Planning a Server Security Strategy
|
EXAM 70-293 OBJECTIVE 1, 1.1
The only truly secure network is one that is totally inaccessible. No one would be able to misuse applications, damage equipment, delete data, or mistakenly modify information. In providing this level of security, however, the network would also become useless, because it could not provide the services and resources needed by users. Security is always a trade-off between usability and protection. When planning security, you need to find an acceptable balance between the need to secure your network and the need for users to be able to perform their jobs.
In creating a security plan, it is important to realize that the network environment will never be completely secure. If people are willing to invest enough time, effort, and money into hacking a system, they will probably find a way in. The goal is to make it difficult for intruders to obtain unauthorized access, so it isn’t worth their time to try or continue attempting to gain access. It is also critical to protect servers from potential disasters and to have methods to restore systems if they become compromised.
A good security plan considers the needs of a company and tries to balance it with their capabilities and current technology. As you’ll see in the sections that follow, this means identifying the minimum security requirements for an organization, choosing an operating system, and identifying the configurations necessary to meet these needs. To develop a security plan, you must identify the risks that potentially threaten a network, determine what countermeasures are available to deal with them, figure out what you can afford financially, and implement the countermeasures that are feasible.
Choosing the Operating System
EXAM 70-293 OBJECTIVE 1.4
In planning a strategy for server security, you will need to determine which operating systems will be used in the organization. Different network operating systems provide diverse features that can be used as part of your security strategy. If you’re setting up a new network and need to choose a server operating system, or you’re unfamiliar with what operating systems are used on an existing network, you will not know what features can be used for managing and maintaining security.
Of course, there are non-Microsoft network operating systems available to use on your server, but we will consider only the following Windows server systems here:
-
Windows NT Server 4
-
Windows 2000 Server
-
Windows 2000 Advanced Server
-
Windows 2000 Datacenter
-
Windows Server 2003 Standard Edition
-
Windows Server 2003 Enterprise Edition
-
Windows Server 2003 Datacenter Edition
-
Windows Server 2003 Web Edition
One of the first considerations for the operating system you choose will be the minimum system requirements for installing the operating system. Obviously, if your existing server cannot handle a particular version of Windows, you will not be able to install it. If this is the case, you will need to upgrade the hardware, purchase a new server to support the operating system you want, or choose an operating system that does match the current server’s hardware. The minimum system requirements for Windows server operating systems are shown in Table 2.1.
| Server | Computer/Processor | Memory (RAM) | Hard Disk | CPU Support |
|---|---|---|---|---|
| Windows NT Server 4 | 486/33 MHz or higher/Pentium, or Pentium Pro processor | 16MB; 32MB recommended | Intel and compatible systems: 125MB available hard disk space minimum. RISC-based systems: 160MB available hard disk space | Up to 4 CPUs (retail version); Up to 32 CPUs available from hardware vendors |
| Windows 2000 Server | 133 MHz or higher Pentium-compatible CPU | At least 128MB: 256MB recommended; 4GB maximum | 2GB with 1GB free space; additional free space required for installing over a network | Up to 4 CPUs |
| Windows 2000 Advanced Server | 133 MHz or higher Pentium-compatible CPU | At least 128MB; 256MB recommended; 8GB maximum | 2GB with 1GB free space; additional free space required for installing over a network | Up to 8 CPUs |
| Windows 2000 Datacenter | Pentium III Xeon processors or higher | 256MB | 2GB with 1GB free space; additional free space required for installing over a network | 8-way capable or 64 higher server ( ports up to 32-way) |
| Windows Server 2003 Standard Edition | 133 MHz | 128MB | 1.5GB | Up to 4 CPUs |
| Windows Server 2003 Enterprise Edition | 133 MHz for x86-based computers; 733 MHz for Itanium-based computers | 128MB | 1.5GB for x86-based computers; 2GB for Itanium-based computers | Up to 8 CPUs |
| Windows Server 2003 Datacenter Edition | 400 MHz for x86-based computers; 733 MHz for Itanium-based computers | 512MB | 1.5GB for x86-based computers; 2GB for Itanium-based computers | Minimum 8-way capable machine required; maximum |
| Windows Server 2003 Web Edition | 133 MHz | 128MB | 1.5GB | Up to 2 CPUs |
| Note | All of the Windows server operating systems also require a CD-ROM or DVD drive (except Window NT Server 4, which does not use a DVD drive), VGA or higher resolution monitor, keyboard, and mouse. |
Beyond the minimum requirements, you will need to look at the features available in different versions and editions of Windows, and how they can be used to enhance network security. The progression from one version to another has offered improvements and additions to security, with Windows Server 2003 offering the most security features. By identifying which features are necessary for your organization, you can create a network that provides the necessary functionality and security.
Security Features
Windows 2000 offers a number of new security features that were not previously available in Windows NT. Many of the features we’ll discuss next were implemented in Windows 2000 and have been updated in Windows Server 2003. In addition, new features have been added that make Windows Server 2003 the most secure Windows server product Microsoft has ever marketed.
Windows 2000 Server was the first version to provide encryption of data over the network and in the file system. IPSec allows encryption of data across the network. EFS uses a public key system to encrypt data on hard disks. Encryption ensures that unauthorized parties are unable to view the data if they gain access to it.
Windows 2000 was also the first version to provide built-in support for smart cards. Smart cards are generally the size of a credit card and have the ability to store data. When a smart card is inserted into a smart card device, it provides information that can be used for authentication and other purposes. With smart cards, the security of a network can be greatly enhanced because it is necessary to physically possess the card to log on.
A major advance that first appeared in Windows 2000 was Kerberos authentication. Kerberos version 5 is an industry-standard security protocol that uses mutual authentication to verify the identity of a user or computer, as well as the network service that is being accessed. In Windows 2000 Server and later, Kerberos is the default authentication service.
With Kerberos, each party to a transaction proves that they are who they claim to be through the use of tickets. A Kerberos ticket is encrypted data that is issued for authentication. Tickets are issued by a Key Distribution Center (KDC), which is a service that runs on every domain controller. When a user logs on, the user authenticates to AD using a password or smart card. Because the KDC is part of AD, the user also authenticates to the KDC and is issued a session key called a ticket granting ticket (TGT). The TGT is generally good for as long as the user is logged on and is used to access a ticket-granting service that provides another type of ticket: service tickets. A service ticket is used to authenticate to individual services by providing a ticket when a particular service is needed.
As mentioned earlier in this chapter, AD is a directory service that was first introduced in Windows 2000 Server. Because AD was not available when Windows NT 4 was released, it cannot be installed on a Windows NT server. Once AD is installed on Windows 2000 Server or Windows Server 2003, the server becomes a domain controller that can be used for authentication and management of user accounts and other objects in AD.
When AD is installed, a number of features and tools become available. There are three graphical tools that can be used with Windows 2000 Server or Windows Server 2003:
-
Active Directory Users and Computers This utility allows you to administer user and computer accounts, groups, printers, OUs, contacts, and other objects stored in AD. Using this tool, you can create, delete, modify, move, organize, and set permissions on these objects.
-
Active Directory Domains and Trusts This utility allows you to manage domains and the trust relationships between them. Using this tool, you can create, modify, and delete trust relationships; create and remove user principal name (UPN) suffixes; raise the domain mode (Windows 2000 Server only); and raise domain and forest functional levels (Windows Server 2003 only).
-
Active Directory Sites and Services This utility allows you to create and manage sites, and control how the directory is replicated within a site and between sites. Using this tool, you can specify connections between sites and how they are to be used for replication.
Exam Warning Active Directory Users and Computers, Active Directory Domains and Trusts, and Active Directory Sites and Services are tools that are installed with AD. These tools are not available on servers that have not been configured as domain controllers. They are the primary tools for interacting with AD, and they allow you to configure different aspects of the directory.
A new feature in Windows Server 2003 is that AD allows you to select multiple user objects, so that you can change the attributes of more than one object at a time. After selecting two or more user objects in Active Directory Users and Computers, you can bring up the properties and modify some of the attributes that are common to each of these objects. This makes it faster to manage users, because you do not need to make changes to one account at a time.
Windows Server 2003 AD also provides the ability to drag and drop objects into containers. To use this feature, select an object with your mouse, hold down your left mouse button to drag the object to another location (such as an OU), and release the button to drop the object into the container. This ability also makes it easy to add user and group objects to groups. Dragging and dropping a security principle’s object (user, computer, or group) into a group adds it to the group membership.
In addition to these graphical tools, Windows Server 2003 also provides a number of command-line utilities for managing AD. Using these tools, you can perform management tasks through the textual interface of the command prompt. These tools allow administrators to manually enter commands to run operations from a command prompt or use the commands in batch files and scripts that can be scheduled to run at specific times.
Another new Windows Server 2003 feature is that domain controllers can be created from backups. Backups are used to copy data to other media, such as tapes, and can be used to restore lost data if problems arise. For example, if the hard drive on a server fails, you can use the backup to restore the data to a new drive and have the server up and running again. This same process can be used to restore AD to a new domain controller, so you do not need to replicate the entire directory across the network. Allowing domain controllers to be added to an existing domain through the use of backups is of great benefit when you are setting up a new domain controller across a slow WAN link from the nearest existing domain controller.
Functional Levels
When a Windows Server 2003 domain controller is created on a network, AD is installed with a basic set of features. Additional features can be enabled, depending on the operating systems running as domain controllers and the functional level that is configured for the domain or forest.
| Note | Windows 2000 contained two modes: mixed and native. In Windows Server 2003, these are now called functional levels, but they remain unchanged. Just as Windows 2000 installed in mixed mode, Windows Server 2003 installs in the Windows 2000 mixed functional level. In Windows 2000, there was only one level of forest operation. Modes existed only at the domain level. With Windows Server 2003, there are domain functional levels and separate forest functional levels. In order to raise the forest functional level, the functional level of all domains in the forest must be set to the appropriate level. |
Domain Functional Levels
The domain functional level determines which servers are supported in a domain and the features that are available in AD. When one or more Windows 2003 Server computers are installed on a domain, the domain functional level can be set for AD. At lower levels, older versions of Windows servers can still be used in the domain, but more advanced features for AD are sacrificed. At the highest level, only Windows 2003 Server machines can be used in the domain, and a full set of these advanced features become available. By not setting the domain functionality to an appropriate level, you may be forfeiting a number of the features you need for your network.
There are four different levels of functionality for AD:
-
Windows 2000 mixed Allows domains to contain Windows NT Backup domain Controllers (BDCs) that can interact with the PDC emulator in a Windows Server 2003 AD domain. In this level, the basic features of AD are available. However, you cannot use additional group nesting, universal security groups, or security ID histories (SIDHistory) when moving accounts between domains. Because it accommodates the widest variety of domain controllers on your network, this is the default level of functionality when a Windows Server 2003 domain controller is installed.
-
Windows 2000 native The highest mode available for Windows 2000 and the next highest level for Windows Server 2003 domain controllers. This functional level removes support for replication to Windows NT BDCs, so these older servers are unable to function as domain controllers. In this level, only Windows 2000 and Windows Server 2003 domain controllers can be used, and support for universal security groups, SIDHistory, and group nesting becomes available.
-
Windows Server 2003 interim New in Windows Server 2003, this level is used when your domain consists of Windows NT and Windows Server 2003 domain controllers. It provides the same functionality as Windows 2000 mixed mode, but is used when you are upgrading Windows NT domains directly to Windows Server 2003. If a domain has never had (and will not have) Windows 2000 domain controllers, this is the level used for performing an upgrade.
-
Windows Server 2003 The highest functionality level for AD, this level is used when there are only Windows Server 2003 domain controllers in the domain. When this level is set for the domain, a number of additional features are enabled, which we’ll discuss shortly.
If you’re upgrading from Windows 2000 Server on your network, you’re probably familiar with the first two levels. Each of these appeared in Windows 2000 and allowed control of which operating systems were supported and the features that were available in AD. Windows 2000 mixed mode provides backward-compatibility with older operating systems like Windows NT 4, allowing Windows NT BDCs to still be used in a domain. Windows 2000 native mode restricted the domain to using only Windows 2000 Server machines on the network, and it provided an expanded feature set for AD. In Windows 2003 Server, these modes are now referred to as functional levels, and they allow Windows 2003 Server to provide backward-compatibility to domain controllers using these operating systems. In addition to these functional levels, Windows 2003 also introduces two new domain functional levels that were not available in the previous versions: Windows Server 2003 interim and Windows Server 2003.
The tool used to raise domain and forest functional levels is Active Directory Domains and Trusts. To raise a domain level, right-click the domain in the left console pane and click Raise Domain Functional Level in the context menu. The Raise Domain Functional Level dialog box appears, as shown in Figure 2.13. Select the functional level that you want, and then click Raise.
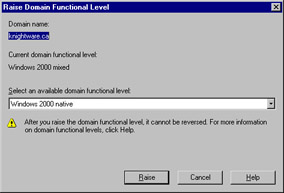
Figure 2.13: Raising the Domain Functional Level
When raising the domain functional level, it is important to remember that it is a one-way change. After raising the level, you cannot lower it. For example, if you raise the domain from Windows 2000 mixed to Windows Server 2003, you cannot return the level to Windows 2000 mixed again. This means that you cannot add Windows NT BDCs or Windows 2000 domain controllers to the domain after the upgrade. If you attempt to change the domain functional level after raising it to Windows Server 2003, a dialog box similar to the one shown in Figure 2.14 will be displayed.
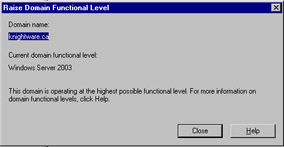
Figure 2.14: Attempting to Change a Domain Functional Level After Raising the Functional Level
After all domain controllers are running Windows Server 2003 and the domain functional level has been raised to Windows Server 2003, new features are automatically available. One such feature is the domain controller renaming tool, which allows you to rename a domain controller without needing to demote it first. This can be useful when you need to restructure the network or simply wish to use a more meaningful name for a particular domain controller. When you use this tool, AD and DNS entries for the renamed domain controller are automatically updated.
| Note | You can also rename domains using the domain rename utility (rendom.exe). Using this tool, you can change the NetBIOS and DNS names of a domain, including any child, parent, domain tree, or forest root domains. By renaming domains, you can move them in the DNS hierarchy. For example, you can change the name of dev.web.syngress.com to dev.syngress.com, placing the web.syngress.com and dev.syngress.com domains on the same level of the hierarchy. You can even rename a domain so that it becomes part of a completely different domain tree. The only domain that you cannot reposition in this manner is the forest root domain. |
The Windows Server 2003 domain functional level also provides a new attribute for user and computer accounts. The lastLogonTimestamp is added to user and computer objects, and it is replicated within the domain to all domain controllers, so that the last time these accounts were used to log on to the domain can be recorded. This way, a history of the user or computer account is created.
Another feature that becomes enabled when the domain functional level is raised is the ability to add a password to InetOrgPerson accounts. InetOrgPerson is an object class in AD that is used to create accounts that represent users in non-Microsoft directory services, and it is used in the same way as a user object. Other network operating systems, such as Novell NetWare, use their own implementations of a directory service, which are not always compatible with AD. InetOrgPerson is used to assist applications written for other directories or when migrating from these directory services to AD. Object classes are sets of attributes used to determine which attributes an object may have when it is created. Using the InetOrgPerson class, you can create a type of user account that is compatible with accounts from other directory services.
The features we’ve covered so for are only available in the Windows Server 2003 functional level. However, other features for the Windows Server 2003 level may also be available when lower functional levels are implemented. Windows 2000 native and Windows Server 2003 functional levels provide the ability to nest security and distribution groups in one another. Security groups are used to assign permissions and rights to groups of accounts, rather than modifying each account individually. Distribution groups are used to send bulk e-mail to large groups of users as a single entity. By nesting groups, one group can be added as a member of another group, saving the need to repeatedly add the same accounts to the membership of various groups.
Limited group nesting is available for domains running in Windows 2000 mixed mode. When this functional level is used, group nesting for distribution groups is allowed, but there is limited support for security groups. You can nest security groups only if you are adding global groups to the membership of domain local security groups. Aside from this, nesting isn’t permitted.
InetOrgPerson Object Class
The InetOrgPerson object class and the attributes it contains originate from RFC 2798. RFC is an acronym for Requests for Comments, and is a document that is used to specify information and/or technical specifications. RFC 2798 was created by the Internet Engineering Task Force (IETF) to address the need for a class of user that accessed directory services over the intranet or Internet. This class of user was designed to hold attributes about people who accessed the directory using the Lightweight Directory Access Protocol (LDAP) in this way.
Because of the need for this type of user class, Microsoft provided a kit that added an InetOrgPerson object class to the schema in Windows 2000. The schema is part of AD and defines the classes of objects and the attributes that can be used in AD. In Windows Server 2003, an InetOrgPerson object class is included in the AD schema as a type of user class that can be used by LDAP applications that require this type of object and when migrating to AD from other directory services. This saves administrators from needing to extend the schema to create a new InetOrgPerson object class.
Another benefit of the Windows 2000 native or Windows Server 2003 functional level is that universal security groups can be used. (Domains that have the functional level set to Windows 2000 mixed do not allow universal security groups to be created.) Universal security groups can contain accounts and groups from any domain in the forest, and they can also be assigned permissions to resources in any domain in the forest. In this situation, the group can contain user accounts, global groups, and universal groups from any domain in the forest, and it can be assigned permissions to resources in any domain. Universal distribution groups can be used at any functional level, including Windows 2000 mixed.
In summary, some features are available but limited in the Windows 2000 mixed functional level. In other cases, however, support for a particular feature isn’t available at all. Windows 2000 native or Windows Server 2003 functional levels provide the ability to convert groups. Each of these higher functional levels allows conversion between security groups and distribution groups. In addition, the Windows 2000 mixed functional level does not support SIDHistory, which allows user and computer accounts to be moved from one domain to another without affecting existing permissions. By failing to raise the functional level of a domain, you make several features unavailable to it.
Forest Functional Levels
In addition to the domain functional level, you can also set the functional level of a forest. A domain functional level is individually set for each domain. The forest functional level is set for the entire forest and thereby affects all domains within that forest. There are three different forest functional levels:
-
Windows 2000
-
Windows Server 2003 interim
-
Windows Server 2003
By default, the functional level of a forest is set to Windows 2000. The Windows 2000 forest functional level allows Windows NT, Windows 2000, and Windows Server 2003 domain controllers on the network. However, it also provides fewer features than the higher functional levels. Elevating the functional level of a forest enables additional features. At the Windows Server 2003 interim level, domain controllers running Windows NT Server 4 and Windows Server 2003 can exist within the forest. This level is used when directly upgrading from Windows NT 4 to Windows Server 2003. When the default level is raised to Windows Server 2003, additional features in AD become available.
To raise the forest functional level, all domains in the forest must consist only of domain controllers running Windows Server 2003. In addition, the functional level of all domains must be set to Windows 2000 native or higher. After the functional level has been raised, all domains will have their functional level set at Windows Server 2003, even if it was set at Windows 2000 native prior to the forest level being elevated.
Like domain functional levels, forest functional levels are raised using Active Directory Domains and Trusts. As shown in Figure 2.15, this tool has an Active Directory Domains and Trusts node in the left pane. Right-click this node and click Raise Forest Functional Level in the context menu. You will see a dialog box that is similar to the one for raising the domain functional level (see Figure 2.14). Select the new functional level from the drop-down list, and then click Raise to complete the task.
Figure 2.15: Using Active Directory Domains and Trusts
As with domain functional levels, raising the forest functional level is a one-way change. After raising the level, you cannot lower it. Therefore, it is important that you decide which domain controllers exist on your network or may be added in the future prior to raising the level. If older operating systems are used for domain controllers in the forest, you will need to upgrade them before raising the level, and you will not be able to add these older systems after you make this change.
By raising the functional level to Windows Server 2003, new features become available to the forest. One such feature is the ability to create forest trusts. Forest trusts are one or two-way transitive trust relationships between two different forests. A trust relationship allows pass-through authentication, so users who are authenticated in a trusted domain can use resources in a trusting domain. Because the trust between a parent and child domain is bidirectional, meaning that both domains trust one another, users in each domain can access resources in the other domain. This expands the network, so users are able to use services and resources in both forests.
| Note | Forest trusts are new in Windows Server 2003. They involve a great deal of complexity that does not exist in other trust relationships. It is important to note that when a forest trust exists, the Global Catalog for each forest remains separate. Much of the additional complexity stems from this fact. When a user who is logged on to a domain in one forest attempts to access resources in a domain located in the other forest, special pointers in the local forest’s Global Catalog must be present. The default settings often allow for a free exchange of users in each direction the trust allows. For maximum security, these pointers should be manually configured by an administrator, so that only specific domains or resources on each side of the trust are accessible from across the trust. |
To improve the performance of replication across the network, the Windows Server 2003 level allows linked value replication. To ensure that all domain controllers have a duplicate copy of AD, directory data is replicated between them. Linked value replication improves replication by having less information copied between domain controllers. Rather than treating the entire membership of a group as a single unit of replication, linked value replication allows individual members of groups to be replicated (instead of the entire group).
When the functional level is raised to Windows Server 2003, you can make additional modifications to the schema by disabling classes and attributes. When a particular type of object or an attribute is no longer needed in an object, the class or attributes within it can be deactivated. The ability to disable schema objects was available in Windows 2000, but Windows Server 2003 provides the ability to reactivate them again when needed. If schema objects are no longer required, you can deactivate them, and then reactivate them later if the situation changes. (Although classes and attributes can be disabled, they cannot be deleted.)
Now that we’ve discussed raising the domain and forest functional levels, let’s look at the procedure for doing it. Exercise 2.2 will walk you through the process of raising both of these functional levels, so that all of the features discussed earlier are available for use.
Exercise 2.02: Raising Domain and Forest Functionality
The following steps should not be performed on a production network. This exercise assumes that all domain controllers in the domain are running Windows Server 2003. After raising the functional levels, you will not be able to roll back to a previous level.
-
Select Start | Administrative Tools | Active Directory Domains and Trusts.
-
When Active Directory Domains and Trusts opens, expand the Active Directory Domains and Trusts node and select your domain.
-
Select Action | Raise Domain Functional Level.
-
In the Raise Domain Functional Level dialog box, select Windows Server 2003 from the drop-down list, and then click the Raise button.
-
A warning message will appear, informing you that this action will affect the entire domain and cannot be reversed. Click OK.
-
After you raise the level, a message box will inform you that the action was successful. Click OK to continue.
-
Select the Active Directory Domains and Trusts node.
-
Select Action | Raise Forest Functional Level.
-
In the Raise Forest Functional Level dialog box, select Windows Server 2003 from the drop-down list, and then click the Raise button.
-
A warning message will appear, informing you that this action will affect the entire forest and cannot be reversed. Click OK.
-
After you raise the level, a message box will inform you that the action was successful. Click OK, and then exit the utility.
Identifying Minimum Security Requirements for Your Organization
EXAM 70-293 OBJECTIVE 1.4.1
Before you can begin implementing security measures, you need to know what needs protecting. Different organizations have different needs, so the systems and data that are essential to one company may be superfluous to another. For this reason, the security planning process involves considerable analysis. You need to determine which risks could threaten a company, what impact these threats would have on the company, the assets that the company needs to function, and what can be done to minimize or remove a potential threat.
Risk is the possibility of experiencing some form of loss. This isn’t to say that a risk will become a real problem, only that it has the potential of happening. To address risks, you need to determine which events and factors in an organization are potential threats, and then devise ways to deal with them before they become actual problems. There are many different risks that can affect an organization, and the types of risks will often vary from business to business. The following are the main types of threats:
-
Environmental threats, such as natural and man-made disasters
-
Deliberate threats, where a threat was intentionally caused
-
Accidental threats, where a threat was unintentionally caused
Environmental threats can be natural disasters, such as storms, floods, fires, earthquakes, tornadoes, and other acts of nature. The types of disasters that can occur generally vary from one geographical region to another. For example, a business in California might be more prone to earthquakes, while an organization in Canada might be at risk of severe snowstorms. When dealing with this type of disaster, it is important to analyze the entire company’s risks, considering any branch offices located in different areas that may be prone to different natural disasters.
Human intervention can create problems as devastating as any natural disaster. Man-made disasters can also occur when someone creates an event that has an adverse impact on the company’s environment. For example, faulty wiring can cause a fire or power outage. In the same way, a company could be impacted by equipment failures, such as the air conditioning breaking down in the server room, a critical system failing, or any number of other problems.
The deliberate threat type is one that has appeared numerous times in the news over the last number of years. These types of threats result from malicious persons or programs, and they can include potential risks such as hackers, viruses, Trojan horses, and various other attacks that can damage data and equipment or disrupt services. This type of threat can also include disgruntled employees who have authorized access to such assets and have the ability to harm the company from within.
Many times, internal risks are not malicious in nature, but accidental. Employees can accidentally delete a file, modify information with erroneous data, or make other mistakes that cause some form of loss. Because people are fallible by nature, this type of risk is one of the most common.
Each business must identify the risks it may be in danger of confronting and determine what assets will be affected by a potential problem. Assets are property and resources that have value to the company, and they can include the following:
-
Hardware Servers, workstations, hubs, printers, and other equipment.
-
Software Including commercial software (which is purchased off the shelf) and in-house software (which is developed by programmers working for the company).
-
Data Including documents, databases, and other files needed by the business.
-
Personnel Employees who perform necessary tasks in the company (for example, the network administrator who knows how to restore damaged systems from a backup).
-
Sundry equipment Office supplies, furniture, tools, and other assets needed for the business to function properly.
-
Facilities The physical building and its components.
As you can see, any number of risks could result in the loss of a wide variety of assets. For example, a fire could destroy a building, including the facilities containing servers that store critical software and data. It might also injure key personnel who are necessary for the business to function. With one disaster, an entire company can be crippled.
When identifying minimum security requirements, it is important to determine the value and importance of assets, so you know which are vital to the company’s ability to function. You can then prioritize risk, so that you can protect the most important assets of the company and implement security measures to prevent or minimize potential threats.
| Test Day Tip | Questions dealing with identifying the minimum security requirements will be mixed with issues directly related to Windows Server 2003. They will test your knowledge by matching the minimum requirements shown in a scenario against the features and functionality of Windows Server 2003. |
Determining the value and importance of assets can be achieved in a number of ways. Keeping an inventory of assets owned by the company will allow you to identify the equipment, software, and other property owned by the company. By referring to this list, you can see the possessions of the business, and you can update this list to reflect the current monetary value. For example, you could see that a new server has specific software and hardware installed on it, and it would cost a specific amount to replace. In the same light, an older server may cost less to replace, but contain sensitive data that makes it valuable to the company.
To determine the importance of data and other assets, and thereby determine what is vital to secure, you can meet with department heads. Doing so will help you to identify the data and resources that are necessary for people in each department to perform their jobs. For example, a Human Resources department might specify that a particular database is used for critical information and that specific software is needed. At the same time, you could find that a folder on the server contains a Web site used by employees to advertise items for sale, upcoming events, and other material that is not work-related. By discovering this information, you make great strides in being able to protect the work-related material while expending little to no effort in preserving non-work-related files. You will also probably find that you need the assistance of the Accounting department to determine appropriate values.
In addition to interviewing different members of an organization, review the corporate policies for specifications of minimum security requirements. For example, a company may have a security policy stating that all data is to be stored in specific folders on the server, and that the IT staff is required to back up this data nightly. Such policies may not only provide insight on what is to be protected, but also what procedures must be followed to provide this protection.
Organizational policies are not the only method of acquiring information on security requirements. Companies may be required to protect specific assets by law or to adhere to certain certification standards. For example, hospitals are required to provide a reasonable level of security to protect patient records. This may include implementing firewalls to prevent hackers from accessing these files through the Internet. If such requirements are not met, an organization can be subject to legal action.
Identifying Configurations to Satisfy Security Requirements
To protect assets from risks that were identified as possible threats to a business, countermeasures must be implemented. Servers will need certain configurations to provide security, and plans must be put into practice. By applying methods to protect assets, the potential loss can be minimized or removed, and the security requirements of a business can be met.
Compare the risks faced by an organization with an operating system’s features to find support that will address certain threats. Configuring the server to use these services or tools can assist in dealing with potential problems. For example, installing AD and using domain controllers on a network can heighten security and provide the ability to control user access and security across the network. In the same way, configuring a file server to use EFS so that data on the server’s hard disk is encrypted can augment file security. Using security features in an operating system allows you to minimize many potential threats.
The same technique should be used when determining which roles will be configured on servers. As described earlier in this chapter, different server roles provide different services to a network. By comparing the functionality of a server role to the needs of a company, you can identify which roles are required. For example, if you need secure communication and transmission of data on a network, configuring IPSec will be a viable solution. Similarly, configuring servers to be DNS or WINS servers will provide name resolution. Domain controllers allow you to benefit from AD. By understanding what people need in your organization, you can determine which server roles must be configured.
Although it may be tempting to configure a server with every possible role, this can cause problems. When a server is configured to play a certain role in an organization, a number of different services, tools, and technologies may be installed and enabled. Because there is a possibility these may be exploited, you should avoid this risk by never installing more roles than are needed. Always disable any unneeded services on the server.
Although roles are helpful, running a wizard to configure servers in a particular role isn’t enough to create a secure environment. Additional steps should be followed to protect these servers and the data, applications, and other resources they provide. By customizing servers in this manner, you can ensure that the company will be able to benefit from Windows Server 2003 without compromising security. We’ll discuss these steps in the “Customizing Server Security” section later in this chapter.
|
EAN: 2147483647
Pages: 173