Planning for BitLocker Deployment
Servicing a BitLocker-Protected Computer
A computer is not a static thing. You will need to apply patches, or update applications or even firmware. With BitLocker using a TPM to validate the state of the system, which changes are you allowed to make? What will trigger recovery?
You may recall reading about how the VMK helps BitLocker remain secure on occasions where you may want to disable BitLocker without re-encrypting the disk. This is usually referred to as "disabled mode," but is probably more correct to say that "protection is off." By disabling BitLocker, you can cause the keys to be resealed by the TPM. That is, BitLocker is disabled while you make a change that would otherwise cause recovery, and then when Bit-Locker is reenabled, the new keys are sealed to the new PCR values.
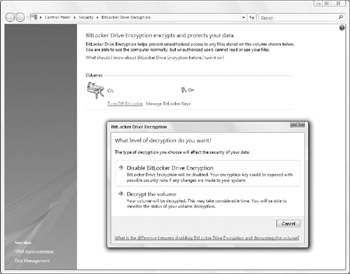
As you can see in this figure, when you use the control panel, you can choose whether or not to decrypt the drive:
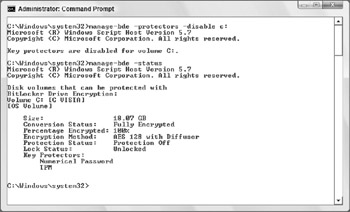
Disabling BitLocker can also be done through the command line, and the status can also be checked. (In fact, for batch files, you can even return the protection status as an ERRORLEVEL value. Pretty clever.)
Since the BIOS is hashed by the TPM and monitored by BitLocker, a BIOS upgrade would cause BitLocker to lock the volume and go into recovery mode. Accordingly, you should always disable BitLocker for a BIOS upgrade.
On the other hand, updates to Microsoft Windows Vista sent through the Windows Updates process (including Automatic Updates) are signed and BitLocker aware; therefore, you do not need to disable BitLocker in the course of regular Windows updating.
What's in between is the gray area of other updates. Patches sent by application and software vendors or perhaps upgrades to hardware components or drivers may or may not need BitLocker to be disabled-probably not, if the update is only touching user-mode application software. When dealing with drivers, it certainly won't hurt to be cautious and disable BitLocker, or to be prepared with a recovery password (ideally on a USB flash drive) just in case.
EAN: 2147483647
Pages: 101