Secure Decommissioning
Managing the TPM and BitLocker in the Enterprise
Group Policy is only one tool that can be used to manage BitLocker. Because BitLocker and TPM Base Services both include WMI providers, there operations are exposed through WMI. If you have a WBEM management console, you can access BitLocker as part of your WBEM strategy. But WMI brings a couple of other interesting features into play.
The first is remote management. Anything that you can do locally through WMI you can do remotely. This makes management of a large number of machines much more palatable. There is one limitation to the remote aspect of managing BitLocker. Part of the TPM specification requires proof of a user's physical presence to take ownership of a new TPM chip, in order to prevent malware from gaining control of the TPM. Xian Ke blogged about the impact of physical presence in a post on the BitLocker team blog, available at http://www.blogs.technet.com/bitlocker/archive/2006/05/12/428173.aspx. In that situation, someone needs to be present at the computer being managed.
The second feature built on WMI is rather helpful for us mere mortals. The BitLocker team has created a command-line tool that does the work of talking to WMI and the BDE and TBS providers for you. The tool is named manage-bde.wsf and it ships with Vista. It is expected that there will be a downloadable document detailing the operation of manage-bde, but really, the help included with the file is very complete. The following screenshot gives you some idea of the commands available with manage-bde.
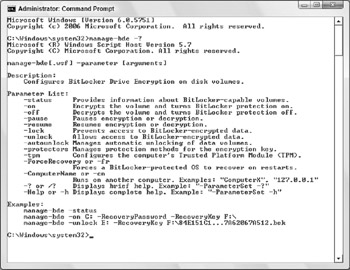
Notice that the –cn (or –computername) parameter lets you run manage-bde against remote computers.
Here are some examples of using manage-bde to accomplish real tasks. Let's say you have a remote computer on which you'd like to determine whether or not BitLocker is enabled. (Oh, and let's say you've cleverly named your computer bhynes-vistabde.)
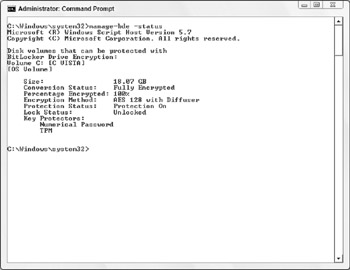
Manage-bde.wsf -cn bhynes-vistabde -status c:
You'd get results like this:
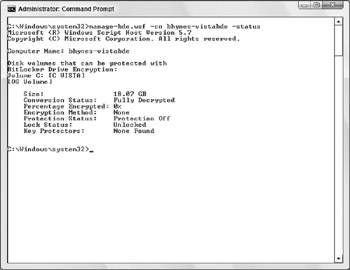
Since you know that the computer has already had it's TPM activated, perhaps by IT when Vista was installed, and now it is ready to have you turn on the TPM and take ownership, use these commands:
Manage-bde.wsf -cn bhynes-vistabde -tpm -TurnOn Manage-bde.wsf -cn bhynes-vistabde -tpm -TakeOwnership NewPassword
Your results from these commands will vary depending on the exact state of your TPM. But now, you want to turn on BitLocker, including the enabling of recovery, and verify that encryption has started:
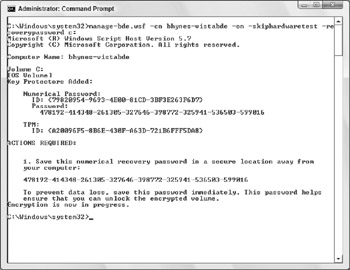
Manage-bde.wsf -cn bhynes-vistabde -on -skiphardwaretest -recoverypassword c:
Manage-bde.wsf -cn Bhynes-vistabde -status c:
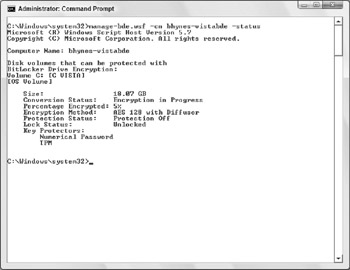
A few things to note: I happened to give the name of the computer even though I was using that computer's console, so you can use manage-bde locally (with or without the -cn parameter) or remotely (with the –cn parameter). Since I was working locally, this was also evidence that the computer remains fully available when the initial encryption is occurring.
Since I don't consider a picture in a Mark Minasi book to be a "secure location" (although it does qualify as "away from the computer"), I have already changed my recovery password.
EAN: 2147483647
Pages: 101