Chapter Scenario: Fabrikam, Inc.
Fabrikam, a defense contractor with offices located across the United States, is investigating the use of IPSec to improve security on their local network and on the network link to their business partner, A. Datum Corporation.
The Network
Fabrikam's Wide Area Network (WAN) is linked with 1.544 megabit-per-second (Mbps) private network links. Each office is assigned a class B address space, but not all addresses at the office are currently in use, as shown in Figure 12.1.
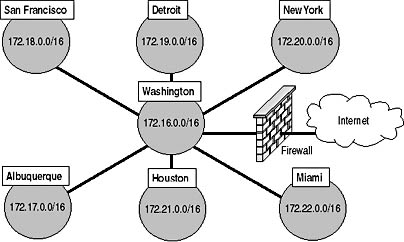
Figure 12.1 The Fabrikam WAN configuration
Fabrikam has deployed a firewall to protect the Washington office from attacks coming from the 45 Mbps link to the Internet. On the Internet, Fabrikam owns the 131.107.2.0/24 network range.
Connecting to A. Datum Corporation
Fabrikam is working with A. Datum Corporation to develop a new sonar system for the Department of Defense. Several Fabrikam employees are working at the A. Datum Corporation office in Chicago.
A. Datum Corporation wants to establish a secure WAN link between the two organization's networks using their existing Internet connections. Due to the sensitive nature of the projects, all data that's transmitted over the Internet must be encrypted to ensure that the data isn't compromised. Figure 12.2 shows the current network configuration for A. Datum Corporation and Fabrikam.
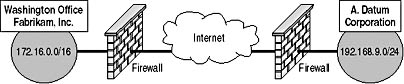
Figure 12.2 Connectivity between the Fabrikam and A. Datum Corporation offices
A. Datum Corporation and Fabrikam have had great difficulty configuring this WAN connection. Authentication has been failing between the two tunnel servers.
The Data Collection Package
Fabrikam is also involved in a project with the Department of Defense developing a new radar system. The radar's prototype is complete and they're testing it to determine if the prototype meets the Defense Department's design specifications. The testing is being performed at Fabrikam's Albuquerque office.
To test the design, Fabrikam has created a custom data collection application housed at the Washington office. The application's server portion is hosted on a Windows 2000 member server. The data collection software uses Transmission Control Protocol (TCP) and clients will connect to the application by connecting to port 5555 on the server. The server is located at IP address 172.16.100.123.
To collect and transmit test data, the radar prototype is connected to a Windows 2000–based laptop using a Universal Serial Bus (USB) connector. The client portion of the data collection software connects to the server at the Washington office to upload the latest data. The client uses a random port for the connection to the server. All data that's transmitted must be protected from impersonation and from inspection attacks. The data must also be protected from attacks, such as a source routing attack, that attempt to reroute the packets.
Fabrikam plans to test additional radar devices in the future. The testing will require multiple laptops configured to use IPSec to protect data streams to the server at the Washington office. All the laptops will be based at the Albuquerque office.
EAN: 2147483647
Pages: 172