an administrator can also view, pause, resume, and/or delete print jobs.
By configuring Windows Server 2003 in the role of a print server, you can manage printers remotely through the GUI and by using Windows Management Instrumentation (WMI). WMI is a management application program interface (API) that allows you to monitor and control printing. Using WMI, an administrator can manage components like print servers and print devices from a command line.
Print servers also provide alternative methods of printing to specific print devices. Users working at machines running Windows XP can print to specific printers by using a Uniform Resource Locator (URL). If you’ve used the Internet, you’re probably already familiar with URLs. A URL is the address that is entered to access a Web site. Using URLs, other resources can also be accessed from remote locations, such as printers offered by Windows Server 2003 print servers.
File Servers
File servers are used to provide access to files that are stored on the server’s hard disks. Users are able to store files in a centralized location, rather than to their local hard disks, and share them with other users. When a file is saved to a volume on a file server, clients who have access to the directory in which the file was saved can access it remotely from the server. This type of server is also important when multiple employees use network-accessible applications. In such cases, data may need to be saved from the application to a shared database, spreadsheet, or other type of file.
Administrators benefit from file servers by being able to manage disk space, control access, and limit the amount of space that is made available to individual users. If NTFS volumes are used, disk quotas can be set to limit the amount of space available to each user. This prevents users from filling the hard disk with superfluous data or older information that may no longer be needed.
In addition to these features, a file server also provides other functionality that offers security and availability of data. File servers with NTFS volumes have the Encrypted File System (EFS) enabled, so that any data can be encrypted using a public key system. This makes it difficult for unauthorized users to access data, while being transparent to authorized users. To make it easier for users to access shared files, the Distributed File Service (DFS) can be used, which allows data that is located on servers throughout the enterprise to be accessible from a single shared folder. When DFS is used, files stored on different volumes, shares, or servers appear as if they reside in the same location. This makes it easier for users to find the data they need, because they do not need to search through multiple locations to access the files they are permitted to use.
DHCP, DNS, and WINS Servers
The roles of DHCP, DNS, and WINS servers are used for uniquely identifying computers and finding them on the network. A DHCP server issues a unique number called an IP address to a computer. DNS and WINS servers resolve this number to and from user-friendly names that are easier for users to deal with. With Windows Server 2003 acting as a DHCP, DNS, and/or WINS server, clients can be automatically issued a number that distinguishes them on the network, and find other machines and devices more effectively.
DHCP Servers
DHCP is the Dynamic Host Configuration Protocol, and it is used to issue IP addresses to clients on networks using the Transmission Control Protocol/Internet Protocol (TCP/IP). An IP address is a number that uniquely identifies a client when sending or receiving packets of data. When information is sent across the network, the data is broken up into smaller packets, which are reassembled by the receiver. Each packet contains the IP address of who is sending the data and who should receive it. This is similar to a letter with an address of who should receive the message and a return address of who sent it.
Because no two computers on a network can have the same IP address at the same time, assigning these addresses to clients is an important responsibility. IP addresses can be assigned statically, so that each computer always uses the same IP address. Allocating addresses in this way can result in mistakes and is difficult to consistently track. Many enterprises use static IP addresses only for their servers and network infrastructure equipment (switches, routers, and so on). Dynamic addresses are used for all clients. Dynamic addresses are assigned using DHCP. When an IP address is dynamically assigned, the client contacts the DHCP server for an IP address. The DHCP server responds by issuing an IP address from a pool of available addresses stored in a database, as well as any configuration information (such as the IP addresses of the default gateway, DNS server, and WINS server) that is needed by the client.
When a DHCP server allocates an IP address to the client, it is for a limited amount of time. Because there are only so many IP addresses available in a pool, they are often recycled between computers. This can happen if a client is shut off for an extended period of time, or if it is a laptop that is assigned to a user who is typically on the road and away from the office. For this reason, when a DHCP lease expires, the DHCP server is free to issue the IP address to other clients.
DNS Servers
Because remembering a series of numbers can be difficult, methods have been created to resolve IP addresses to user-friendly names and vice versa. Imagine trying to remember what Web site or computer the IP address 192.168.10.250 represented on a network, in addition to all the other IP addresses you would need to remember for other sites and computers. To remedy this situation, name resolution is used, so users can enter a name that is translated to a corresponding IP address.
The Domain Name System (DNS) is a popular method of name resolution that is used on the Internet and other TCP/IP networks. AD is integrated with DNS, and it uses DNS servers to allow users, computers, applications, and other elements of the network to easily find domain controllers and other resources on the network. DNS is a hierarchical, distributed database that maps user-friendly domain names (like syngress.com) to IP addresses. When a user enters a DNS name into a browser or other application, it is sent to a DNS server, which looks up the IP address for that domain. This IP address is sent back to the client, which uses the numeric address to locate and communicate with the computer at this address.
Figure 2.4 illustrates name resolution using DNS. In this example, a user wants to connect with the syngress.com domain. As shown in step 1 of this figure, because machines use IP addresses to locate and communicate with each other on a TCP/IP network, the client contacts the DNS server and requests the IP address of syngress.com. In step 2, the DNS server checks its database to find the IP address that maps to this particular domain name. After finding it, step 3 is performed, and the DNS server sends the information back to the client, informing it that the IP address of syngress.com is 209.164.15.58. Now that the client has this information, the client performs step 4, by connecting to syngress.com using the numeric address.
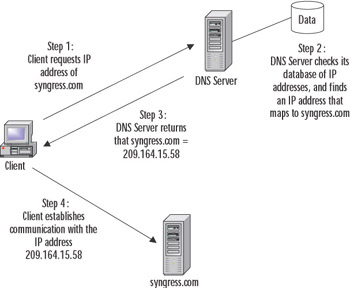
Figure 2.4: Name Resolution Using DNS
WINS Servers
The Windows Internet Name Service (WINS) is another method of name resolution that resolves IP addresses to NetBIOS names, and vice versa. NetBIOS names are used by pre-Windows 2000 servers and clients, and they allow users of those operating systems to log on to Windows Server 2003 domains. They are supported in Windows Server 2003 for backward-compatibility with these older systems. By implementing a WINS server, you allow clients to search for computers and other resources by computer name, rather than by IP address.
WINS is similar to DNS in that user-friendly names are mapped to IP addresses within a database. When clients attempt to connect to a computer or resource using its NetBIOS name, they can send a request to a WINS server to provide the IP address of that resource. The WINS server searches its database for the name-to-address mapping and returns the IP address to the requesting client. Once the client has this address, it can connect to and communicate with the computer or resource.
Web Servers
Web servers allow organizations to host their own Web sites on the Internet or a local intranet. An intranet is a local area Network (LAN) that uses the same technologies that are used on the Internet, so that users can access Web pages and other resources using Web browsers and other Web-enabled applications. Implementing a Web server in an organization allows users to benefit by accessing information, downloading files, and using Web-based applications.
Web Server Protocols
Microsoft’s Windows Server 2003 Web server product is Internet Information Services (IIS) 6.0, which is included with Windows Server 2003. IIS allows users to access information using a number of protocols that are part of the TCP/IP suite, including the following:
-
Hypertext Transfer Protocol (HTTP) Used by the World Wide Web Publishing service in IIS. Allows users to access Web pages using a Web browser like Internet Explorer or other Web-enabled applications. By connecting to sites created on your Web server, users can view and work with Web pages written in the Hypertext Markup Language (HTML), Active Server Pages (ASP), and Extensible Markup Language (XML). This allows users to not only view static information, but also to benefit from Web-based programs.
-
File Transfer Protocol (FTP) Used for transferring files between clients and servers. Using this service, clients can copy files to and from FTP sites using a Web browser like Internet Explorer or other FTP client software. By using such software, clients can browse through any folders they have access to on the FTP site, and they can access any files they have permissions to use.
-
Network News Transfer Protocol (NNTP) Used for newsgroups, which are also called discussion groups. The NNTP service in IIS allows users to post news messages. Other users can browse through messages stored on the server, respond to existing messages, and post new ones using a newsreader program. For example, a group of users could have a discussion group that deals with a certain project, so that members of the team can exchange ideas and discuss problems in a forum that can be viewed by all members of the group. Another group could also be created that allows employees to post messages regarding items for sale, charitable events, or other things that you might see on a typical bulletin board. NNTP allows organizations to incorporate such message groups into the way that employees exchange information with one another.
-
Simple Mail Transfer Protocol (SMTP) Used to provides e-mail capabilities (as described in the discussion of the mail server role later in this chapter). The SMTP service that is installed with IIS isn’t a full e-mail service, but provides limited services for transferring e-mail messages. Using this service, Web developers can collect information from users of a Web site, such as having them fill out a form online. Rather than storing the results of the form locally in a file, the information can be e-mailed using this service.
Web Server Configuration
Although a Web server can facilitate a company’s ability to disseminate information, it isn’t an actual role that is configured using the Configure Your Server Wizard. It is installed as part of the application server role, which we’ll discuss later in this chapter. The Configure Your Server Wizard provides an easy, step-by-step method of configuring Web servers through the application server role; however, it isn’t the only way to install IIS. You can also install IIS through the Add or Remove Programs applet in the Windows Control Panel.
Using Add or Remove Programs to install IIS takes a few extra steps, but it allows you to perform the installation without installing other services and features available through the application server role. To use Add or Remove Programs to install IIS, follow these steps:
-
Select Start | Control Panel | Add or Remove Programs.
-
Click the Add/Remove Windows Components icon to display the Windows Components Wizard, which provides a listing of available components to install.
-
In the list, select Application Server and click the Details button to view the Application Server dialog box, shown in Figure 2.5.
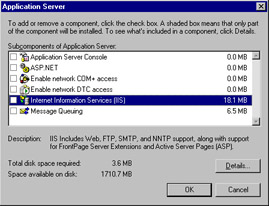
Figure 2.5: Installing IIS through the Application Server Dialog Box in the Windows Components Wizard -
The Application Server dialog box contains a number of subcomponents. To install IIS, select the check box for Internet Information Services (IIS), and either click OK to install the default components or click Details to view even more subcomponents that can be installed within IIS.
-
When you’ve made your selections, click OK to return to the Windows Components Wizard.
-
Click Next to have Windows make the configuration changes you requested from your selection.
-
Once the Wizard has finished copying the necessary files and changing system settings, click Finish to complete the installation process and exit the Wizard.
Database Servers
Database servers are used to store and manage databases that are stored on the server and to provide data access for authorized users. This type of server keeps the data in a central location that can be regularly backed up. It also allows users and applications to centrally access the data across the network. A large number of the databases used in your organization can be kept on one server or a group of servers that are specifically configured to protect data and service client requests.
The Configure Your Server Wizard does not include a configurable role for database servers. A database server is any server that runs a network database application and maintains database files, such as Microsoft SQL Server or Oracle. SQL Server is a high-performance database management system. It is used for data storage and analysis, and it provides users with the ability to access vast amounts of data quickly over the network. Because SQL Server provides additional measures of security that would not otherwise be available (as discussed in the “Securing Database Servers” section later in this chapter) and processing occurs on the server, transactions can occur securely and rapidly.
Data stored in database management systems is generally accessed through user interfaces that are developed by an organization or third parties. For example, a company might create custom applications in Visual Basic (or some other programming language), or use ASP on the Web server to display information that is stored in a database. While the user interacts with the data through the user interface, the data is actually stored in the SQL Server or Oracle database located on a database server.
Mail Servers
Mail servers enable users to send and receive e-mail messages. Users send e-mail to other users through at least one mail server. When the message arrives, the destination mail server stores the message until it is retrieved by the user. If the mail server does not handle the e-mail account for an intended recipient, it will transfer the message to a mail server that does. In this way, mail servers will work together to ensure a message reaches its intended audience.
When a server is configured to be a mail server, two protocols are enabled: SMTP and Post Office Protocol (POP3). As shown in Figure 2.6, SMTP is used by clients and mail servers to send e-mail. POP3 is used by clients when retrieving e-mail from their mail server. Each of these protocols is part of the TCP/IP protocol suite and installed when TCP/IP is installed on a computer. However, even if TCP/IP is installed on Windows
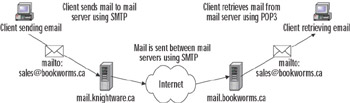
Figure 2.6: How E-mail Is Transmitted and Retrieved
Server 2003, the services provided by mail servers still need to be enabled by configuring the machine to take the role of a mail server.
E-mail addresses determine which mail server and client the e-mail should go to. Each e-mail address uses the format of account@domain. The first part of the address specifies the account the e-mail is destined to reach, and the second part specifies the domain in which this account resides. In the example in Figure 2.6, a message destined for sales@bookworms.ca is sent from the knightware.ca domain. Because the mail server in knightware.ca recognizes that the message is being sent to a user in another domain, it uses the SMTP protocol to send it to the mail server in the bookworms.ca domain. When the bookworms.ca mail server receives this e-mail, it will see it is for the account named sales and put it in the mailbox for that user. The client that uses the sales account can then use the POP3 protocol to retrieve his or her e-mail from the mail server.
Certificate Authorities
Certificate authorities (CAs) are servers that issue and manage certificates. Certificates can be used for a variety of purposes, including encryption, integrity, and verifying the identity of an entity, such as a user, machine, or application. Certificates can be used to prove an entity is who (or what) they claim to be, in much the same way that your birth certificate is used to prove your identity. They are digitally signed files that contain data a wide range of information, often including a cryptographic key, information about whom or what the key is issued to, an expiration date, where the validity of the certificate can be checked, and which CA signed the certificate. Certificates are typically part of a larger security process known as a Public Key Infrastructure (PKI).
PKI
PKI is a method that uses unique identifiers called keys, which are mathematical algorithms used for cryptography and authentication. There are two different kinds of keys used in PKI: public keys and private keys.
For data confidentiality, the public key is used to encrypt session keys and data; the private key is used for decryption. The public key is openly available to the public. The private key is secret and known only to the person for whom it is created. The members of a key pair are mathematically related, but you cannot extrapolate the private key by knowing the public key. Using the two keys together, messages can be encrypted and decrypted using PKI.
For authentication, the roles of the public and private keys are reversed. The private key is used for encryption, and the public key is used for decryption. The private key is unique to the person being identified, so each user has his or her own private key for authentication purposes. Because each private key has a corresponding public key, the public key is used to decrypt information used for authenticating the user.
The public and private keys are generated at the same time by a CA. The CA creates and manages keys, binding public and private keys to create certificates, and vouching for the validity of public keys belonging to users, computers, services, applications, and other CAs.
In addition to a CA, a registration Authority (RA) can also be used to request and acquire certificates for others. The RA acts as a proxy between the user and the CA, and it relieves the CA of some of the burden of verification. When a user makes a request to a CA, the RA can intercept the request, authenticate it, and pass it on to the CA. When the CA responds to the request, it sends it to the RA, which forwards it to the user.
Private and public keys are created when someone or something needs to establish the validity of his, her, or its identity. When the public and private keys are created, the private key is given to the person or entity who wants to establish the credentials, and a public key is stored so that anyone who wants to verify these credentials has access to it. When a person wants to send a message using PKI with the data encrypted so that it cannot be read by anyone but the holder of the private key, the public key is acquired from the CA and used to encrypt the message. When a person who holds the private key receives this message, the public key is validated with the CA. Since the CA is trusted, this validates the authenticity of the message. After this is done, the private key is used to decrypt the message.
Conversely, if a person wants to send a message and validate that he or she is the actual sender, that person can encrypt the message with his or her private key. Then the recipient decrypts it with the sender’s public key, thereby proving that the message really did come from that sender.
Certificates
Certificates use PKI by binding the value of a public key to the person or thing that holds the private key. The certificate stores information that identifies its holder and contains a copy of the key value. When communicating with another party that has a corresponding key, data exchanged between the two can be securely transmitted using encryption.
Certificates may be used for a number of different purposes. Windows 2003 Server computers acting in the role of a Web server may use certificates to authenticate users or to authenticate Web servers themselves. In doing so, the certificate provides proof of the identity of a particular user or machine. Mail servers can also benefit from certificates, because they are used to allow e-mail to be digitally signed. This provides proof of the integrity and origin of a message. In sending secure mail, certificates are used with Secure/Multipurpose Internet Mail Extensions (S/MIME), which allows the e-mail to be sent encrypted across a network.
Certificates may also be used by different protocols to ensure secure communication, as in the case of Internet Protocol Security (IPSec) or Transport Layer Security (TLS). Encrypting communication between clients and servers with these protocols allows data to be transmitted and users to be authenticated with little (or no) chance of others intercepting and viewing the information. By using certificates for authentication, encryption/decryption of data, and secure communication, Windows 2003 Servers Certificate Services can provide enhanced security to a network.
Certificates can contain a variety of facts about a user’s or machine’s identity and about the certificate itself. Data included in a certificate may include the following:
-
The value of a key issued by a CA
-
Information about the person, machine, or other entity that was issued the certificate, which may include their name, e-mail address, or other data
-
Information about who issued the certificate
-
The digital signature of the issuer, which ensures the certificate is valid
-
How long the certificate is valid
Because different systems must be able to understand the format of a certificate, specific standards are used in the generation of a certificate. Windows 2003 Server supports X.509, which is a standard that specifies the syntax and format of digital certificates. X.509 is a popular standard for digital certificates, published by the International Organization for Standardization (ISO). It dictates how information is organized in the certificate and what information is included. An X.509 certificate includes facts about the user to whom the certificate was issued, information about the certificate itself, and can also include information about the issuer of the certificate (who is referred to as the CA). To prevent the certificate from being used indefinitely, it also contains information about the period for which the certificate is valid.
Certificate Services
Certificate Services is used to create a CA on Windows Server 2003 servers in your organization. With Certificate Services, you can create a CA, format and modify the contents of certificates, verify information provided by those requesting certificates, issue and revoke certificates, and publish a Certificate Revocation List (CRL). The CRL is a list of certificates that are expired or invalid, and it is made available so that network users can identify whether certificates they receive are valid.
Certificate Services supports implementing a hierarchy of CAs, so that a single CA isn’t responsible for providing certificates to the entire network or authenticating the entire intranet or Internet. This isn’t to say that multiple CAs must be used in an organization, but it is one possibility. Using a hierarchy of CAs is called chaining, where one CA certifies others. In this hierarchy, there is a single root authority and any number of subordinate CAs.
A root authority (or root CA) resides at the top of the hierarchy. Because the hierarchy uses a parent-child relationship, all subordinate CAs reside beneath the root authority. The root CA is the most trusted CA in the hierarchy—any clients that trust the root CA will also trust certificates issued by any CA below it. This makes securing a CA vital (as discussed in the “Securing CAs section later in this chapter).
Subordinate CAs are child CAs in the hierarchy. They are certified by the root authority and bind its public key to its identity. Just as the root CA can issue and manage certificates and certify child CAs, a subordinate CA can also perform these actions and certify CAs that are subordinate to it in the hierarchy.
In addition to having different levels of CAs in an organization, there are also different types of root and subordinate CAs that can be used. Enterprise CAs use AD to verify information that is provided when requesting a certificate and to store certificates within AD. When the certificate is needed, it is retrieved from directory services. Stand-alone CAs can be used in environments that do not use AD (CAs do not require AD).
As with IIS, Certificate Services isn’t an actual role that can be set up with the Configure Your Server Wizard. Instead, you must follow these steps:
-
Select Start | Control Panel | Add or Remove Programs.
-
Click Add/Remove Windows Components to display the Windows Components Wizard, which provides a listing of available components to install.
-
In the list of available components, click the check box beside the Certificate Services item so it is checked. A warning message will appear, stating that after Certificate Services is installed, the name of the machine cannot be changed. This is because the server’s name is bound to the CA information stored in AD, and any changes to the name or domain membership would invalidate certificates issued by this CA.
-
Click Yes to continue with the installation. (Clicking No will cancel it.)
-
You are presented with the window shown in Figure 2.7, which allows you to specify the type of CA that will be set up. As mentioned earlier, you have the option of creating an enterprise root CA, an enterprise subordinate CA, a stand-alone root CA, or a stand-alone subordinate CA.
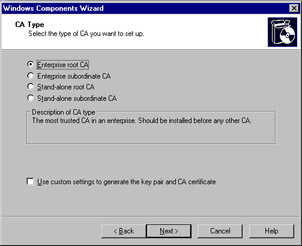
Figure 2.7: Choosing a CA Type in the Windows Components Wizard -
For this example, we will assume that this is the first CA being created and AD is used. Select Enterprise root CA and click Next
-
You are then presented with a window shown in Figure 2.8, which allows you to provide information to identify the CA you’re creating. Enter a common name and distinguished name suffix for the CA. Distinguished names are used to provide each object in AD with a unique name. A distinguished name represents the exact location of an object within the directory. This is comparable to a file being represented by the full path, showing where it is located on the hard disk. With an object in the directory, several components are used to create this name:
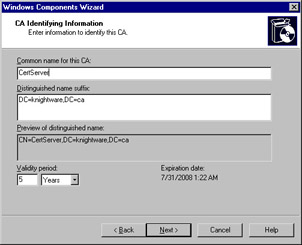
Figure 2.8: Entering CA Identifying Information in the Windows Components Wizard-
CN, which is the common name of the object, and includes such things as user accounts, printers, and other network elements represented in the directory.
-
OU, which is the Organizational Unit. OUs are containers in the directory, which are used to hold objects. To continue with our example of files on a hard disk, this would be comparable to a folder within the directory structure.
-
DC, which is a domain component. This is used to identify the name of the domain or server, and the DNS suffix (for example .com, .net, .edu, .gov, and so forth).
When combined, these components of a distinguished name are used to show the location of an object. In the case of the CA being created here, the common name is CertServer, and the distinguished name suffix is the domain components. This makes the distinguished name CN=CertServer,DC=knightware,DC=ca, which you can see in the preview in Figure 2.8.
-
-
Optionally, you can change the Validity period of certificates issued by the CA. As shown in Figure 2.8, the default validity period is five years. You can modify this by specifying a different number and whether the period is in Years, Months, Weeks, or Days.
-
Click Next when you are finished entering CA identifying information.
-
This will bring you to the Certificate Database Settings window, shown in Figure 2.9, where you can specify the location of the certificate database and log file. By default, the database and log are named after the common name you specified for the CA, and each is stored in the System32 folder of the %systemroot% (for example, C:\Windows\System32). Click Next to continue.
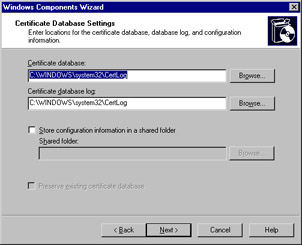
Figure 2.9: Choosing Certificate Database Settings in the Windows Components Wizard -
A message box will appear informing you that IIS must be stopped before installation can continue. Clicking No will return you to the previous window. Clicking Yes will stop the service and cause Windows to make the configuration changes you requested from your selection. If ASP is not enabled on the machine, a message box will interrupt the process, asking if you want to enable ASP. Clicking Yes will enable ASP and continue the installation.
-
After the Wizard has finished copying the necessary files and changing system settings, click Finish to complete the installation process.
Application Servers and Terminal Servers
Application servers and terminal servers provide the ability for users to access applications over the network. Rather than running solely on the client’s machine, all or parts of these programs run on the server. This frees resources on the client machine and enables users to benefit from newer application technologies.
Application Servers
Application servers allow users to run Web applications and distributed programs from the server. Web applications are programs that use Internet technologies to provide functionality and are accessible across networks and the Internet using Web browsers like Internet Explorer. These programs are often created using ASP or XML. Applications can be created in a wider variety of programming languages (such as Perl, Visual Basic, and Visual C++). Distributed applications divide the program so that part of it runs on the client while the rest runs on one or more servers. For example, a distributed program might have a user interface that is installed on the client’s machine, which allows the user to access a SQL Server database. In reality, the program might access a number of other network-aware programs, which correlate data from a number of different database systems and return it to the client. By using the application server role, the server is configured to provide greater reliability and performance to these applications.
Because Web applications require Internet technologies, when Windows Server 2003 is set up as an application server, IIS subcomponents such as ASP can be installed. As explained earlier in this chapter, IIS is a Web server that comes with Windows Server 2003 and can be used to make Web applications available to users on the network. If IIS has been installed, the application server role will appear as a configured role in the Manage Your Server tool. This is despite the fact that only some components for the application server role have been installed. To modify the installed components, you can either use the Windows Components Wizard or the Configure Your Server Wizard.
As an example of configuring a server role, in Exercise 2.1, we will set up an application server in Windows Server 2003.
Exercise 2.01: Adding an Application Server Role to Windows Server 2003
-
Select Start | Administrative Tools | Manage Your Server.
-
When Manage Your Server starts, click the Add or remove a role button.
-
When the Configure Your Server Wizard starts, read through the information on the Preliminary Steps window, and then click Next.
-
After the Wizard checks your network settings and operating system version, the Server Role window will appear. From the list, select Application server (IIS, ASP.NET), as shown in Figure 2.10. Then click Next to continue.
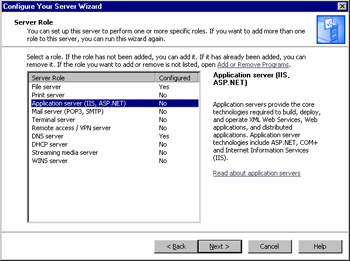
Figure 2.10: Choose the Application Server Role -
The Application Server Options window appears, as shown in Figure 2.11. Here, you can add components that are used with IIS. Note that IIS will be installed regardless of what you select on this page. Select the FrontPage Server Extensions check box to add Web server extensions that allow content created with FrontPage, Visual Studio, and Web Folders to be published to the IIS Web site. Select Enable ASP.NET to allow Web-based applications created using ASP.NET to be used on the site. After selecting the options you wish to add, click Next to continue.
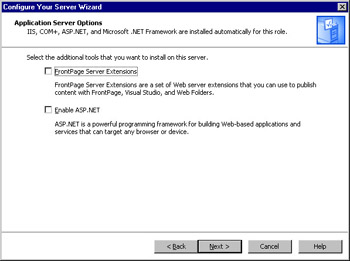
Figure 2.11: Select Application Server Options -
The Summary of Selections window, shown in Figure 2.12, provides a list of components that will be installed as part of the application server configuration. Review these settings, and then click Next to begin installing these components.
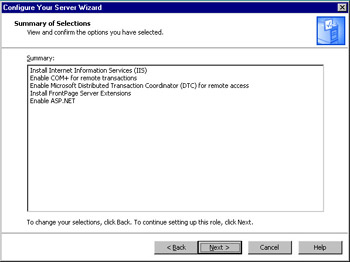
Figure 2.12: Review the Summary of Selections -
After copying files, the Windows Components Wizard will open and continue the installation. Once it has completed, you will be returned to the Configure Your Server Wizard. Click Finish to complete the installation.
Terminal Servers
Terminal servers allow remote access to applications using thin-client technology. This makes the user’s machine act as a terminal emulator (similar to the concept of a dumb terminal). The user connects to the terminal server using client software installed on their machine, logs on to the Terminal Services session, and is presented with a user interface (normally a Windows Server 2003 desktop). Keystrokes and mouse clicks generated by the user at the client are sent to the terminal server. Updated screen images are sent back from terminal server to the client system. When working in a session, the user is essentially working at the server. All processing is occurring at the server, which is being interacted with through the client software.
A benefit of Terminal Services is that users can run programs that they might otherwise be unable to use. For example, a user running an older version of Windows might need to use Office XP, but she doesn’t have the minimal requirements install it. Through Terminal Services, she can connect and be presented with a Windows Server 2003 desktop. If Office XP is installed on the terminal server, the user can open and use the application. Because all processing is actually occurring on the server, the user can run applications that are impossible to install on her local system.
There are a wide variety of clients that can use Terminal Services. Client software is available for Windows 3.11 and later, as well as Macintosh and UNIX. Internet Explorer can also be used to access a terminal server, using the Web client software.
|
EAN: 2147483647
Pages: 173